Methods for Cybersecurity
| ✅ Paper Type: Free Essay | ✅ Subject: Information Systems |
| ✅ Wordcount: 1970 words | ✅ Published: 18 May 2020 |
INFORMATION SYSTEM
Data framework (IS) a framework that give the data which is essential to deal with an association all around adequately. Information frameworks (IS) are the methods by which individuals and associations, progressively using innovation, accumulate, process, store and scatter data.
A data framework as “a framework wherein human members as well as machines perform work (procedures and exercises) utilising data, innovation, and different assets to create enlightening items or potentially benefits for inner or outer clients (Geiger, Rosemann, Fielt and Schader 2012).
CYBER SECURITY
Cybersecurity is that the act of securing frameworks, systems, and comes from advanced assault. These cyberattacks are typically gone for getting to, changing, or pulverising delicate data; coercing cash from clients; or interfering with ordinary business forms (Von Solms and Van Niekerk 2013). Cyber security is that the insurance of internet associated frameworks as well as instrumentality, programming and information from cyber-attacks. See below figure…
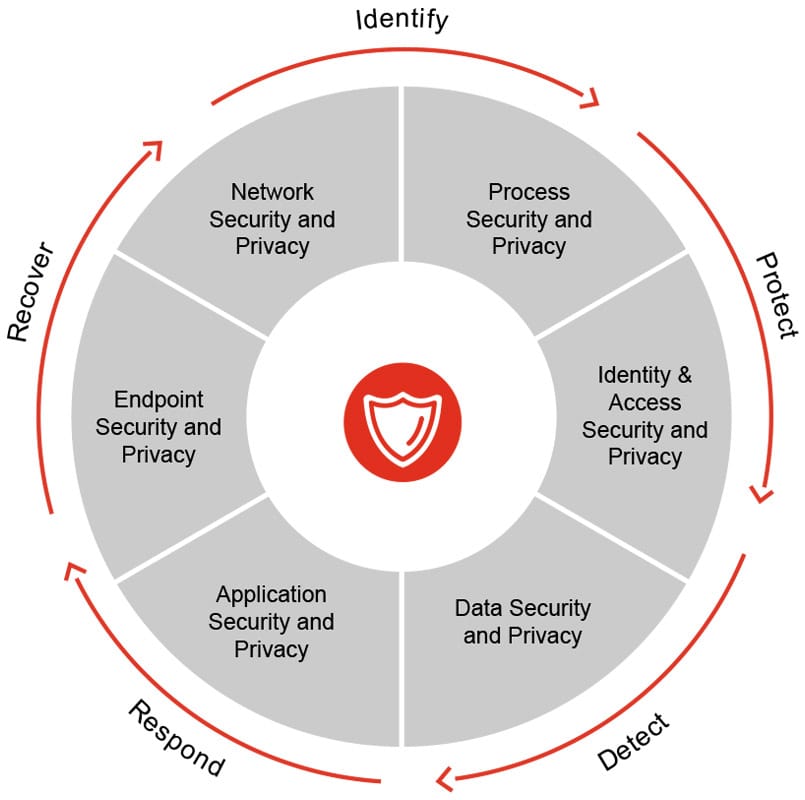
Figure: cyber security
CURRENT TREATEMENT OF CYBER SECURITY
There are numerous methods which associations are doing and they can do to shield their business from cyberattacks. The European Union agency for cyber security (ENISA) is working in Europe from 2004 and all the countries in European Union have a National cyber security strategy (NCSS). This strategy helps them to tackle risks. (European Union agency for cyber security 2018)
According to European Union agency for cyber security (2018) ENISA’s work in supporting these techniques has concentrated on the investigation of existing NCSS; on the advancement and execution of NCSS; on laying out and bringing issues to light of good practice to give direction and pragmatic apparatuses to the Member States for assessing their NCSS. Refreshed NCSS Good Practice Guide (New!)
- NCSS: An Implementation Guide
- National Cyber Security Strategies
- An Evaluation Framework for NCSS
- Motivating forces and hindrances of the digital protection advertise in Europe
- Digital Insurance: Recent Advances, Good Practices and Challenges (New!)
A typical goal of each European national digital security procedure is joint effort to improve digital security over all dimensions, from risk data sharing to mindfulness raising. Joint effort is frequently accomplished through two formal structures: Information Sharing and Analysis Centers (ISACs) and Public Private Partnerships (PPPs).
