Tracks Covering in Penetration Testing
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 1580 words | ✅ Published: 22 Jun 2018 |
- Er. Ramesh Narwal
- Er. Gaurav Gupta
Abstract
After completing attack, covering tracks is the next step in penetration testing. In tracks covering after completing attack we will return to each exploited system to erase tracks and clean up all footprints we left behind. Tracks covering is important because it gives clue to forensics analyst or Intrusion Detection System (IDS). Sometimes it’s difficult to hide all tracks but an attacker can manipulate the system to confuse the examiner and make it almost impossible to identify the extent of the attacker. In this research paper we describe all of the methods used in tracks covering and their future scope.
Keywords: Exploit, Payload, Vulnerability Assessment, Penetration Testing, Track Covering
Introduction
Penetration testing is nowadays an important organisation security testing method. Penetration testing is also known as Pentesting. Main objective of penetration testing is to identify the security threats in networks, systems, servers and applications. Penetration testing consists of various phases which we discuss in overview of penetration testing. After gaining administrative access on a system or server, attacker first task is to cover their tracks to prevent detection of his current and past presence in the system. An attacker or intruder may also try to remove evidence of their identity or activities on the system to prevent tracing of their identity or location by authorities. To prevent himself an attacker usually erases all error messages, alerts or security events that have been logged.
Overview of Penetration Testing
Penetration Testing used for validation and effectiveness of security protections and controls of an organisation. It reduce an organisation’s expenditure on IT security by identifying an remediating vulnerabilities or loopholes. It provides preventive steps that can prevent upcoming exploitation. Penetration testing phases
- Pre-engagement Interactions
- Intelligence Gathering
- Threat Modeling
- Vulnerability Analysis
- Exploitation
- Post Exploitation
- Covering Tracks
- Reporting
Pre-engagement Interactions
Planning is the first step in pre-engagement. During this phase scope, goal and terms of the penetration test is finalised with the client. Target and methods of planned attacks are also finalised in this phase.
Intelligence Gathering
This is most important phase if we miss something here we might miss an entire opportunity of attack. All information regarding target is gathered by using social media networks, google hacking and other methods. Our primary goal during this phase to gain accurate information about target without revealing our presence, to learn how organisation operates and to determine the best entry point.
Threat Modeling
The information acquired in intelligence gathering phase used in this phase to identify existing vulnerabilities on the target system. In threat modelling, we determine the most effective attack methods, the information type we need and how attack can be implemented at an organisation.
Vulnerability Analysis
Vulnerability is loophole or weakness in the system, network or product by using which can compromise it. After identification of most effective attack method, we consider how we can access the target. During this phase we combine information acquired in previous phases and use that information to find out most effective attack. Port and Vulnerability scans are performe in this phase and all data is also gathered from previous phases.
Exploitation
Exploit is a code which allows an attacker to take advantage of the flaw or vulnerability within system, application or service. We must perform exploit only when we are sure that the particular exploit will be successful. May be unforeseen protective measures might be on the target that inhibit a particular exploit. Before trigger a vulnerability we must sure that the system is vulnerable.
Our exploit must do proper clean-up after execution at compromised system and must not cause the compromised system to grow into unstable state. Given below figure shows some system shutdown prompt at compromised windows machine due to without proper clean-up of exploit after execution.

