Types of Cyber Attacks and Mitigation Strategies
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 1776 words | ✅ Published: 23 Sep 2019 |
Technical Research Paper
Report
Contents
IP Spoofing: Assuming the identity
Man in the Middle attack using Packet Sniffers
Cross Site Scripting (XSS Attack)
Network layer Secure socket layer
Session ID generated by server
Attack
An attack is a security threat to the computer systems and its can be attacked through different ways of attack. Attacks take place to alter add or delete and fetch information from the network through unauthorized access. It is major vulnerability in information technology. This is also called cyber-attack. It can target computer systems, networks, infrastructure as well as the personal systems. [1]
Types of Attack
Attacks are of different kinds and the most common cyber-attacks are:
- Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks
- Man-in-the-middle (MitM) attack
- Phishing and spear phishing attacks
- Drive-by attack
- Password attack
- SQL injection attack
- Cross-site scripting (XSS) attack
- Eavesdropping attack
- Birthday attack
-
Malware attack
TCP Attack
TCP attack is known as Man in the Middle attack. IP spoofing is a technique which is used by attackers for hiding their IP and replacing it with random IP address which makes them untraceable. The man in the middle attack hits the transmission channel and steals the information or alter it for its own personal use or to harm any organization or the society. [1,2]
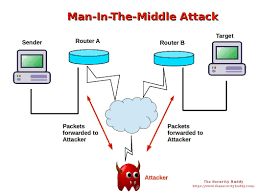
A TCP Hijacking is like a two-phased man-in-the-middle attack where the attacker waits in the circuit between a client and a server to get the information of the port and sequence number which is used in the connection. TCP hijacking is when an unauthorized user hijacks a network connection of another user for example the attacker monitors the network transmission and analyzes the source and destination IP addresses of the two computers once the attacker discovers the IP address of one of the users the attacker can knock one of the users off their connection using a denial service attack or other types of attack and then resume connection by spoofing the IP address of the disconnected user the other user is tricked into thinking that he is still talking to the same legitimate user when they actually he’s not to prevent this type of attack you can install some sort of encryption mechanism such as an IP security IP security works at the internet layer it secures the IP including everything within the IP packets data field IP security is a gold standard for virtual private network security it gives protection to both transport layer and application layer messages here’s an example of TCP IP hijacking so first you have system a who’s communicating with system B at this IP address of 192.168.0.0 zero and the system B IP address of 192.168.0.0 so as you can see in the TCP header you have your source destination sequence number acknowledgment number and length so the source is system at the destination is system B and over here you have the TCP header for packets going to system a from system B source system B destination system a again sequence number acknowledged among acknowledged mint number and length but here you have the attacker system by hijacking the session here the source has system a when naturality is sits the attacker system the destination going to system B and so that’s what TCP hijacking is he hijacks the IP address of the source pretending to be system a when naturally assists as the attacker stem and so system B will communicate with the attacker system unaware that actually again communicating with the attacker system and not with actual system.