Ways to make cyber security strategic within organisation:
- Staff preparing
Assailants are sharp about finding a point of section into your frameworks and system. This could be a clueless worker with feeble passwords or who falls for a phishing or social designing endeavor. Ensure your group knows how cybercriminals can deceive them, how to recognise a suspicious email or telephone call, particularly those that appear to be authentically from companions or another office. Prompt them on the most proficient method to shield the association from these endeavors.
- Keep programming refreshed
According to Arora & Juneja (2019) any product used by organisation ought to be the most recent rendition. Old applications are helpless to zero-day adventures and assaults, which can take data, infiltrate systems, and cause extreme harm. While hostile to infection programming routinely reports without anyone else, different projects might not have this capacity. Routinely check all significant programming on in any event an every other week premise.
- Nonstop danger checking
Assaults can occur whenever and from anyplace. Actualise 24X7 checking abilities to remain always cautious and catch assaults before they can cause harm. Security Event and Incident Monitoring (SEIM) programming can caution you to suspicious client movement or information peculiarities that may demonstrate an assault is in progress. Security Operations Center administrations can give extra help as security investigators prepared in deciphering the cautions and homing in on the ones that sign inconvenience (Arora & Juneja 2019).
- Physical security
As a rule, aggressors access login qualifications, exchange mysteries, foundation schematics and other significant and exploitable data by being nearby and increasing physical passage into structures or server farms.
Utilise security best practices like badged entryway passage, camera reconnaissance and a strategy of regulating guests. Keeping calls and discussions, just as screens, private while in these outer situations are only a couple of tips to think about when your faculty are outside of the ensured bounds of the home office.
- Outside digital knowledge
According to Arora & Juneja (2019) while it’s significant to utilise cybersecurity evaluations to continually search for your vulnerable sides, and it is fundamental that you execute capacities to always screen your frameworks, systems and condition for interruptions or suspicious movement, it is similarly critical to screen the outer systems and scenes that could affect you. Digital knowledge is a significant segment of a powerful cybersecurity program. Through Dark web observing and other digital knowledge strategies, you can pick up understanding into assaults that might be in the arranging stages, the criminal systems prone to target you and how they intend to do it.
- Be careful with equipment burglary
Finally, if your organisation utilises cell phones –, for example, workstations, tablets or different gadgets through a BYOD approach – have an approach to remotely ensure information. In the most ideal situation, you should follow gadgets. In the most pessimistic scenario, shutdown login capacities if a gadget is stolen. At least, guarantee that encryption is utilised to ensure the data that the gadget may contain (Arora & Juneja 2019).
- The best method to introduce security into an organisation is to create an Information Security Steering Committee, made up of security and business management. According to Lincke (2018) first, an organisation chart will identify potential key players that should be befriended. Various stakeholders are interviewed to determine important assets, threats, security issues and security regulation. These issues are combined into a Security Issues document. Many of the key people expressing interest and concern can be invited to become part of the Information Security Steering Committee. This committee can then develop a set of Security Policies from the Security Issues, which are presented to management for review and approval. Once approved, the steering committee uses the Security Policies to develop security training materials and compliance test plans. After cycling through training and testing, the steering committee can perfect training and testing materials. See below figure…











- SCCDocumentation
- Meeting partners (HR, legal, finance) to decide association issues and concerns.
- Security issues
- Develop security policies for endorsement to Mgmt.
- Training materials

- Info security
- steering committe
- Security policies
 e
e
- Direct security preparing and test for consistence.

- Improve guidelines develop consistence checking system.
Figure: Introducing security to an organisation Lincke (2018)
The factors or circumstances that need to be considered are discussed below:
(1). Putting resources into Your People
There are dangers coming explicitly for your representatives, so there are numerous new arrangements and methodology to acquaint with them as a piece of your cybersecurity procedure – framework access and benefits, proper use, logging strategies, new devices. Your representatives need to comprehend what the majority of this implies and how to secure themselves. You never need your cybersecurity technique to be undercover, confounding, or unengaging; this will leave your group uninterested and unmotivated to help the activity.
A cybersecurity procedure should likewise include preparing. Security mindfulness is your first line of resistance, so put resources into significant, drawing in, predictable preparing. For those colleagues who are an indispensable piece of your cybersecurity methodology, give fitting proficient improvement to stay up with the latest on strategies and procedures that could be utilised against new dangers.
(2).The organisations build up a cybersecurity program that secures touchy client data and the privacy, uprightness, and accessibility of organisations’ data innovation frameworks. NIST, PCI DSS, entrance testing, merchant consistence evaluations – these are for the most part reactions to the manners in which data frameworks are amazingly interconnected and how associations can ensure their information, system, frameworks, and resources ( Lincke 2018).
