Project Design of ABC Corporation: Security Assessment
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 1462 words | ✅ Published: 11 Aug 2017 |
ABC Corporation Computer Network
Organization
ABC Corporation is a big brokering company which is founded in China and has a workforce of about 9,000 situated over different office branches distributed all over. The corporation is setup in Los Angeles. The people that sets up the corporation’s branch in Los Angeles that helps with the current system which they want it to be dependable, quick, secure and will satisfy any future prerequisites of the organization.
The implementation of this system is to offer the following platforms: cloud computing, distributed computing and centralized computing in the network which supposed to be a secure computer network system.
Purpose:
The purpose if this security assessment report is to provide a documentation outlining security gaps and vulnerabilities the project design of ABC Corporation may have experience and may be a threat to corporate security policies of ABC Corporation. The management will be required to allocate the necessary resources to correct any problems and gaps in its project design security. The management may also decide to accept the risk, since its already an informed risk or a reward analysis. This will make sure that the necessary security controls will work best for ABC company and are integrated into the IT design of ABC company.
Scope:
The scope is to cover all aspects of the Computer Network Design project since it is aimed at creating a “risk free” Network System. It will cover both vulnerabilities, risks and security gaps that can be a threat due to insider dealings (people working in the company who might have any malicious intentions) and threats that may come from the outside (people who are part of the workforce) to people who might use these vulnerabilities and security gaps if they come to learn their existence. People that works for the organization is a threat to the organization’s computer network design project as those from the outside the fact that they are more accustomed to the working of the system they pose as a much greater threat.
Data
The ABC Corporation has built a LAN and a WAN system program that can help the association to develop a more extensive network system that can boost the financial frameworks which has more benefits and will deal in the forthcoming years. The ABC Corporation LAN have a topology of frameworks trading contraptions which is to work as switches in the center. They are appropriated and can get to the layers that can indicate the structure jointly with a set up plan. They put all the gadgets together.
This technique will redesign the system presentation and dispose not so important interconnections at the same time providing flexibility. At the end of the network, the ABC Corporation has different edge switches. They are to be utilized for “Web Access Provider (ISP) Openness”, Intrusion Prevention Systems and Firewalls that are deliberate to changes and other square intruders which can offer the use and end gadget framework. This system is designed to assist the partnership specialists with employing any new applications that are urgent and the most efficient operation of new preparation plans for the organization deals and constraints.
Methodology
Although there are different methodologies of conducting a Security Assessment Report, the best methodologies for ABC Company are the ones that was used to access the vulnerability of ABC Computer Network Design and the risks that company may face. The following methodologies were used to access the security state of ABC Computer Network Design:
- Requirement study and situation analysis: The situation of the ABC Computer Network Design was analyzed using the wireshark program.
- Document review: Documents recorded by IT personnel were also reviewed for any information that may be suspicious regarding manipulation of the Computer Network Design of ABC Company.
- Risk identification: Risk identification was mainly done by using the wireshark program, which analyzed the activities that was going on in the network of a given computer design.
- Data analysis: Data that stored in the computer network due to previous activities that were conducted within the computer network that has analyzed for any suspicious data that may be due to security gaps in the computer network design of ABC Company.
- Vulnerability scan: A scan that is conducted in the Computer Network Design to cite any vulnerable in the computer network of ABC company that may pose as a threat.
Findings
The risk levels of ABC Computer Network were high and the vulnerability described as a critical. This is mainly based on the following findings after the scan of the ABC Computer Network:
- There were many ports which were open and these ports could be used by hackers to get access into the Computer Network. Most of these hackers are malicious individuals that may send viruses and malwares into the Computer Network or use these privileges acquired to exploit the system.
- The remote host of the Computer Network was seen to be running on a computer with an OS of Windows version. This computer had a fault in its RPC interface, 98 netbios-ssn and 10 microsoft-ds. The flaw can give a hacker an access to execute some arbitrary codes making them to acquire privileges of the computer system. This weakness can also be utilized by a worm and give an ability to control the host.
