Recovery of Digital Evidence
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 1321 words | ✅ Published: 18 Aug 2017 |
Introduction
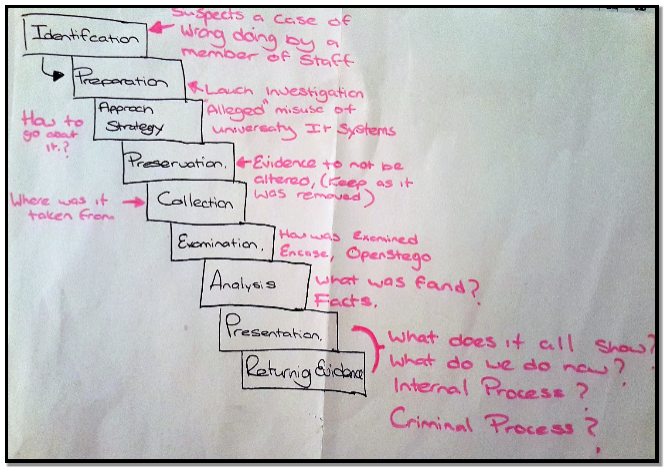
The University suspects that a case of wrongdoing has been undertaken by a member of staff within Edge Hill University and the computer forensic team, of which you are part of, has been asked to investigate.
You and your team have been asked to launch an investigation into alleged misuse of the University’s IT system. The office used a member of staff has been isolated, sealed and secured.
The staff member has been interviewed by IT services as well as the Dead of faculty and HR and has subsequently denied all wrongdoing. Items from the staff office have been recovered by your team. The evidence recovery has been conducted in a rigorous secure manner in lines with a strict methodology.
The Principles of Digital Evidence

Evidence Recovery Process
From the start of the process there must be a set way to conduct the investigation, the crime scene is a very delicate place in terms of collection of critical vital evidence, which if left unsecure could be easily be altered or corrupted, therefore it’s important to follow several key stages, the first being;
The Plan of the Investigation
- Where are, we going to find the suspected evidence, i.e. on Computer system, Smart phone, USB, floppy disc, Hard Drive.
- Should social media i.e., Twitter, Facebook, Chat Forums, be checked for relevant evidence they may hold.
- Contact of user ISP for trace history
- Mobile network contact, may have on online account with online storage.
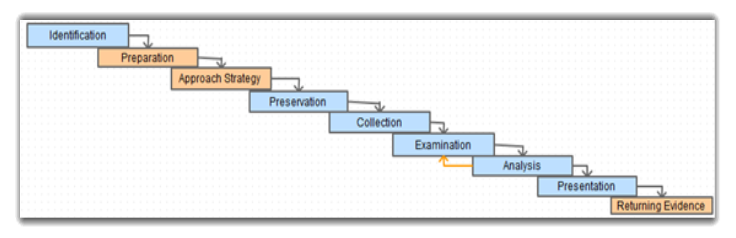
How to conduct the Investigation – My Flow Plan
Right to Search and Seizure
In order to conduct an investigation there are Legal and ethical aspects that are very important and must always be adhered to key points that would always be considered when its decided that evidence will need to be received;
- Just because there are several computers in the house doesn’t necessary mean that they should all be seized for forensic inspection, the person attending the crime scene must have Reasonable grounds to remove possessions and there must be justified reasons for doing this.
- Due to the sensitive nature of the investigation it would always be a necessary moral characteristic that the investigator would be honest and truthful.
- Consideration as to whether what items are likely to hold key information, i.e. there would no point in seizing a microwave when we are looking at a computer related crime.
- Consider the offence, narrow down the time period of suspected crime.
- Items found that are connected to internet are likely to contain key information and should be seized.
- Documents/booklets, notepads to be seized as they may hold online storage accounts and passwords where information is held.
Approach Strategy
This all would be done using a Flow plan for the team to follow as discussed in Assignment 1,
Capture of relevant information
One of the most important steps within the whole process, if mistake is made here then the whole investigation is under threat.
- The room was secured and isolated to risk the impact of any tampering with evidence.
- This could basically fail in to a very similar category, this may involve the collection of volatile date.
- Volatile data is the data that we have at the scheme of the crime that may be lost if the investigator doesn’t follow the correct procedure, i.e. recording what state the computer is on at that time. The Volatile data would be stored for example on a PC in the Ram (Random Access Memory) and would contain key information such as website data, chat history etc. that may be key to overall success of the investigation.
