Case Study on Network Management Protocols
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 2708 words | ✅ Published: 23 Sep 2019 |
Table of Contents
Introduction
AUT is one of the biggest Universities in New Zealand and has 3 campuses in different locations; City campus, North campus and South campus. Every campus has 1200-1500 users who use wireless connections, around 250-300 personal computers. VOIP services to cut down cost of phone lines. AUT has outsourced the IT services to a third party called ‘Netcom’ and they are responsible for configuration, troubleshooting and managing the network. However Netcom is charging a huge amount for these services. So, to avoid this AUT management decided to take case of these services themselves and hired Mr Hanks as network manager. Currently AUT is facing a member of network related issues like Mr Hanks has to provide a solution to the issues after analysing the network, taking measures of different KPI;s and traffic patterns with appropriate network management tools, software and techniques for AUT.
Task 1
(A) Based on the case study provided, evaluate at least two (2) Network Management Protocols and apply the most suitable protocol on current wireless network for analysis of traffic pattern.
A: Network Management Protocol is applicable to all network enabled devices like switches, routers, computers and servers. The two popular Network Management Protocols are ICMP (Internet Control Message Protocol) and SNMP (Simple Network Management Protocol).
Internet Control Message Protocol (ICMP): It is used to report errors and diagnose problems with the network layer as IP doesn’t provide any guarantees about delivery but it helps and will prove a valuable tool to get some hints and information when something goes wrong in the network. ICMP helps communicate information about the network layer between the end host and the routers. When an end host or router wants to report an error using ICMP it puts the information that it wants to send back to the source into an ICMP payload and gives it to IP to send as a Datagram. This Datagram is a simple message which does not make any attempt to resend the message and it typically contains an indication of what the problem is for the packet to be not forwarded. (Techopedia)
Simple Network Management Protocol (SNMP): This protocol allows us to proactively view what’s going on with all the devices and computers in our network and fix issues before they become major problems. SNMP is usually a component used in larger software package, e.g.: Spiceworks and land view. SNMP provides information from the device in real time. SNMP sends alerts to the management console incase if anything goes wrong with the hardware of the devices this helps us detect an issue before it becomes a major problem. (Techopedia)
Based on the scenario I would like to recommend AUT to implement SNMP as the North and South campus are having issues like DNS is unknown, limited connection, IP conflict and not getting IP address from server. However, if AUT uses ICMP it will only provide information if the IP is working or not working. But in regards to SNMP it will give detailed information about IP if it is working or not. The IP conflicts along with solution, the usage and network traffic.
(B) Based on the case study provided, analyse at least three (3) different key parameters that can affect the performance of wireless local area network.
A: Interference in the network is inevitable, however it can be avoided if IT teams take measures. There are many parameters that can affect the performance of the AUT WLAN. Below are the three parameters affecting the WLAN based on the scenario provided by AUT.
Network Latency: The time taken to send a packed from source to destination is called Network Latency. The time varies depending on the below situations.
Physical Distance
Number of devices to be crossed
Performance of each device (Rogier, 2016)
Network Congestion: When the path between the source and destination is overloaded while sending a packet is called Network Congestion. If packet does not reach the destination in time due to being dropped or put in queue then it will be difficult to set up a new session or if no queuing system is available. (Rogier, 2016)
Network Interference: As the WLAN is very commonly used and is more popular these days, there are chances that the signal operates through the same frequency which causes interference. When the signal is interfered it put a negative effect on the performance of the AUT network. Due to overcrowding the most popular frequency (2.4GHz unlicensed band) gets severally affected and reaches a stage where the device cannot perform at an expected level. AUT needs to work with businesses, operators etc. around to avoid future interference problems as it has a huge number of users. (4Gon Solutions)
Task 2
(A) Evaluate at least two (2) network management tools and select the most appropriate tool for the case study provided. Explain how the selected tool could be helpful to enhance the performance of the WLAN in the city campus in terms of coverage, bandwidth utilization and monitoring.
