ISP Network Potential Threats
| ✅ Paper Type: Free Essay | ✅ Subject: Information Technology |
| ✅ Wordcount: 2840 words | ✅ Published: 06 Sep 2017 |
Threat Identification
A danger is an event which could take benefit of the vulnerability and make a terrible effect at the ISP network. potential threats to the ISP network need to be diagnosed, and the associated vulnerabilities need to be addressed to reduce the danger of the threat.
Trends Driving Network Security
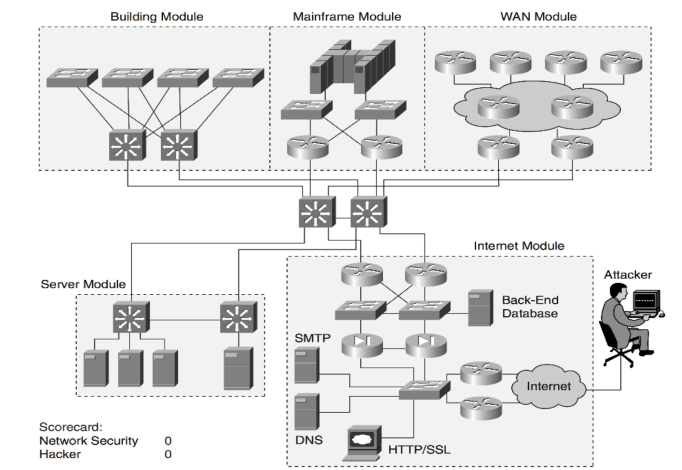
As in any rapid-growing enterprise, modifications are to be predicted. The varieties of capability threats to network protection are usually evolving. If the security of the network is compromised, there may be extreme effects, like lack of privateness, stealing of information, and even legal potential.
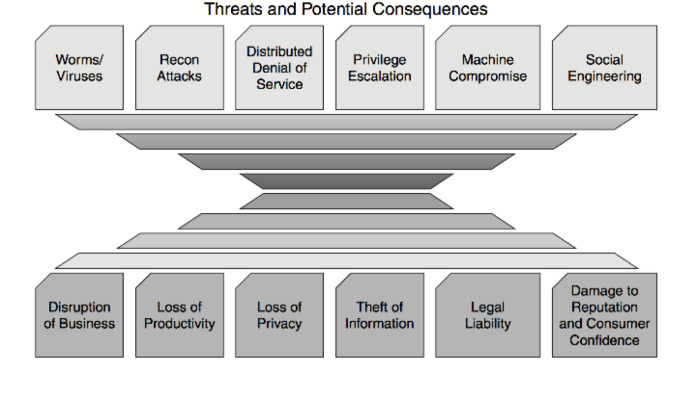
Figure (——) illustrates several threats and their potential consequences.
Figure (———)
Introduction to Vulnerabilities, Threats, and Attacks:
Although studying network security, the three usual terms used are as follows:
- Vulnerability-A weak point that is essential in every network and device. This contains routers, switches, desktops, servers, and similar security gadgets themselves.
- Threats-The people keen, prepared, and eligible to take advantage of each security flaw, and they frequently examine for new exploits and weaknesses.
- Attacks-The threats use a selection of kits, scripts, and software to release attacks towards networks and network devices. Normally, the network devices beneath attack are the endpoints, such as servers and PC.
The sections that comply with talk vulnerabilities, threats, and attacks in more detail.
First aspect: let’s talk about vulnerabilities in ISP
Vulnerabilities within ISP network security can be summed up as the “soft spots” which can be found in each network. The vulnerabilities are be found in the network and separate devices that build up the network.
Networks are classically troubled by unique or all of three main vulnerabilities or weaknesses:
- Technology weaknesses
- Configuration weaknesses
- Security policy weaknesses
The sections that follow inspect separately of those weaknesses in further detail.
Technological Weaknesses:
Computer and network technologies have intrinsic security weaknesses. These include TCP/IP protocol weaknesses, operating system weaknesses, and network equipment weaknesses. Table (——) describes these three weaknesses.
