Creating a WAN Diagram
| ✅ Paper Type: Free Essay | ✅ Subject: Information Technology |
| ✅ Wordcount: 1139 words | ✅ Published: 20 Sep 2017 |
- BY: JAN AVIT MICOLH MATUGAS
“Creating WAN Diagram”
a) Create a WAN diagram detailing and labeling all components of a WAN network according to the scenario (network devices, computers and server’s configurations). Every branch must have their own IP range.
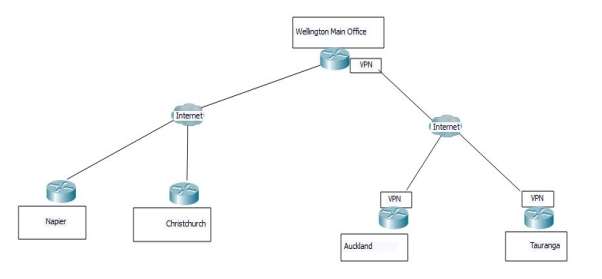
Figure 1 Actual Diagram of Wellington being connected to its all branches
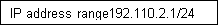
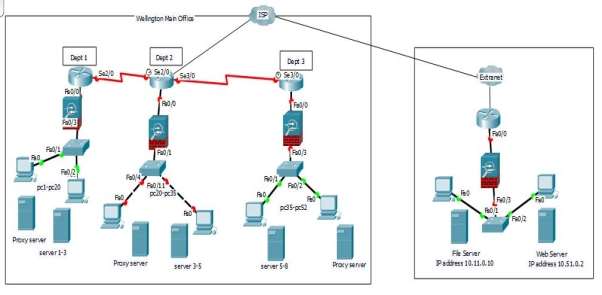
Figure 2. Actual Diagram of Wellington Main Office
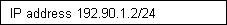
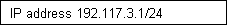
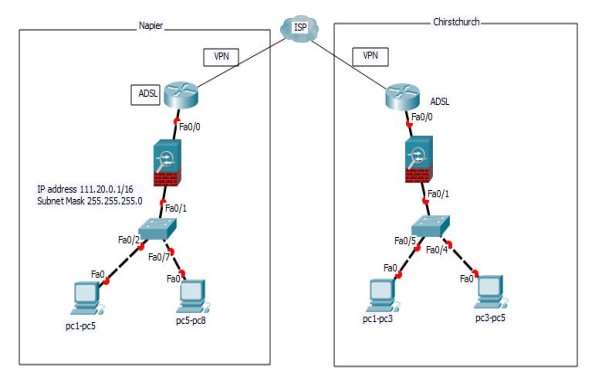
Figure 3. Actual Diagram of Napier and Christchurch
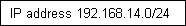
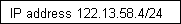
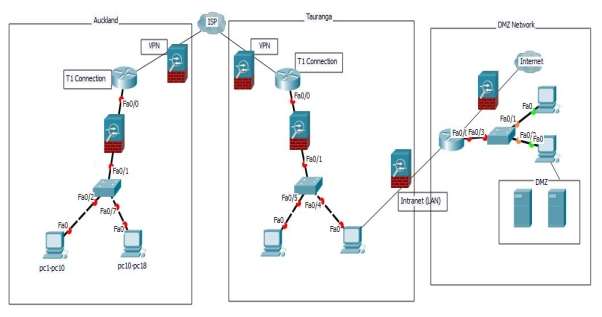
Figure 4. Actual Diagram of Auckland and Tauranga
b) Write down the IP address range for all branches.
1. Wellington 192.110.2.1/24
2. Napier 192.90.1.2/24
3. Christchurch 192.117.3.1/24
4. Auckland 122.13.58.4/24
5. Tauranga 192.168.14.0/24
c) List down the components used in the network you have created with their configuration, separated by branch:
|
Component |
Configuration |
|
Wellington |
|
|
52 PC |
HP Z240 SFF i5-6500 3.2GHz 8GB DDR4 1TB Win7Pro |
|
8 Servers |
Intel 7th Gen Core i7 7700 3.6Ghz Quad Core/ 16 GB DDR4 RAM |
|
4 Routers |
Netgear Orbi RBK50 MU-MIMO Wi-Fi System, Orbi Router + Orbi Satellite, Tri-Band AC3000, 4 x Gigabit LAN, |
|
4 Switches |
Ubiquiti UniFi Switch US-8-150W, 8-Port Gigabit Managed PoE+ Switch, with 8 x PoE/PoE+ (Max 150W) and 2 x SFP Rackmountable, Fanless, Passive 24V & 802.3af/at |
|
Napier |
|
|
8 PC |
HP Z240 SFF i5-6500 3.2GHz 8GB DDR4 1TB Win7Pro |
|
2 Router |
Netgear Orbi RBK50 MU-MIMO Wi-Fi System, Orbi Router + Orbi Satellite, Tri-Band AC3000, 4 x Gigabit LAN, |
|
2 Switch |
Ubiquiti UniFi Switch US-8-150W, 8-Port Gigabit Managed PoE+ Switch, with 8 x PoE/PoE+ (Max 150W) and 2 x SFP Rackmountable, Fanless, Passive 24V & 802.3af/at |
|
Chirstchurch |
|
|
5 PC |
HP Z240 SFF i5-6500 3.2GHz 8GB DDR4 1TB Win7Pro |
|
Router |
Netgear Orbi RBK50 MU-MIMO Wi-Fi System, Orbi Router + Orbi Satellite, Tri-Band AC3000, 4 x Gigabit LAN, |
|
Switch |
Ubiquiti UniFi Switch US-8-150W, 8-Port Gigabit Managed PoE+ Switch, with 8 x PoE/PoE+ (Max 150W) and 2 x SFP Rackmountable, Fanless, Passive 24V & 802.3af/at |
|
UTP cable |
Cat45 |
|
Auckland |
|
|
18 PC |
HP Z240 SFF i5-6500 3.2GHz 8GB DDR4 1TB Win7Pro |
|
Router |
Netgear Orbi RBK50 MU-MIMO Wi-Fi System, Orbi Router + Orbi Satellite, Tri-Band AC3000, 4 x Gigabit LAN, |
|
Switch |
Ubiquiti UniFi Switch US-8-150W, 8-Port Gigabit Managed PoE+ Switch, with 8 x PoE/PoE+ (Max 150W) and 2 x SFP Rackmountable, Fanless, Passive 24V & 802.3af/at |
|
Tauranga |
|
|
4 PC |
HP Z240 SFF i5-6500 3.2GHz 8GB DDR4 1TB Win7Pro |
|
2 Routers |
Netgear Orbi RBK50 MU-MIMO Wi-Fi System, Orbi Router + Orbi Satellite, Tri-Band AC3000, 4 x Gigabit LAN, |
|
2 Switches |
Ubiquiti UniFi Switch US-8-150W, 8-Port Gigabit Managed PoE+ Switch, with 8 x PoE/PoE+ (Max 150W) and 2 x SFP Rackmountable, Fanless, Passive 24V & 802.3af/at |
|
2 Servers |
Intel 7th Gen Core i7 7700 3.6Ghz Quad Core/ 16 GB DDR4 RAM |
d) Explain the WAN diagram in terms of how the branches network are connected and justify your choose of network devices and components for each branch.
As I observed, most of the connection is being done by the VPN connections. Like Napier and Christchurch, they are equipped with router-to-router VPN connections. Through this, it’s very easy to connect from branch to main office. Also with the Auckland and Tauranga they are also using VPN that can stay connected 24/7 a day. It is also equipped with T1 connection that allows them to have a smooth transition experience. For me the most important device is the Router. Through this all the connections of all branches is possible (Intranet and Extranet VPN Business Scenarios, 2007).
e) Provide a scenario explaining how a branch will connect to the company main office.
This company is already expanding. In fact it has already 4 branches across the country. So for this the company will make sure that all employees can have access to all network resources that they need in order to perform their job effectively. With this, it is very important also to assure the security of creating the path on how you connect it. By the use of site-to-site VPN, it will create a path called tunnel between two sites via internet. This will allow the branches to access the file servers at the main office. The data being transfer are all encapsulated so you’re both protected as you send and receive data.
f) Provide a scenario explaining how a business partner will access the extranet.
The business partner is one of the most valuable parts in any organization. We should care and provide good communications to create a good bond. In order to make this happen, the Main office and the business partner should be connected through a secure IPSec tunnel (VPN), then allowing the business partner to access the Main office’s file server to perform their various tasks, like updating and monitoring the product stocks (Intranet and Extranet VPN Business Scenarios, 2007).
“Using the diagram that you created before, answer the following questions”
a) Create a routing table for every branch if applicable.
This routing table is from Christchurch branch, where it has 5 PC.
|
Destination |
Subnet Mask |
Gateway |
Interface |
Metric |
Protocol |
|
192.117.3.2 |
255.255.255.0 |
192.117.3.1 |
Local Area Network |
1 |
Local |
|
192.117.3.3 |
255.255.255.0 |
192.117.3.1 |
Local Area Network |
1 |
Local |
|
192.117.3.4 |
255.255.255.0 |
192.117.3.1 |
Local Area Network |
1 |
Local |
|
192.117.3.5 |
255.255.255.0 |
192.117.3.1 |
Local Area Network |
1 |
Local |
|
192.117.3.6 |
255.255.255.0 |
192.117.3.1 |
Local Area Network |
1 |
Local |
b) Which protocol or protocols should be used to ensure the routing tables are correct and working.
There are 3 types of Routing Protocols
- Static
- Default
- Dynamic
Static – This type of protocol is being done my manual configurations. Each destination is all configured manually, like configuring the known destination and subnet mask.
Default – In this protocol, the main feature is to send packets into unknown network destination. (Not in routing table) and it has also one exit port.
Dynamic – This protocol caters all the features that able find and update routing tables on routers. This is very efficient to use because it will directly connect all known networks and send/receive data between two routers.
I choose the Dynamic protocol, because as you can see it is packed with all the good features that very useful and convenient to use. In this protocol you can save more time and resources(Academy, 2014).
References:
Academy, C. N. (2014, March 24). Cisco Networking Academy’s Introduction to Routing Dynamically. Retrieved from http://www.ciscopress.com: http://www.ciscopress.com/articles/article.asp?p=2180210&seqNum=7
Academy, C. N. (2014, March 24). Cisco Networking Academy’s Introduction to Routing Dynamically. Retrieved from http://www.ciscopress.com: http://www.ciscopress.com/articles/article.asp?p=2180210&seqNum=7
Intranet and Extranet VPN Business Scenarios. (2007, August 3). Retrieved from http://www.cisco.com: http://www.cisco.com/c/en/us/td/docs/security/vpn_modules/misc/Archive_-6342/6342cmbo.html#wp1057569
Academy, C. N. (2014, March 24). Cisco Networking Academy’s Introduction to Routing Dynamically. Retrieved from http://www.ciscopress.com: http://www.ciscopress.com/articles/article.asp?p=2180210&seqNum=7
Intranet and Extranet VPN Business Scenarios. (2007, August 3). Retrieved from http://www.cisco.com: http://www.cisco.com/c/en/us/td/docs/security/vpn_modules/misc/Archive_-6342/6342cmbo.html#wp1057569
Intranet and Extranet VPN Business Scenarios. (2007, August 3). Retrieved from http://www.cisco.com: http://www.cisco.com/c/en/us/td/docs/security/vpn_modules/misc/Archive_-6342/6342cmbo.html#wp1064626
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


