Influence of Stakeholders Partnership Frameworks on Combating Cybercrimes
| ✅ Paper Type: Free Essay | ✅ Subject: Law |
| ✅ Wordcount: 3563 words | ✅ Published: 23 Sep 2019 |
AN INVESTIGATION OF THE INFLUENCE OF STAKEHOLDERS PARTNERSHIP FRAMEWORKS ON COMBATING CYBERCRIMES IN KIGALI CITY, RWANDA
DCU: Digital Crimes Unit
ITU: International Telecommunication Unit
NCSA: National Cyber Security Authority
Rw-CSIRT: Rwanda Computer Security and Incident Response Team
CHAPTER ONE: INTRODUCTION
1.1.Introduction
This chapter covers the general aspects of the study namely the background to the study, statement of the problem, purpose of the study, research objectives, research questions, rationale of the study, significance of the study, scope of the study, limitations of the study, delimitation of the study, assumption of the study and the operational definition of terms.
1.2.Background and Context for the Problem
The introduction of internet in late 1960’s – an open network that nobody controls- and the web in 1990’s with subsequent digitalisation and automation of most of vital services transformed the world and allowed many conveniences in the daily lives of all the categories of the population as key enabler for their social and economic development (Wight, 2015; International Telecommunication Unit [ITU], 2017)). One can easily access his/her account and withdraw or transfer money without any need to go to the bank, apply for a job, do business online, order and pay for electricity and many other services, to name but a few. However, the easy accessibility and use of electronic technologies have also exposed the same population to the biggest threat of cybercrimes which increases in frequency, volume, sophistication and knows no borders. Cybercrimes have become a challenge for both the States, business communities, financial institutions as well as the individual citizens given their implications on the national security, economy, critical infrastructures, human rights, civil liberties and international legal frameworks (Carr, 2016). One cannot overemphasise the damaging effects of emerging cyber criminality including but not limited to bank and credit card fraud, extortion, child pornography and other types of crime related to terrorism, hate crimes, appeals for violence as well as crimes directly related to the cyber world and internet which cannot be executed outside the cyber sphere such as hacking, ransomware attacks, phishing, cyber bulling, misuse of devices, to name but a few.
The global threat of cybercrimes is so concerning to such extent that 12 people online become victim every second, totalling more than 1 million victims around the globe every day while the Malware costs $3 trillion loss to the global economy each year as stated in the Microsoft Digital Crimes Unit [DCU] Facts Sheet (2017). According to Norton Cyber Security Insights Report Global Results (Cymantec, 2017), 978 million people in 20 countries have been affected by cybercrime in the course of that year resulting into the loss of $172 billion for the consumers– an average of $142 per victim.
In response to this growing threat, most States’ policy frameworks and practices have subscribed to the beliefs formed since Westphalia treaties of 1648 on state sovereignty which give to the State the exclusive power and responsibility to respond to all security threats occurring on the territory under its jurisdiction. This understanding has led some states to believe that they can deal with all security threats including cybercrimes with little or no involvement of stakeholders. However, the scale, the dynamic nature and risks that cybercrimes present to both State and non-State actors including individuals make it apparent that it is increasingly difficult to ignore the role of private stakeholders in developing common initiatives and measures that enable effective combating of cybercrimes on a national, regional and global level (World Economic Forum, 2016; Carr, 2016).
The overriding importance of stakeholders’ partnership in ensuring cyber-security has also been underscored in the United Kingdom (UK) National Cyber Security Strategy (2016-2021) which recognises that the government alone cannot provide all aspects of the nation’s cyber security and that an embedded and sustainable approach is needed where citizens, industry and other partners in society and government, play their full part in securing the county networks, services and data. Garland cited in (MICHAEL & MATTHEW, 2013:2) argues that “this recognition of the limits of policing and of other state agencies promotes governing strategies that rely on ‘responsibilising’ private actors and civil society to govern their own spaces in crime and disorder reduction efforts”. The two scholars are of the view that this applies as well to the domain of cybercrime and cybersecurity because the challenge posed by cybercrime cannot be met by the police alone and the expertise required must be brought in from outside the police.
The need for developing stakeholders’ partnership for enhancement of cybersecurity was reemphasised by many other scholars based on different countries’ contexts. In the United States of America’s (USA) context, it was contended that prevention and detection of cybercrimes as well as the decrease in response time to real threat and crimes require instantaneous response from multiple entities within both the public and private sectors (Rogers, 2016).