Table ( ——) Network Security Weaknesses
|
Weakness |
Description |
|
|
TCP/IP protocol weaknesses |
FTP, HTTP, and ICMP are naturally insecure. (SNMP), (SMTP), and SYN floods are linked to the naturally insecure building upon which TCP was created. |
|
|
Network equipment weaknesses |
Many types of network tools, such as switches, routers, IDS, and firewalls have security flaws that should be known and shielded against. Example of These flaws are as follows Protocols Firewall Holes Password Protection Absence of authentication Routing |
|
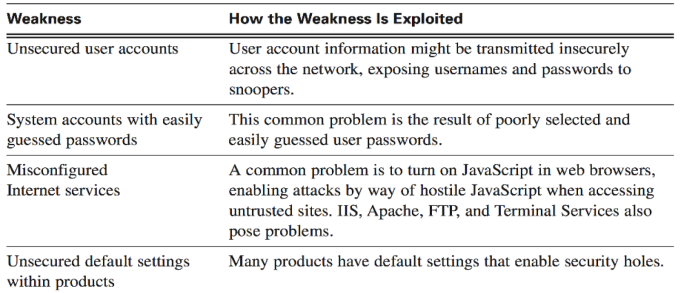
Configuration Weaknesses
Network administrators or network engineers must discover what the configuration flaws are and perfectly setup their computing and network devices to balance. Table (—–) includes usual setup weaknesses.
Table ( —— ) Configuration Weaknesses

Security Policy Weaknesses
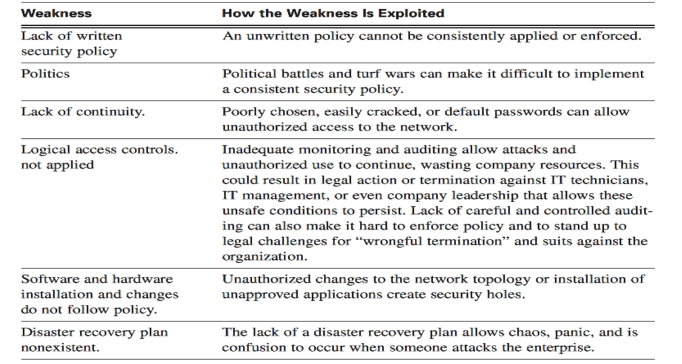
Security policy flaws can generate unexpected security risks. The network can pose security threats to the LAN if workers do not follow the security policy. Table (——) lists selected usual security policy weaknesses and how those flaws are misused.
Table (—–) security policy weaknesses
Threats
There are four main classes of risks to network security, as Figure (—-) depicts. The list that follows defines all class of risk in additional detail.
Figure (———) Variety of Threats
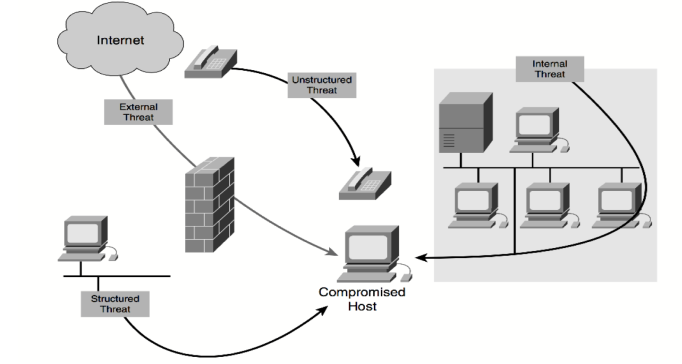
- Unstructured threats– these types of threat happen when users with little experience try to be hackers by using some ready hacking software like shell scripts and knowing password. Even these types of threats which only comes hackers can form a significant harm to companies.
- Structured threats– the source of these threats are hackers who have more technical knowledge and with stronger drive. Such hackers are equipped with knowledge about the weaknesses in the system and are willing to misuse codes and programs. They study, make and use advanced hacking methods to enter business’ systems without their awareness of the hacking.
- External threats– these threats come from persons or groups outside the business without having an official and legal access to business’s system.
- Internal threats– these threats come from people with official access to the system by having an online account or physical access to the system.
Attacks:
There are four main types of attacks:
- Reconnaissance
- Access
- Denial of service
- Worms, viruses, and Trojan horses
each of the above-mentioned attacks will be explained in the next paragraphs.
