Ethical Hacking for Cyber Security
| ✅ Paper Type: Free Essay | ✅ Subject: Information Technology |
| ✅ Wordcount: 6002 words | ✅ Published: 18 May 2020 |
Part A Requirements
This part of Ethical Hacking assignment requires a full demonstration of server configuration and 2 attacks within a controlled laboratory environment. On virtual machines supporting the understanding how the countermeasures are applied protecting vulnerable infrastructures.
1. Configuration of the Server and Clients
1.1 Installation and Configuration
Soon after installing windows server 2012 and the other client machines, the required services and roles were configured. In windows server 2012 few roles were added through the Server Manager Dashboard.
Figure: 1.1 Dashboard
The following screenshot clearly shows that there are many roles that can be added to the server for different purposes. Only three of them
- Active Directory Domain Services
- DHCP Server
- DNS Server
are added in this server to fulfil the task requirements.

Figure: 1.2 role selection
By going through some easy steps all the roles are installed.

Figure: 1.3 installation
1.1.1 Active Directory Configuration
After the installation process is completed, Active Directory Domain Services is configured first. A new forest is added and hence the Root domain name is set to test.com. This domain name is used throughout this assignment. Following screen shot depicts that

Figure: 1.4 AD deployment
After going through each configuration step and setting all other options to their default values, Active Directory is configured.
Inside the Active Directory Users and Computer dialog box under the test.com a new user is created as Administrator

Figure: 1.5 User Creation
The Following credentials were used while creating the following user.
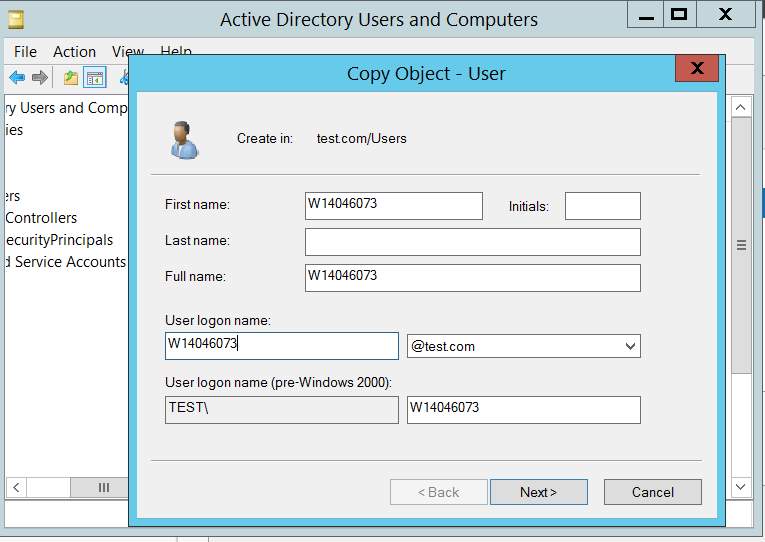
Figure: 1.6 Object Copy
1.1.2 DNS Server Configuration
Inside the DNS Manager window, under TESTSERVER > Forward Lookup > test.com a new host is added named Windows7 with a FQDN windows7.test.com and IP 192.168.120.12. It gave an error that It can’t create the Pointer record but it is managed in the next step.

Figure: 1.7 Adding new host
A new zone is created named as test.com.

Figure: 1.8 adding new zone
Then Reverse Lookup Zone Name is also setup using the network id = 192.168.120, and the reverse lookup zone name is set automatically.

Figure: 1.9 setting reverse lookup
After clicking next Dynamic updates menu was set as follows.

Figure: 1.10 dynamic update
And finally, pointer (PTR) is configured as follows. Same IP address is assigned to the client Windows 7 machine.

Figure: 1.11 confirming the host
Same way Ubuntu Client is also added as a host in the DNS records.

Figure: 1.12 adding host
The server has also given a domain name here testserver.test.com with points towards the IP 192.168.120.11.
After DNS configuration on the Server End. The Client Machine was logged in and assigned the following DNS Server address 192.168.120.11. This is the IP address of Windows Server 2012 i.e. DNS server. It won’t get an IP address as the DHCP server is not set yet.

Figure: 1.13 dns settings
Same settings are setup on the Ubuntu Client as well.
1.1.3 DHCP Configuration
Before DHCP configuration the Name of the Server machine is changed to testserver.
Inside DHCP configurational window, under testserver.test.com (test.comthe root domain setup previously) IPv4 a new scope is created with name scope1.
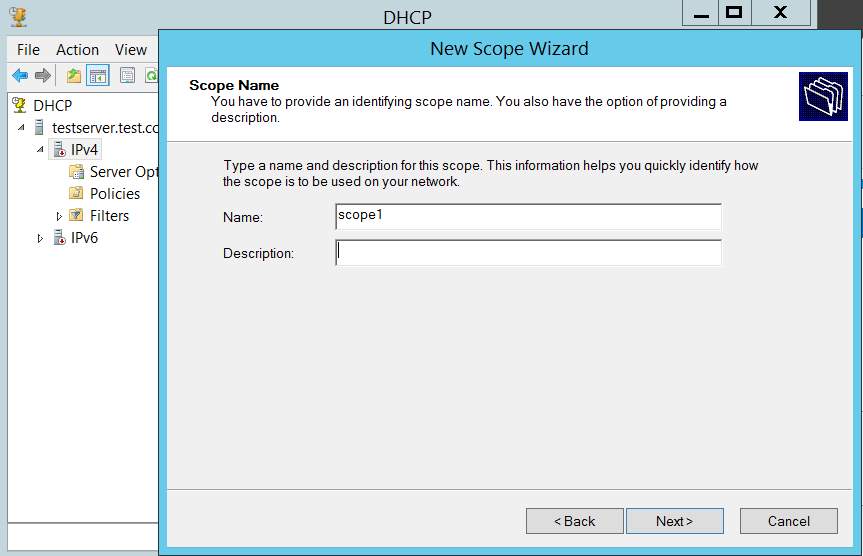
Figure: 1.14 adding new scope
IP pool is defined with its starting and ending range between 192.168.120.12 192.168.120.50. Subnet mask shows that this is a class C network. And the lease duration is set to one day.