This idea that the government needs enhance its collaboration with stakeholders in combating cybercrimes is also echoed by Bonna (2016), the founder and the chief executive officer of DarkMatter in Dubai, United Arab Emirates, a company involved in provision of cybersecurity protection services. He argues that the model of government as regulator and companies as regulated is not sustainable in the realm of cyber security. For him, though Public-Private Partnership (PPP) is not a panacea, it is a compelling way to respond effectively. This position is not far from one of the recommendations of the Global Multistakeholder Meeting on the Future of Internet Governance held in Sao Paulo from 23- 24 April 2014 which suggests that the achievement of the satisfactory level of internet security requires the involvement and cooperation of several stakeholders in any cybersecurity initiative beyond the efforts of a single organization or structure (Hoepers, Steding-Jessen, & Faulhaber, 2014).
In Africa, the Africa Cyber Security Report 2016 (Musuva-Kigen, et al., 2016) shows that African countries lost at least $2 billion in cyber-attacks in that year. By the time of the report, the estimated cost of cybercrime was $550 million in Nigeria, $175 million in Kenya, $85 million in Tanzania, $50 million in Ghana and $35 million in Uganda. Most organisations in Africa are ill-prepared to deal with information security threats due to the lack of enough budgets, lack of skilled professionals and lack of visibility within the organisation. Therefore, Djossou (2016) is of the view that African public-private partnership is key to strengthen cyber resilience. The same view is held in the report of African Union Commission (2016) and by SHAW (2018)
In Rwanda, despite a series of measures put in place by the government to fight cyber criminality such as the establishment of National Cyber Security Policy (Government of Rwanda [GOR], 2015); the National Cyber Security Authority (NCSA) in 2017; a specialized department in charge of digital forensics in the Rwanda National Police; enactment of the new law on the prevention and punishment of cybercrimes (Primature, 2018); the Rwanda Computer Security and Incident Response Team (Rw-CSIRT) with the primary mandate to prevent and respond to cyber security incidents in public and private cyberspace and raise awareness for the general public; installation of cybersecurity system; to name just a few, the ever-escalating cyber-attacks are still a threat to the national security, economy and daily social life of citizens in Rwanda and especially in Kigali City.
In 2014 for example $516,397 meant to cover tuition for 14 Rwandan students in Nigeria were transferred by the Rwanda central bank and was diverted to another account in Spain (Times, 2016) while in 2015, it was reported that Cyber attackers tried 25 million times to steal money from the Central Bank (BNR in official French abbreviation) but were unsuccessful (Sabiiti, 2018). In 2016, Rwanda prevented more than 1,000 cyber-attacks daily before they could affect targeted individuals, companies and institutions. The Criminal Investigation Department recorded 73 cybercrime cases involving Rwf1.3 billion and €340,000 (CID, 2016). In 2017, at least eight million cyber-attackers have attempted to hack into Rwanda’s financial institutions including the Central Bank in several occasions and managed to enter into one of the systems stealing Rwf900million. The cases recorded by former Criminal Investigation Department (CID) increased to 78 and the stolen money raised to Rwf2.612,101,816 and $605,028 (CID, 2017; Iradukunda, 2018) though 95% of the money involved in 2016 and 2017 was recovered. The police also intercepted a cyber-attack targeting to steal $700,000 (Rwf 574 million) and the heist was repelled before accomplishing their mission (Igihe, 2017). In the same year, the cyber thieves attempted to walk away with Rwf2billion and $ 605,028 in vain (Sabiiti, 2018). As of now, a case involving 13 persons is pending before Nyarugenge Intermediate Court over hacking Access Bank (The New Times, 2018).
The most common cybercrimes committed in Rwanda include but not limited to ATM fraud, mobile money fraud, bank frauds mostly committed by hackers with complicity of insider staff, bogus financial proposals to mobile telephone subscribers being hoodwinked for winning a certain amount of money, e-mail hacks, using stolen IDs to register sim-cards, to name but a few.
It is believed that some of these threats could be prevented through effective cooperation and timely information sharing, joint strategy to protect critical infrastructure, awareness on cybercrime, establishment of guiding operational policies and procedures, regular compliance review, systems monitoring, capacity building and basic security hygiene among others (Rwangombwa, 2018). However, there is little evidence of the existence of such sought stakeholders’ partnerships in addressing the threat of cybercrimes. This study is undertaken to fill this gap through an investigation of the influence of stakeholders’ partnership frameworks on combating cybercrimes in Kigali City, Rwanda.
- Statement of the Problem
The digitalisation and automation of most of vital services delivered by government institutions, private companies, civil society organisations and individuals contributed to the well-being of citizens, but they also exposed the government institutions, public and private companies, normal citizens to the threats of cyber vulnerabilities. In response to these threats, governments and companies have taken several measures to protect themselves and it is the Rwandan Government’s belief that to be successful in cyber security, the Government should collaborate with the private sector (Cymantec, 2016: 85).