Reconnaissance
It is the unapproved revelation or the systems’ vulnerabilities, planning, or services (see Fig …)
There are some elements of similarities between reconnaissance and a robber who watches areas to notice any easy target to enter like empty houses, unlocked doors and windows.
Figure (——–) Reconnaissance
Access
This attack can take place when an unapproved interloper gets an access to the system without an account or a password.
Denial of Service (DoS)
This attack is the most worrying type of attacks. It means that hackers make the intended users no longer able to access services, systems or networks. Dos attacks make the systems useless by damaging it or making it too slow. Mostly attacks happen by a hack or a script.
Worms, viruses, and Trojan horses
This type of attack is widespread online through an internet.
Attack Examples
The next section is dedicated to representing examples of attacks to elaborate and explain it more.
Access Attacks
Access attacks take advantage of recognized vulnerabilities in authentication services, FTP services, and internet services to benefit access to internet accounts, private databases, and different private info get entry to attacks can include the following:
- Password attacks
- Port redirection
- man-in-the-middle attacks
- Social engineering
- Password attacks
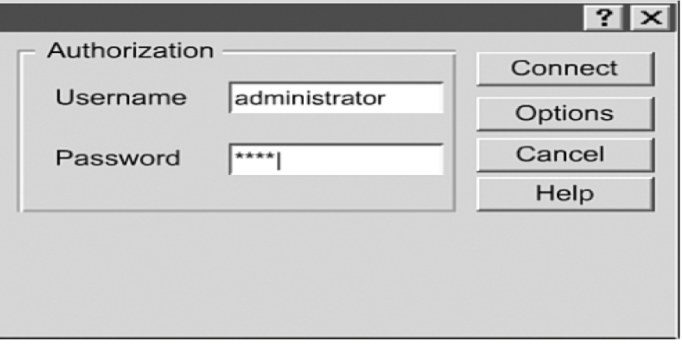
Password attacks may be applied using multiple techniques, such as brute-force attacks, malicious program applications, IP spoofing, and packet sniffers. (see figure ——- for an example of a try to attack the use of the administrator’s profile) brute-force attacks.
Figure (——–) Password Attack Example
¨
Port Redirection
This type of attack (please see Fig) happens when there a trust is taken advantage of through cooperated host to penetrate a firewall which originally is hard to penetrate. For example, when a firewall has a host for each of its three interfaces. External host can contact the public services segment host but not the internal host. The public service segment is also known as a demilitarized zone (DMZ).
Figure (——–) Protocol Analyser
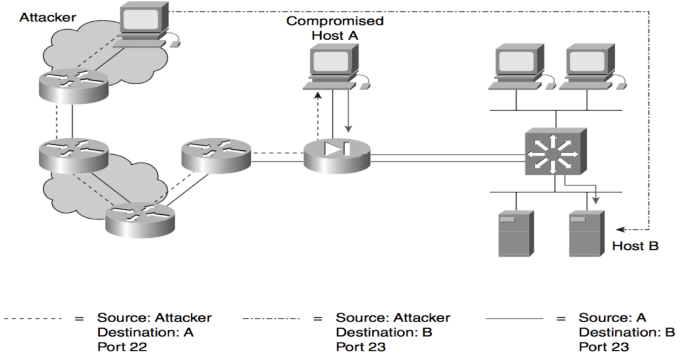
Port redirection may be mitigated typically via using right trust models, that are network (as referred to in advance). Assuming a system underneath attack, a host-based IDS can assist discover a hacker and save you set up of such utilities on a host.
Man-in-the-middle attacks
a person-in-the-middle attack calls for that the hacker has get admission to to net packets that come upon a net. A sample might be operating for (ISP) and has access to all net packets transferred among the ISP net and some other net.
man-in-the-centre attack mitigation is performed by encrypting traffic in an IPsec tunnel, which might permit the hacker to look only ciphertext.
Social Engineering
simplest hack (social engineering) If an outsider can trick a member of an corporation into giving over valued data, which includes places of documents, and servers, and passwords, the technique of hacking is made immeasurably simpler. 90 percent of workplace workers gave away their password in trade for a cheap pen.