A: Network management tools are important for many reasons like the tool can provide real-time view of the service status and infrastructure health. Mostly these tools are used to check signs of poor performance on the network. The two popular network management tools are solar winds and zabbix.
Solar-Winds: This network performance monitor is easy to set and is functional at real time. This tools detects issues quickly, diagnose the issue and it gives accurate solution. Solar winds tool manages and monitors the network and also manages wireless network on separate location. This tool is mostly used to analyse bandwidth and traffic congestions of network performance. The IT team can create a design a tailored topology and also create customized dependency aware intelligent alerts for entire network infrastructure. (Wilson)
Zabbix: This is an open source tool for monitoring and the main focus for this tool is to monitor and trend functionality. This software is mostly used to monitor network hardware and servers. Zabbix provides the use of open source solution with vendor lock-ins which includes all components. A combination of SNMP and IMPI is used by Zabbix. This tool performs well in the area of customization. (KEARY, 2019)
After considering both the options given above I would recommend AUT to use solar winds to resolve their issues.
|
Issues |
Benefits of using Solar Winds |
|
Bandwidth, coverage and monitoring |
It quickly finds the issue with performance in the network with critical path visualization feature. |
|
Concerns related to hardware routers, server, switches, firewall, desktop |
Can monitor WLAN and VPN easily and provide quick and accurate solution avoiding downtime. |
(B) Based on the case study, analyze at least two (2) network management techniques to find out the reason of frequent network connection loss and network congestion.
A: Network technique is used for planning, scheduling (programming) and controlling the progress of a network. It provides an effective management, determines the project duration more accurately and identifies the activities which are critical at different stages of the network. Below are the two network management techniques that will help to find out the reason of frequent network connection loss and network congestion in AUT.
Connection Admission Control (CAC): In a network communication a set of actions and permissions are used that identifies where the connection is permitted based on the network ability. These sets of actions are usually used during a call set up or when call is being reconnected. CAC is used to decide which traffic is allowed or rejected by a specific network. CAC plays an important role especially for traffic congestion control.
CAC performs the following two operations while establishing a connection:
- Establishment of connection when resources are free and available.
- A notification is sent back to the requester of the call or connection when the connection is rejected in the absence of free or available resources. (Techopedia)
Selective Packet Discard (SPD): This technique is used to manage the process level of queuing on the Router Processor (RP). The main goal of SPD is to allow and give priority to IOS traffic which is important for network’s stability when the interface input queue is congested. SPD is available on all Cisco routers. Two additional queues are created when SPD is enabled, the SPD Headroom and the SPD Extended Headroom. (nyquist, 2012)
Task 3
(A) To resolve the problem of WLAN IP address allocation with the knowledge of troubleshooting methodology, apply appropriate steps to troubleshoot the failure of IP address allocation. At least six (6) to be discussed.
A: The below steps need to be followed to resolve WLAN IP address allocation failure:
Check if all the access point is well configured in the WAN and VLAN and router configuration can be checked manually.
Configure the router with radius protocol.
Check if the IP pool is full and also the task display the availability of the IP address. By providing enough IP addresses we can adjust the mask length.
To resolve the problem of WLAN IP allocation we must check the DHCP server database. The issue can be resolved if we check the host’s network configuration.
Check if the requested IP address is not in DHCP, the request is dropped by the server for IP allocation.
Check if the lease was not negotiated and timed out. (Phifer)
(B) The monitoring of the inter-campus WAN links is crucial to ensure smooth network operations. Analyze at least three (3) reasons for the links failure and suggest most suitable solution.
A: As per the scenario AUT needs to operate network smoothly and for that take into consideration the most common reasons for link failure and their solution. As a network administrator below are the three link failure reasons that I came across along with a solution.
Device failure: When the device is not functioning properly due to maintenance reasons or is broken causes link failure.
