Unified User Profiles- Advantages and Disadvantages
| ✅ Paper Type: Free Essay | ✅ Subject: Technology |
| ✅ Wordcount: 3904 words | ✅ Published: 23 Sep 2019 |
UNIFIED USER PROFILES- ADVANTAGES AND DISADVANTAGES

Abstract
This study sheds light upon a new research on unified user profiles. In a recent survey, it is seen that the amount of total global data is expanding to double in number in every two years. This rate of increase in the total amount of global data has helped to exceed the total amount by 1.8 Zetta-byte. Based on this challenge the Unified User Profile system is been developed. This system works as the linker between profiles or interfaces. It gives importance towards the additional properties of each user interface. This discussion has shed light over the working process of the UUPM system and the relative framework of the technology. IT has also highlighted the general advantage and disadvantages of the system in context to the business environment. This discussion has also highlighted the gap in the past researcher. This discussion has included different stages of conducting the research. Hence, it is seen that the research will promote the positivist theory while conducting the research and will follow the deductive approach. However, the researcher will use both the primary and secondary data collection process. To avoid any external influence the researcher will follow random sampling.
Table of Contents
1.1 Background of the research
2.2 The Unified User Context Model
2.3 User profile management method
2.3.2 UCC generation and dissemination
2.4 Advantage and disadvantages of UUPM
Appendix 1: Interview questions
1.1 Background of the research
Nowadays development in the data based digital system has changed the definition of the modern IT technology. Storage of information and transfer of information is based on data-driven technology. In a recent survey, it is seen that the amount of total global data is expanding to double in number in every two years. This rate of increase in the total amount of global data has helped to exceed the total amount by 1.8 Zetta-byte. On the other hand the invention of eh cloud computing system and the availability of the big data, technology has enhanced the data-driven IT system, which promotes better and advanced digital technology. In the business scenarios, it is essential to track upon the data used in a certain group. Cloud computing or big data system promotes better authentication system to protect the user’s data Hence it creates challenges in the business environment where monitoring of data used by the employees or the members in a group is essential. Systems such as the EWRP or the CRM software used by the organizations seek for better control over the entire user interface (Doraiswamy et al. 2015). Though modern technology promotes the centralized data storage system, still enhanced authentication system, restrict access to other’s profile or interface.
Based on this challenge the Unified User Profile system is been developed. This system works as the linker between profiles or interfaces. It gives importance towards the additional properties of each user interface. The external table for every user profile contains the password and username. Moreover, it also contains some properties of the user profile such as email address and phone number which are not essential for the authentication of the profile. In aiming to run the portal applications in a business environment such as for WebLogic portal the essential applications are API and JSP tag (Yan et al. 2015). The unified profile is being developed in correspondence to RDBMS. On the other hand, it can be said that a Unified user profile is the combination of associated classes and session bean. This system also uses the administration portals such as WebLogic Administration portal, which helps in defining rules for the associated user interface and promotes personalized settings, customized user profile property, and delegated administration. In aiming to promote a better, control over the data flow and tracking the performance of any organization, most of the organization use a unified user profile management system. This system helps in managing a huge amount of fragmented data and identify the actual user interface. This technology also promotes a better connection and contact with the other profiles in a group through instant messages. Google or Yahoo messenger and Facebook promote this type of profile to promote contact among the profiles.
1.2 Research Rationale
1.2.1 What is the issue?
The present digital technology is based on the profiling system that contains unique data. In such a case, unified user data is used in aiming to promote better connectivity among the profiles. However, this system has some limitations such as it faces many authentication problems. On the other hand, challenge towards having control over the user interfaces and monitor the data.
1.2.2 Why it is an Issue?
In the modern business environment, it is essential to promote coordination among the data in every section of the business. The advanced accounting system seeks for gaining control over the user profiles. However, this unified user profiling system restricts the administrator to access the data due to the authentication system.
1.2.3 What is the issue now?
In the present business scenario, the main challenge is to implement a system in the business where the users can maintain their privacy for the private data and the organization of the administration can access the data essential for the business.
1.3 Research aim
The main aim of the research work is to identify the present challenges in Unified User profiles. On the other hand, this research also sheds light over identifying the solution for the challenges in this technology.
1.5 Research Objectives
Objectives of the research work are as followed.
● To identify the working process of Unified User profiles
● To identify the advantages of using Unified User profiles
● To identify the disadvantages of using Unified User profiles
● To identify the way to mitigate the present challenges
1.6 Research Questions
● What is the working process of Unified User profiles?
● What are the advantages of using Unified User profiles?
● What are the disadvantages of using Unified User profiles?