Figure: 1.15 IPaddress range

Figure: 1.16 Lease
The default Gateway is set to 192.168.120.2.

Figure: 1.17 gateway
As this server is also going to be a DNS server, so the following DNS information is also added.

Figure: 1.18 DNS
After setting all this DHCP server is restarted to take the changes effect.

Figure: 1.19 reboot DHCP
After restarting the DHCP server. On windows 7 client in command prompt nslookup command is executed to see the DHCP and the DNS working.
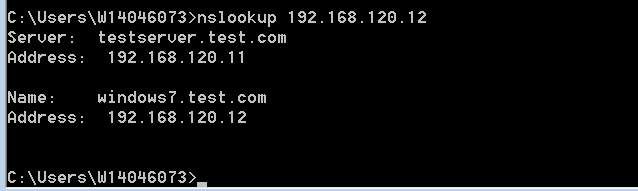

Figure: 1.20 nslookup
It is clear that the domain name is assigned correctly from the new DNS server and also it is pointing towards the IP address that the windows7 client have got from newly created DHCP server.
Finally, a ping test is conducted on both the clients to ensure that everything is working fine.
It is clear from the following ping test that windows 7 machine is working absolutely fine with the DNS.
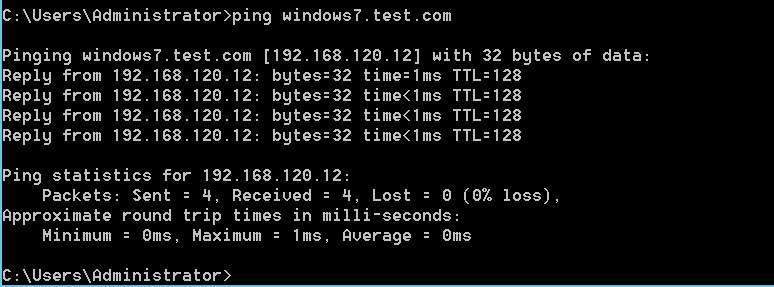
Figure: 1.21 ping
Our other client machine Ubuntu is also on the same network and getting the IP address from the same DHCP, e.g. 192.168.120.13 for (Ubuntu).
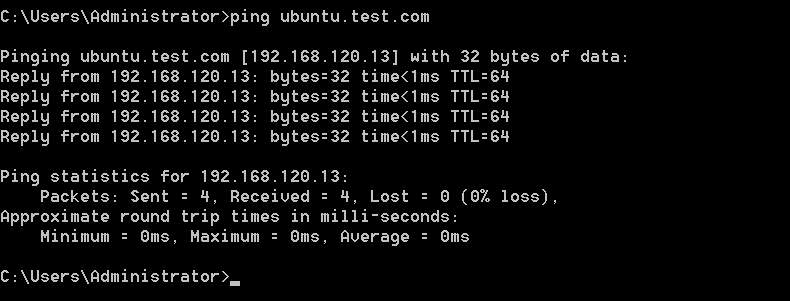
Figure: 1.22 ping
Ubuntu.test.com is successfully assigned to the IP 192.168.120.13.

Figure: 1.23 ubuntu network
1.2 Services and Technology Rationale
Windows: “Microsoft Windows is a group of OSs manufactured by Microsoft. Windows is available in 32 and 64-bit versions and offers a graphical user interface (GUI), multitasking functionalities, virtual memory management capabilities, and support for several peripheral devices. Windows OSs constitute client as well as server versions” (Techopedia, 2017).
Ubuntu Linux: “Ubuntu is an open-source operating system (OS) based on the Debian GNU/Linux distribution. Ubuntu incorporates all the features of a Unix OS with an added customizable GUI, which makes it popular in universities and research organizations. Ubuntu is primarily designed to be used on personal computers, although a server edition does also exist.” (Technopedia 2017)
Kali Linux: Kali Linux is a Linux distribution among some other that is used for the Penetration Testing and Ethical Hacking. This Linux Distro is a Debian based and contains many programs and features pre-installed which are used by Hackers as well as security analysts.
DNS (Domain Name System):
The DNS is a service that runs on Windows, Linux or Mac server to point the human-readable domain names (websites in most cases) to the IP addresses which are
DHCP (Dynamic Host Configuration Protocol):
“The Dynamic Host Configuration Protocol (DHCP) is a network management protocol used on UDP/IP networks whereby a DHCP server dynamically assigns an IP address and other network configuration parameters to each device on a network so they can communicate with other IP networks.” (Wikipedia 2019)
2 Demonstration of Attacks
In this section, all the attacks directed towards the server and the clients are depicted with detailed screenshots.
2.1 DHCP and DNS Spoofing
2.1.1 DNS Spoofing with setoolkit and ettercap
There are numerous issues related to the DNS framework. On the off chance that a programmer figures out how to make the resolver report back the wrong IP address, at that point anybody attempting to gain admittance to a specific site will be sent on a selected wrong one, with no conspicuous technique for the client to identify or even consider what’s going on behind the shades precisely.
In the following DNS spoofing attack, Social Engineering Tool Kit is used to clone a website’s login page. After cloning Ettercap – a tool to spoof the DNS is used to launch the attack. The website used in this attack is your.uopeople.edu.
In the Kali Linux terminal, setoolkit is opened as follows.

Figure: 2.1 Social Engineering Tool Kit
1 Here are different options that can be used for different kind of attacks. The website mentioned above is cloned using the options Social-Engineering Attacks > Website Attack Vectors > Credential Harvester Attack Method > Site Cloner.

