Evolution of Mobile Device Technology
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 2801 words | ✅ Published: 18 Aug 2017 |
Introduction
Since the revolution of the smartphone in 2005 the development progress in this field grows rapidly. It became a part of our life and played a big role to change the attitude of our life style. This technology (smartphone) didn’t stop at that level but it spread everywhere to cover all sides of our daily activities. Even anew terminology appear to name this technology is Internet of Things (IoT) where this concept describe any device connected to the internet. All this technology convert our life to something called smart, so nowadays we have smartphones, smart home, smart car ext. These smart devices facilitate our daily tasks where no need to set on the front of the computer or trying to find an open Wi-Fi because you are expecting an important email you don’t know when it will be delivered to your inbox. This technology gave the people almost everything they need which has made people ask for more and it became their partner or even addicted. Day by day people relay more and more on the smart technology and they share all information even sometimes the secrets. This information start attract some people for any reason either to sell this information to third party or to blackmail their victim. This bring a new challenge to everybody in the society and there are a new cases daily because of the smart devices. The device can be a tool to attack the victim data or it found in the crime scene in both scenarios can be consider an evidence.
Mobile device technology
The mobile devices evolution is linked to the mobile technology where each one effect on the other one. Because the mobile device technology required a specific features.
First Generation
By looking to the first generation and list it’s features we can guess what kind of mobile device technology can be used in that period. According to (Agrawal, 2015)] the first generation was analog it was introduced in 1980. The technical specification was not that much where they focused on produce a mobile phone. The main feature of 1G mobile
- Speed up to 2.4 kbps so it was used for calling only
- It use analog signals (analog telecommunications standards)
- Poor voice quality
- Poor battery life
- Limited capacity
- No security
Focusing on the last two points because they are related to the research paper. Regarding the security at that time 1G does not support the encryption. The security was limited where some phones (e.g. Mitsubishi MT-7) in 1993 has a pin code only. The memory as well didn’t get that much attention, but later on in 1989 Motorola (8900X-2) add a small volume of memory which can store 20 telephone numbers in the address book. This generation is limited in everything even in the forensics user couldn’t do bad things with it just verbally.
Feature phones and smartphones
From second generation the improvement obviously in the mobile device technology. (Qualcumm, 2014) Show the evolution on theses generations used digital signal compare to the first generation. This change took the mobile devices technology ahead with new features the users didn’t experience them before in the previous versions of 1G mobile devices. In these generations there are basic features with different specifications. The diagram (DAS, 2015) show the different parts of the mobile phone.

As the diagram shows the mobile device component, most mobile devices have a common hardware component (GSM Mobile Phone, n.d.), consist of microprocessor, a radio module, read only memory (ROM), a microphone and speaker, random access memory (RAM), a digital signal processor, a variation of hardware keys and interfaces and display screen. The operating system (OS) of a mobile device may be stored in either NAND or NOR memory while code execution normally happens in RAM. The general changes in the mobile devices is the size (capacity, screen) and the speed as well the quality of the display, but some time do any change in the phone means change the component chips used. This changes can lead to another technology.
Overview of the feature phone and smartphone
|
Feature phone |
Smartphone |
|
|
Processor |
Limited speed(~52Mhz) |
More speed(~1GHz dual-core) |
|
Memory |
Limited capacity(~5MB) |
Large capacity(~128GB) |
|
Data transmission Speed |
64-144 kbps |
300 mbps |
|
Display |
Small size color, 4k -260k (12-bit to 18-bit) |
Large size color, 16.7 million (~24-bit) |
|
Card slot |
None, MicroSD |
MicroSDXC |
|
Camera |
Still, Video |
Still, Panoramic, and Video(HD) |
|
Text input |
Numeric Keypad, QWERTY-style keyboard |
Touch Screen, Handwriting Recognition, QWERTY-style keyboard |
|
Voice input |
None |
Voice Recognition (Dialing and Control) |
|
Cell interface |
Voice and Limited Data |
Voice and High Speed Data transfer (4G and LTE) |
|
Positioning |
None, GPS receive |
GPS receive |
|
Wireless |
IrDA, Bluetooth |
Bluetooth, Wi-Fi, and NFC |
|
Battery |
Fixed/Removable, Rechargeable Li-Ion Polymer |
Fixed/Removable, Rechargeable Li-Ion Polymer |
Feature phone and smartphone has common facility, but the capability is much different. Where both types of phone support SMS (text messaging), voice and personal information management such as phonebook and calendar. Smartphone has a better capabilities and larger then feature phone where it support better screen resolution and have integrated keyboard or touch screen. Smartphones act as a small PC and support wide range of applications.