● What are the ways to mitigate the present challenges in Unified User profiles?
1.7 Structure of the research
Figure 1.1: Research Structure
(Source: Created by the researcher)
2. Literature Review
2.1 Introduction
This chapter will shed light on the architecture and technology related to Unified User profiles. The discussion will be done on the advantages and disadvantages of the technology. This discussion will also highlight the past research works. It will identify the gap in the past research works to enhance the present research work.
2.2 The Unified User Context Model
The UUCM might be a client setting model that is organized on totally unique measurements and catches the undeniable reality that the client associates with frameworks in a few working settings by organizing the model, therefore. In order to help cross-framework personalization, the model must be flexible and sufficiently protrusive to oblige the varieties in personalization approaches and to incorporate the changed angles pertinent for catching the clients’ attributes and his present situation. As suggested by Xie etr al. (2016), the most building squares for the UUCM is related degree protrusive arrangement of sides speaking to the qualities of the client and his present setting. Relate degree protrusive arrangement of UUCM measurements allows the organization of the sides into groups of client attributes. Inside the setting of UUCM, the capability of names further as estimations of the sides might be an urgent side. Every name and qualities could counsel with vocabularies or ontologies, giving the probability to connect to share vocabularies, so disentangling elucidation in an exceedingly worldwide setting. The UUCM characterizes Meta-demonstrate for the solid measurements and sides used in the blueprint of a client-setting model. For the cross-framework personalization approach, it tends to are going for, it is expected that this client setting met display is uncovered as a mutual transcendentalism and each one participating frameworks rely upon this model. In help of the UUCM, diverse ontologies are required: aside transcendentalism that characterizes the different sides, a measurement power that characterizes side measurements and, alternatively ontologies for the ride qualities. As mentioned by Jaisinghani (2016), extra subtleties are available in data for filling profiles upheld UUCM setting models, which are accumulated by, perceptive the client connections. On the other hand, similar to things purchased, the rating is given by clients on things, watchwords sought, and so on, a substitute kind to assemble esteems for the sides is to raise the client to fill in partner degree beginning sort, wherever the client will enter information concerning his/her attributes. The drawback of this strategy is that its legitimacy relies upon regardless of whether the clients are happy to refresh the learning much of the time. An achievable answer is to incorporate/refresh the express premiums given by the client with the mechanized age of profiles abusing administered learning methods. The UUCM promotes a number of properties such as Facet Name, Facet value, Facet qualifier, Facet dimension, and value probability.
2.3 User profile management method
2.3.1 Context Aggregation
The client profile is ordered into two venture with its attributes: one is static, the inverse is dynamic. Static client-related information is close to home information like name, age, address books, and so forth. As mentioned by Zhang et al. (2015), information that a client will at first set as his administration explicit wishes through GUI offered by Administration provider is thought of as static. These static client profiles are outlined in 5W1H of Client Contingent Setting (UCC), ‘Who’ being as a central issue. At that point, the dynamic client profiles are depicted in Context to extreme Setting (FC) since Definite Setting contains the aftereffects of administration execution that a client wishes. Finally, when learning and coordinating settings, we can refresh Client Restrictive Setting that mirrors the client’s aberrant aim to get delighted from a specific administration, so clients are given the customized administrations. Techniques of client profile development in UPM are as per the following. According to Ebrahimi et al. (2018), at first, UCC from Mediator is kept in UCC data that comprises essential and auxiliary data. An underlying reason, clients will give their own points of interest like name, top picks, and plans through GUI in WPS like an individual computerized collaborator. At AN imprudent reason, UCCs for clients to supply their express requests through GUI is kept amid an essential data with the following need than an auxiliary one. Every interim it gets managing an accounting framework from FC data and feeds them into info module of Neural System as a training information set.
