Spear Phishing: Statistics, Past Incidences and Defense Mechanisms
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 2535 words | ✅ Published: 18 May 2020 |
Spear Phishing
Abstract—Spear phishing is an attack which is very useful for an attacker to gain access in an organization .There are numerous reasons why spear phishing is so effective. Firstly, it becomes very complicated to detect which email is regular and which is an anomaly. Secondly, with the help of social engineering, the attacker can determine what sort of email design the user would feel trustworthy, in order to access it. In this report, we have discussed about the statistics of spear phishing, past incidents that have affected firms, steps involved in spear phishing and defense mechanisms against spear phishing.
Key words: Spear phishing, exploit, backdoor, malicious link, phishing awareness, content analyzer
I. Introduction
In today’s world due to the usage of emails we are becoming more vulnerable to attacks like ‘Phishing’. Phishing is a broad spectrum attack in which the victims can be of large numbers wherein the victims are duped into opening an email, a text message. Phishing can also be done via a phone call, this particular type is called ‘Vishing’(voice Phishing) [1]. The main objective of this attack is to gather victim’s user credentials such as username and password by luring them with an exciting offer or a task which is to be completed urgently. In recent times, a new type of effective phishing attack has surfaced, known as ‘Spear Phishing’. This attack is very specific towards an organization, or a person with high level of access rights within a firm. Unlike its parent attack, Spear Phishing is implemented only on a specific person via emails. In this attack social engineering techniques are used for extracting information about the victim. In usual cases the victims are selected on the basis of financial responsibilities or high level privileges in an institute [2].
This report is divided into the following sections. First of which is an overview of the impact of spear phishing over the previous years, which lists a few reports made by firms such as Kaspersky, Symmantec, Avanan and Flashpoint. Section three discusses about the generic steps an attacker takes to infiltrate an organization. Section four is a detailed description about some of the past attacks that took place in large scale corporations causing a devastating impact financially as well as affected the stature of the company.
II. Impact of spear phishing
In the times gone by, the reports on the impact of spear phishing states that, even large scale corporations with state of the art security mechanisms are also susceptible to email attacks like phishing and more specifically spear phishing.
A. According to the report made by the Verizon’s data breach investigation commitee stated that phishing was used in 32% of the data breaches that happened in 2018. Also, 78% of the cases involving cyber espionage like backdoor installation happened with the help of phishing [3].
B. Report made by Avanan Inc states that, two out of every fifty emails on an average are phishing emails.
for you [4].
C. In 2017, Phishing was used to attack 76% of the firms that were audited [5].
D. 83% professionals in the field of information security experienced Spear Phishing attacks in 2018[6].
E. In 2012, spear phishing was responsible for over 90 percent of the cyber attacks [4].
F. According to a report made by the firm Avanan, a cloud security firm was attacked with more than half of the phishing emails having malicious links [4].
G. According to report made by Phish labs, more than 50% of the malicious phishing sites had SSl certificates that authenticated them [7].
H. According to a report by Kaspersky Labs, 21% of the users in Brazil were targeted by phishing attacks [8].
I. Reports of ProofPoint, states that the most common effect of phishing is compromising of credentials which is 65% of the phishing attacks [9].
J. Another research report made by Avanan, the research suggests that out of the 4% of phishing emails 33% bypass the default security parameters of an organization [4].
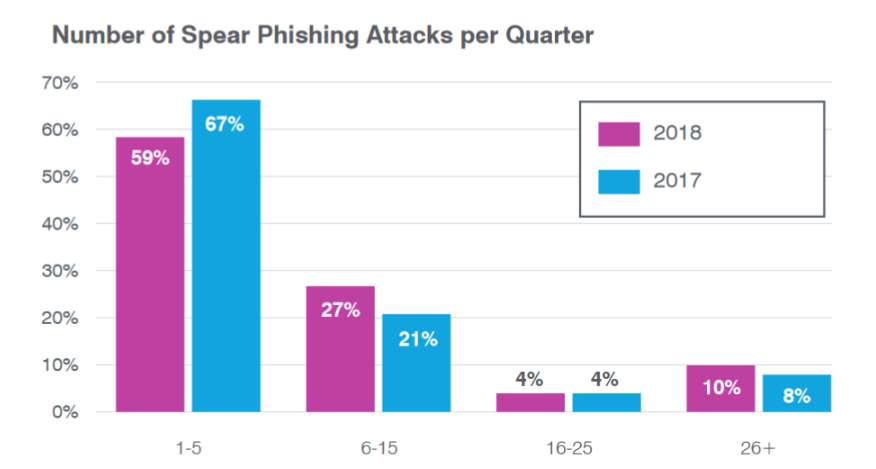
Statistics of spear phishing in 2017, 2018 quarterly [14]
III. Steps of spear phishing
- Selecting the victim:
This is the core part of the attack. The attackers in certain cases have to choose people within the institution who have the authority of transferring funds to other departments [2]. Another requirement that the victim should have is higher access privileges that will eventually enable the attackers to either plant a backdoor or exploit the user credentials to gain access rights of the firm.
- Reconnaissance:
Spear Phishing involves digital reconnaissance of a particular victim. From the reconnaissance the interest areas of the victim are used to craft an email. Social media sites such as Facebook, instagram and linkedInare used to find outdetails about the victim. For example, the linkedIn profile can display the current organization the victim is working in and also the stature the victim holds in the institution.
- Crafting the Fraudulent email:
This step requires utmost attention to detail. The forged email has to be very identical to the original one victim gets in similar circumstances. The email is designed in such a way which is tempting for the victim to open. Once the victim clicks on the link mentioned in the email, the victim is redirected to a webpage that looks original but is actually hosted by the attacker as hoax to steal whatever data the victim enters as input [10]. The web page can consist of a login form or credit card detail form which will fool the victim into believing the fake webpage as real. Cases have emerged where phishing emails have been sent to employees of a firm, falsely stating that an update of login credentials such as password is needed.

Sample email phishing [13]
IV. Past incidents
- Ubiquiti
Real life examples in which spear phishing has caused havoc in the technological world can be summarized from a reports made by the United States securities and exchange commission of the year 2015. In this report, a firm named Ubiquiti Networks Inc which is known for its services, products and enterprises in the field of network technology was attacked with the help of spear phishing causing which the loss of money amounted to 46.7 million dollars. The funds were kept by a child company in Honk Kong whose parent company was Ubiquiti. The funds were given by the employees that were duped into thinking that requests for money were coming from the higher authorities of the organization. Instead the requests were from malicious outer entities that were impersonating the higher authorities of the company via spoofed email addresses and identical links that looked like the original ones. This example proves that spoofed emails and identical links can cause catastrophic damage to company or an institution [11].
- EMC Corp
The RSA unit of security in data-storage was exploited by a flash object which was inserted in a excel file, which was sent as an attachment in an email. The subject line of the email stated 2011 recruitment plan. The email was very intelligently crafted and was sent to two groups of small number of employees. Although, the email after the filtration landed in the junk folder, the email was sent twice in two days but because of its authentic design it was retrieved by an employee. The email comprised of an excel sheet which had a malicious payload, used for exploiting a vulnerability which had no patches yet. The payload was inserted in Adobe Flash. Once the attachment was opened, the payload installed a backdoor, which successfully stole the credentials of the employees and sent them to the attackers [11]. This particular case proves that even top tier firms that are known for data storage and collective security of data as well as the firm can also be the victims of Spear Phishing attacks.
- WIPRO Spear Phishing attack 2019.
In 2019, one of the largest IT firms in India was hit by spear phishing attack. The attack comprimised Windows user credentials of many employees. As per the report published by security researchers from Flashpoint Allison Nixon, Joshua Platt and Reeves Jason stated that the attack resulted in dozens of user credentials being stolen and more than hundred devices have been infected. A previous report by KrebSecurity states that the attack had possibly started as early as April 2015. The phishing attack used numerous applications, used for security mechanisms. These applications were used as templates for security awareness programs within the company. For example, attackers used a sample of phishing design to mislead the employees. This sample was infact was used by the security teams within the company to spread awareness about phishing which was stolen by the attackers and was used in crafting of the email used for phishing. In order to infect devices inside the organization an application called Screenconnect. It was also found that domains used by the attacker to host their phishing links were running Powersploit and scripts of powerkatz in the background. The tools Screenconnect is used for remotely accessing a device. It can be used for logging in into a meeting remotely. Powerkatz which is a commandline powershell was used for searching various authentication parameters of employees or devices which stored in the system. Powerkatz is very efficient because it also has the power to look for clues within the device or even a database to look for things like username, default password of the devices and password. The other script which was running in the background was Powersploit. This tool is a compilation of scripts which run exploits in the background for attacking a device or an infrastructure. After examining the phishing links, IP adddresses, and DNS, the links were maliciously hosted on the servers. Flashpoint researchers came to a conclusion that numerous domains were used for hosting the phishing links with similar domain names to fool the employees. The phishing links were used for stealing credentials which were then used for accessing encrypted emails. The employees were lured into clicking via gift card advertisement that was often seen by employees within the company [12].
V. Defense Mechanisms
- Phishing Awareness Programme
In this report we have seen that most of the phishing attacks were due to the unaware employees clicking on malacious web links. The problem with phishing is that anyone could be easily targetted into opening and accessing the email. In order to tackle this problem, regular security training should be given to the employees such as Phishing awareness modules. These modules should explain the details of previous attacks to technical as well non technical staff members [11] .
- Internal Email Infrastructure
An internal email structure should be devised so that the employees use this email only for official work within the
organization. The email system should be setup in such a way that it would filter out all the emails which are not coming from the organization. This would decrease the attack surface significantly [5].
- Content Analyzer
Any foreign content being sent should be analyzed with the help of algorithms in Machine learning and Data analytics [5].
- Regular updates
Any organization is susceptable to zero day attacks which do not have a patch yet. These type of attacks can be sent as a payload in one of the emails as an attachment. In order to protect against these attacks it is very essential that all systems and devices should be patched in advance. Patches can be of multiple types like software patches, operating system patches or any software devices patches.
- Automating the process of Isolation
Inorder to stop the spread of malacious processes . The infected section should be isolated autmatically [5].
VI. Conclusion
This report is a compilation of all the different types of spear phishing attacks. Steps in which spear phishing is planned from the attacker’s perspective have been discussed which is very important to get inside the mind of an attacker. The three different styles of spear phishing attacks that have taken place in the past which resulted in tremendous loss of data or fianance. The number of cyber attacks in the future are likely to rise as per reports, therefore to break through a very sophisticated and highly advanced security infrastructure hackers will resort to email attacks like phishing and spear phishing whose prevention requires awareness. It only takes one ill timed click from a unaware employee inorder to compromise a well defended security fortress. Thus we can conclude that attacks like spear phishing are going to rise proportionally with the rise in cyber attacks because hackers also exploit the psychology of employees.
References
[1] T. Halevi, N. Memon and O. Nov, “Spear-Phishing in the Wild: A Real-World Study of Personality, Phishing Self-Efficacy and Vulnerability to Spear-Phishing Attacks”, SSRN Electronic Journal, 2015. Available: 10.2139/ssrn.2544742.
[2] “CiteSeerX”, Citeseerx.ist.psu.edu, 2019. [Online]. Available:http://citeseerx.ist.psu.edu/viewwdoc/download?doi=10.1.1.467.904&rep=rep1&type=pdf. [Accessed: 12- Oct- 2019].
[3] “2019 Data Breach Investigations Report”, Verizon Enterprise, 2019. [Online]. Available: https://enterprise.verizon.com/resources/reports/dbir. [Accessed: 12- Oct- 2019].
[4] “Avanan | How Email Became the Weakest Link”, Avanan.com, 2019. [Online]. Available: https://www.avanan.com/how-email-became-the-weakest-link. [Accessed: 12- Oct- 2019].
[5] Info.wombatsecurity.com, 2019. [Online]. Available: https://info.wombatsecurity.com/hubfs/Wombat_Proofpoint_2019%20State%20of%20the%20Phish%20Report_Final.pdf. [Accessed: 12- Oct- 2019].
[6] Information about Spear Phishing attack”, Success.trendmicro.com, 2019. [Online]. Available:https://success.trendmicro.com/solution/1121072-what-is-spear-phishing. [Accessed: 12- Oct- 2019].
[7] “Stop threats that exploit employees, customers, and brands. | PhishLabs”, PhishLabs, 2019. [Online]. Available: https://www.phishlabs.com/. [Accessed: 12- Oct- 2019].
[8] M. Vergelis, T. Shcherbakova and T. Sidorina, “Spam and phishing in Q1 2019”, Securelist.com, 2019. [Online]. Available: https://securelist.com/spam-and-phishing-in-q1-2019/90795/. [Accessed: 12- Oct- 2019].
[9] ]”2019 State of the Phish – Cyber Security Insights Report | Proofpoint”, Proofpoint.com, 2019. [Online]. Available: https://www.proofpoint.com/us/resources/threat-reports/state-of-phish. [Accessed: 12- Oct- 2019].
[10] “What is Spear Phishing? – Definition from WhatIs.com”, SearchSecurity, 2019. [Online]. Available: https://searchsecurity.techtarget.com/definition/spear-phishing. [Accessed: 12- Oct- 2019].
[11] “SEC.gov Reports and Publications”, Sec.gov, 2019.[Online].Available:https://www.sec.gov/reports. [Accessed: 12- Oct- 2019].
[12] “Flashpoint – Wipro Threat Actors Active Since 2015”, Flashpoint, 2019. [Online]. Available: https://www.flashpoint-intel.com/blog/wipro-threat-actors-active-since-2015/. [Accessed: 12- Oct- 2019].
[13] “Phishing Emails Impersonating University Leaders | Office of the CIO”, Ocio.osu.edu, 2019. [Online]. Available: https://ocio.osu.edu/blog/community/2016/03/18/phishing-emails-impersonating-university-leaders. [Accessed: 13- Oct- 2019].
[14] P. UK, A. Moscaritolo and A. Moscaritolo, “Beware: Phishing Attacks Are on the Rise”, PCMag UK, 2019. [Online]. Available: https://uk.pcmag.com/news/119374/beware-phishing-attacks-are-on-the-rise. [Accessed: 13- Oct- 2019].
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