Figure: 2.2 URL entry
After cloning the site /etc/Ettercap/etter.conf is edited. Both the uid and gid parameters are set to zero as follows

Figure: 2.3 Etter.conf
Hash (#) sign is removed from the start of both the highlighted lined below.
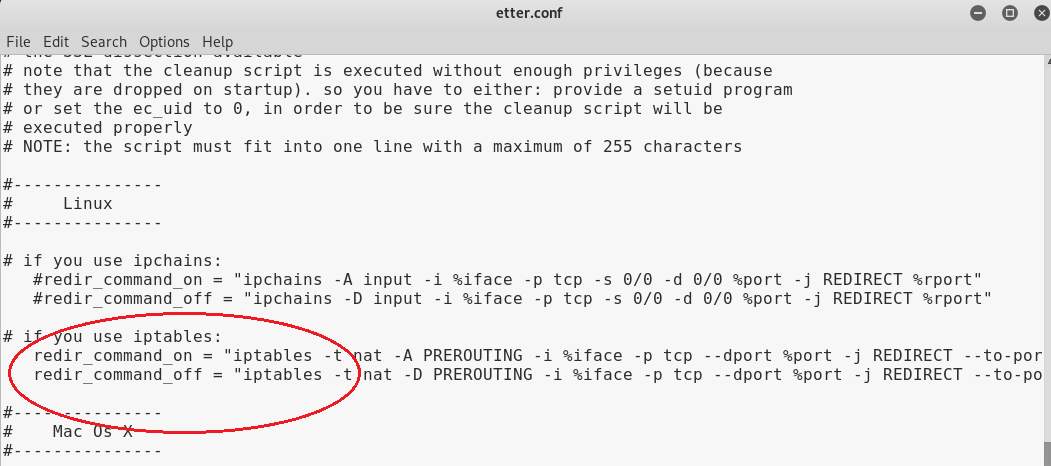
Now,/etc/Ettercap/etter.dns is also edited as follows.

Figure: 2.4 etter.dns
The target website is pointed towards the IP address of the Kali Linux machine. So that every time the client opens the target website, it is pointed towards the Kali Linux IP address where a cloned version of this website is already ready, and setoolkit is waiting for the credentials to be entered.
Ettercap is opened and selected the Windows 7 and the gateway IP addresses as the targets, and DNS spoofing plugin is selected.


Figure: 2.5 ettercap
After this the option sniff remote parameters is checked and then unified sniffing s started.

As soon as the client enters the website, it redirects the client to the Kali Linux VM and opens the cloned page which looks exactly like the original webpage.

A dummy username dog@lilbub.comand a dummy password ilovecates!!!!!!! Is used.

Figure: 2.6 logins
As soon as the credentials are entered the setoolkit running behind the scenes is actively captured the entered creds.

Figure: 2.7 logins captured
The above picture clearly shows that creds are captured successfully.
2.1.2 DHCP MITM Attack
Numerous DHCP servers are presented to MITM (Man in the middle) attacks. In this attack, Kali Linux is going about as a Fake DHCP server. At whatever point a customer demands for the IP address from the DHCP server this rouge server reacts quicker than the first one and allocates the IP address to the target PC and consequently, all the traffic from the unfortunate casualty PC goes from the Attacker Machine.
To depict this attack, Graphical version of Ettercap and Wireshark was used to capture the credentials from the victim computer as he enters them in his web browser. The following information was entered in the Ettercap to create a rouge DHCP server on Kali Linux attacker Machine.

Figure: 2.8 MITM attack
The rouge IP address was assigned to the victim machine.
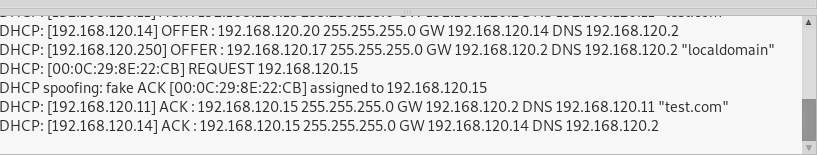
To confirm this, the IP address from the cmd of the victim Machine (Windows 7 this time) is checked.
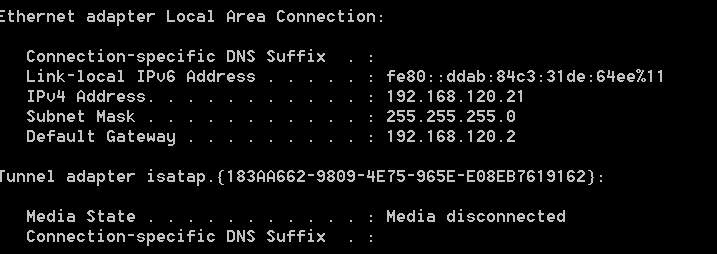
Figure: 2.9 windows 7
Now website named portal.flexispy.com was opened from the victim browser and sign in information was entered. The webpage is unable to download some images because this is an older version of internet explorer on windows 7.
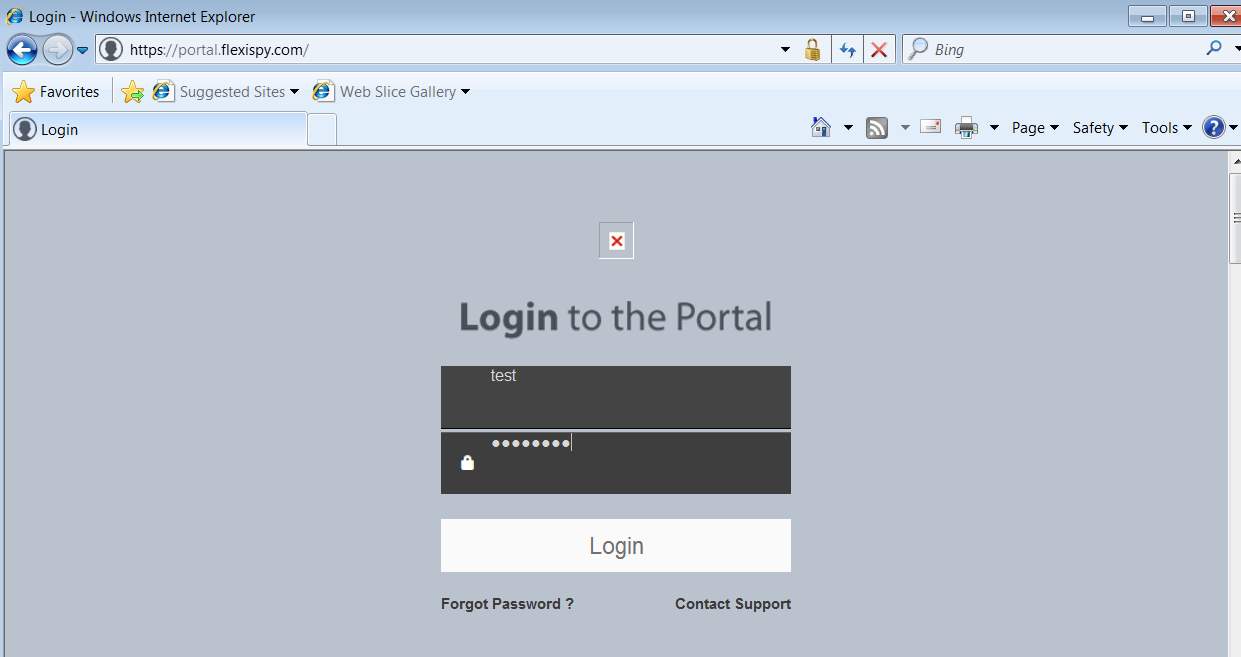
Figure: 2.10 flexspy.com
Wireshark was running out of sight while all above activity was occurring. In the wake of entering the qualifications, it tends to be unmistakably observed that they were caught in the Wireshark.
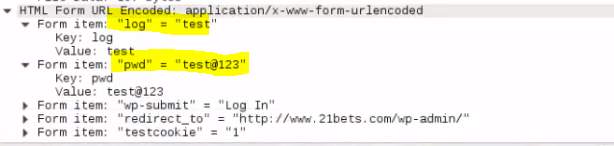
Figure: 2.11 logins captured
2.2 Session Hijacking
In this experiment, a web session was hijacked using arp spoofing and sslstrip. On the Kali Linux machine, all the machines present in the network were scanned for their IP and mac addresses using a tool called scapy.