There are many operating system (OS) (Guru, 2015) in the market for the smartphone the top OS popular are Symbian (Nokia), Android (Google), Apple IOS, Blackberry (RIM), Windows (Microsoft) and BADA (Samsung). These operating system support multi-tasking and designed to match the user requirements for a high end mobile device. Feature phones has a closed operating system, so the supported applications, games, personal information management and chat are limited.
Memory
Mobile devices contain two types of memories. The first type is volatile memory and the second one is none-volatile both of them work side by side. The volatile memory (RAM) is used for code execution. This type of memory is effected by the power, so if the power goes off RAM is lose all contents. The second type is non-volatile memory the contents are not effected when the power goes off.
The main technologies for non-volatile flash memories are NOR and NAND. NOR memory first introduced in 1988 by Intel. In 1989 Toshiba introduced the NAND flash technology which has many benefits over NOR memory. NOR came to replace ROM with EPROM and EEPROM. The most advantage of NOR is the reading speed faster than NAND. In the other hand NAND has many features which is not applicable for NOR. These are the general difference between NAND and NOR
- NOR reads slightly faster than NAND.
- NAND writes faster than NOR.
- NAND erases data much faster than NOR.
- NAND has smaller erase units, so less erases are needed.
There are different types of NAND memories but the paper focusing on the EMMC and UFS.
EMMC stand for embedded multimedia card this chip is an advanced managed memory. According to (Samsung, 2013) it is widely used in phones, cameras, GPS and smart TV. It helps the designer to save time and make the product thinner. Also it enhanced the storage capacities and speed. One of the advantage of EMMC reduced the development time and control cost. The NAND memories before EMMC required changes either in the chipset or the OS. EMMC is a half-duplex because the interface is parallel so it will be read or write.
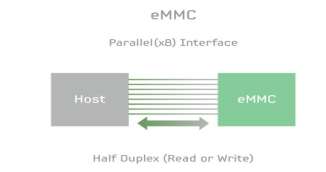
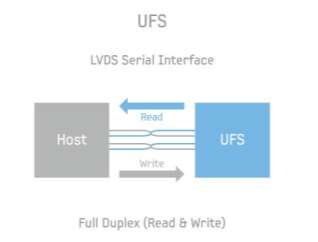
UFS
Mobile devices growth rapidly last few years this bring a challenge to the manufacturer to add memory that (Toshiba, 2015) will have a high bandwidth, high capacity, low power consumption and low cost. These factors were very important to improve the mobile devices. Because adding ordinary extra memory it will increase the cost of all mentioned factors. In 2014 Samsung announce about the new memory which meet the requirements of the four factors of the manufacturer. Universal flash storage (UFS) was built specially for mobile devices which required low power and at same time provide high performance. UFS is a full duplex because it has serial interface read and write done separately.
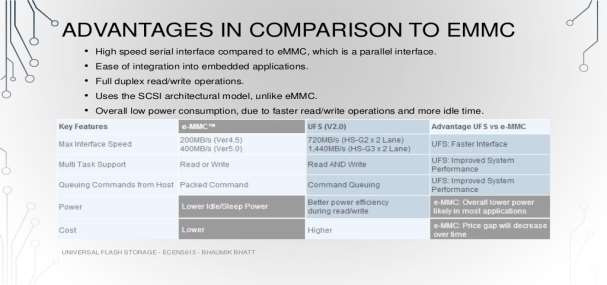
The image below (BHATT, 2014) shows the advantage of UFS over EMMC
Challenges according to (Zareen, 2010):
The major challenges in mobile forensics are:
- The changes in the architecture of the new released of mobile devices, where the examiner has to be up to date and do more tests to be sure he can do data extraction.
- The new mobile devices it has the ability to encrypt the date this can be a big challenge to the examiner.
- Hardware differences there are different brand and model of mobile devices in the market the examiner has to come across as much as can of brands and model to be familiar about the technology.
- Lack of resources the rapid growth of mobile devices required new tools and acquisition accessories.
- Anti-forensic techniques make the investigation more difficult, as an example data hiding, data obfuscation, data forgery, and secure wiping.
- Passcode recovery the examiner has to work carefully to access the device without damaging the data.
- Malicious programs can be a challenge to the examiner it may attempt to spread to other devices over the wired interface or a wireless.
- Safety the examiner life can be on danger, the device can contain different kind of risk on the examiner life. The device may contain a biology or chemical hazards which will impact on the examiner.