Denial-of-Service (DoS) Attacks
This is definitely the most common method of attack. DoS are also one of the hardest attacks to remove entirely. Even amongst hackers, DoS hackers are seen unimportant due to the fact that this method is easy to perform. In spite of that, this form of threat requires high security attention because it can cause a possible huge harm using easy steps (also clarified in Fig…..).
Figure (———). Denial of Service
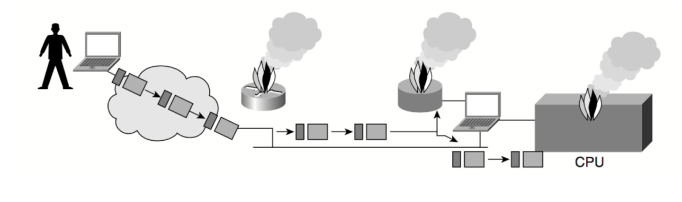
The next example of a some common type of DoS threats:
Ping of death-This attack changes the IP part of the header to deceive others into thinking that there is extra data in the packet than the reality, as a result the system which plays the recipient part will fall apart, as explained in Figure (…..).
Figure (——–). Ping of Death
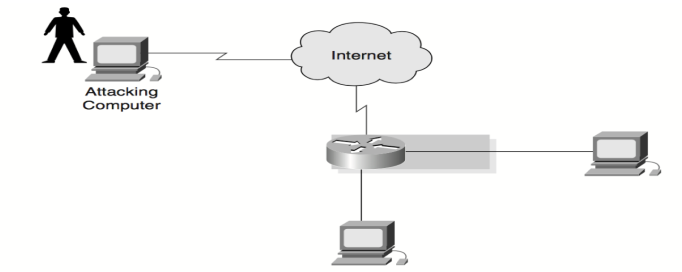
Distributed Denial-of-Service Attacks
Distributed denial-of-service attacks (DDoS) these attacks take place by filling the network links with false data. This data can crush the internet link, which means that consequently the genuine traffic will be denied. DDoS attacks use similar techniques to those used by DoS attacks but the former is performed on a wider scale. They usually use thousands of attack centers to overpower a target (see an example in figure …..)
Figure (——) DDos Attack
Malicious Code
The main vulnerabilities for end-consumer workstations are next:
- Trojan horse-A software created to seem like something else that in reality is an attack app
- Worm-A software that performs random program code and installs duplicates of itself within the RAM of the infected PC, which then infects different hosts
- Virus-Malicious program is connected to some other software to perform a specific undesirable function on the user computing device
Worms
The types of a worm attack is :
- The enabling vulnerability-A computer virus installs itself the usage of an take advantage of the vector on a susceptible system.
- Propagation mechanism-After having access to PC, a worm repeats and selects new devices.
- Payload-After the PC or device is hit with a worm, the attacker has to get entry to the host- frequently as a privileged user. Attackers may want to use a local exploit to increase their privilege degree to the admin.
Vulnerability Analysis
It is vital to analyse and study the present state of network and the administrative practice to know their present amenability with the security needs. This step is needed before working on the addition of new security solutions to an established network. This study will create a chance to find potential enhancements and the possible requirement to reshape part of the system or reconstruct it entirely to meet the requirement. The study/analysis can take place through these steps identifying the policy, analysing the network and analysing the host.