Figure: 2.12 scapy
This time Ubuntu Client machine is undergoing the above mention attack, using its IP address 192.168.120.13.
An arpspoof attack using the command “arpspoof -I eth0 -t 192.168.120.2 -r 192.168.120.13”.

Figure: 2.13 arpspoof
It is clear from the below screenshot taken from the victim Ubuntu Machine that the attack worked perfectly as the router and the Kali Linux Machine have the same Mac address. So, anything done on the victim browser can be logged on the attacker machine by using Wireshark or any other sniffing tool.
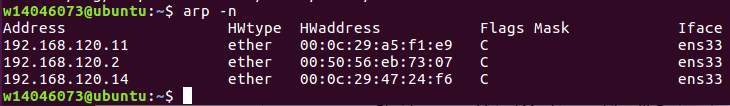
Figure: 2.14 ubuntu arp
IP needs to be forwarded in order the sslstrip attack to work. Now what this attack does, it strips off any https strip from the website and redirects the traffic to HTTP so that we can blatantly get all the information our target user is giving on that particular website.
To do that the following commands are used and then started the sslstrip from the terminal.

Figure: 2.15 Kali Linux iptables
A logfile of the sslstrip is used to capture the credentials.
When the website opened in the victim Ubuntu Machine’s browser and the user entered the credentials, they were capture by the logfile as shown. Also, there is no https button on the URL bar of the browser.
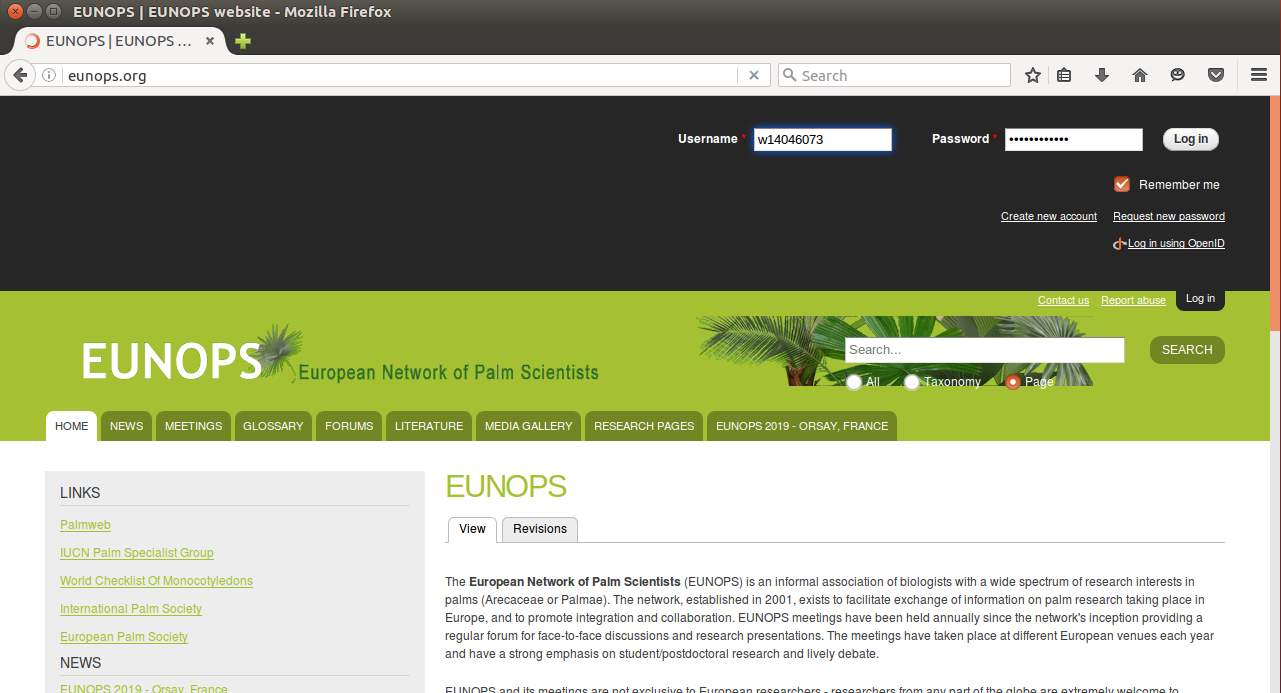

Figure: 2.16 logins captured
2.3 DHCP Starvation Attack
DHCP starvation attack is a typical DoS assault on numerous DHCP servers. What makes this assault increasingly hazardous is the majority of the associations does not have a legitimate instrument for the avoidance of DoS or DDoS attacks.
In this attack, Yersinia is used. Yersinia is a hidden tool that is present in Kali Linux by default. This is not a very common but very handy and powerful tool. To start the Graphical version of Yersinia, the following command is executed.
Figure: 2.17 Yersinia
Under Launch attack > DHCP menu, the Sending Discover Packet (DoS) option is selected and pressed OK. All other parameters are set by default.

Figure: 2.18 DHCP attack
As soon as the attack launched, it started sending packets to our DHCP server filling its lease table with rouge values.

Figure: 2.18 DHCP attack
Now when the clients are checked one by one and sent solicitations to renew their IP address, this is the thing that is found. Both the client machines are unfit to associate with the new DHCP server.

Figure: 2.19 windows 7

Figure: 2.20 Ubuntu IP check
3 Prevention Mechanisms and Countermeasures
News of large-scale cybersecurity threats and cyberattacks dominate the headlines all too often in today’s Information Age: hackers exploiting vulnerabilities of a retail giant, foreign influence in elections, and new forms of ransomware underscore the importance of preparing for these types of emerging threats.
As a result, cyber risk management has become a fundamental component of business operations, understanding and mitigating risk has become an essential skill for business leaders, thought leaders, analysts, as well as security and technology specialists.
3.1 Cost of a Cyber attack
There are four factors that influence the indirect costs of a breach.
Data Loss
According to recently collected data on cybersecurity, around 2.6 billion records were stolen, lost or uncovered worldwide in 2017. The loss of this data piles on alot bigger bills than simply the underlying information recuperation, prompting potential fines, punishments, and case for a business.
Investor perception
When a breach occurs, an abrupt drop in an organisation’s apparent esteem is probably going to pursue. Negative media inclusion can fuel the “sell now” mindless obedience, which could be the last nail in the box if your business is unfit to afloat in the wake of an assault. This is particularly valid for littler organisations that don’t have the infrastructure.
“The average cost of a successful cyber attack to an organisation can be as much as $5 million” -Ponemon Institute (Feb 2018)
Notoriety
Organisations don’t just lose current clients following a cyber-attack; a harmed brand notoriety implies they likewise lose the possibility to increase new ones down the road. An organisation’s image is connected to all parts of the business, including development and income. Indeed, 85% of U.S. buyers are faithful to brands that defend and ensure their own information, meaning an information break can have genuine ramifications for the eventual fate of your business.
Operational expense
Over the loss of information, cybercriminals will now and then spotlight their endeavours on bringing down a business’ online activities through DDOS attacks, which can prompt loss of clients, and at last money. This hazard, specifically, is one that requires key strength wanting to survive.
3.2 Creating a Cyber Security Culture
A standout amongst the most powerless regions for any association is its workers. As indicated by IBM’s yearly X-Force Threat Intelligence Index 2018, human carelessness remains the main source of information breaks, representing 66% of the considerable number of records bargained in 2017. Along these lines, all representatives are in charge of guaranteeing the system is remained careful. You could have the most recent enemy of infection innovation; however, unintentional human blunder can still permit malicious software a way in.
Concentrating on encouraging a solid cybersecurity culture could be a superior safeguard against cyber threats than any single mechanical approach. A cybersecurity culture expects to make data security contemplations a fundamental piece of a representative’s everyday life, and is just accomplished by weaving cybersecurity through authoritative systems and rehearses and keeping up dynamic discussions with staff.
To guarantee you pursue best practice with regards to your security, your arrangement ought to envelop the following:
- Set up a cybersecurity consistency standard and information use approach for all employees
- Perceive potential dangers, and the numerous structures they come in like phishing and ransomware
- Keep your work secure by utilising passwords within any event six characters, one of which ought to be an uncommon character and it ought to likewise incorporate at any rate one uppercase letter. Update these passwords somewhere around each 30 to 60 days
- Instruct representatives to distinguish and report suspicious behaviour
3.3 Strategising for cyber risk mitigation
Consider these procedures when creating your cyber mitigation strategy:
Do hardware assessments
Guarantee that your business just uses ‘clean’ equipment. Try not to permit equipment that hasn’t been checked for a conceivably perilous infection. After which, an inventory of key assets, data, systems and infrastructure is essential to the business’s operations in order to track them.
Secure wireless networks
Encrypt wireless networks that company data is on. Use more grounded AES (Advanced Encryption Standard) encryption and a complex passphrase to give better security from more grounded attacks. Channel clients’ entrance to sheltered and vital websites. Block unsubstantiated sites and sites that permit unlawful downloading and spilling.
Back up information
All business information ought to be sponsored up. In case of a break, any lost information ought to be retrievable. Execute access control, restricting appropriate data on a need-to-know premise, to guarantee security and protection.
Update the Softwires
Cybercriminals are continually advancing, so you need to plan to be one stage ahead. Ensure your software are updated to the latest version, to reduce the odds of an effective digital attack.
Go threat hunting
Organizations should find a way to anticipate assaults by procuring cybersecurity experts like ethical hackers, penetration testers, and threat investigators to effectively chase for dangers rather than just responsively protecting their organization information.
In order to optimise the cyber risk mitigation strategy, there is a need to manage cyber breaches before, during and after they happen through a proactive approach. In a world of ever-evolving threats, making sure the organization, its network, and the staff have what it takes to stay secure in the face of an impending attack is fundamental to surviving in today’s cyber landscape.
4 References Part A
- Broad, J. and Bindner, A. (2014). Hacking with kali. Practical Penetration Testing Techniques
- Owasp.org. (2018). Session hijacking attack – OWASP. [online] Available at: https://www.owasp.org/index.php/Session_hijacking_attack [Accessed 6 Nov. 2018].
- Lee N. (2015) Cyber Attacks, Prevention, and Countermeasures. In: Counterterrorism and Cybersecurity. Springer, Cham
- Sans.org. (2018). SANS Institute: Reading Room – ISO-17799. [online] Available at: https://www.sans.org/reading-room/whitepapers/iso17799/paper/33558 [Accessed 7 Nov. 2018].
- Ashford,W. (Feb, 2019). ‘IT Priorities 2019: Cyber security and risk management among top priorities for 2019’. Retrieved from Computer Weekly.
- Leskin, P. (Dec, 2018). ‘The 21 scariest data breaches of 2018’. Retrieved from Business Insider.
- (2017). ‘Cybercrime damages $6 Trillion by 2021‘. Retrieved from Cybersecurity Ventures.
- Crowe, J. (Feb 2018). ‘10 Must-Know Cybersecurity Statistics for 2018’. Retrieved from Barkley.
- Ismail, N. (Apr, 2018). ‘Cyber security failings grow as 2.6BN records stolen or compromised in 2017’. Retrieved from Information Age.
- Eubanks N. (Jul, 2017). ‘The True Cost Of Cybercrime For Businesses’. Retrieved from Forbes.
- (Feb, 2017). ‘Organizations wasting billions on customer loyalty programs that don’t work like they used to’. Retrieved from Accenture.
- Weisman, S. (Nd). ‘What is a distributed denial of service attack (DDoS) and what can you do about them?’. Retrieved from Norton.
- Dobrygowski, D. (Jul, 2016). ‘Cyber resilience: everything you (really) need to know’. Retrieved from World Economic Forum.
- Bailey, L. (Apr, 2016). ‘Cyber risks spill over into the physical world‘. Retrieved from Zurich.
- (Mar, 2018). ‘ IBM X-Force Threat Intelligence Index 2018’. Retrieved from IBM.
- Hayslip, G. (Mar, 2018). ‘9 policies and procedures you need to know about if you’re starting a new security program’. Retrieved from CS Online.
- Rashid, F. (Oct, 2017). ‘Types of phishing attacks and how to identify them’. Retrieved from CS Online.
- Jones, B. (Sep, 2017). ‘How often do you really need to change your passwords?’. Retrieved from Psafe.
- Cooper, C. (May, 2017). ‘How to get your staff to take cybersecurity seriously’. Retrieved from CNET.
- Shein, M.D. (Jan, 2018). ‘Mitigating cyber risk in 2018’. Retrieved from Risk management.
- Woollven, C. (2017). ’5 ways SMEs can mitigate cyber security risks’. Retrieved from IT Governance.
- Woollven, C. (2017). ’5 ways SMEs can mitigate cyber security risks’. Retrieved from IT Governance.
- Woollven, C. (2017). ’5 ways SMEs can mitigate cyber security risks’. Retrieved from IT Governance.
- (Nov, 2018). ‘Cyber insurance and why you need it’. Retrieved from IT Web.
- Nelson, N. (Mar, 2018). ‘7 Jobs you didn’t know about in cyber security’. Retrieved from Woz-u.
END OF PART A
============================================================================================================================================
5 Part B – Abstract
Drones, also known as “Unmanned Aerial Vehicles (UAV) has brought much convenience to our personal and business lives. Drones are typically used as a commercial product and for personal use. They have usually transitioned from first being used for military-only applications, which is now used as a strategic tool that has transformed a range of industries including in insurance, agriculture and real estate. As the usability of drones continues to grow, it also represents increased security and privacy concerns. The rapid development has gradually proven to expose its safety in aspects such as sensors and communications. Without additional safeguards, malware through forms of cyber attacks could be used as entities for terrorism and crime. Where drones are managed through information, it only takes a small attack for the information to be misused, for it to perform incorrect action and judgments. Even sensor damage can cause failure to read and process information. The lack of communication or hacked links increases the susceptibility of privacy and security. As predicted by the FAA, there could be as many as 30000 drones which naturally raises justified concerns on human, cyber and digital crimes.
6 Introduction
As it has been well recorded, Drones are unmanned aircraft, which can be remotely controlled or fly autonomously through software-controlled systems, typically with onboard sensors and GPS. The evolution of drone technology has caused many individuals and businesses to adopt drones for various purposes (Nassi et.al, 2019). The media have expressed many malicious attacks that have occurred with drones at present. Although drones offer many advantages, security and privacy continue to be a societal threat. Drones were restricted to military-only operations, but now many sectors, particularly private, have begun to use drones for a wide range of diverse use. Drone-related incidents are being reported on a regular basis, and the volume of attacks is expected to increase due to the “open sky” policy adopted by many countries such as the UK, New Zealand the US (Insider, 2018; Wired, 2017). This has continuously highlighted and flagged for the need for mechanisms that controls malicious activity through various drone operations. As flights have been targeted for attacks, it is arguably expected that drones could next become prime targets for terrorists and criminals, not to crash or physically harm, but to obtain key information that may aid cybercriminals with the cyber and digital crimes. Therefore, it is justified that society is at risk with the use of drones and that laws must be ratified to ensure better policing of drones (McKelvey et al. 2015).
This report aims to outline the popular malicious and security concerns that have occurred, along with critical analysis on any mediums being proposed for better security of future drone operations, including the review of challenges that have arisen. The result is for the reader to be able to understand its current state whilst understanding the suggestions that should be investigated to propel the ability of society to handle threats posed by drones. This will be summarized in the form of a concluding response.
The report is to focus its analysis on the characteristics of drone technology and the capabilities that cybercriminals have unauthorizing access to user information and security to take over its performance and commands. The intended focus is to identify the characteristics of drone technology that are most vulnerable, such as the sensor configuration and GPS integration. The research used will be factual sources that illustrate examples the kinds of typical drone attacks, along with other supporting journals that analyse privacy and security in drones. The journals and materials used will be critically analysed to illustrate a progressive argument on opinions from other authors in terms of any challenges to counter these security and privacy issues.