- Some suspicious activities in the Computer Network were also noticed. An example of this was an activity from an unknown user who was using an unidentified OS with a mac address 00:ff:eb:48:41:88 (unknown). All unknown users are supposed to be flagged immediately until their identities is known.
In addition to these risks and vulnerabilities identified, “insider” intimidation also poses a risk to ABC Corporation. Individuals working from within the corporation are a potent a threat to the computer network as risks from the outside. The corporation should choose to care if any of its employees might be using commerce information malevolently for their own benefits.
Results
After assessment of the security situation of the ABC Company Computer Network Design, there were found to be some security gaps which need to be addressed by the management. These gaps are known by a malicious party that would pose as vulnerable to the computer design of ABC Company Computer Network Design. Since the system administrators have full access of the entire system, they should do a follow up on risks and vulnerabilities. The network administrators would be the best to do the follow up on security gaps identified.
Labs
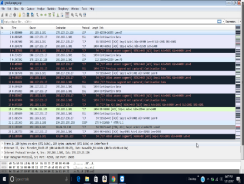 Â
 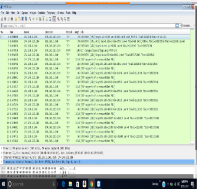
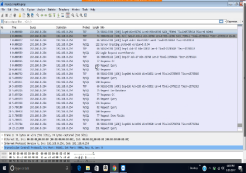
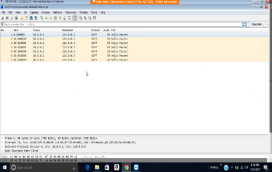
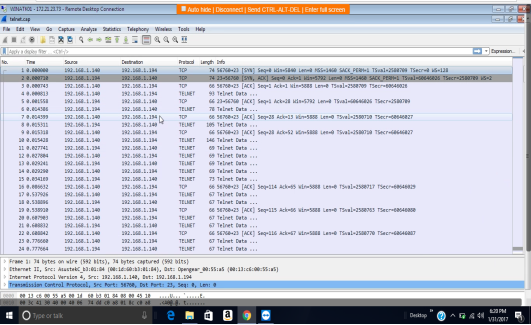
The computer that I scanned was WINATK01 with IP address 172.21.23.73. The transmission control protocol is a service that links and works between an application program sending information and the internet protocol. It also provides host-to-host connectivity at the internet model’s transport layer. The transmission control protocol can detect any problem at the lower levels of the transport layers such as poor network connectivity and network congestion. There are several vulnerabilities as far as transmission control protocol (TCP) is concerned. The two most used attacks are denial of service whereby the attackers use spoofed IP address and connection hijacking whereas the hacker can eavesdrop on an on-going transmission and takes over one of the receiving ends and goes on with the communication as if is the original recipient.
Findings
The scan was done using Wireshark vulnerability assessment tool. The following are the transmission control protocol/internet protocol (TCP/IP) discovered; TCP and HTTP. The scan further revealed that there was a security communication provided by the security data transport methods especially contained in MySQL. The components of MySQL are;
- Connectors (Connector/C, Connector/J, and so forth)
- MySQL Proxy
- Communication between master and slave replication servers
MySQL proxy is a very vital component which encrypts and compresses information end-to-end for proper security optimization to prevent and avoid possible attacks. MySQL protocal also aids in data transmission just as the TCP.
Conclusion
In conclusion, the network system that analyzed above was found to be effective in information transmission between the different sources and destinations. The security status was also found to be superb with an end to end encryption provided by the proxy in MySQL. Thus, the vulnerability status can be concluded to be at minimum and attackers cannot easily manipulate their ways to attack the network systems.
Recommended safeguards
The management should there are no ends left unguarded with firewalls and any other programs which would make the network inaccessible from any unauthorized parties from the outside. The dealings of internal workers too should be closely supervised to make sure employees do not use the system malevolently for their own benefits. The network administrators should also look closely to the network system frequently to make sure that there are no ports left open or no suspicious activities take place either due to internal dealing or from outside of the network.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