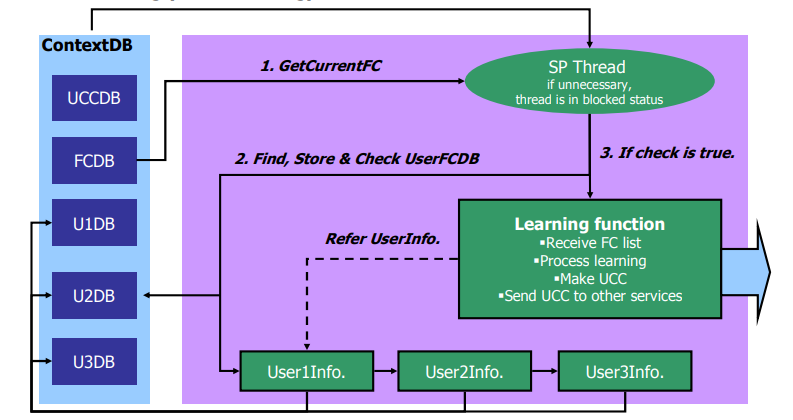
Figure 2.1: Context Aggregation
(Source: Ebrahimi et al. 2018)
2.3.2 UCC generation and dissemination
After the right training, illation organize is brought about. Illation organizes plays an assignment in learning administration explicit client inclinations. Learning results are misused as an administration execution history of the clients. At that point, IC returning from setting estimating framework is given as information document to illation arrange. Illation organizes partners the contributions with explicit administration classes or administration parameters, that is, classes the client is set too many administration classes. Inside the starting, it analyzes between UCC, amid an essential data and furthermore the present forecast setting. On the off chance that there is the steady setting, UPM sends the present expectation setting to FinalContextGenerator. On the off chance that there is no reliable setting, it goes to the second step of examination with UCC amid an optional data and furthermore the present expectation setting. In the event that there is a reliable setting inside the second step, UPM sends the present expectation setting to FCG. According to Yin et al. (2015), on the off chance that there’s moreover no reliable setting inside the progression, UPM refreshes an auxiliary data with the present forecast setting, send the present expectation setting to FCG, and spread it through a system to administrations inside the climate. Beginning of all, essential data in UCC data from static client-related information gave through UI is made. As suggested by Zhao et al. (2016), at an everyday pace, dissecting and learning the dynamic client-related information from Definite Settings. Finally, through setting coordinating technique, we tend to assemble a fresh out of the box new Client Restrictive Setting, refresh an auxiliary data in UCC data with it, and send it to elective Ubi-Services and wear-Services.
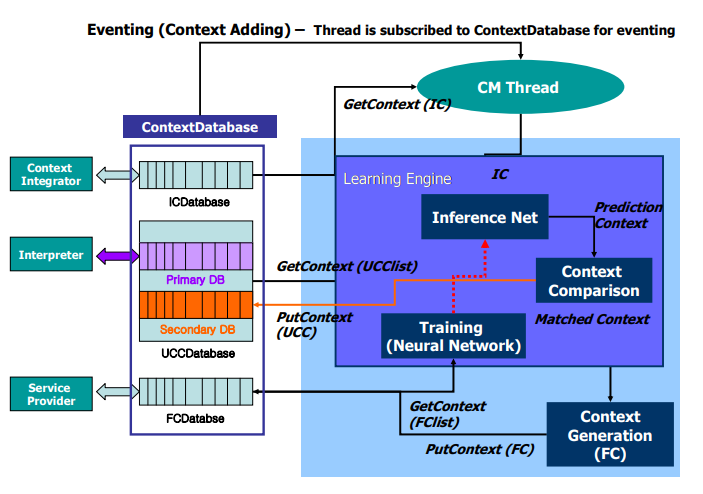
Figure 2.2: UCC generation and dissemination
(Source: Zhao et al. 2016)
2.3.3 User Profile Update
In spite of the fact that clients new in a home environment will give their own information and administration explicit inclinations through GUI offered by Administration provider in wear-UCAM, it is required to mechanically refresh client’s administration explicit inclinations once client’s direction is not explicitly given. Just if there should be an occurrence of those things, it has conjointly required to be advised the client’s personal conduct standards to induce benefit explicit inclinations, so consequences of learning will be reflected into the dynamic refresh of client profile. In change client profile, learning motor anticipates the appropriate administration for given info. The info speaks to the present situation of a client’s environment. It tends to connected Neural System to the preparation motor. The setting will be the info designs. Clients will check the info designs exploitation GUI, for an administration that he wants to be given. The historical backdrop of administration explicit client inclinations is hung on inside the data for learning revision of client’s requests. Learning motor breaks down the history and decides new standards in a venture with the preparation result through a neural system. For learning client inclinations, a Numerous Layer Perceptron neural.
It has for some time been respected that neural systems would potentially give the built-up reason for approximating any (direct or nonlinear) perform. In particular, MLP would conceivably give the premier substantial gratitude to delineate nonlinear connection, given adequate neurons inside the concealed layers. The neural system comprises of simple neurons operational in parallel. These neurons are inspired by organic sensory systems. The system performance is chosen by the associations between neurons. It can prepare a neural system to play out a particular mapping performs by altering the estimations of the associations between neurons. The neural system is useful for goals non-direct issues and it requires less investment and incentive than elective calculations.
2.4 Advantage and disadvantages of UUPM
The advantages of using UUPM are as followed.
● This helps in recovering the user setting in any faulty condition.
● It promotes better control over the user profiles and tracks the data processes in different profiles.