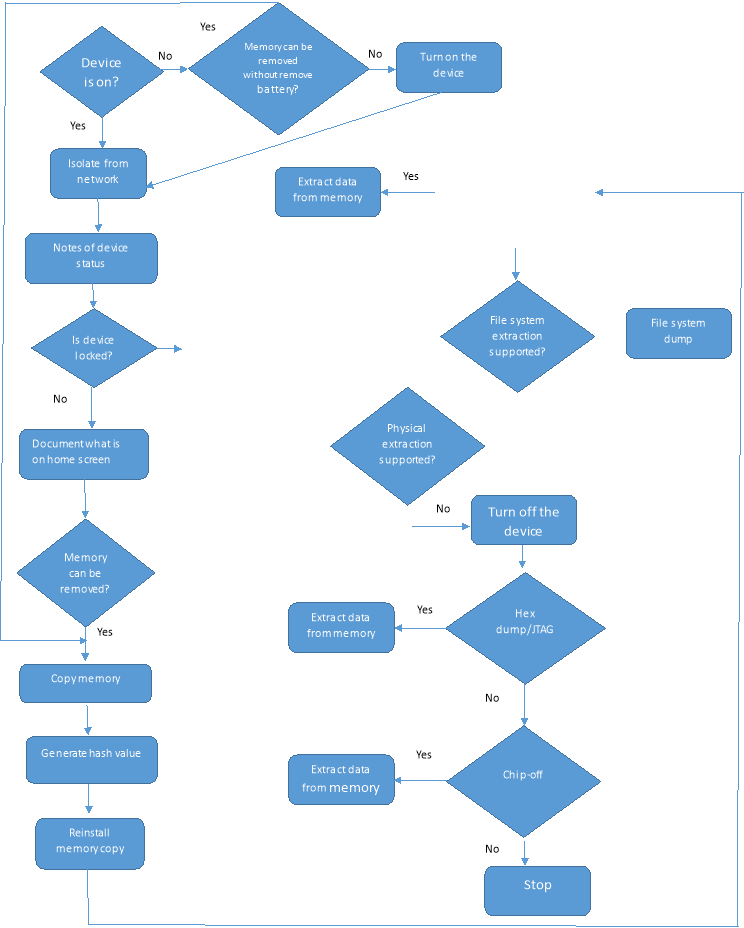 Data acquire process
Data acquire process











Capability
Logical extraction, file system and physical extraction normally done by software. Even the locked mobile devices and with passkey can be unlocked using software. Not all mobile devices support the same process of data acquisition.
Joint Test Action Group (JTAG) support in-system (ISP) programming and reading. It is an advanced hardware level data acquisition in the physical extraction stage. It depend on the Test Access Ports (TAPs) of the device and instructing the processor to transfer the raw data stored on connected memory chips. If the memory support JTAG then the TAP can be addressed of the memory through the JTAG interface. All memory address goes the though the data bus and it can be read by shifting the boundary-scan register value through JTAG chain. In this way the entire memory content can be read by find the memory address. The entire memory can be copied in this way. If the memory doesn’t support the JTAG then it can connect to TAP of another device this could be the processor. The processor has direct access to the memory through the system bus. By connecting to CPU TAP the memory can be read.
Steps of JTAG according to (Elder, n.d.)
- Identify TAPs by researching the forums and related websites as well documented devices. If the TAPs cannot be identified then check the device PCB for possible TAPs and trace it manually to find appropriate connector pins.
- Solder wires to the pinout in the mobile device.
- Connect the other side of the wires to JTAG emulator (RIFF box, volcano, ATF nitro).
- Select the memory sitting than read the flash memory.
- Analyze the data with the forensics tools.
Chip-off
Chip-off forensics is the next level if the JTAG method not work properly to extract data. This level involve physically remove the flash memory to extract the data from the mobile device then acquiring the raw data using specialized equipment. This way is powerful where it can be used to collect all data from the memory even if the device is damaged jut memory must be in a good condition. The examiner must pay attention to highest temperature can apply the chip to remove before it get damage. According to Samsung the temperature range of EMMC used in mobile devices are -25°C ~ 85°C.
- Remove the memory (de-soldering) chip using appropriate heat (-25°C ~ 85°C) always the examiner must monitor the temperature to be within the range.
- Clean the chip carefully to remove the comical suck on the chip memory.
- Use special chip programmer and adapter to acquire the data from a variety of flash memory (UP-828P Programmer).
- Analyze the data with the forensics tools.
