Fundamentals of Information Technology
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 1839 words | ✅ Published: 18 Aug 2017 |
Human Computer Interface (HCI)
Kurosu (2011) defines usability as the extent to which a product can be used by specified users to achieve specified goals with effectiveness, efficiency and satisfaction in a specified context of use. Usability is dependent on the context of use and that the level of usability achieved will depend on the specific circumstances in which a product is used. The context of use consists of the users, tasks, equipment, and the physical and organizational environments which may all influence the usability of a product
Microsoft Visio and Word Interfaces look almost identical with its white shaded ribbons of tools. What are so vastly different between the two applications is their uses. Microsoft Word is a word processing application used for professional looking documentation while Visio is a diagramming and vector graphics application. An enhancement in terms of usability with Microsoft Word would be its spelling and grammar tool found on the review ribbon.
An integrated Speech to text within Word could add to its HCI. This type of feature could make Swagger Distribution’s document creation seamlessly faster by adding speech dictation.
Databases
The Clothing Manufacturers Table houses the manufacturer’s name, street address, city, state and zip. The Clothing Products table holds the clothing item, color, manufacturer’s name, wholesale price and retail price The Retail Stares table stores the information for store name, street address, and city, state, zip and clothing item. The Clothing Products table bears currency fields while the Clothing Manufacturers and Rectal Store table has number fields,
When opening the Clothing Products table, I could see both the wholesale and retail prices were incorrectly formatted. When changing the retail price from text to currency the prices became correctly formatted. Custom formatting only changed how the data is displayed and does not affect how the data is stored in a Microsoft Access database, or how users can enter or edit data (Microsoft Blog, n.d.).
The query creates a list of clothing items in retail stores. It shows the retail store name and state and the clothing item, manufacturer name and retail price. The report is sorted alphabetically by retail store name. There is no secondary sort, because of this, the list of clothing items in each retail store will come out in a random, unpredictable and inconsistent order (Microsoft Blog, n.d.). The Retail Stores table links to the Clothing Products table based on the clothing item. The Clothing Products table links to the Clothing Manufacturers table based on the Manufacturer Name.

Visio
There are many kinds of Visio diagrams, including flow charts, networking diagrams, and home or office plans. However, you use the same three basic steps to create most of them:
- Opening a template.
- Dragging and connect shapes.
- Adding text to shapes.


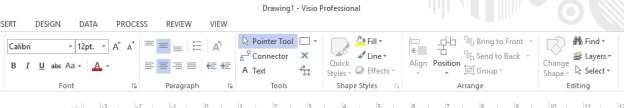
The Connector Tool in Visio 2013 found in the tools section of the Home Ribbon is used to Auto Connect shapes and stencils.



 On the insert ribbon of Visio you can insert objects such as pictures on to the canvas. You can begin this process by clicking insert on the Insert ribbon and clicking the option you’d like in the illustrations section..
On the insert ribbon of Visio you can insert objects such as pictures on to the canvas. You can begin this process by clicking insert on the Insert ribbon and clicking the option you’d like in the illustrations section..


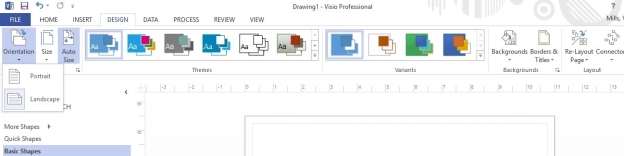
 Within the Visio Design Ribbon a user can select their page layout between Portrait and Landscape, whichever works best for that users display. To select an orientation, click on the Orientation option in the Page Setup section of the Design Ribbon.
Within the Visio Design Ribbon a user can select their page layout between Portrait and Landscape, whichever works best for that users display. To select an orientation, click on the Orientation option in the Page Setup section of the Design Ribbon.

Users can Save their stencils and diagrams by clicking the save option on the Title Bar.



A user can consult the Help option on the Visio Title Bar to search the database for help using the application.
Visio Help Database
Networking
“Computer Rooms typically provided by libraries to the public, academic institutions to retain access to the Computers” (Tomsho, Tittel, & Johnson, 2015, p. 315). Swaggered Distributions consists of three segments towards network offices, computer room, and warehouse. The wide area network fits into the computer room private network with the means of the T1 demarcation router. The demarcation router switches over toward the public wide area network where swagger distributions private network resides. The system has a main router whose main is to apply Dynamic Host Control Protocol and routes IP addresses to all connected devices in the network segment. The DHCP server then allocates IP address to the firewall. The firewall based on the security policies allows certain packets of information in and out of the network. Within the computer room, there is a server which acts as a dedicated place for storing files & applications where other network based computers which are permitted to log into and retrieve specific information. There is also an Ethernet switch whose main duty is to direct packets of information towards the correct connected device in the network and allocate the priority for each data packet sent and received throughout the network. The Ethernet switch acts as the type of hub that extends the network in the direction of the warehouse where it connects by using fiber optic cable to link the two network segments. The fiber optic cable transmits data. The computer room then has another panel that functions as a hub to the segment of the computer room along with the office PCs. The warehouse and the office consist of one remote Ethernet switch. The office, where the PC are connected via category 5 twisted-pair networking cabling runs through the wall into a face plate and directly to the PC allowing that PC to connect to the central servers.
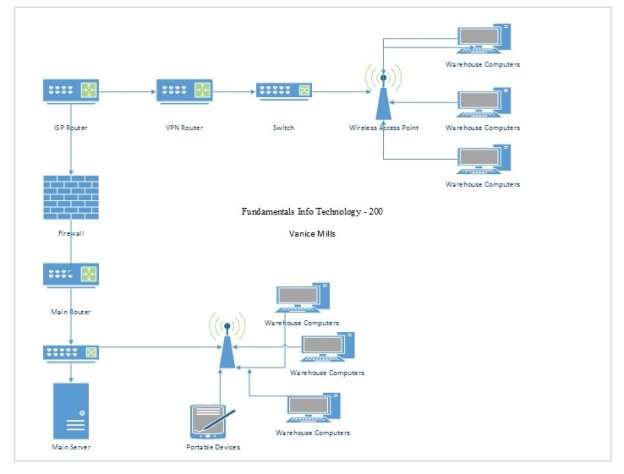
Diagram for WLAN
Programming:
import java.util.*;
import java.lang.*;
import java.io.*;
/* Name of the class has to be “Main” only if the class is public. */
public class HelloWorld
{
public static void main (String[] args) throws java.lang.Exception
{
int day;
int month;
int year;
GregorianCalendar date = new GregorianCalendar();
day = date.get(Calendar.DAY_OF_MONTH);
month = date.get(Calendar.MONTH);
year = date.get(Calendar.YEAR);
System.out.println(“Welcome to Swagger Distribution!”);
System.out.println(“Welcome, Today’s date is “+(month+1)+”/”+day+”/”+year);
}
}
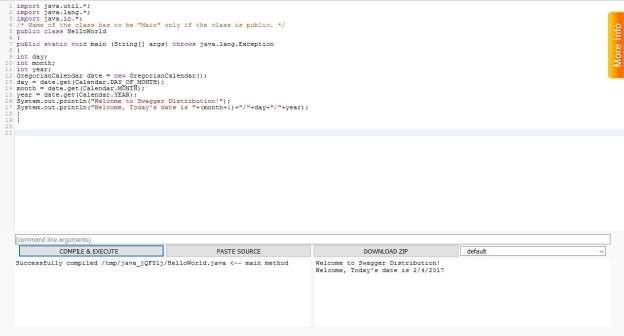
Code Compiled Successfully
The main changes to the original code have been bolded and can be summarized as follows. SYSTEM.OUT.PRINTL is a built in class in the Java language in which Downing (1999), states the OUT aspect functions to print various data values specified While the PRINTLN() aspect prints data values within a a public method (p.144). “The SEMICOLONis a Java compiler expression that communicates within the compiler a statement is complete”. The Calendar Code is a built in Java class returns a general object of its type whose calendar fields have been initialized with the current date and time (Downing & Downing, 1999, p. 217).
Web Technologies
According to W3C’S standards’ a website built solely with HTML 5 may have cross compatibility issues across multiple web browsers. “HTML5’s is not always supported on all browsers, so it is one of the major drawbacks of HTML5. (Dahl, 2017)”
Core Web Functionalities:
- Navigation: The ease of access and functionality of a user navigational experience improves the initial website assessment of said user which if positive will cause the user to become a repeat customer.
- Search: A search function could prove to be beneficial to a user in the case of Big Data. The website has too large data set volumes for traditional data processing applications to handle.
- Readability:Â All part of ease of access; readability is just as pivotal. A user should have a seamless time reading the content presented in all aspects.
- Site Map: A secondary to navigation provided to the user when said user has trouble finding specific information.
- Accessibility: Following the W3 standards it is important to have accessibility features so that the disabled users can also access and utilize a website successfully with features such as page magnifying, text to speech and on board keyboard.
- Plug-in: Plug-ins such as social media accounts and other traffic building tools add functionality to a webpage.
- Subscribe: Subscribing to the company’s mailing list to receive the latest on the company happenings and offers to persuade user purchasing of participation.
- Validation: Ensuring that all vital information required for successful submission on a form is present
- Conditions and Privacy: It is imperative to cover the legal aspects of using a Company’s services and how they may us your entered data.
- Speed: The speed in which a website loads relies on whether it’s content and media is optimized appropriately.
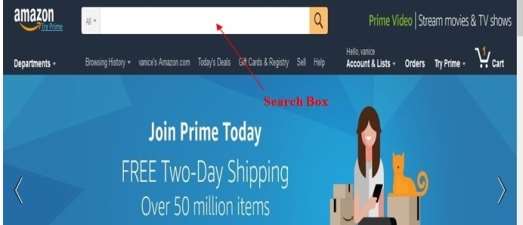
Amazon, one of the largest online retail stores utilizing the Search Box function.
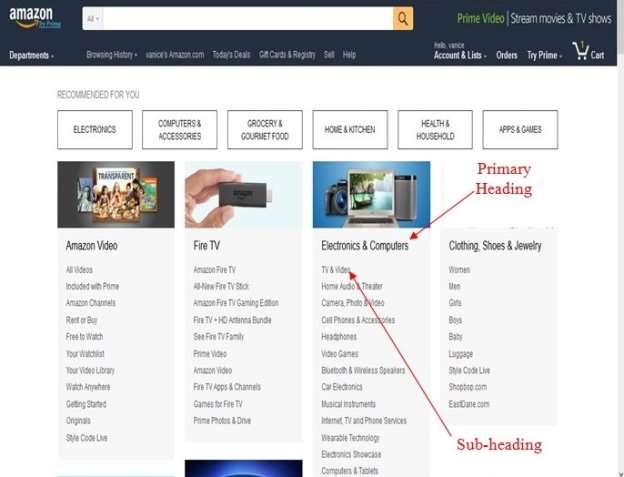
Same retailer, Amazon utilizing structured navigation with the added user ability of headings and sub-headings.
Information Security
Vacca (2014) defines Information as data that we can organize and process and store distributive or centrally. Any company large or small, data is the most valuable asset and must be securely protected. In terms of the Customers, a data breach could result in the loss of financial information in the form of credit card information and other crucial details. Consumers may lose faith and credibility in the Company for data lose which in turn could cause the total demise of the Company.
It is imperative Swagger Distributions has a well conceived plan of attack and also a preventive plan as well. This past year, half of organizations suffered multiple levels of security incidents. It is recommended that a centralized security team be hired. This team will be responsible for coordinating and executing the security plans.
In keeping with a Central Security Team concept there should be a dedicated Security Monitoring team keeping “real time” track of Applications that has access to Swagger Distributions Data. Statically, “hackers attack through the least secure Applications (Vacca, 2014, p. 3)”; making it easier to corrupt and steal sensitive information. This Monitoring team will report directly to the head of the Central Security Team.
“One of the largest data break-ins in history (Consumers International, 2015, p. 417);” Sony Play Station Network was hacked April 2011. Consumers International (2015) reported the attack is speculated to be an external intrusion that caused the reveal of reported 77 million user accounts information. This information included names, birthdays, email addresses, passwords, security questions, and credit card credentials, of all Play Station Network users. The hack was reportedly caused by an “unknown weakness (Consumers International, 2015, p. 418)”. In Sony’s Network causing Sony to temporarily shut down their Network to investigate.
References
Consumers International (2015). Consumers in the Information Society: Access, Fairness and Representation. Consumers International.
Dahl, D. (2017). Multimodal Interaction with W3C Standards. Springer.
Downing, D. A., & Downing, D. (1999). Computer programming in java, the easy way. New York, NY, United States: Barron’s Educational Series Inc.,U.S.
Microsoft (2017a). Microsoft – A Beginner’s Guide to Visio. . Retrieved from : https://support.office.com/en-us/article/A-beginner-s-guide-to-Visio-bc1605de-d9f3-4c3a-970c-19876386047c
Microsoft. (2017b). Support. Retrieved from Microsoft – Blog, https://support.office.com/en-us/article/Specify-how-data-displays-by-using-custom-formatting-a5e5bcde-85da-4c7a-8164-1fe286636668?ui=en-US&rs=en-US&ad=US
Tomsho, G., Tittel, E., & Johnson, D. (2015). Guide to networking essentials (7th ed.). United States: Thomson/Course Technology.
Vacca, J. R. (2014). Computer and information security handbook (2nd ed.). Amsterdam: Morgan Kaufmann Publishers is an imprint of Elsevier.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


