Radio-frequency identification (RFID) Technology
| ✅ Paper Type: Free Essay | ✅ Subject: Engineering |
| ✅ Wordcount: 3534 words | ✅ Published: 18 May 2020 |
Radio-frequency identification (RFID) technology
Abstract:
To improve the tracking of raw materials and inventory and due to the reducing cost of microchips, interest of retailers and manufacturing companies in the Radio-frequency identification (RFID) is increasing. Starting with the introduction of RFID systems, this article presents definition of what RFID is and its types. Followed by the applications of RFID in present time and its structure.
Introduction:
In this article, we speak about the ever evolving technology that is considered to be one of the most awaited systems especially across the engineering and construction industries called Radio frequency identification (RFID) technologies which will putatively transform all the processes (Goodrum, et al., 2006). Radio frequency identification (RFID) systems have also been acknowledged by practitioners and academicians. It provides authentic data without human interference by basically acquiring the data and storing it using different methods (Koschan et al., 2006). Out of several methods of identification, most common method that is in use is attached to antenna on a microchip (RFID Journal, n.d.). Additionally, Smith (2005) emphasizes that it also has the potential to remove all the barriers associated with controlling the supply chain of the business. There is plenty of benefits RFID technology promises to offer in the supply chain industry. i.e., improved speed, accuracy, efficiency and security of information sharing across the supply chain (Jones et al., 2004).
Additionally, it can also be used for the tracking of documents like the library or legal files (Colling, 2004), and to track and manage pharmaceutical drugs at hospitals and labs (McGee, 2004). It has been identified that the RFID technology is majorly used in the retail sector. Although RFID technology has a lot of potential to offer, it does come with some limitations which will be discussed further in the report.
Definition (What is RFID):
RFID is an acronym of the technology referred to as Radio frequency identification which predominantly uses radio waves to automatically identify people or objects (RFID Journal, n.dd). RFID utilises electromagnetic pulses to consequently distinguish and track labels connected to objects. Information is stored in the tags electronically.
Stockman suggested the first Radio frequency identification (RFID) technology in showcasing the need to analyze the appropriate technology for, “reflected- power communication” (Goodrum et al, 2006). First commercial use of RFID technology took place in the 1990s while it was used for electronic toll collection on US highways in several states (AIM, 2002).
Basically, RFID and barcode technology is identical while tracking the inventory, still, RFID offers extra benefits over barcode system in certain situations:
– The direct sight of code is not required in RFID.
– Updation of data possible in real-time.
– RFID requires a power source while bar codes only need the machine to read the barcode. (Rouse, 2007)
According to Roberts (2006), RFID technology commonly contains three things:
(1) An RFID device;
(2) A tag with an antenna and transceiver; and
(3) A connection to the organization’s system.
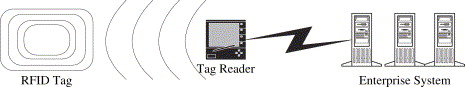
Fig. 1 RFID System (Source: Robert, 2006)
Types of RFID:
RFID consists of two types: (1) Active RFID System (2) Passive RFID System.
Firstly, in the Active RFID Systems, tags utilise their own transmitter and a set of batteries for effective use. Due to the onboard set of batteries, the range of Active RFID system increases greatly in comparison to Passive systems (Goodrum, 2006).
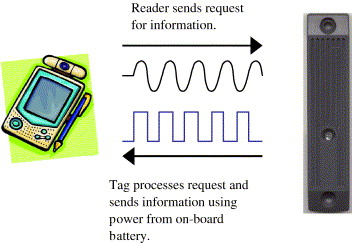
Fig 2. Active RFID system
(Source: Goodrum, 2006)
This technology has a great range which extends up to 100 m in several cases. The main purpose of using the Active tags are to access and track large equipments or assets like machines or vehicles. Due to its usability for large assets, Active tags comes at very high cost in comparison to the Passive RFID tags and not many organisations can afford to have such technologies (Lowry Solutions, 2014).
On the contrary, passive tags are much less expensive and small in size. Most of it is because it receives data from reader which removes the need of batteries.