Solution: To avoid this failure the IT teams needs to complete the required maintenance in time and any broken devices should be replaced as soon as possible so that the downtime does not affect the productivity. (Prescient solutions)
Power outage: Power outage happens due to bad storm, floods and lighting which causes short circuits and results in link failure in the system.
Solution: To avoid the power outage problem a backup needs to be there and UPS one of the commonly used solution. It helps us create an immediate data backup and save data to the data centre avoiding any data loss. (Prescient solutions)
Human error: Link failure happens when people don’t have the knowledge about the system and use incorrect commands , pulling out incorrect plug, manually updating incorrect setting or incorrect installation, also moving the servers can also cause link failure
Solution: Providing proper training and be attentive while working with server rack or the power cord to avoiding damage. Configuration and installation should be done under supervisor attention. Signs should be placed around in regards to using the plugs. (Prescient solutions)
Task 4
You are provided with a simulated Packet tracer file of a network by the lecturer. You are required to apply the troubleshooting techniques to resolve the following problems using the Packet tracer tool:
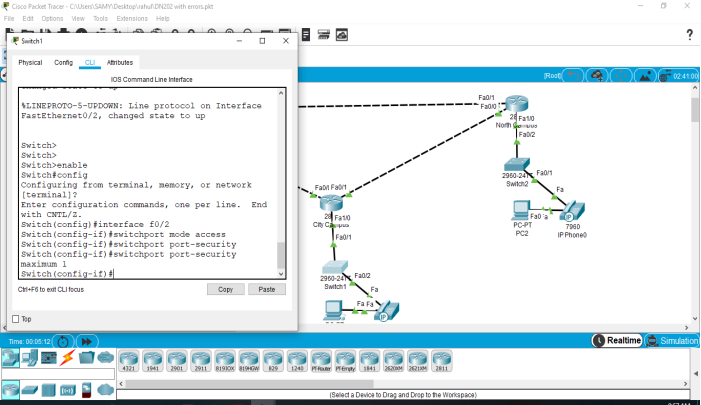
1) Port turns down as a computer is attached to the switch in the city campus LAN
A: If the new computer is attached to the switch and it turns down the reason behind that the SWITCH PORT SECURITY
Switch port security means it only allows one computer at one time. So if you want to connect more than one computer you have to setup SWITCH PORT SECURITY up to 5.
Switch port security enables switch to read the MAC address and allow connection to specific MAC address one at a time and saves it. When a computer with different MAC address is connected it prevents connection. The reason why the ports turn down when the computer is attached with network because the there is limitation of only one computer. when we connect the computer, switch read the MAC address and save the MAC address. On the other side, when we connect the other computer it does not allow to access, the MAC address does not match.
Below is a network diagram which will help us understand Switch Port Security Layout. In this case, we can configure the SWITCH- POTS SECURITY:
2) IP leasing takes excessive amount of time and releases within an hour in case of WLAN
A: IP leasing takes excessive amount of time and releases within an hour in case of WLAN because lease time of 1 hr is set by every company, so it is very easy to set more lease time if you want to do it.
In WLAN setup, most organization for security reasons prefers to have 1 hour of IP lease time. This time can be modified by using the below command. The reason why it happens is because every company in WLAN set the lease time up to 1 hour.
So if you want to get more lease time you can set easily.
DHCP – LEASE [DAYS[HOURS[TIME]]]
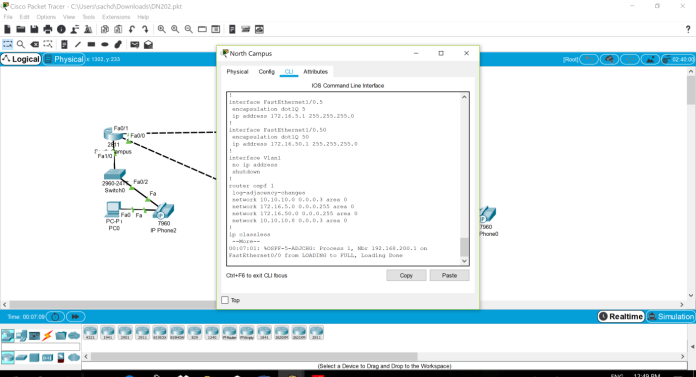
3) Auto failover to be verified to resolve the issue of north-south WAN connectivity.
A: In north and south campus the path is not defined accurately that’s the reason auto failure occurs. There was no routing in north and south campus so we did routing as shown below.
Auto failover could occur due to incorrect configuration or setup of path between North and South campus. By implementing OSPF routing we could prevent such failover. The reason why the auto failure occurs because the path or route in the NORTH CAMPUS is not defined between the NORTH AND SOUTH.
We can make the route between the NORTH and South campus with the help of OSPF ROUTING
#router ospf 1
#network 10.10.10.0 0.0.0.3 area 0
4) VoIP services are not working fine for inter-campus communication
A: In north campus the IP given to phone is incorrect and IP of phone in city campus is not configured that’s the reason VoIP services are not working fine for inter-campus communication.
VOIP services need correct configuration of IP address of phone and have VOIP services at both locations. In this case at North campus the IP address of the phone is 172.16.50.2, instead of 172.16.5.2. In addition the City campus does not have VOIP configured. VOIP service is not working the reason behind that in NORTH campus the IP address of PHONE is not correct which is 172.16.50.2 which should be 172.16.5.2 and in CITY campus there is no VOIP configured.
5) One of the switches in city campus restarts very frequently
A:
Bibliography
- 4Gon Solutions. (n.d.). https://www.4gon.co.uk. Retrieved January 25, 2019, from https://www.4gon.co.uk: https://www.4gon.co.uk/solutions/technical_factors_affecting_wireless_performance.php
- battosai. (n.d.). freeradius. Retrieved from http://freeradius.1045715.n5.nabble.com/IP-Allocation-FAILED-td5733376.html
- chron. (n.d.). Retrieved from https://smallbusiness.chron.com/determine-router-failing-35890.html.
- Harwood, M. (2009, June 9). http://www.pearsonitcertification.com. Retrieved January 24, 2019, from x
- KEARY, T. (2019, January 23). https://www.comparitech.com. Retrieved January 25, 2019, from https://www.comparitech.com: https://www.comparitech.com/net-admin/network-monitoring-tools/
- nyquist. (2012, November 12). http://nyquist.eu. Retrieved January 25, 2019, from http://nyquist.eu: http://nyquist.eu/spd-selective-packet-discard/
- Phifer, L. (n.d.). https://searchnetworking.techtarget.com. Retrieved January 25, 2019, from https://searchnetworking.techtarget.com: https://searchnetworking.techtarget.com/tip/Wireless-network-troubleshooting-Connectivity
- Rogier, B. (2016, October 12). https://accedian.com/enterprises. Retrieved January 24, 2019, from https://accedian.com/enterprises: https://accedian.com/enterprises/blog/5-network-performance-factors-slow-data-transfers-identify/
- Techopedia. (n.d.). https://www.techopedia.com. Retrieved January 25, 2019, from https://www.techopedia.com: https://www.techopedia.com/definition/5473/simple-network-management-protocol-snmp
- Techopedia. (n.d.). https://www.techopedia.com. Retrieved January 26, 2019, from https://www.techopedia.com: https://www.techopedia.com/definition/24887/connection-admission-control-cac
- Techopedia. (n.d.). https://www.techopedia.com. Retrieved January 26, 2019, from https://www.techopedia.com: https://www.techopedia.com/definition/24887/connection-admission-control-cac
- Wilson, M. (n.d.). https://www.pcwdld.com. Retrieved January 24, 2019, from https://www.pcwdld.com: https://www.pcwdld.com/best-network-monitoring-tools-and-software
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