- Bagging in secure bags that are tamper proof insuring that they are labelled acutely with a reference number for later inspection.
- Suspected member of staff interviewed denied any wrong doing.
Analyse of Evidence
Evidence has been recovered from the staff office by a colleague within the forensic team, we have found the following;
- A USB pen drive seized bagged up in secure zipper bag
- Feedback to be given to give information on where to investigation in going.
- Each step to be recorded
- Time scales available
- Resources available to investigator
- Tools that are available for the forensic analysis.
Data recovered from the USB drive, seems to just be Standard information but further analysis is needed to establish truth.
Evidence Seized
Note pad with 3 passwords on;
- Cabbage
- Apple
- Pear
USB device seized from the office. From what we can see on the USB is
- 3 PDF’s
- 3 Images
- A word document Titled “Payments for paper4you”


Files present on USB Un touched
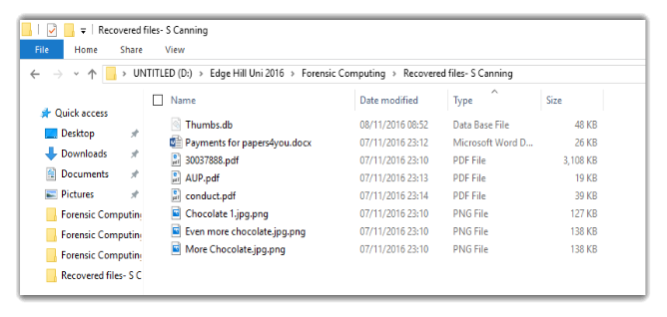
On the next step of my investigation I will open each file without any interference from any Encryption programs.
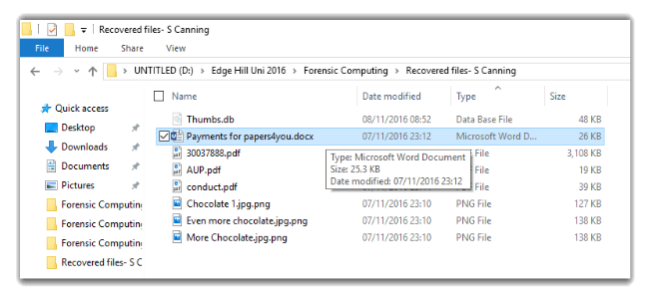
File – Payments for papers4you.docx
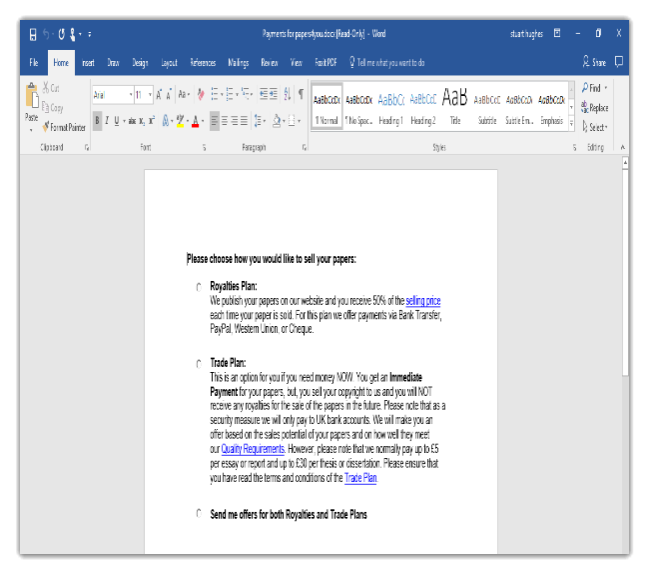
File – 30037888.pdf


File – AUP.pfd




,
File – conduct.pdf





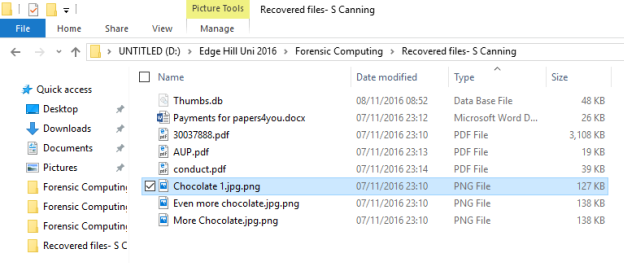
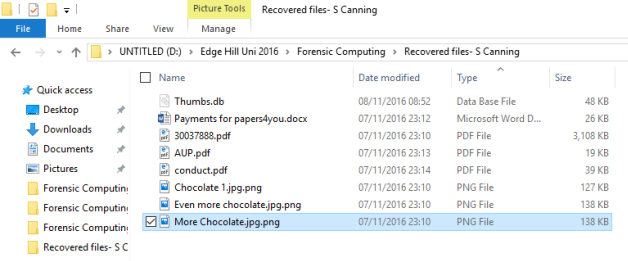
Chocolate 1.jpg.png

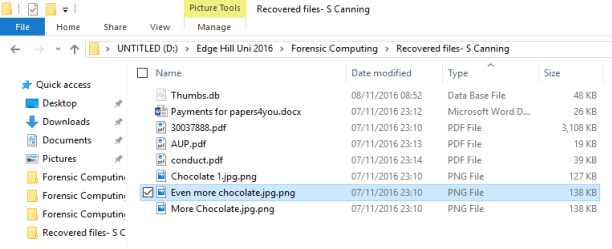
Even more chocolate.jpg.png

More Chocolate.jpg.png

Investigation of the Evidence
For the pupose of the investigation I will now check to see if the items sesiued are extactly as they seem. I do think this step is necessary aspart of the on going investigatiion.