Fig 3. Passive RFID system
(Source: Goodrum, 2006)
Jaselskis and El-Misalami (2003) examined that passive RFID systems were more sturdy in comparison to barcodes but also found a drawback of system requiring the reader to be within a certain range of the tag. Further details of both active and passive RFID are discussed in the structure section of the article.
How RFID works:
Basically, The RFID reader devices emits electromagnetic waves at a certain frequency, at that time, the RFID tags in the operational area will sense these electromagnetic waves and then transmit information back to the RFID reader device, also with this way, the RFID tags could retrieve power from the RFID reader through electromagnetic waves. From there, the RFID reader knows which tags are in its operational area. The principles of operation can be illustrated in the graph below (Vinod & Mohan 2018).
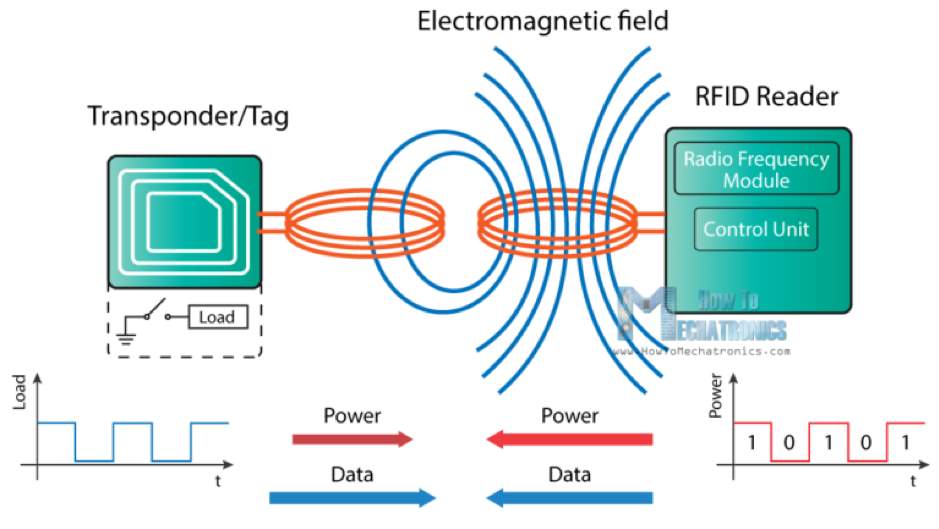
Figure 2: how RFID system works.
As stated previously, the RFID reader is a combination of a radio frequency module, controller and antenna coil that creates frequency electromagnetic field. On the other hand, the RFID tags are usually a passive component, consisting only of antennas and electronic circuits. Due to the induction, when those RFID tags near the electromagnetic field, a voltage is generated in the antenna coil and voltage serve as the power source for the tags. Now when the tag is powered, it can extract the information transmitted from the reader and send the message back to the reader, using a technique called “download operation”. Turning on or off the load on the antenna of tags will affect the power consumption on the reader’s antenna. This can be measured as a voltage drop and the voltage change will be recorded as 0 and 1. That is how the data is transmitted from the tags to the readers. There is also another way of transmitting data between readers and tags, called “backscatter coupling”. In this case, the tag uses parts of the received energy to create another electromagnetic field that will be chosen by the reader’s antenna. Hence, to communicate between readers and tags, the RFID system uses protocols called “air-interface” protocols. Additionally, there are many standards for those protocols depending on type of the RFID system used. According to Roberti (2013), there are 6 common air-interface protocol standards which ratified by the ISO (International Organization for Standardization) are being used: ISO 14443, ISO 15693, ISO 18000-3, “Near Field Communication”, ISO 18000-6C, ISO 24730. Firstly, ISO 14443, this is HF (high frequency) standard, which created for secure payments purpose. Since this standard is built for proximity cards (or tags), it is designed to have short read range and encryption included. Secondly, ISO 15693, developed for vicinity tags and is HF standard also. Compares to ISO 14443, there is no encryption and longer reading range with ISO 15693. It is considered being used in many access control systems such as inventory management. Thirdly, ISO 18000-3, a HF standard, established for item management only, but the goal has never been achieved because enterprises like to use ISO 15693 for item management purposes. Next one, NFC, which stands for Near Field Communication, although not an official ISO standard, NFC is based on ISO 14443 with some enhancements, such as mirror tags from readers ability. Moreover, it is acknowledged that with an NFC enabled mobile phone, people can enter the building because ISO 15693 incorporated with NFC over the time. Penultimately, ISO 18000-6C, this is the ultra-high frequency (UHF) standard. This standard is based on EPCGen 3 air-interface protocol. Furthermore, it is considered that ISO 18000-6C is mostly used although there is ISO 1800-6A and ISO1800-6B. lastly, ISO 24730, operating at 2.45GHz, this protocol controls the communication of the active RFID tags and usually used in location system with real-time supported.
Structure of RFID:
Over many years of development. An RFID system typically is a combination of 2 main components: RFID tag (or device or smart label) and tag reader (AB&R). Generally, the tag reader is equipped with an antenna and transceiver so that they can read the tag, and an RFID tag is usually equipped with silicon chip (some RFID tag also being equipped with antenna). Similarly, it is believed that the memory of RFID chip may stores to 512 bits of data, and it can communicate with the reader through radio waves with the distance from 0.5 to 30 metres. However, according to Roberts (2006), there is one more component should be listed on an RFID system is a host system or a connection that connects to a business system. The figure below is how Roberts demonstrates an RFID system’s components.

Figure 3: an RFID system.
Additionally, it is good to noted that, an RFID tag is divided by 2 big categories: powered tag and unpowered tag. Which means tag with power supply (or so-called battery) and tag without power supply. Furthermore, an RFID tag with battery, or powered tag that actively transmitted signal to reader is also known as transponder (transponder is a combination of 2 words: transmitter and responder). On the contrary, the unpowered tag (without power supply) is also known as just “tag” itself. However, on these days, the commonly used of RFID technologies have called transponder as “active tags” and the tag without power supply as “passive tags”. Typically, the differences between the 2 kinds of tag are acknowledged as active tags can read and write while passive tags are read only. Other points to distinguish those tags are their size and their value, usually, those active tags are larger (noted that both active and passive kind of tags are pretty small, about a few centimetres) and more expensive than passive tags. At this point, it is acknowledged that there are a massive variety of tag’s shape, size, and protective case depending on different purposes. For instance, the animal tracking tag is very tiny, just approximately 0.5-millimeter radius and 10 millimetres long and most of the case, it is injected under the animal’s skin. Comes to the life of tags, differs from passive tag, active tag has a limit of lifetime depends on its battery, with the current battery technologies, it is considered that the active tag might survives for at least 5 years and 10 years at the most. In contrast, passive tag has no limitation of its life, also lighter, smaller and less expensive (Roberts 2006). Yet, it is proven that passive tags have limitation in their storing ability of data, shorter reaching ability to the reader and more power reader required as a trade-off for the unlimited lifetime. More importantly, performance of passive tags is diminished as the increased of “noisy” environment (the interference). On the other hand, there is a different kind of RFID tag that pulls power from the reader for its communication but use battery for operating the chip’s circuitry. That kind of RFID tag named “semi-passive tags”.
Application of RFID:
The RFID technologies have a widely implementations in many different industries such as inventory management, asset tracking, personnel tracking, controlling access to restricted area, ID badging, supply chain management or counterfeit prevention. However, the most significant applications are implemented in the management and warehousing fields. To illustrate, to solve the cold storage temperature monitoring problems, the manufacturers have attached the temperature monitoring RFID tags on their products. These tags then transmit data to the readers, after that, the readers will continuously push gathered data to enterprise system then stored. From that, it gives the manufacturers the ability to access from the internet at anywhere, anytime in order to track their goods. Apart from this, one of the most common implementations of this technology is to prevent lost of goods in supermarkets or retail stores. For example, RFID device (RFID tag) attached to the goods together with reader device and antenna which are mounted at the control bases (usually putted at the entrance or exit door), if any unmounted chip (RFID tag) passes through the control bases, the reader device then can easily read and identify, then issues a warning or usually an alarm sound will goes off. Also, it is possible to use an RFID tag implanted beneath pet’s skin to identify their origin or to avoid from loss and theft by tracking them. In the library, RFID tags are attached to books to reduce the time taken from searching and inventory with a view to prevent book theft. Some fields are capable of using a large number of RFID tags such as smart cards, identity cards, electronic passports, goods in supermarkets, luggage management in aviation, public transport systems, the garment industry, and footwear. In some developing countries such as Vietnam, one application of RFID technology that well-known is creating smart lock for motorbike in order to prevent the owner’s vehicle lost from thieves.