In real sense, the collaboration and partnership between the government and private sector would mean the existence of framework for coordination of efforts to protect critical infrastructure, exchange of information, participation in joint strategies and building capacity of private sector to deal with threats of cyber-attacks. In Rwanda, while the government has established policies, frameworks and institutions to ensure such a coordination and partnership, it has been observed that this partnership between public and private sector remains a topic for study. Some of the predicted leading causes are the fear of collateral consequences of involving the government in cyber incident response, confidence that they will handle the threats on their own (Germano, 2014:2), fragile private companies’ cybersecurity systems, reluctance to communicate cyber-attacks for fear of reputation, and ineffective multi-sectoral partnerships in combating cybercrimes.
Recent developments in the field of governance in general and law enforcement in particular, have led to compelling need to resort to stakeholders’ partnerships as an effective tool to prevent crimes and it is assumed that combating cybercrimes should not escape from such arrangements as no single institution acting alone has the capacity to deal with them (MICHAEL & MATTHEW, 2013; Germano, 2014). However, despite the stringent measures taken by the government including prosecution and punishment of cybercrimes, there is increasing concern that too little attention has been paid to multi-sectoral partnership as a tool to combat cybercrimes.
Ideally, the magnitude of the threat posed by cybercrimes would have required a combined effort of a government and private actors through a structured framework. This partnership would contribute to the effective prevention of cybercrimes through joint strategy, cooperation and timely information sharing, coordination of activities, common operational policies and procedures, adoption of cyber security protection policy, regular compliance review, promotion of security awareness, systems monitoring, capacity building, and basic cyber security hygiene. This identified gap in bringing together efforts of the public and the private sector have led to the vulnerability of Rwandan Cyberspace whereby the cost of cyber criminality has been enormous especially for the private sector and normal citizens who are exposed to financial fraud, mobile money fraud and other cybercrimes. The purpose of this study is therefore to investigate the influence of stakeholders’ partnership frameworks on combating cybercrimes in Kigali City, Rwanda.
- Relation of the Problem to the Specialization
Some of the key responsibilities of enforcement agencies are to ensure compliance with the law, maintaining public order inside the country and ensuring safety and security of the people and their property. To accomplish these responsibilities, law enforcement institutions have to work in harmonious collaboration with the community (Police Act, 2010). Combating cybercrimes crimes falls within the mandate of law enforcement agencies as they threaten the security of persons and their properties. Nurturing effective partnership between stakeholders is a major concern of law enforcements agencies for the successful accomplishment of their mission. Thus, this study fits well within the area of law enforcement and justice administration.
- Purpose of the study
The purpose of this study is to investigate the influence of stakeholders’ partnership frameworks on combating cybercrimes in Kigali City, Rwanda.
- Research Objectives
(i) To establish the influence of joint partnership strategies on combating cybercrimes in Kigali City, Rwanda.
(ii) To examine the influence of stakeholders’ mapping on combating cybercrimes in Kigali City, Rwanda.
(iii) To determine the influence of stakeholders’ participation on combating cybercrimes in Kigali City, Rwanda.
(iv) Find out the influence of stakeholders’ coordination on combating cybercrimes in Kigali City, Rwanda.
(v) To ascertain the influence of stakeholders’ communication on combating cybercrimes in Kigali City, Rwanda
- Research Questions
This study will attempt answer the following research questions:
(i) What is the influence of joint partnership strategy on combating cybercrimes in Kigali City, Rwanda?
(ii) To what extent does the stakeholders’ mapping influence combating cybercrimes in Kigali City, Rwanda?
(iii) How does stakeholders’ participation influence combating cybercrimes in Kigali City, Rwanda?
(iv) What is the influence of stakeholders’ coordination on combating cybercrimes in Kigali, Rwanda?
(v) To what extent does stakeholders’ communication influence combating cybercrimes in Kigali City, Rwanda?
- Significance of the Study
The findings of this study is likely to benefit Public institutions that are mandated to make policies on cyber security, provide Information Communication Technology services, prevent, investigate, prosecute and punish cybercrimes. These public institutions are respectively the Ministry having ICT in its merits (MINICT), Rwanda Information Society Authority (RISA), Rwanda Development Board, the recently established National Cybersecurity Authority (NCSA), Rwanda National Police, Rwanda Investigation Bureau (RIB), the Public prosecution and Courts. On the other hand, this study will be specifically of paramount importance for financial institutions mainly the Central Bank, other banks and SACCOs, telecommunication companies, etc. who are the most affected by the cybercrimes through frauds. This study would also benefit Rwanda Utility Regulation Authority (RURA) whose mandate is the regulation of public utilities to ensure that they deliver to the expectations.