In order to check individual files, I will use OpenSteg application, the reason to do this is it will check each induvual file in order to establish any hidden files located on the the USB.
To do this I will use a programe called OpenSteg which will highlight any hidden information
OpenStego Menu,- As you can see we can Hide or Extract Data from a any file, in this case we will be Extracting the Data from the chosen file.
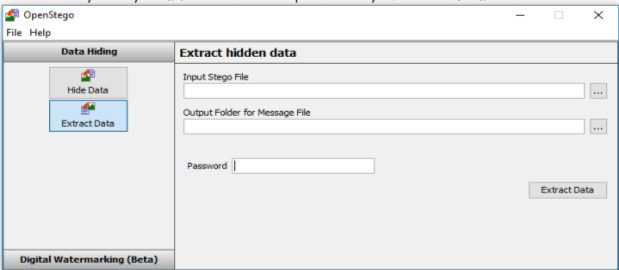
Menu of the file which I wish to look at though OpenStego – Chocolate 1
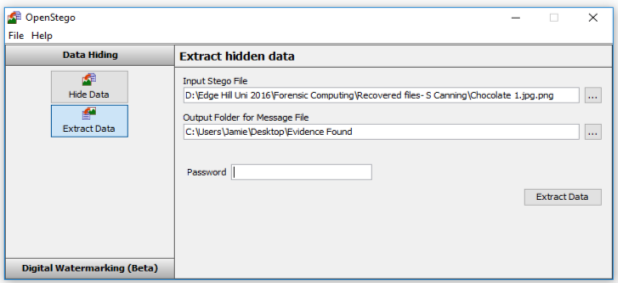
On checking the file, it is clear the it needs a password to open it, I will try the 3-password written down on the note pad recovered from the scene, which are:
- Apple
- Cabbage
- Pear