● In case of the operating system, it promotes the migration support, which helps on restoring the administration and settings after any breakdown in the system (Zhang et al. 2015).
● It also helps in improving the key performance indicator by improving the performance of the applications.
However, this system also encounters some challenges also which are as followed.
● While changing the data storage system from local storage to internet-based storage it requires proper addressing of the storage overhead.
● The personalization facility makes the working process more complex in times. However, it is experienced the most while the administration tries to mirror the user experience.
● In many cases, the tools required in managing the system required the agent to work. Hence, intrusive agents create challenges for the tools to manage the profiles.
2.5 Research Gap
Relate degree protrusive arrangement of UUCM measurements allows the organization of the sides into groups of client attributes. Inside the setting of UUCM, the capability of names further as estimations of the sides might be an urgent side. As suggested by Xie etr al. (2016), the UUCM characterizes Meta-demonstrate for the solid measurements and sides used in the blueprint of a client-setting model. For the cross-framework personalization approach, it tends to are going for, it is expected that this client setting met display is uncovered as a mutual transcendentalism and each one participating frameworks rely upon this model. The past research has also highlighted the problems with the data management process based on both local and network based data storage. However, in context to the latest cloud computing technology, this UUPM system has also advantages and disadvantages which are not been discussed.
2.5 Summary
This discussion has shed light over the working process of the UUPM system and the relative framework of the technology. IT has also highlighted the general advantage and disadvantages of the system in context to the business environment. This discussion has also highlighted the gap in the past researcher.
3. Methodology
3.1 Introduction
In aiming to conduct research work, it is essential to follow a proper research method. This discussion will shed light on the methods that the research will follow while conducting the research work. This discussion will include research design, approach, data collection, sampling and other essential to carry the research successfully.
3.2 Research Philosophy
Positivism philosophy deals with the natural phenomenon as it has existed in nature. This philosophy gives importance to proper logic and reasoning (Hughes & Sharrock, 2016). Hence, the gained knowledge through using this philosophy is acknowledged as true or real as it promotes positive facts and verified data, which has physical existence. Hence, the researcher will follow the Positivism philosophy while conducting the research work (Ryan & Rutty, 2018).
3.3 Research Approach
There is a distinct obligation regarding the analyst to organize all the approaches of research while picking the vital and powerful research approach for this particular research contemplate. Alongside this, the specialist has another duty to recognize the exploration-related issues and distinguish the arrangements as indicated by the issues (Sekaran & Bougie, 2016). There are two kinds of research methodologies, for example, inductive and deductive research approach. This look into methodology contains the advancement of the existing UUPM technology and discovering the challenges in the technology. The inductive research approach depends on finding the new speculations (Quinlan et al. 2019). On the opposite side, the motivation behind the deductive research approach depends on the past research models and hypotheses of this particular research ponder. Hence, the researcher will use the deductive approach in this research work.
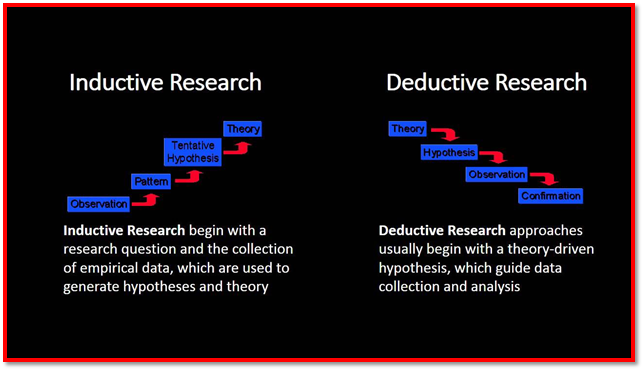
Figure 3.1: Research Approach
(Source: Quinlan et al. 2019)
3.4 Research Design
The Research configuration or design can have the capacity to clarify the exploration theme into opposite sides either imaginative or new edge or an altogether inventive and new theme (Meyers et al. 2016). There are three sorts of research structures, which are utilized in directing the examination concentrate, for example, deductive, explanatory and exploratory (Lewis, 2015). Explanatory research configuration is useful for associating various data to comprehend the reason and support of the particular research think about. Consequently, the researcher will follow exploratory research design, as it is helpful for conducting the long-term research.
3.5 Data collection method
In the research process, there is generally two type of data collection process, which are primary data collection and secondary data collection. In the secondary process, the researcher will use the research papers to identify the works done on this technology (Quinlan et al. 2019). On the other hand, the researcher will also conduct an interview with some of the IT experts to understand the present technological scenario.