As new apparatuses, prerequisites, and structures become accessible, assess which ones apply to your association or which you ought to consider being tried against. A solid cybersecurity activity necessitates that your group know how businesses and controllers are reacting to cybersecurity dangers.
Recommendations
It is recommended that cybersecurity is made strategic in organisations. Below are specific recommendations to help achieve this.
1. Utilise a firewall
One of the principal lines of barrier in a digital assault is a firewall. The Federal Communications Commission (FCC) suggests that all SMBs set up a firewall to give a hindrance between your information and cybercriminals. Notwithstanding the standard outside firewall, numerous organisations are beginning to introduce interior firewalls to give extra security. It’s likewise significant that representatives telecommuting introduce a firewall on their home system too. Consider giving firewall programming and backing to home systems to guarantee consistence (Segal 2019).
2. Report your cybersecurity strategies
While private companies regularly work by listening in on others’ conversations and intuitional information, digital security is one region where it is basic to archive your conventions. The Small Business Administration (SBA’s) Cybersecurity entry gives internet preparing, agendas, and data explicit to ensure online organisations.
The FCC’s Cyber planner 2.0 gives a beginning stage to your security archive. Consider likewise taking an interest in the C3 Voluntary Program for Small Businesses, which contains a nitty gritty toolbox for deciding and archiving digital security best practices and digital security approaches (Segal 2019).
3. Instruct all representatives
Representatives regularly wear numerous caps at SMBs, making it basic that all workers getting to the system be prepared on your organisation’s system digital security best practices and security arrangements (Segal 2019).
Since the arrangements are advancing as cybercriminals progressed toward becoming savvier, it’s fundamental to have normal reports on new conventions. To consider workers responsible, have every representative sign a record expressing that they have been educated regarding the approaches and comprehend that moves might be made whether they don’t pursue security strategies.
4, Enforce safe secret word rehearses
Indeed, workers observe changing passwords to be a torment. Notwithstanding, the Verizon 2016 Data Breach Investigations Report found that 63 percent of information breaks occurred because of lost, stolen or frail passwords. As indicated by the Keeper Security and Ponemon Institute Report, 65 percent of SMBs with secret word strategies don’t implement it. In the present BYOD world, it’s fundamental that all representative gadgets getting to the organisation system be secret phrase ensured (Segal 2019).
5. Introduce hostile to malware programming
According to Segal (2019) It’s anything but difficult to expect that your workers know to never open phishing messages. In any case, the Verizon 2016 Data Breach Investigations Report found that 30 percent of workers opened phishing messages, a 7 percent expansion from 2015.
Since phishing assaults include introducing malware on the representative’s PC when the connection is clicked, it’s basic to have against malware programming introduced on all gadgets and the system. Since phishing assaults frequently target explicit SMB worker jobs, utilise the position-explicit strategies laid out in the Entreprenuer.com article “5 Types of Employees Often Targeted by Phishing Attacks” as a feature of your preparation.
6. Use multifaceted ID
Despite your readiness, a representative will probably commit a security error that can bargain your information. In the PC Week article “10 Cyber Security Steps Your Small Business Should Take Right Now,” Matt Littleton, East Regional Director of Cybersecurity and Azure Infrastructure Services at Microsoft, says utilising the multifaceted recognisable proof settings on most real system and email items is easy to do and gives an additional layer of insurance. He suggests utilising workers’ cell numbers as a subsequent structure, since it is far-fetched a criminal will have both the PIN and the secret phrase (Segal 2019).
References:
- Arora,Y. and Juneja,S.,2019 ‘Cyber security-Are we really safe?’, Journal of applied science and computations, vol. 6, no. 5, pp. 258-260
- European Union agency for cyber security, 2019, National cyber security strategies, viewed 2019, https://www.enisa.europa.eu/topics/national-cyber-security-strategies?tab=publications
- Geiger, D., Rosemann, M., Fielt, E. and Schader, M., 2012. Crowdsourcing information systems-definition typology, and design.
- Lincke, S., 2015. Security planning: an applied approach. Springer.
- Segal, C., (Cox blue, the intersection of business, growth and technology) 2019, Cyber security best practices for business, viewed 2019, https://www.coxblue.com/8-cyber-security-best-practices-for-your-small-to-medium-sise-business-smb/.
- Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber security. Computers & security, 38, pp.97-102.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