It would appear that there is a file within this picture titled;Master_Sheet.xlsx
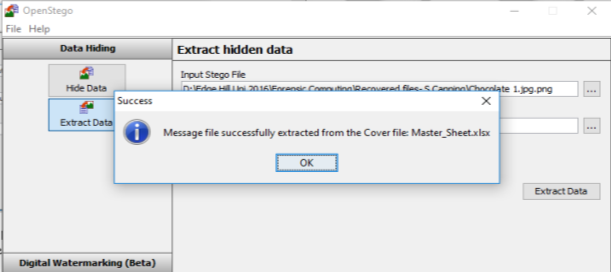
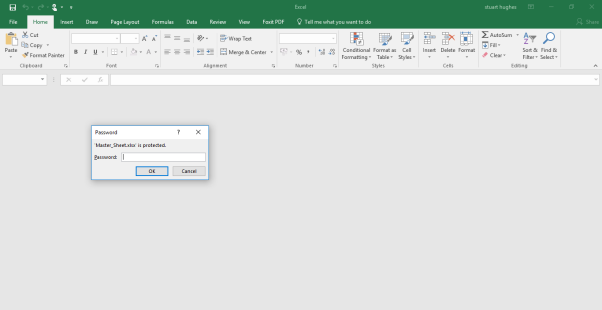
Upon opening the Excel File it appers that it requires a password of which I have 3 ;
- Apple
- Pear
- Cabbage
Apple and Pear are unsuccessful, but Cabbage has grated me access to the Excel file
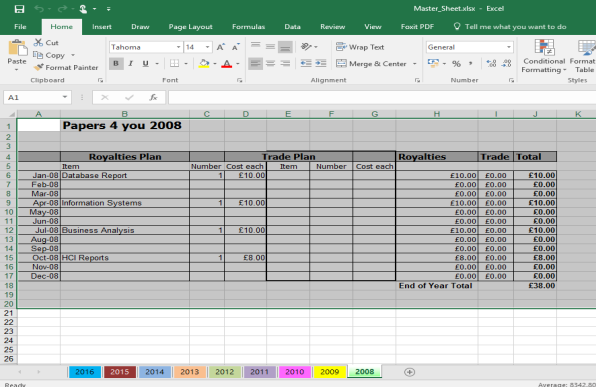
It appears to show Financial transactions from Papers 4 you dated from 2008 to 2016
2008
2009
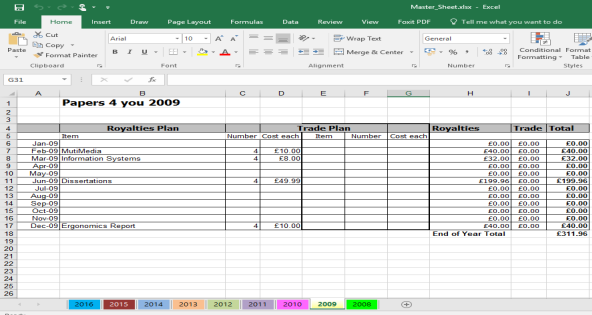
2010
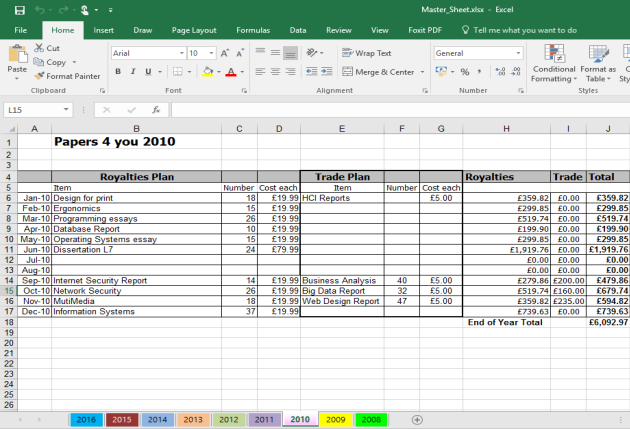
2011
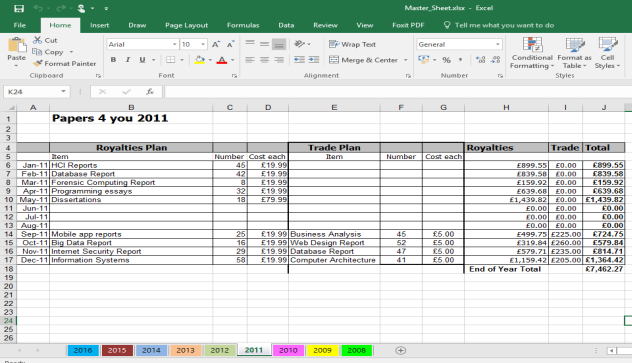
2012
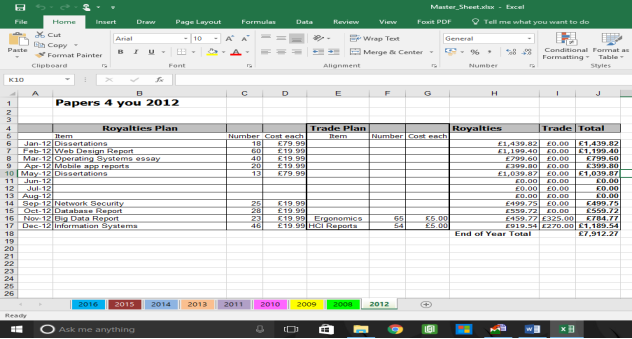
2013
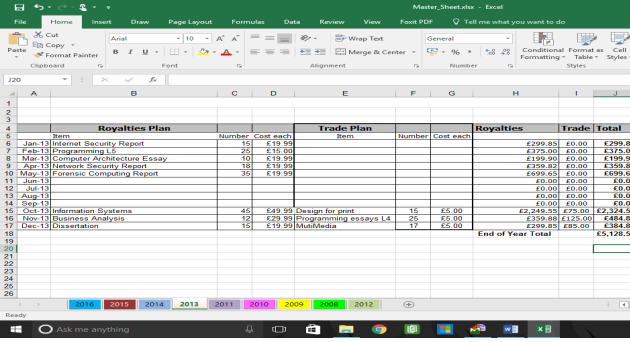
2014
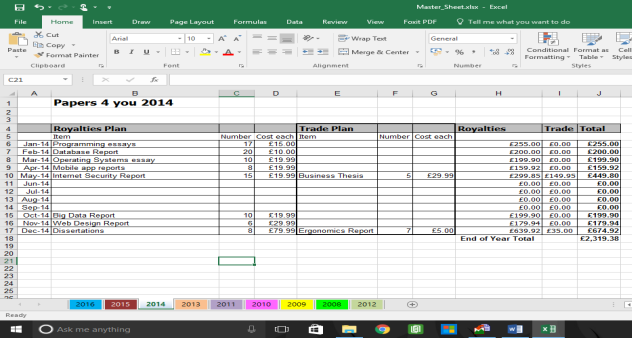
2015
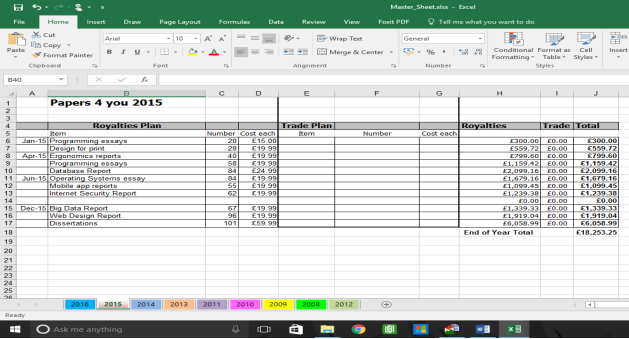
2016
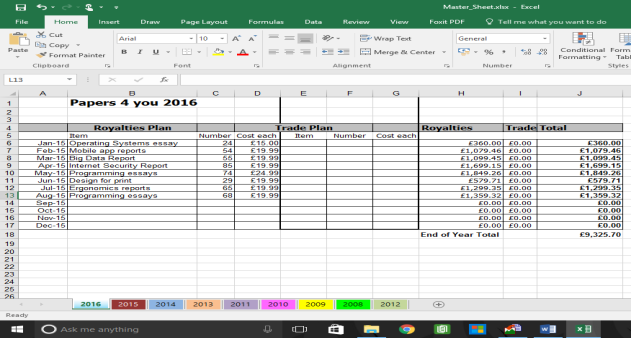