7 Report Analysis
Individual entrepreneurs, small organizations and business and authorities are not realizing the amazing potential of drones, and the purposes in which it can be used for. With law and regulation continuously updating to accommodate for the quality and usability of drones, they are also identified for various malicious entities in order to misuse drones for illegitimate purposes (Nassi et al. 2019), promoting heightened security and privacy concerns. Nassi et al. (2019) state that as an increase in drone sales creates new threats and opportunities for attacks. As explained by Altawy and Youssef (2016) “Accordingly, protecting civilian drones from adversaries and protecting individuals and their properties from malicious drones is still an open problem.” It has been well documented through history that drones were mainly used for military-only services and used for recreational purposes more recently, however giant companies including Amazon, Google and Facebook are exploring with the idea of employing drones for goods and services says Cat et al. (2014). It can predict that as the number of drones increases, continued vulnerability of privacy and security will emerge, for example, civilian drones threat consists of interference with aviation systems. Where Marshall et al. (2015) states that “security and safety of individuals were not of significant interest”, this shows negligence to the use of drones and that the common characteristics of cyberattacks are frequently through the use of sensors and GPS configuration, where information can be easily misguided and compromised. Which brings us to the ability to launching a cyber-attack. Sedjelmaci (2016) states that the drones’ network is typically attacked against two things; Data Integrity and Network Availability. He goes on to state that the main goal of cyber-attacks is to viciously alter information that legitimately injects from data into its sensors, delivering false information and jeopardising data integrity. The second class, Network Availability is the most “well-known” threat for Denial of Service (DNS) attacks, to “exhaust resources by launching exhaustion attack or disturb routing protocol operations”. Whether the article from Sedjelmaci (2016) is focusing on two distinct areas or is severely lacking knowledge on the subject is debatable. There is a lack of knowledge that demonstrates an example cyberattack process and history of these attacks happening. There is also a lack of security challenges proposed. The article fails to address the proven methods unlike Javaid et al. (2012) who emphasises the different threat techniques that are typically operated by attackers. The article emphasises that several recording of UAV incidents were controlled by terrorist groups, which have occurred since 2009. Sedjelmaci (2016) also didn’t address Confidentiality as another vulnerability. UAV systems consist of very confidential data which is sensitive in nature, and obtaining it requires a high-level of security clearance. Compromising its security is common through interception of information through communication links and GCS (software). These kinds of attacks can affect UAV through hacking, eavesdropping, spoofing and multi-protocol attacks (Foss, 1998). Integration of a system can be compromised through modification of existing information and fabrication of new information, meaning to alter data whilst it’s in transit or while in storage. Gudla et al. (2018) believe Denial of Service attacks (DNS) is the most popular form of attack: “the remote-control device is disconnected from the drone by continuously sending the de-authentication commands. The drone will crash immediately, or the attacker will take control of the drone by connecting to his device”. Gudla et al. (2018) continue to present executable examples of commands that may typically be disrupted by attackers to perform misguided signals to the drone. The experiments reported in the paper by Gudla et al. (2018) and Javaid et al. (2012) are broad and well thought-out compared to other referenced resources. They better conceptualize experiments of how attacks may thoughtfully be carried out to deliver disrupt the integrity, security and confidentiality of attacks.
Integrity falls into a form of privacy. Privacy is a keyframe in particular for surveillance technologies (drones) yet a precise conceptualisation and definition of privacy is yet to be identified and solidified. Finn and Wright (2012) and Whitman (2004) described privacy as important yet “an unusually slippery concept”, and Solove (2008) believes that privacy is “a concept in disarray. Nobody can articulate what it means.” The conception of privacy within drone technology remains elusive and it is assumed that privacy is comprised of multiple dimensions as opposed to just one concrete definition, such privacy of the person, data, communication or behaviour. Solove also believes that the effects of privacy surveillance have been attempted with data protection legislation to mitigate concerns. Lyon argues that privacy legislation and data protection is difficult to connect to a basic human right and privacy is inadequate to capture surveillance effects. These thoughts seem to suggest that privacy has been utterly neglected which emphasises the latest attacks that have occurred. They are now becoming a growing threat for law enforcement and business security says Pritchard (2019), explaining that “rogue drones grounded planes at London Gatwick, the UK’s second-busiest airport. But, increasingly it’s not just the air traffic controllers sounding the alarms over drones, it’s also the cybersecurity community.” They are now becoming more prone to cyberattacks, disrupt networks and capturing sensitive data. Some other forms of privacy breaches of drones, as explained by Nassi et al. (2019), may consist of radio transceivers can be used to locate and track people, by extracting unencrypted information through internet and radio protocol, performing MITM attacks on telephony and additional eavesdropping into conversations. So, it has been determined that privacy may be considered as multiple definitions. Drones transition from military-only applications to a strategic asset has required law legislation to act. Maxim (2019) explains that GDPR has now made it harder to legally fly drones in Europe, which is expected to evolve exponentially. This