The findings will help each of the above institutions understand their responsibilities and the need for developing common strategies, timely sharing information and knowledge for combating cybercrimes but also to review their safety measures towards the prevention of cyber- attacks. Finally, the finding of this study will add value to the existing body of knowledge in the area of law enforcement.
- Topics in the Literature Review
8.0. Introduction
8.1. Stakeholders’ partnership
8.2. Combating cybercrimes
8.3. Influence of joint partnership strategies on combating cybercrimes
8.4. Influence of Stakeholders’ mapping on combating cybercrimes
8.5. Influence of stakeholders’ participation on combating cybercrimes
8.6. Influence of stakeholders’ coordination on combating cybercrimes
8.7. Influence of stakeholders’ communication on combating cybercrimes
- Theoretical framework
This study is anchored by the theory of cooperation and competition on one hand, and on the other hand, the crime opportunity theories. The cooperation theory was formulated by Deutsch in 1949 and suggests that persons perceive their goals attainment as positively related and that one’s movement towards one’s goal facilitates others’ goals (Dean, 1984). Those involved in cooperation have interdependent goals such that they have to communicate, influence and exchange resources as they strive to complete the common task. Thus, each institution be it public or private associated with the efforts to combat cybercrimes cannot achieve its goals without depending on the partnership with other institutions with the same aspirations.
As for the crime Opportunity theories (routine activity, crime pattern and rational choice theory), their main tenet is that offenders make rational choices and thus choose targets that offer a high reward with little effort and risk (Hindelang, Gottfredson, and Garofalo, 1978; Cohen and Felson, 1979; Cohen, Felson, and Land, 1980). This means that opportunities play a role in causing all crime and crime can be prevented by reducing opportunities (Felson and Clarke, 1998). Applied to the current study, this would mean that cyber criminals become successful because there are no effective mechanisms to minimise the opportunity for them to victimise and benefit from the crime.
- Conceptual framework
- The trend and magnitude of cybercrimes and its destructive nature on different field of
STAKEHOLDERSPARTNERSHIP FRAMEWORKS
Joint partnership strategies
- Critical infrastructure protection
- Network Security
- Incidents management
- understanding the threat
- Strengthening cyber security skills
COMBATING CYBERCRIMES
Detection
Dater
Disruption
Investigation
Punishment

Stakeholders’ mapping
- Stakeholders identification
- Stakeholders mapping
- Stakeholders integration
- Risks prioritisation





Participation
- Law and policy development
- Policy implementation
- Active cyber defense
- Awareness programmes
 Dependent variable
Dependent variable
Globalisation
Constant evolvement of technology
Unharmonised and fragmented legislation
Competing domestic and foreign policy
Coordination
- Liaison
- Mobilisation
- Research and documentation
- Monitoring and evaluation

Communication
- Timely information-sharing
- Knowledge sharing
- Mutual trust and open dialogue
- Effort harmonization
 Intervening variables
Intervening variables
Independent variable
- Research Methodology
This study will use a mixed method with concurrent quantitative and qualitative approaches. The quantitative approach will be used to measure some numerical indicators. Its aim is to explain how one variable affects another (Cresswell, 2011). On the other hand, qualitative approach will be used to explore attributes data to explain the problem under study (Cresswell, 2011). In this study, it will be used to explore some attributes aspects such as trust, awareness, reasons, opinions and perceptions of the stakeholders.
- Research design
This study will use concurrent triangulation design. In this single-phase design the researcher will attempt to merge the two data sets, typically by bringing the separate results together in the interpretation or by transforming data to facilitate integrating the two data types during the analysis (Creswell, 2006). This design will give equal priority to both quantitative and qualitative data with a view to compare and more accurately illustrate how the stakeholders’ partnerships influence combating cybercrimes. The table below illustrate the concurrent triangulation design.
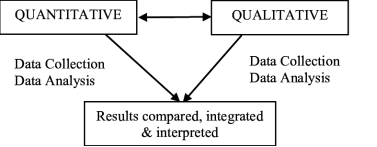
Source: The triangulation mixed methods design (Creswell & Clark, 2007)
- Data Collection instruments
As a mixed research, this study will use questionnaires as a quantitative data collection instrument and in-depth interview schedule, focus group and observation as qualitative data collection instruments.