As a consequence, RFID usage could be classified into four different categories because of the distinct purposes, there should be 4 classes of usage: EAS (Electronic Article Surveillance), portable data capture, networked systems and positioning systems (Robert 2006). For the first category, EAS, this is the most common use for anti-theft devices and widely used in the supermarkets or retail stores. This might be because the presence or absence of the objects could be noticed by the systems, and in order to detect the existence of objects, people use 1-bit systems to “feel” objects’ attendance. By this way, the tags are attached to objects which are clothing, food or goods people have to pay for it. Before tags deactivated, if things attached with tags go through the control station (usually located near the entrance or exit door), the alarm will be triggered. Because of its widely use, it could be easily seen at many retail stores like clothing (Zara), appliances (Smith), electrical devices (JB Hi-fi). Next, the second category is portable data capture, this commonly use in the scientific studies or similar. With the variety of data needed to capture, people use portable devices, attached with tags which may incorporate with sensors to capture the indexes, for instances, capture radiation value, movement tracking, temperature monitoring, etc. Moreover, those portable devices can store gathered data for later use, for example, downloading and analyzing recorded information. The third category, networked systems, mostly used in inventory management or asset tracking fields. To point out the characteristics of this systems, there are basically two components: fixed location readers at predetermined places and RFID tagged objects. Normally, this system directly connected with the company’s system and those RFID readers have the mission to track the movement of the objects, then transmit the data recorded from objects to business’ systems. For the last category, positioning systems, as can be seen from those applications above, the RFID systems could be used for automatic tracking the objects. To demonstrate, in order to provide locations automatically and support navigational systems, objects which can be vehicles, animals, pets or even human are tagged with RFID tags.
PROS AND CONS
With all of the applications stated before, there are many advantages and disadvantages have been recorded.
Pros: (Numbering to make it clear)
First, the scanning process of RFID does not require “line of sight”, which means it opposes to barcode labels. Compared to barcode labels, the barcode scanner (some are fixed position) must be given a clear sight of barcode to process a reliable scan. Moreover, RFID systems can read their tags without caring about direction of tags (orientation can be up or down, front or behind, etc.) while with barcode labels, employees have to reposition the packets for the barcode reader to read. Also, RFID reader can reader multiple tags at the same time, which saves a huge time for business.
Second, labor cost reduction, it is believed that 50% to 80% of costs could be accounted for labor, especially in distribution center (Michael & McCathie 2005). With the implementation of RFID systems, enterprise could handle the whole processes (such as inventory management) in just a few minutes with a few employees.
Third, according to Furlong (2017), she stated that RFID systems might help enterprise to increase the transparency of inventory by providing real-time updates and cut down time from scanning process. The problem from barcode system which is goods are leaving the facility without being scanned now have been solved with RFID systems. RFID readers placed at doorway can provide exactly the import or export timestamp of goods.
Fourth, optimize inventory management, for enterprise that uses automatic pallets, RFID provides a solution for loss and theft reduction by tracking items across the supply chain.
Fifth is, RFID can store more data compared to the traditional barcode (linear barcode). For barcodes, a serial number represents a limited database. For RFID tags, there are different types of data with large amount can be stored and even readable from remote stations.
Finally, the RFID tags have longer durability than barcode labels. The impact of weather could affect the barcode labels’ quality. For example, sunlight might cause the barcode to fade away, or barcode might fall out by the affection of rain. Nowadays, RFID tags are not only weatherproof, it is acknowledged that they are also withstand in harsh environments such as chemical baths or autoclave cycles.
Cons:
The biggest disadvantage of RFID systems is its cost. That is, barcode systems are dramatically less expensive. It is considered that RFID systems commonly used for higher value goods. However, a careful ROI analysis could give the answer for the question should or should not.
Another problem of the RFID systems is the interference problems. If the tags are deployed in such a dense magnetic environment or environment that contains a lot of liquid, business could be required different types or more expensive tags.