also means organizations must address their operations on the use of drones. Finn and Wright (2012) believe that ethics and privacy are more likely to impact and marginalise these population more than anything else. A thoughtful recommendation to counter these privacy issues, specifically from Finn and Wright (2012) who state that since privacy may not be adequately protected, and because drones require the undertaking of visual surveillance, the benefits of using imaging cameras and sensors, if deployed, must be accompanied with legislation so that regulator parties are able independently oversight its use. “Improvements are needed in our legal and regulatory framework if privacy is indeed to be respected by law enforcement authorities and intelligence agencies.” (Wright, 2010). The confusion and current concerns surrounding privacy where there is no concrete definition towards the use of drones, along with a lack of legislation or ruling in order to safeguard the privacy of its characteristics from cyber attacks goes to show just how much privacy has been neglected, and that the use of drones is exponentially rising, however there are no restrictions of its use, compromising confidentiality and integrity. The criticism to the authors is that it seems that a lack of research and a lack of knowledge is prudent. There is also no forecast of future solutions to current privacy challenges. Privacy vulnerability is currently at large, and this also demonstrates the negligence of its use, paving the way for more attacks.
8 Conclusion And Summary of Findings
The research conducted demonstrates that there is currently growing negligence on the privacy and security for the use of drones. The exponential rise of the use of drones across various industries is currently struggling to be controlled, yet its release in the early 2000s for military-specific operations may have demonstrated that there was a lack of foresight that the use of drones would expand away from just military use. Its use in commercial, civilian and military operations are continuing to increase, and its vulnerabilities are creating risks to the public and private sectors. The use of sensors and GPS carry sensitive and confidential information, picture and video feed. Mitigating the risk requires stringent legislation of use and analysis of various vulnerabilities and attack techniques. There is a lack of defensive techniques against its physicaal and cyber vulnerabilities and cyberattacks can easily exploit wireless networks or connected devices. It is recommended that a form of wireless encryption and detection systems are controlled to make it complex for the attacker to attack. Considering privacy legislation and defensive techniques are still not concrete, which they would be if applied to government legislation, the exponential growth in the use of drones is causing catch-up to ensure stringent security and privacy control is applied to manage its use and protect from attacks.
9 References Part B
- Altawy, R. and Youssef, A. (2019). Security, Privacy, and Safety Aspects of Civilian Drones: A Survey. ResearchGate, 10, pp.7-12.
- Alves-Foss, J. (1998). Multi-Protocol Attacks and the Public Key Infrastructure. [online] Uidaho.edu. Available at: https://www.uidaho.edu/engr/departments/cs/our-people/faculty/jim-alves-foss [Accessed 31 May 2019].
- Finn, R. and Wright, D. (2012). Unmanned aircraft systems: Surveillance, ethics and privacy in civil applications. Computer Law & Security Review, 28(2), pp.184-194.
- Gudla, C. and Rana, M. (2018). Defense Techniques Against Cyber Attacks on Unmanned Aerial Vehicles. ResearchGate, [online] 1, pp.111-115. Available at: https://www.researchgate.net/publication/328135272_Defense_Techniques_Against_Cyber_Attacks_on_Unmanned_Aerial_Vehicles [Accessed 31 May 2019].
- How to Detect Cyber-Attacks in Unmanned Aerial Vehicles Network?. (2016). ResearchGate, [online] 10(1), pp.1-6. Available at: https://www.researchgate.net/publication/313452376_How_to_Detect_Cyber-Attacks_in_Unmanned_Aerial_Vehicles_Network [Accessed 31 May 2019].
- Javaid, A., Sun, W. and Alam, M. (2012). Cyber security threat analysis and modeling of an unmanned aerial vehicle system. ResearchGate, [online] 10, pp.595-590. Available at: https://www.researchgate.net/publication/235676360_Cyber_security_threat_analysis_and_modeling_of_an_unmanned_aerial_vehicle_system [Accessed 31 May 2019].
- Nassi, B., Shabtai, A. and Masuoka, R. (2019). SoK – Security and Privacy in the Age of Drones: Threats, Challenges, Solution Mechanisms, and Scientific Gaps. [online] Arxiv.org. Available at: https://arxiv.org/pdf/1903.05155.pdf [Accessed 31 May 2019].
- Stewart, J., Stewart, J., Marshall, A., Baker-Whitcomb, A., Adams, E., Davies, A., Davies, A. and Davies, A. (2019). Trump Moves to Fill America’s Skies with Drones. [online] WIRED. Available at: https://www.wired.com/story/faa-trump-drones-regulations/ [Accessed 31 May 2019].
- Whitman, J. (2004). The Two Western Cultures of Privacy: Dignity versus Liberty. [online] Digitalcommons.law.yale.edu. Available at: https://digitalcommons.law.yale.edu/cgi/viewcontent.cgi?referer=https://www.google.com/&httpsredir=1&article=1647&context=fss_papers [Accessed 31 May 2019].
- Threatpost.com. (2019). Drones are Quickly Becoming a Cybersecurity Nightmare. [online] Available at: https://threatpost.com/drones-breach-cyberdefenses/143075/ [Accessed 31 May 2019].
- Wright David, Friedewald Michael, Gutwirth Serge, Langheinrich Marc, Mordini Emilio, Bellanova Rocco, et al. Sorting outsmart surveillance. Computer Law & Security Review 2010;26(4):343e54, 344.
- B. Insider, “Amazon and ups are betting big on drone delivery,”. Available at: http://www.businessinsider.com/amazon-and-ups-are-bettingbig-on-drone-delivery-2018-3
- Pritchard, S. (2019). Drones are Quickly Becoming a Cybersecurity Nightmare. [online] Threatpost.com. Available at: https://threatpost.com/drones-breach-cyberdefenses/143075/ [Accessed 31 May 2019].
- Maxim, M. (2019). The Security And Privacy Implications Of Drones. [online] Forrester. Available at: https://go.forrester.com/blogs/the-security-and-privacy-implications-of-drones/ [Accessed 31 May 2019].
- Douglas M. Marshall, Richard K. Barnhart, Eric Shappee, and Michael Thomas Most. 2015. Introduction to Unmanned Aircraft Systems. CRC Press.
- McKelvey, N. and Diver, C. (2015). Drones and Privacy. [online] RessearchGate. Available at: https://www.researchgate.net/publication/283867327_Drones_and_Privacy [Accessed 31 May 2019].
- Wright David, Friedewald Michael, Gutwirth Serge, Langheinrich Marc, Mordini Emilio, Bellanova Rocco, et al. Sorting outsmart surveillance. Computer Law & Security Review 2010;26(4):343e54, 344.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal



