Analysis of P1 Control Panel
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 1201 words | ✅ Published: 23 Sep 2019 |
P1 Control Panel/VNC/Questioning of Users/Fault log and Solutions Database
P1 explain the tools and techniques used for technical support
What is the Control Panel?
 The Control Panel contains everything a user requires to control the PC. Through the Control Panel, the user can add new pieces of hardware or setting the time correctly. Control Panel also gives the user the ‘Internet’ options along with ‘power’ options.
The Control Panel contains everything a user requires to control the PC. Through the Control Panel, the user can add new pieces of hardware or setting the time correctly. Control Panel also gives the user the ‘Internet’ options along with ‘power’ options.
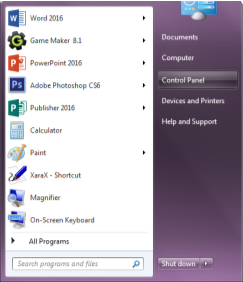
The way a user can reach the Control Panel is through the ‘Windows’ icon on the bottom left hand side of the screen a menu that looks like the screenshot to the side will appear. Next, the user would have to click on the ‘Control Panel’ text, which is under ‘Computer’ and on top of ‘Devices and Printers’.
The following box will appear on the screen.
If the user is an Administrator it gives them the option to change some of the settings in the Control Panel whereas a normal user would not be able to change as it would not even appear. Along with this the Administrator has their own set of ‘Administration Tools’ which only they can access.
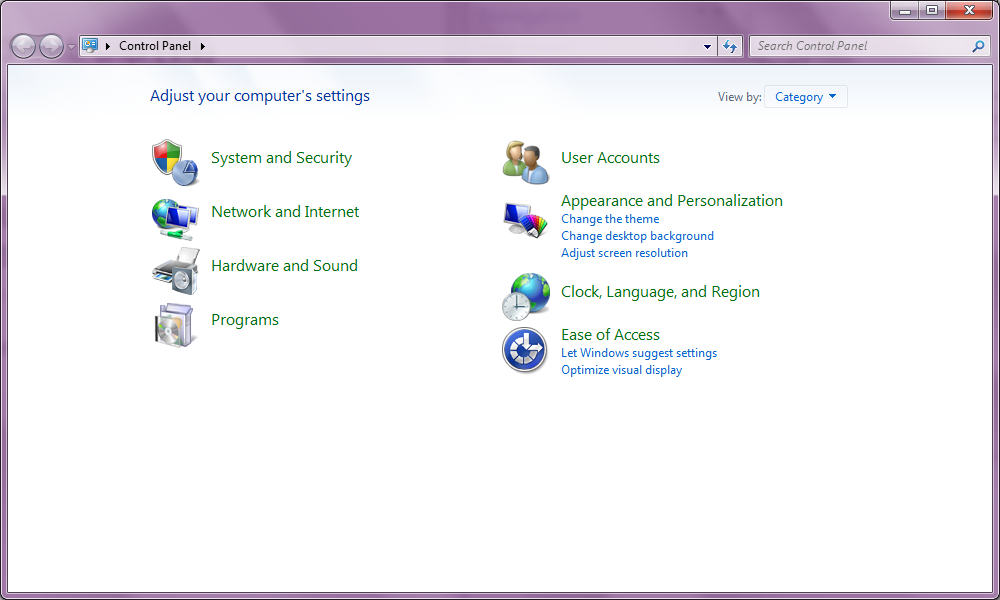
This above is a full version of the Control Panel but in this view of the Control Panel the normal user cannot access much whereas the Administrator can access all of them. The ‘Programs’ options allow the Administrator to install and uninstall software they can also set the ‘Clock, Language, and Region’ so the normal users don’t have to. Finally, a big option for the Administrator would be the ‘Network and Internet’ settings, which gives the Administrator the options to set up the computer to the network or wireless Internet.

P1 explain the tools and techniques used for technical support
What is a VNC?
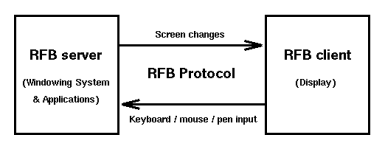
VNC stands for ‘Virtual Network Computing’, which is a technology for remote desktop sharing. Using Virtual Network Computing enables the use of visual desktop displays of a single computer that can be remotely viewed and controlled over a network connection.
Technology support can use VNCs to help people that use the same network connection as them for example: a company technology support can access any computer that a user is having trouble on and help them.
VNC was originally an open-source research project in the late 1990s. After this, it turned into many other VNCs.
VNCs work in a client/server, which uses a network protocol, called Remote Frame Buffer (RFB) them servers used by VNC capture local display ‘framebuffer’ contents and share them back to a client.
VNC is regarded as generally slower and others fewer features then other means of security options than newer verisons. Microsoft had incorporated remote desktop functionality into its operating system (OS) starting with the version ‘Windows XP’. This feature is called ‘Windows Remote Desktop’ which allows the PC to receive remote connection requests from compatible clients.
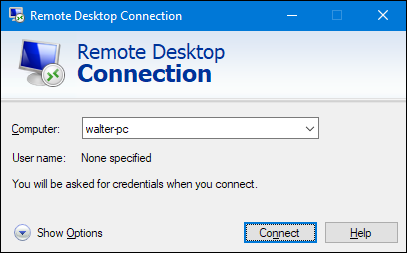 In this screenshot, it shows the first version of ‘Windows Remote Desktop’ on Windows XP. This checks if the connection is acceptable to receive requests from clients.
In this screenshot, it shows the first version of ‘Windows Remote Desktop’ on Windows XP. This checks if the connection is acceptable to receive requests from clients.
 Direct questioning of users –
Direct questioning of users –
This is a form of communication where the end user contacts the support technician to fix a problem they have encountered. During the exchange, the end user tries to explain the problem to the support technician the goal of this is to find out as much as possible so that the support technician can make the decisions on where the fault lies and how the problem can be resolved.
Before accepting the call, the support technician would have to check to see if the caller is entitled to the support services, they provide. This means they would have to ask for the caller’s user name and password or account number this allows the technician to get personal data on the caller that they can use to help.
Depending on the caller’s status on the ‘service level agreement’ determines what they should expect from the technician, making sure their needs have been met.
After finding out if the end caller is entitled to the support services find out what has happened up to date if the information is known the technician can ask ‘What seems to be the problem?’. All the important information is reported into a fault log.
P1 explain the tools and techniques used for technical support
What is a Fault Log? –
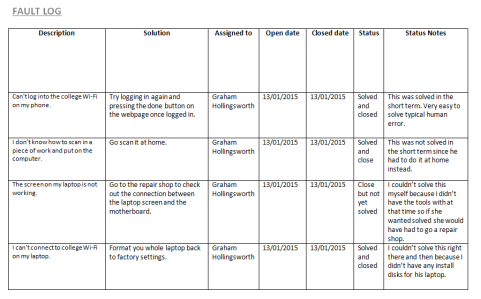 A fault log is a record of events that have occurred this can include information about faults and how they were fixed. IT technicians tend to use faults logs as a means to record problems and how they were solved for example the fault log may content the following information: Name, Where the fault took place, Time of fault, the actual reported fault, how long the fault has been going, Platform (PC/Mac), and the ‘Suggested Solution’.
A fault log is a record of events that have occurred this can include information about faults and how they were fixed. IT technicians tend to use faults logs as a means to record problems and how they were solved for example the fault log may content the following information: Name, Where the fault took place, Time of fault, the actual reported fault, how long the fault has been going, Platform (PC/Mac), and the ‘Suggested Solution’.
An example of this would be the fault log I have made in a later task Freya has appeared with a login problem I found out the name, location, platform, and fault to solve this I reset the password with a default password.
Generally, most of the problems recorded in fault logs are hardware and software related while recording in the fault log can remind the technicians of the faults if they arise again it can also teach the colleagues experiencing the problem. Below is an example of what a fault log looks like.
What is a Solutions database? –
A solutions database is like a fault log but more of a repository of information which are stored as ‘problems’ and ‘solutions’ and are indexed for immediate retrieval. This is used by knowledge administrators use the Solution Database to define problems that have already been solved. The solutions database was created to store problems that people can quickly search queries which saves people time from researching it again. An example of various things that can be stored in a Solution Database are ‘Call ID’ this is a unique reference number for the caller so the fault can be recorded easily with the person its affected. ‘Date and time of initial call’ the reasons behind this is so the fault can be recorded at the time it was spotted and the time it was solved. ‘Recommendations’ this section of the database is for what should be recorded during the problem solving of the fault also who solved the problem along with equipment that should be purchased if a hardware/software problem occurs.
Solution databases can be written in different forms like hand written or typed on a computer. Technicians can choose a range of software to write databases like ‘Microsoft Access’ or ‘Microsoft Excel’ or programmed by the companies that don’t want to use Access or Excel. Some companies choose to create the databases themselves because they believe that Access or Excel is to tedious while creating databases. Excel can get too in depth with all the graphs that can be made up in Excel.
- http://itexperiencesandhelpdesk.blogspot.com/2015/06/my-fault-log-from-help-desk-day.html – Fault log example.
- https://www.lifewire.com/vnc-virtual-network-computing-818104 – VNC
- https://support.microsoft.com/en-us/help/13764/windows-where-is-control-panel – Where to locate control panel on different platforms of windows
- https://www.howtogeek.com/howto/windows-vista/turn-on-remote-desktop-in-windows-vista/ – Picture of the Remote Desktop Connection
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