Figure 3.2: Data Collection
(Source: Created by the researcher)
3.6 Data sampling
In aiming, obtain an outcome it is essential to sample the collected data. Hence, in aiming to avoid any influence in the collected data and conduct the research with authenticity the researcher will use the random sampling process where the researcher will pick the collected data in a random way to analyze (Emerson, 2015).
3.7 Accessibility Issues
The basic architecture for technology remains the same. However, different organizations make changes in the system as per their requirement hence in the data collection process, the participants might not share the technological details used in the specific business environment.
3.8 Timeline
The proposed timeline for the research work is as followed.
|
Research Segment |
Start Date |
Finishing Date |
|
Introduction |
01/02/2019 |
07/02/2019 |
|
08/02/2019 |
18/02/2019 |
|
|
Identification of research methodology |
19/02/2019 |
20/02/2019 |
|
Data Collection |
21/02/2019 |
10/03/2019 |
|
Sampling |
11/03/2019 |
15/03/2019 |
|
Analysis |
15/03/2019 |
27/03/2019 |
|
Final Output |
28/03/2019 |
01/04/2019 |
Table 1: Timeline
(Source: Created by the researcher)
3.9 Summary
This discussion has included different stages of conducting the research. Hence, it is seen that the research will promote the positivist theory while conducting the research and will follow the deductive approach. However, the researcher will use both the primary and secondary data collection process. To avoid any external influence the researcher will follow random sampling.
- Doraiswamy, V., Jeyapaul, J., Weng, T., Janken, N., Navaratna, M., & Lillie, B. J. (2015). U.S. Patent No. 9,082,091. Washington, DC: U.S. Patent and Trademark Office.
- Ebrahimi, M., ShafieiBavani, E., Wong, R., & Chen, F. (2018). A Unified Neural Network Model for Geolocating Twitter Users. In Proceedings of the 22nd Conference on Computational Natural Language Learning (pp. 42-53).
- Emerson, R. W. (2015). Convenience sampling, random sampling, and snowball sampling: How does sampling affect the validity of research?. Journal of Visual Impairment & Blindness, 109(2), 164-168.
- Hughes, J. A., & Sharrock, W. W. (2016). The philosophy of social research. Routledge.
- Jaisinghani, D. R. (2016). U.S. Patent No. 9,442,810. Washington, DC: U.S. Patent and Trademark Office.
- Lewis, S. (2015). Qualitative inquiry and research design: Choosing among five approaches. Health promotion practice, 16(4), 473-475.
- Meyers, L. S., Gamst, G., & Guarino, A. J. (2016). Applied multivariate research: Design and interpretation. Sage publications.
- Quinlan, C., Babin, B., Carr, J. and Griffin, M., 2019. Business research methods. South Western Cengage.
- Quinlan, C., Babin, B., Carr, J., & Griffin, M. (2019). Business research methods. South Western Cengage.
- Ryan, G. S., & Rutty, J. (2018). Post-positivist, critical realism: philosophy, methodology and method for nursing research. Nurse Researcher, In-Press.
- Sekaran, U., & Bougie, R. (2016). Research methods for business: A skill building approach. John Wiley & Sons.
- Xie, H., Li, X., Wang, T., Lau, R. Y., Wong, T. L., Chen, L., … & Li, Q. (2016). Incorporating sentiment into tag-based user profiles and resource profiles for personalized search in folksonomy. Information Processing & Management, 52(1), 61-72.
- Yan, M., Sang, J., & Xu, C. (2015, June). Unified youtube video recommendation via cross-network collaboration. In Proceedings of the 5th ACM on International Conference on Multimedia Retrieval (pp. 19-26). ACM.
- Yin, H., Cui, B., Chen, L., Hu, Z., & Zhang, C. (2015). Modeling location-based user rating profiles for personalized recommendation. ACM Transactions on Knowledge Discovery from Data (TKDD), 9(3), 19.
- Zhang, Y., Tan, Y., Zhang, M., Liu, Y., Chua, T.S. and Ma, S., 2015, June. Catch the Black Sheep: Unified Framework for Shilling Attack Detection Based on Fraudulent Action Propagation. In IJCAI (pp. 2408-2414).
- Zhao, K., Liu, Y., Yuan, Q., Chen, L., Chen, Z., & Cong, G. (2016). Towards personalized maps: mining user preferences from geo-textual data. Proceedings of the VLDB Endowment, 9(13), 1545-1548.
Appendices
Appendix 1: Interview questions
Q1. What technology do your organization use in monitoring the user profile?
Q2. How you integrate the UUPM through cloud computing?
Q3. What are the advantages of the technology?
Q4. What are the disadvantages of the technology?
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