The previous sections attempted to present different types of attacks and suggested some solutions. However, the next table summarises different attacks and presents more solutions to these attacks
|
Threats |
Good practices |
Assets, assets covered |
Gaps (assets not covered) |
||||
|
Routing threats |
|||||||
|
AS hijacking |
Internet protocol addressing, Routing protocols, Administrators |
Administrators |
|||||
|
Make use of useful resource certification (RPKI) to offer AS authentic validation. The reader needs to be conscious that on the time of writing, it’s far impossible to discover AS hijacking mechanically. |
Internet protocol addressing, Routing protocols |
Administrators |
|||||
|
Address space hijacking (IP prefixes) |
Routing, Internet protocol addressing, System configurations, Network topology |
– |
|||||
|
Make use of resource certification (RPKI) to offer AS authentic authentication. |
Routing, Internet protocol addressing, System configurations, Network topology |
||||||
|
set up the best Use policy (AUP), which promotes guidelines to safe peering. |
Routing, Internet protocol addressing, System configurations, Network topology |
||||||
|
set up access filtering from the edge router site to the net. |
Routing, Internet protocol addressing |
System configurations, Network topology |
|||||
|
set up Unicast opposite direction path Forwarding to conform the legitimacy of the main sources IP address. |
Routing, System configurations, Network topology |
Internet protocol addressing |
|||||
|
set up egress filtering on the boundary router to proactively clear out all traffic going to the client that has a source address of any of the addresses which have been assigned to that client. |
Routing, Internet protocol addressing |
System configurations, Network topology |
|||||
|
filter out the routing announcements and apply methods that decrease the danger of placing an extreme load on routing created via illegitimate path updates/announcements. for example, Route Flap Damping (RFD) with a properly-described threshold might also make a contribution to lowering router processing time |
Routing, Network topology |
Internet protocol addressing, System configurations |
|||||
|
filter out the routing announcements and apply methods that decrease the danger of placing an extreme load on routing created via illegitimate path updates/announcements. for example, Route Flap Damping (RFD) with a properly-described threshold might also contribute to lowering router processing time |
Routing, Internet protocol addressing, System configurations |
Network topology |
|||||
|
Setup updates for the routing organization infrastructure may simply be accomplished via a described authority the usage of solid authentication. |
Routing, System configurations, Network topology |
Internet protocol addressing |
|||||
|
Manage the status of BGP to discover uncommon activities like path modifications or uncommon announcement. |
Routing, Internet protocol addressing, System configurations, Network topology |
||||||
|
Route leaks |
Routing, Network topology |
– |
|||||
|
Configure BGP Max-prefix to make sure the legitimacy of routes broadcast. If extra prefixes are received, it’s miles a signal of a wrong behaviour and the BGP session stopped. |
Routing, Network topology |
||||||
|
Utilize useful resource certification (RPKI) to offer AS source authentication. |
Routing, Network topology |
||||||
|
BGP session hijacking |
Routing, Internet protocol addressing, System configurations, Network topology |
– |
|||||
|
set up prefix filtering and computerisation of prefix filters. |
Routing, Internet protocol addressing, System configurations, Network topology |
||||||
|
Use AS route filtering. |
Routing, Internet protocol addressing, System configurations, Network topology |
||||||
|
Employ (TCP-Authentication option) to safe & secure BGP Validation so that you can update TCP- MD5.TCP-Authentication option to make it simple to a trade of keys. |
Routing, Internet protocol addressing, System configurations, Network topology |
||||||
|
DNS registrar hijacking |
Domain name system, Addressing units, Applications, Credentials, Administrators |
– |
|||||
|
Registrants need to defend account credentials and outline authorized customers, at the same time as registrars need to offer a secure and safe authentication technique. |
Addressing units, Credentials, Administrators |
Domain name system, Applications |
|||||
|
Registrants need to defend account credentials and outline authorized customers, at the same time as registrars need to offer a secure and safe authentication technique. |
Addressing units, Applications |
Domain name system, Credentials, Administrators |
|||||
|
Registrants need to keep documentation to “show registration”. |
Addressing units, Applications |
Domain name system, Credentials, Administrators |
|||||
|
Registrants should usage isolated identities for the registrant, admin, technical, & invoicing contacts. therefore, registrars should permit an extra complicated user rights control. |
Credentials, Administrators |
Domain name system, Addressing units, Applications |
|||||
|
Registrars have to set up an effective sector information control. |
Domain name system, Addressing units, Applications |
Credentials, Administrators |
|||||
|
Registrars must keep in mind assisting DNSSEC. |