- Data Analysis
Given the fact that some of the indicators of variables are numeric and others are attributes and based on the functionality, this study will use descriptive and inferential statistics analysis for quantitative data and thematic analysis for qualitative analysis.
- References
- Bannai, F. (2018). A rallying call for public private partnerships in the cyber security domain.Retrieved fromhttps://darkmatter.ae/rallying-call-public-private-partnerships-cyber-security-domain/.
- Beetham, D. (1996). Bureaucracy. 2nd edition. Buckingham: Open University Press
- CARR, M. (2016). Public–private partnerships in national cyber-security strategies. International Affairs. The Royal Institute of International Affairs. John Wiley & Sons Ltd, Malden, MA 02148, USA.
- Cohen, L.E. and Marcus, F. (1979). Social Change and Crime Rate Trends: A Routine Activity Approach. American Sociological Review 44: 588-608. Retrieved from http://www.personal.psu.edu/exs44/597b-Comm&Crime/Cohen_FelsonRoutine-Activities.pdf.
- Cohen, L.E., Marcus F., Land, K. (1980). Property Crime Rates in the United States: A Macrodynamic Analysis, 1947-1977; with ex ante forecasts for the 1980’s. American Journal of Sociology. 86: 90–118.
- Cresswell J.W. (2011). Educational Research: Planning, Conducting, and Evaluating Quantitative and Qualitative Research. Pearson. Boston Columbus.
- Germano, H.J. (2014). Cybersecurity Partnerships: A New Era of Public-Private Collaboration. The Center on Law and Security. New York University School of Law.
- Government of Rwanda (2015). National Cyber Security Policy.
- Hindelang, M., Gottfredson, M. & Garofalo, J. (1978). Victims of personal crime: An empirical foundation for a theory of personal victimization. Cambridge, Mass.: Ballinger.
- Hoepers, C., Steding, J.K, Faulhaber, H. (2014). The Importance of a Multistakeholder Approach to Cybersecurity Effectiveness. Retrieved from http://content.netmundial.br/contribution/the-importance-of-a-multistakeholder-approach-to-cybersecurity-effectiveness/180
- Hoepers, C., Steding-Jessen, K., Faulhaber, H. (2014). The Importance of a multistakeholder Approach to Cybersecurity Effectiveness, ‘Global Multistakeholder Meeting on the Future of Internet Governance. Sao Paulo, May 20th, 2014. NETmundial. Retrieved from http://content.netmundial.br/contribution/the-importance-of-a-multistakeholder-approach-to-cybersecurity-effectiveness/180.
- JOKE, R. (2016). Public-Private Partnerships: A tool for enhancing cybersecurity. Thesis for the degree of Master of Arts in Global Security Studies Johns Hopkins University. Baltimore, Maryland.
- Kim, B. (2005). Internationalising the Internet the Co-evolution of Influence and Technology. Edward Elgar. pp. 51–55.
- Musuva-Kigen, P., Ekpeke M., Inkoom, E., Inkoom, B., Masesa, D., Kaimba, B. …. Mbae, K. (2016). AFRICA CYBER SECURITY REPORT. Retrieved from http://www.serianu.com/downloads/AfricaCyberSecurityReport2016.pdf.
- Myungsuk, L. (2003). Conceptualizing the New Governance: A New Institution of Social Coordination. Presented at the Institutional Analysis and Development Mini-Conference, May 3rd and 5th, 2003. Workshop in Political Theory and Policy Analysis. Indiana University. Bloomington. Indiana. USA.
- NKUSI, K.F. (2017). Creating the National Cyber Security Authority is vital. The New Times, of 1 May 2017. Retrieved from http://www.newtimes.co.rw/section/read/211603
- Pierre, J. (1999). Models of Urban Governance: The Institutional Dimension of Urban Politics. Williams, D. (2001). Urban Affairs Review. 34(3): 372-396.
- Sabiiti, D. (2018). How Rwanda Stopped Eight Million Cyber Attackers. KT Press, Retrieved from http://ktpress.rw/2018/01/how-rwanda-stopped-eight-million-cyber-attackers/
- SHAW, M. (2018). Unknowns: the threat of cybercrime in Africa. Institute for security studies. Retrieved from https://issafrica.org/iss-today/known-unknowns-the-threat-of-cybercrime-in-africa.
- Stoker, G. (1998). Governance as Theory: Five Propositions. International Social Science Journal. 50(1): 17-28
- World Economic Forum (2016). Recommendations for Public-Private Partnership against Cybercrime. Retrieved from http://www3.weforum.org/docs/WEF_Cybercrime_Principles.pdf
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