The same was done with the file Even more chocolate.jpg.png
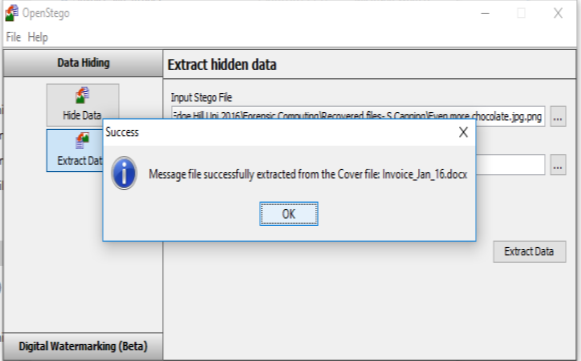
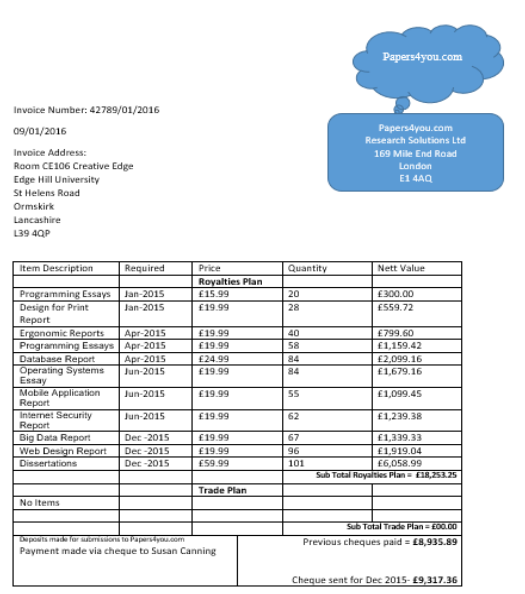
Upon doing this it is clear there is a file hidden within the picture titled Invoice Jan-16.docx As per below;
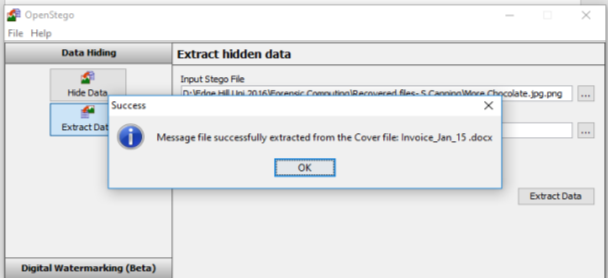
Picture 3 to be checked using OpenStego file name – More Chocolate Using password – Pear
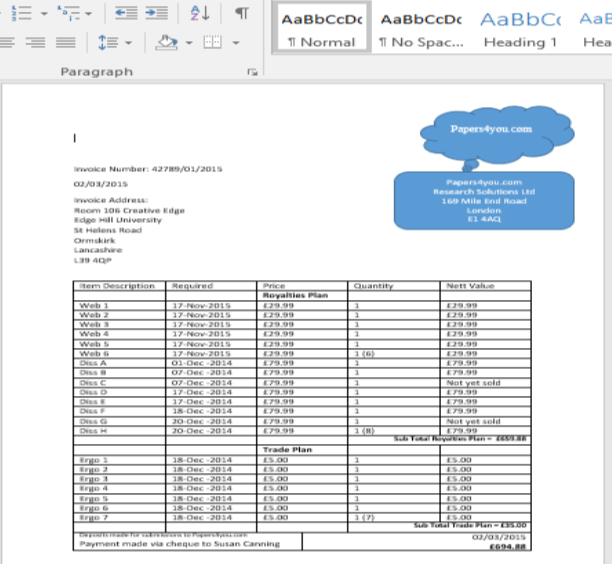
Information from file Jan-15
Bring the evidence together as one we could use Encase this would give us a clear understanding of all the evidence together in one file format I have demonstrated in a walk through via screenshots
Landing Page Encase
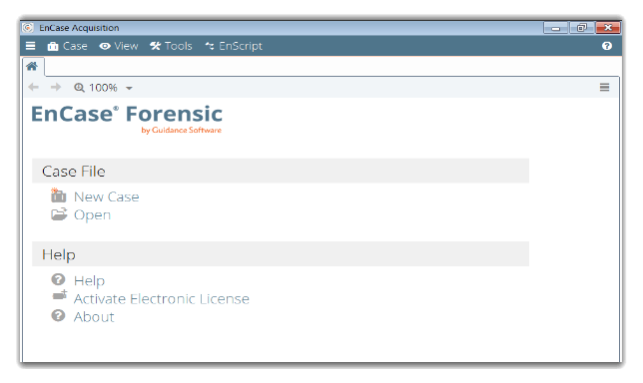 New case Location and name
New case Location and name
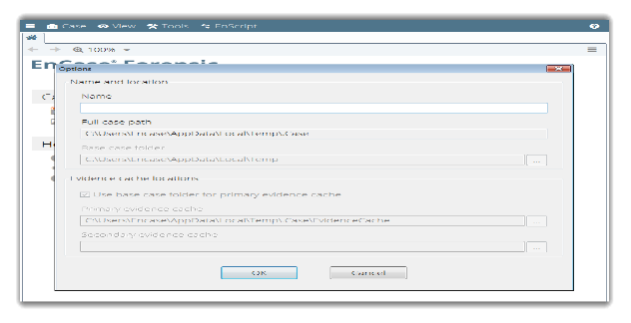
File is now given name “Assignment 2 and location.