Domain name system, Addressing units, Applications |
Credentials, Administrators |
|||||
|
Registrars can also manage DNS exchange events. |
Addressing units, Applications, Administrators |
Domain name system, Credentials |
|||||
|
DNS spoofing |
Domain name system, Addressing units, Applications, System configurations, Essential addressing protocols – DNS, Administrators |
Administrators |
|||||
|
Deploying DNSSEC ambitions to extra secure DNS customers (resolvers) source authentication of DNS information, authentic denial of existence, and info or data integrity. |
Domain name system, addressing units, Applications, System Configurations, Essential addressing protocols – DNS |
Administrators |
|||||
|
DNS poisoning |
Domain name system, Addressing units, Applications, System configurations, Executable programs, Essential addressing protocols – DNS, Administrators, Operators |
Administrators, Operators |
|||||
|
Deploying DNSSEC ambitions to extra secure DNS customers (resolvers) source authentication of DNS information, authentic denial of existence, and info or data integrity. |
Domain name system, Addressing units, Applications, System configurations, Executable programs, Essential addressing protocols – DNS |
Administrators, Operators |
|||||
|
Restrict zone transmissions to decrease load on network & system |
Applications, Executable programs |
Domain name system, Addressing units, System configurations, Essential addressing protocols – DNS, Administrators, Operators |
|||||
|
Limited active updates to only official sources to keep away abuse. Such abuse include the misuse of a DNS server as an amplifier, DNS cache poisoning… |
Addressing units, applications, System configurations, Executable programs |
Domain name system, Essential addressing protocols – DNS, Administrators, Operators |
|||||
|
configure the trusty name server as non-recursive. Discrete recursive name servers from the trusty name server. |
Domain name system, Addressing units, Applications, Executable programs |
System configurations, Essential addressing protocols – DNS, Administrators, Operators |
|||||
|
Permit DNS transference over TCP to provision non-standard demands. Furthermore, TCP could be essential for DNSSEC. |
Addressing units, Applications, System configurations, Executable programs |
Domain name system, Essential addressing protocols – DNS, Administrators, Operators |
|||||
|
Domain name collision |
Domain name system, Applications |
– |
|||||
|
Don’t use any domain names which you don’t own for your inner infrastructure. For instance, do not take into account non-public domain name area as top-level domains. |
Domain name system, Applications |
||||||
|
Stopping DNS demand for inside namespaces to leakage into the net via making use of firewall policies. |
Applications |
Domain name system |
|||||
|
Usage booked TLDs such as. invalid, test, localhost, or. example. |
Domain name system, Applications |
||||||
|
Denial of Service |
|||||||
|
Amplification / reflection |
Applications, security, Generic Internet provider, Hardware, Executable programs, System configuration, Application protocols, Administrators, Operators |
System configuration, Essential addressing protocols, Administrators, Operators |
|||||
|
Undertake source IP address deal with authentication at the edge of net organisation to avoid network address spoofing via egress & ingress filtering. |
Applications, Security, Generic Internet provider, Hardware, Executable programs, Application protocols |
System configuration, Administrators, Operators |
|||||
|
Workers of official name server operative must apply (Response Rate Limiting). |
Applications, Security, Generic Internet provider, Hardware, Executable programs |
System configuration, Application protocols, Administrators, Operators |
|||||
|
ISPs and DNS name server operatives must to deactivate exposed recursion on name servers and may just allow DNS requests from reliable sources. |
Applications, Security, Generic Internet provider, Hardware, Executable programs |
System configuration, Application protocols, Administrators, Operators |
|||||
|
Flooding |
Applications, Security, Generic Internet providers, Hardware, Executable programs, System configuration, Essential addressing protocols, Administrators, Operators |
System configuration, Essential addressing protocols, Administrators, Operators |
|||||
|
Industrialists and configurators of net tools must take footsteps to protected and secure all equipment . One option is to have them update by patching mistakes. |
Applications, Security, Generic Internet providers, Hardware, Executable programs |
System configuration, Essential addressing protocols, Administrators, Operators |
|||||
|
Protocol exploitation |
– |
Applications, Security, Generic Internet providers, Hardware, Executable programs, System configuration, Essential addressing protocols, Administrators, Operators |
– |
||||
|
Malformed packet attack |
– |
Applications, Security, Generic Internet providers, Hardware, Executable programs, System configuration, Essential addressing protocols, Administrators, Operators |
– |
||||
|
Application |
– |
Applications, Security, Generic Internet provider, Hardware, Executable programs, System configuration, Application protocols, Administrators, Operators |
– |
||||
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