To achieve the required visibility, enterprise might need the cooperation from all departments, and it would cost an enormous amount of expense. For instance, to reach the required visibility, all of your facilities may need to be able to read the tags, and it might require collaboration from suppliers, customers, or transportation department.
Apart from that, the data management of RFID systems becomes more and more difficult. This is the other side of the greatness of RFID systems’ traceability data. An expert solution may be required to get the center systems avoid from bombarded by superfluous information.
Lastly, the integration capabilities of the RFID systems. If an enterprise plans to track its goods internationally by using RFID systems, different types of systems in different geographies may needed when deploying because of the standards across countries.
Conclusion
With some planning and forethought, RFID could potentially provide a means to improve inventory visibility and optimization. Carefully weigh the benefits and potential challenges before making a decision about how to use the technology in your inventory operations.
References:
- Association for Automation Identification and Data Capture Technologies (AIM) (2002), Shrouds of Time: The History of RFID. http://www.aimglobal.org, Last accessed September 24, 2019.
- Collins, J. (2004a), “RFID brings order to the law”, RFID Journal, July 7, available at: www.rfidjournal.com/article/ articleview/977/1/4/ (accessed September 24, 2019)
- Goodrum, P.M., McLaren, M.A. and Durfee, A., 2006. The application of active radio frequency identification technology for tool tracking on construction job sites. Automation in Construction, 15(3), pp.292-302.
- Journal, R. (n.d.). RFID Frequently Asked Question – RFID Journal. [online] Rfidjournal.com. Available at: https://www.rfidjournal.com/faq/show?49 [Accessed 26 Sep. 2019].
- Jones, P., Clarke-Hill, C., Shears, P., Comfort, D. and Hillier, D. (2004), “Radio frequency identification in the UK: opportunities and challenges”, International Journal of Retail & Distribution Management, Vol. 32 No. 3, pp. 164-71.
- McGee, M. (2004), “Health-care I.T. has a new face”, InformationWeek, May 10, p. 16.
- Koschan, A., Li, S., Visich, J.K., Khumawala, B.M. and Zhang, C., 2006. Radio frequency identification technology: applications, technical challenges and strategies. Sensor Review.
- Smith, A.D., 2005. Exploring radio frequency identification technology and its impact on business systems. Information Management & Computer Security, 13(1), pp.16-28.
- Jaselskis, E.J. and El-Misalami, T., 2003. Implementing radio frequency identification in the construction process. Journal of Construction Engineering and Management, 129(6), pp.680-688.
- RFID Journal frequently asked questions, http://www.rfidjournal.com.
- Solutions, L., (2014). What Are the Different Types of RFID Technology?. [online] Lowry Solutions. Available at: https://lowrysolutions.com/blog/what-are-the-different-types-of-rfid-technology/ [Accessed 26 Sep. 2019].
- Roberts, C.M., 2006. Radio frequency identification (RFID). Computers & security, 25(1), pp.18-26.
- Rouse, M. (2007). What is RFID (radio frequency identification)? – Definition from WhatIs.com. [online] IoT Agenda. Available at: https://internetofthingsagenda.techtarget.com/definition/RFID-radio-frequency-identification [Accessed 24 Sep. 2019].
- Cited by Chris (we have to re-order it later): Ok done.
- AB&R, What is RFID and how it works?, viewed 20/09/2019, <https://www.abr.com/what-is-rfid-how-does-rfid-work/>.
- Furlong, J 2017, RFID for Retail: Know the Pros and Cons, viewed 23-09-2019, <https://www.business.com/articles/rfid-for-retail/>.
- Michael, K & McCathie, L 2005, ‘The pros and cons of RFID in supply chain management’, in International Conference on Mobile Business (ICMB’05), pp. 623-9.
- Roberti, M 2013, What Protocols Are Used to Communicate Between an RFID Reader and a Tag?, RFID Journal, <https://www.rfidjournal.com/blogs/experts/entry?10795>.
- Roberts, CM 2006, ‘Radio frequency identification (RFID)’, Computers & Security, vol. 25, no. 1, pp. 18-26.
- Vinod, D & Mohan, A 2018, ‘A Successful Approach to Bus Tracking Using RFID and Low Power Wireless Networks’, in TENCON 2018 – 2018 IEEE Region 10 Conference, pp. 1642-6.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal