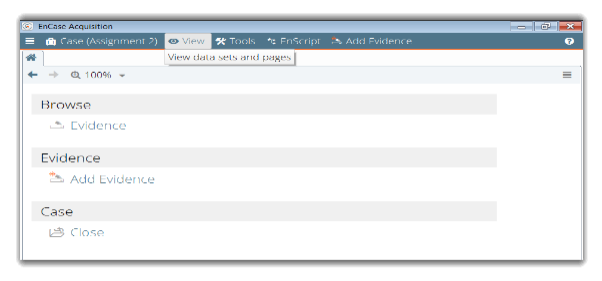
Adding Evidence to the case
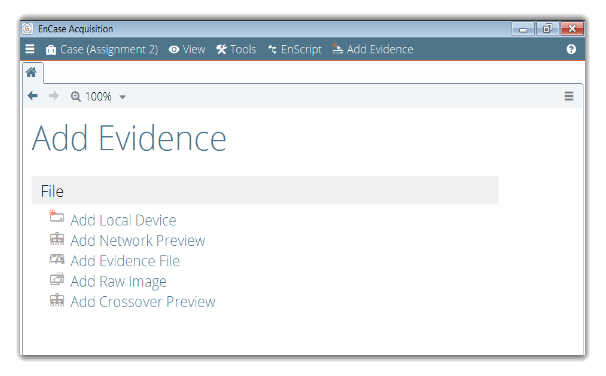
Locate relevant file to add the information needed for the investigation.
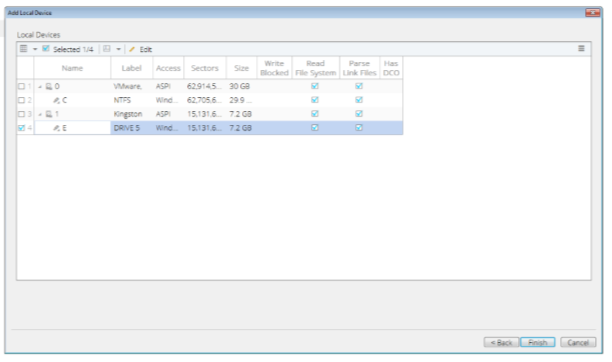
Section of key files to use as evidence.
Summary of the Evidence
From conducting this investigation certain key points must be established when investigating the case
- Facts or fiction and can prove this with hard evidence.
- Prove that it did happen in the first place.
- Are we looking at the right person that is accused?
- Have any mistakes been made., things been missed or thigs been altered.
Forming the whole investigation, we can see from the Time Line, what information and by what process was followed
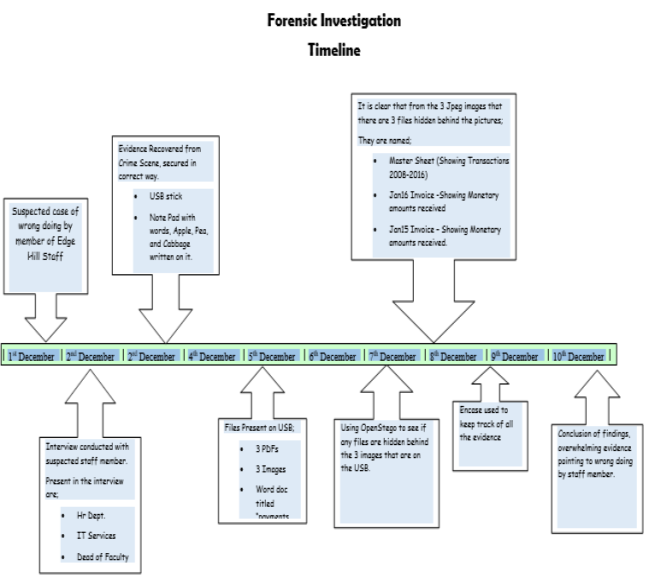
It is with my Recommendation that the Case be referred to CPS for Criminal Proceedings. Due to the many breach’s with in the law, (Data Protection, Computer misuse act, It Computer Policy) and the and the vast amounts of money received, it is unlikely that internal University formal proceedings would bring accountability for the thief.
In Conclusion, it would also be recommended that upon Criminal Proceedings being initiated, that an order for the “Proceeds of Crime Act” be sort to recover the ill-gotten gains.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


