Vigenère Cipher C Program
| ✅ Paper Type: Free Essay | ✅ Subject: Information Technology |
| ✅ Wordcount: 920 words | ✅ Published: 15 Sep 2017 |
Write a C program to implement a Vigenère cipher. You may use whatever IDE you wish but the program must be compile with the standard gcc compiler. Your program should give the user the option to either encrypt or decrypt a message. The user should be prompted to enter the passphrase to be entered and the keyword to be used in the cipher. The output should be text printed to stdout. Comments should be used to explain the rationale behind the design of your code. You must also provide a critical analysis as to the robustness of the Vigenère cipher and provide a recommendation as to whether or not it would be it would be sufficient for use in communications between colleagues within a non-technical environment.
C Programme
/*——————— Vigener Ciper———————————–*/
/*—This is the program to Encrypt and to Decrypt the text using the Vigener ciper method—*/
/*— User has to choose the option either to Encrypt or to Decrypt ——*/
/*—The user has to enter the text to be Encrypted and the Key to———*/
/*—The user has to enter the Encrypted Text and Key to Decrypt the text—*/
#include
#include
main()
{
int select;// variable declairation
int i,j;
char passphrase[256]; char keyword[33];
int value;
while(1)// infinite loop
{
printf(“n1.Encrypt n”);// Display options for the user
printf(“2.Decryptn”);// Encrypt or Decrypt
scanf(“%d”,&select);// read the option selected
if (select == 1)
{
printf(“Please Enter Message to be encryptedn”);//text to be encrypted
scanf(“%s”,&passphrase);
printf(“Please Enter keywordn”); // key word
scanf(“%s”,&keyword);
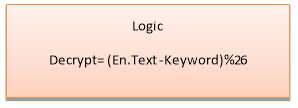
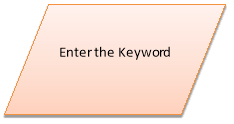
for(i=0,j=0;i { if(j>=strlen(keyword))// repeat the key word { j=0; } value = (((passphrase[i])-97)+((keyword[j])-97)); //logic (passphrase+key)%26 printf(“%c”, 97+ (value %26)); // display Encrypted text } } else if (select == 2) { printf(“Please Enter Encrypted Message to be Decryptedn”); //text to be decrypted scanf(“%s”,&passphrase); printf(“Please Enter keyn”);//key scanf(“%s”,&keyword); for(i=0,j=0;i { if(j>=strlen(keyword)) { j=0;// repeate the key } value = ((passphrase[i])-96)-(keyword[j]-96); //logic (passphrase-key)%26 if( value < 0) { value = value * -1; //make the value positive } printf(“%c”,97 + (value % 26)); // display dencrypted message } } else printf(“Please Choose a correct optionn”); } } Introduction The c-program gives the user to choose either to encrypt or to decrypt a message. The user will be prompted to enter the passphrase to be entered and the keyword to be used in the cipher. Vigenere cipher is a form of polyalphabetic substitution cipher which is used for encrypting a plain text. Vigenere cipher can be explained by Caesar cipher method of encryption. In a Caesar cipher encryption method, every letter of the plain text is shifted to some number of places where as in vigenere cipher every letter is shifted with different shift values. Method of Encrypting and Decrypting The logic to obtain the cipher text by vigener cipher is by modular addition of plaintext and repeating keyword. The formula for the encryption is as follows C(i) = T(i) + K(i) (mod 26) C(i) – i-th letter of the cipher text T(i) – i- th letter of the plain text K(i) – i-th letter of keyword (Key word will be repeated at its end) Similarly, the logic to decrypt the message is by modular subtraction of Encrypted text and keyword The formula for the decryption is T(i) = C(i) – K(i) (mod 26) C(i) – i-th letter of the cipher text T(i) – i- th letter of the plain text K(i) – i-th letter of keyword (Key word will be repeated at its end) The flow of the c- program is explained by the bellow flowchart Flow chart for the C-program Robustness of the vigenere cipher When the Vigener cipher was first invented and came into use, it was difficult to break as it uses 26 different cipher alphabet. Vigenere cipher is a polyalphabetic cipher and these kinds of ciphers are difficult to decipher because of their resistance to letter frequency analysis and the same text will not be encrypted with same key each time. In the year 1854 a British cryptographer Charles Babbage found the method to decipher the message. The above example illustrates how the vigener cipher can be cracked. The plain text used in this is “maths is short for mathematics” and keyword used is “key”. Since the plain text contains the word “math” twice, cipher text also contains the same encrypted text “WERR” twice with 15 letters apart. Now it can be guessed that keyword must be a factor of 15. 1,3,5,15 are the factors, if it is 1 then it is simple caesar cipher , key word can’t be of 15 letter in this case, between 3 and 5 it can be found easily by closely analyzing the ciphertext. Recommendation Considering the colleges within the non-technical environment Vigenere cipher can be recommended because, Conclusion Vigener cipher is implemented by using the c-program and the flow of the program is explained with the help of flow chart. Vigener cipher is critically analyzed and its robustness is explained. Recommendations are made on use of this method for the communication between colleges in non-technical environment. Reference http://crypto.interactive-maths.com/kasiski-analysis-breaking-the-code.html
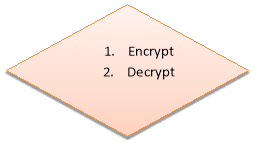


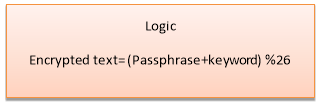
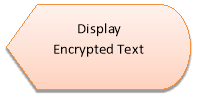
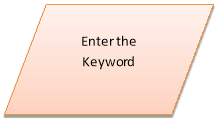
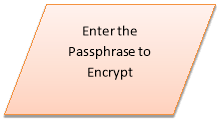
 1. Encryption
1. Encryption
Flow chart for Decryption Function




Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