TCP Hijacking
A TCP/IP hijack is an attack that spoofs a server into thinking it is talking with a valid client, when in fact it is communicating with an attacker that has taken over (or hijacked) the TCP session. TCP session hijacks can be implemented in two different ways: Middle Man
Attack and the Blind attack. This is basically done using the following methods
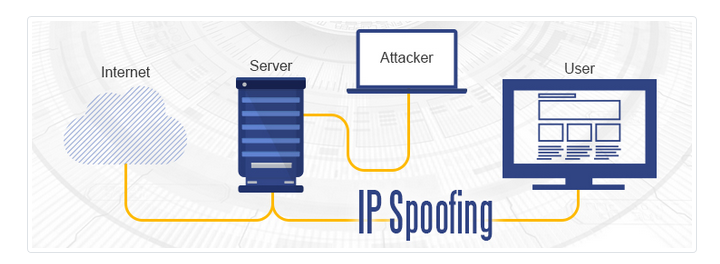
IP Spoofing: Assuming the identity
IP Spoofing is a way of doing things used to gain unauthorized access to machines, within which/by which an attacker illegally (pretends to be) another machine by controlling/moving around/misleading IP packets. IP Spoofing involves changing the packet header with a spoofed source IP address, a checksum, and the order value. Internet is a packet switched network, which causes the packets leaving one machine may be arriving at the destination machine in different order. The receiving machine looks like the message based on the order value which is inserted in IP header. IP spoofing involves solving the set of computer instructions that is used to select the order sent values, and to change them correctly. [4]
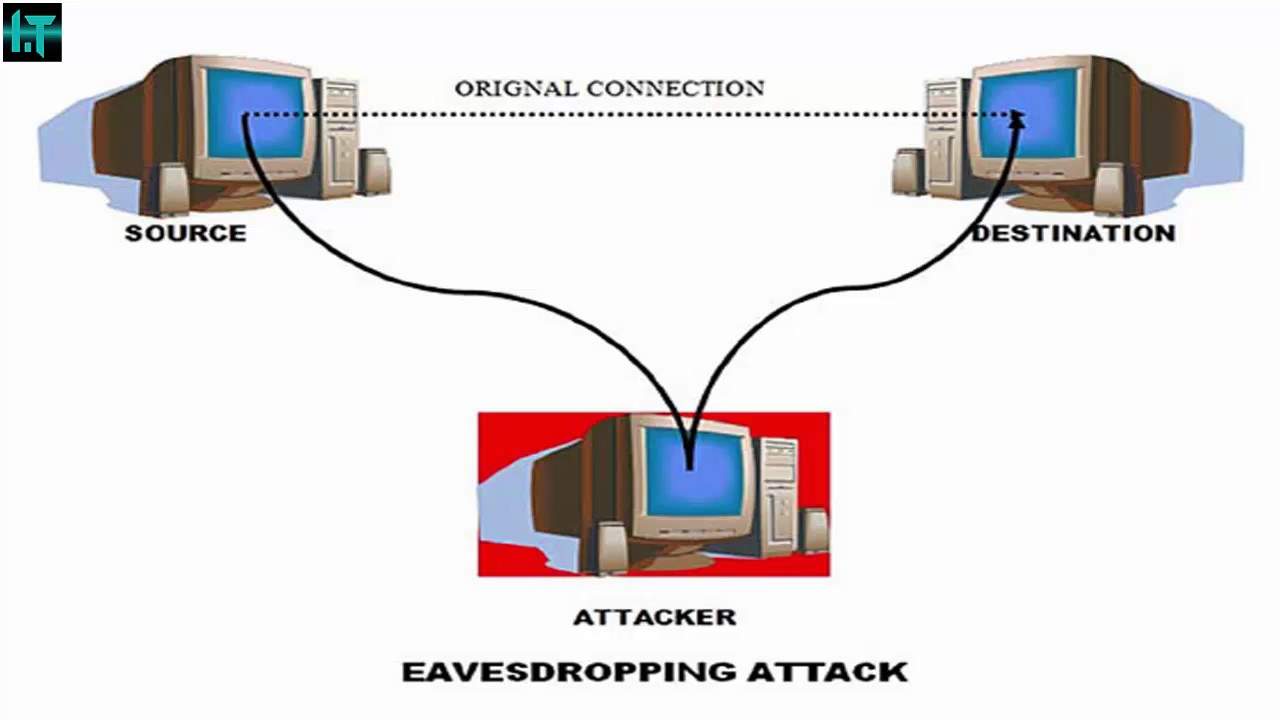
Man in the Middle attack using Packet Sniffers
This technique involves using a packet sniffer to intercept the communication between client and the server. Packet sniffer comes in two categories: Active and Passive sniffers. Passive sniffers monitor and sniffs packet from a network having same collision domain i.e. network with a hub, as all packets are broadcasted on each port of hub. Active sniffers work with Switched LAN network by ARP (Address Resolution Protocol) spoofing, the acknowledgement number, the ports and the protocol numbers, so that hijacker can forge the packet and send it to the server before the client does so. Another way of doing so is to change the default gateway of the client’s machine so that it will route its packets via the hijacker’s machine. This can be done by ARP spoofing (i.e. by sending malicious ARP packets mapping its MAC address to the default gateways address so as to update the ARP cache on the client to redirect the traffic to hijacker).3
Blind Attack
If you are not able to sniff the packets and guess the correct sequence number expected by server, you have to implement “Blind Session Hijacking”. You have to brute force 4 billion combinations of sequence number which will be an unreliable task.
Cross Site Scripting (XSS Attack)
Attacker can also capture victim’s Session ID using XSS attack by using JavaScript. If an attacker sends a crafted link to the victim with the malicious JavaScript, when the victim clicks on the link, the JavaScript will run and complete the instructions made by the attacker.
Mitigation
For defending the network on session hijacking there will have to secure application level and network level. Network level hijacks can be secured by encrypting the packets where the hackers can’t decrypt so that they will be safe. Providing with protocols like IPSEC, SSL, SSH etc. Internet security protocol (IPSEC) has the ability to encrypt the packet on some shared key between the two parties involved in communication. IPsec runs in two modes: Transport and Tunnel. In the transport mode the data packets will be send and in the tunnel mode both the packets and the data will be encrypted. [4]
Network layer
Secure socket layer
In this only secure socket layer should be used which uses end to end encryption for the data. When the data passes through the secure socket layer it will be in encrypted form and even if an attacker gets the data, it is very tough for him to find the real data from the packets. SSL channels use public key 28 bits and symmetric key 256 bits which make the encryptions method more complex, strong and more protected. [4]
Secure shell(SSH)
Secure socket shell is a network protocol used to access remotely situated systems or any remote computers. This also provides a strong way of authentication and more of the encryption between the two systems in any insecure networks.
HTTPS
Usage of Hyper Text Transfer Protocol Secure connection whenever you are login to any website or even any servers where it makes the connection more secure and thus it will show that it is in a secure link for online works.
Application layer
Application layer is the send part of security layer deals with session ID hijacking there some countermeasure which given below. [4]
Complex and strong session ID
Session ID provides the unique identity to each session as well as user in order to track progress of user and the authentication state of the users in the web application, each application provides the users session identifier that is also known as Session ID or a token, which is assigned to the session when the session is created and used to share with the users and application server in order to track users activities. The ID will be valid till the session is valid once the session gets expired.
Random session ID
Usage of random session ID generation will be making attacker very harder to guess the session ID. Long Session ID can be used because the session ID will be long enough then it will provide good security to protect it from brute force attack.
Session ID generated by server
Using of server generated session ID which will make the session ID more complex and stronger because servers user algorithm to generate the session id and it is very tough for the attacker to crack the code.
We can use
a) Encrypted session ID
b) Automatic log out
Some of the ways by which we can safeguard against session hijacking are:
- Use secure shell (SSL) to create a secure communication channel
- Use encrypted protocols that are offered at OpenSSH suite
- Pass authentication cookies over the HTTPS secure connection
- Implement the log-out functionality for each user to invalidate the session
- Generate different session ID after each successful login and logout
- Always pass the encrypted information between the users and the web servers
- Use string or long random variables as a session key
- Use different username and password for each account
- Configure the suitable internal and external spoof rules on gateways
- Do not transport session ID within the query string
-
Limit incoming connections and Minimize remote access
References
1. Article Online Tchopedia
Jeff Melnik, Common Cyber Attacks, 2018
https://www.techopedia.com/definition/6060/attack
https://blog.netwrix.com/2018/05/15/top-10-most-common-types-of-cyber-attacks/
2. Article Online
Alexander Prohorenko, Networking 2000
https://www.techrepublic.com/article/tcp-hijacking/
3. Journal Article on Website
TCP SYN Flood, Imperva Incapsula
https://www.incapsula.com/ddos/attack-glossary/syn-flood.html
4. Anuj Kumar Baitha, Prof. Smitha Vinod, 2018
Research paper on Session hijacking and prevention technique
https://www.researchgate.net/publication/325117343_Session_Hijacking_and_Prevention_Technique
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