Samsung T479 Gravity 3 feature phone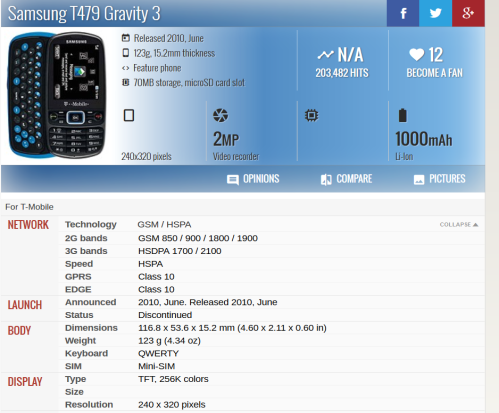
Manual extraction
- if the device is on and unlocked
- Isolate from the network
- Check battery status
- Check device status
- Record date and time
- Browse the device content using keypad or touch screen
- If the device powered off or locked
- Isolate from the network
- Check device status
- Turn on the device
- If not start try to charge it
- If can’t be charge stop proceed
- If the device start but it is locked stop process
Challenges
- Deleted data can’t be retrieve because no tools used to extract data in this stage.
- Error may accrued.
- Browse the device it can be difficult because broken buttons or touch screen problem.
Tools used to record the evidences.


Ramsey’s STE3000FAV Project-A-Phone
Logical extraction
This stage required special software to extract data from the device.
- If the device is on and unlocked
- Isolate form the network (disable Wi-Fi and hotspot, airplane mod)
- Check the status of the device
- Document what on the screen and the apps running in the background
- Enable USB debugging and stay awake
- Check memory card availability
- If available copy card
- Create hash value
- Reinstall copied memory
- Connect mobile to PC has software to extract data
- List of data can be get in logical extraction
- Phone book
- Call Logs
- SMS
- Calendar
- MMS
- ESN/IMEI
- Pictures
- Videos
- Ringtones
- Audio/Music
- Memory Card
- If the device is locked
- connect to a PC has software to break lock (most of forensic tools)
- follow steps in 1
- Tools used in this stage
UFED 4PC, Oxygen and Xry (SIM call not supported)
- Challenges
- Can’t retrieve deleted data
File system
- If the device is on and unlocked
- Same procedure as logical extraction
- List of data can be get in logical extraction
- Extract user lock
- Files Decoding
- File System Reconstruction
- Bookmarks
- Calls
- Contacts
- Installed Applications
- MMS
- Notes
- SMS
- Web History
- Tools used in this stage
UFED 4PC, Oxygen and Xry (SIM call not supported)
- Challenges
Physical Extraction
This phone doesn’t support physical extraction.
JTAG
This phone support JTAG
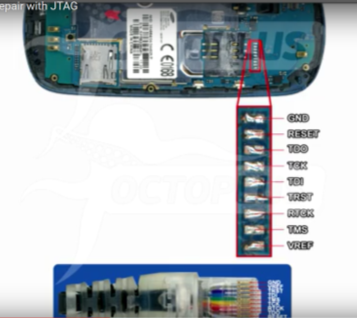
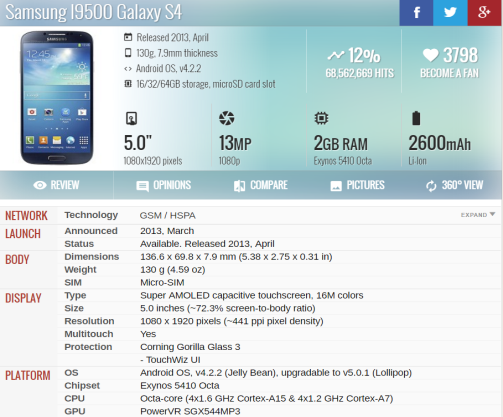

Samsung I9500 Galaxy S4 motherboard
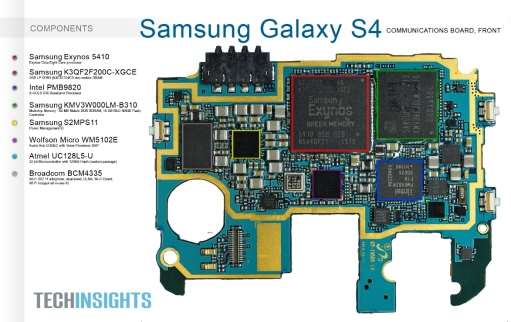
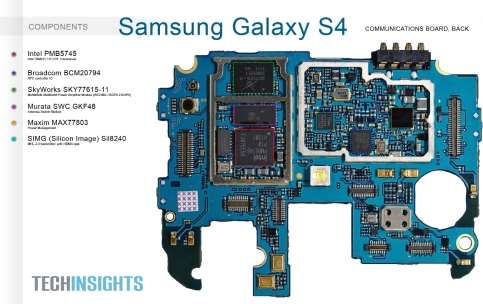
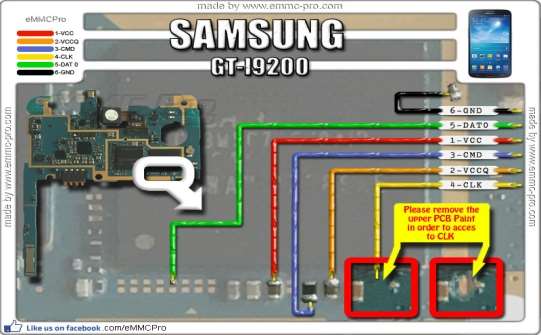
|
Process |
Samsung T479 Gravity 3 |
Samsung I9500 Galaxy S4 |
|
Manual extraction |
Yes |
Yes |
|
Logical extraction |
Yes |
Yes |
|
File system extraction |
Yes |
Yes |
|
Physical extraction |
No |
Yes |
|
JTAG |
Yes |
Yes |
|
Chip-off |
Yes |
Internet of thing overview
Internet of things (IOT) refer to any physical device which can have an IP address and connected to the internet. According (Fremantle, 2015) the IOT come to facilitate people life and make it easier.
It will touch every aspect of our lives, including our houses, work places, transportation and even our bodies. This new technology make humans overcomes the location obstacle between people and the machine enabling them to communicate and interact intelligently. Rapid growth of Information Technology already allowed Internet of Things to start to be as a reality in recent days. If we look around us, we already started to see and touch the smart phones, home automation, smart traffic lights, smart sensor devices at industrial locations, Health services, Radars, Environment Researches, and many other sectors. Definitely, the future of IoT will be full of surprises and new unexpected and unpredictable technologies might be introduced. IoT technology is significantly growing at a critically dangerous pace and Information Technology Researchers predict that by the year 2020, 10th of billions of wireless devices will be connected wirelessly as part of the IoT industry. People will be able to do unimaginable things remotely in an unbelievable time and it is expected that almost anything might be connectable.

According to (Lobaccaro, 2016) there are four categories:
1. Integrated wireless technology (IWT);
2. Home energy management system (HEMS);
3. Smart home micro-computers (SHMC);
4. Home automation (SHS/HA).
Agrawal, J. (2015). Evolution of Mobile Communication Network: from 1G to 4G.
BHATT, B. (2014, 4 13). Universal Flash Storage. Retrieved from Slideshare: https://www.slideshare.net/BhaumikBhatt4/universal-flash-storage
DAS, S. (2015, 8 18). Parts of a Mobile Cell Phone and Their Function. Retrieved from http://www.mobilecellphonerepairing.com/parts-of-a-mobile-cell-phone-and-their-function-big-parts.html
Elder, B. (n.d.). Chip-Off and JTAG Analysis. Retrieved from Evidence: http://www.evidencemagazine.com/index.php?option=com_content&task=view&id=922
Fremantle, P. (2015). A REFERENCE ARCHITECTURE FOR THE INTERNET OF THINGS.
GSM Mobile Phone. (n.d.). Retrieved from RF Wireless World: http://www.rfwireless-world.com/Articles/gsm-mobile-phone-basics.html
Guru. (2015, 10 28). Top 10 Mobile Phones Operating Systems. Retrieved from shout me: https://www.shoutmeloud.com/top-mobile-os-overview.html
Qualcumm. (2014). The Evolution of Mobile.
Samsung. (2013). Samsung Smart Memory. Samsung.
Toshiba. (2015). UFS memory. Toshiba.
Zareen, A. (2010). Mobile Phone Forensics Challenges.
http://forum.gsmhosting.com/vbb/f672/guide-how-find-direct-EMMC-pinout-step-step-pictures-1724774/
https://www.oxygen-forensic.com/download/articles/Oxygen_Forensic_Detective_Getting_started.pdf
https://blog.elcomsoft.com/2016/01/forensic-acquisition-android/
http://www.bulleproof.com/Papers/Android%20Forensics%20Techniques.pdf
https://blog.elcomsoft.com/2016/01/forensic-acquisition-android/
https://www.hackingloops.com/android-forensics-tutorial-4-unlock-android-pattern-lock/
http://resources.infosecinstitute.com/android-forensic-logical-acquisition/#gref
https://digital-forensics.sans.org/media/DFIR-Smartphone-Forensics-Poster.pdf
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal Mobile device
Mobile device