After successful exploitation the compromised system is under the control of an attacker. Many times attacker or penetration tester need to alter the compromised or breached systems to attain privilege escalation.
Post Exploitation
Payload is actual code which executed on the compromised system after exploitation. Post Exploitation phase begins after compromised one or more systems. In this phase penetration tester identifies critical infrastructure, targets specific systems, targets information and data that values most and that must be attempted to secure. In Post Exploitation while attacking systems we should take time to understand what the system do and their different user roles. Every tester and attacker generally spend time in compromised system to understand the information he have and how he can take benefit from that information.
After gaining access of one system an attacker can access other systems in that network by using compromised as a staging point. This method is known as pivoting. Sometimes attackers creates backdoor into the compromised system to regain access of the system in the future
Covering Tracks
In the previous phases penetration tester or attacker often made significant changes to the compromised systems to exploit the sytems or to gain administrative rights. This is the final stage in penetration test in which an attack clears all the changes made by himself in the compromised systems and returns the system and all compromised hosts to the precise configurations as they are before conducting penetration test.
Reporting
All of the information like vulnerability reports, diagrams and exploitation results generated during penetration testing must be deleted after handover to the client. If any information is not deleted it should be in the knowledge of client and mentioned in the technical report which is generated after penetration testing.
Reporting is the last phase in penetration test in which penetration tester organise available data and related result sets into report and present that report to the client. This report is highly confidential which have all the results of penetration tests like vulnerabilities list in the organisation systems, networks or products and recommendations to solve these problems related to the security of the organisation assets, which helps organisation in stopping future attacks.
How to cover tracks
To compromise system successfully an attacker need to be stealthy and avoid detection by various security systems like firewalls, Intrusion detection systems (IDS). System administrators and other security personals uses similar techniques to identify malicious activities, so it’s very important for attacker to be remains undetected. A system administrator can examine processes and log files to check malicious activities. There are various challenges which are faced by a penetration tester after successfully compromise of target system. Now we describe various problem faced by a penetration tester in covering tracks
Manipulating Log Files Data
To manipulate log files data an attacker must have nice knowledge of commonly used operating systems. An attacker must aware of two types of log files system generated and application generated.
Penetraion tester or attacker have two options when manipulating log data first one is to delete entire log and second one is to modify the content of the log file. After deleting entire log an attacker there is surety of undetectability. But there is drawback of deletion of entire log is detection.
Second option an attacker have to manipulation of log files data within the log files so that system administrator is not able to notice attacker presence in the system. But sometimes if attacker removal of so much information make gap between logs files makes it noticeable.
Log Files Management in Various System
Main purpose of log files in various operating systems is to check health and state of operating system, to detect malicious activity, to analysis system if something bad happens(system troubleshooting). Here we show locations of log files in commonly used operating systems Windows, Linux/Unix, Mac.
Windows
In windows log files or stored in event viewer, which is easy to find simply search event viewer and run it. Event viewer is simply look like the figure as given below, where we can see all log files of the system and applications.
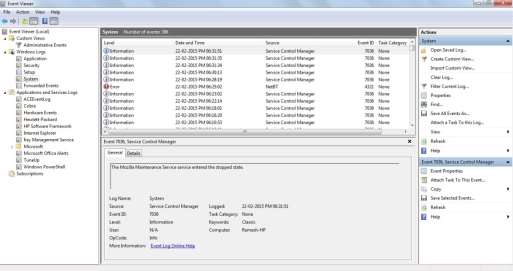
Figure : Log Files Managements in Windows
Linux/Unix
In mainly all linux and unix operating systems log files are stored in the /var/log directory. Mainly system log files are hidden in linux and unix operating systems to see complete list of log files from shell simply type ls –l /var/log/ command in shell. In the below figure we show log files in BackTrack linux operating system

Figure : Log Files Management in Linux/Unix
Mac
To get or access log files in MAC operating system simply open finder and select “Go to Folder” in the Go menu. Type in /Library/Logs and hit Enter here you get the screen like as given in figure which contains all log files.

Figure : Log Files Management in Mac OS X
To manipulation of log files data an attacker must have root privileges.
Challenges in Manipulation of Log Files
If the system administrator configures its system to transfer all log files on the remote server time to time, in that case an attacker or penetration tester can only stop log files transfer process except it they have no other way.
Hiding Files
Various Tools for Covering Tracks
There are so many to compromise a system but after compromising the system the attack must need to cover their tracks because each and every activity that attacker can do is stored or recorded by the system. Every system have different way to record the activity that occurs in the system. Every attacker must covers their tracks that are recorded by the system so that no one can identify him.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


