UAV Swam Communication Architectures
| ✅ Paper Type: Free Essay | ✅ Subject: Communications |
| ✅ Wordcount: 2512 words | ✅ Published: 23 Sep 2019 |
- Introduction
Swarms are a collection of simple individuals who work together to complete complex tasks that are beyond the capabilities of a single individual. Individuals in swarms are autonomous, meaning they can sense, communicate, and act independently [1]. Planning and decision-making are performed cooperatively by the individuals rather than a central authority [2]. Characteristics of swarms include robustness, flexibleness, and scalability which are defined as follows [1]:
- Robustness is the ability for a swarm to keep functioning reliably with the loss of individuals and this is achieved through redundancy and the lack of a leader.
- Flexibility is the ability to function under a variety of different environments and to complete a variety of different tasks.This is achieved by redundancy and the simplicity of individual’s functions in the swarm.
- Scalability is the swarm’s ability to function with varying swarm sizes. Individuals being removed or added do not alter the swarm’s performance.
Robot swarms aim to complete complex tasks that are either too costly, unfeasible, dangerous, or too complex for single robots or humans to do. Robots in swarms can be aerial, ground, or aquatic systems. Currently, there is growing interest in unmanned aerial vehicle (UAV) swarms to complete complex aerial missions. Examples of these missions include space exploration, navigating hazardous environments, surveillance, search and rescue missions, post-disaster relief, and land surveying for agricultural and environmental systems. The extent of these applications is limited by the size, weight, and power (SWAP) constraints of each UAV. Over the last decade, there have been considerable technological advances in the design of UAV swarms. However, insufficient work has been done to secure communications between UAVs in swarms.
Despite the growing interest in UAV swarms and the high importance of securing their communications, only a few research papers have been published in this area. A survey that provides an overview of UAV swarm communication and security is highly needed. In this paper, we present a comprehensive survey about UAV swarm security. Topics covered include communication architectures, attacks targeting UAV swarms, existing detection and countermeasure techniques, security challenges, and future research directions. The rest of this paper is organized as follows. Section II. discusses UAV swarm communication architectures. Section III. provides an overview of attacks targeting UAV swarms, existing detection and countermeasure techniques, security challenges, and future research directions.
- UAV Swam Communication Architectures
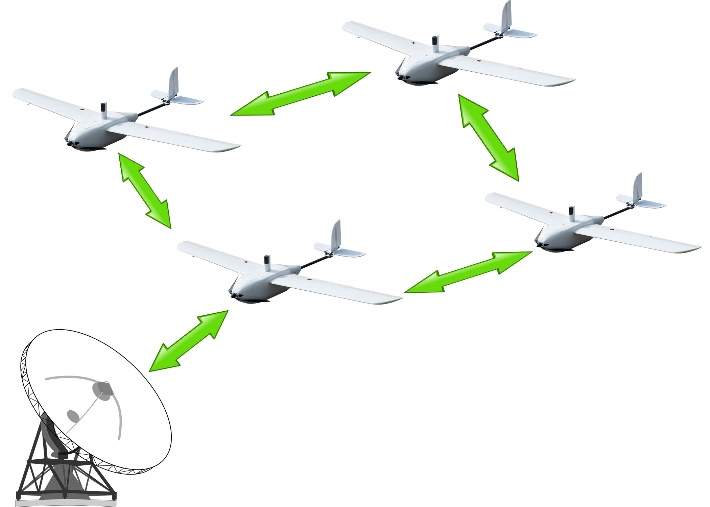
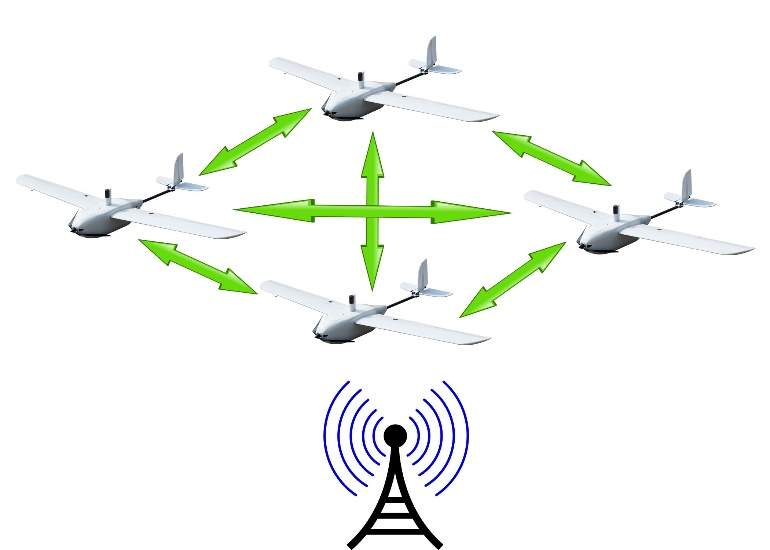
When designing communication networks for UAV swarms, elements like topology, bandwidth, communication range, and protocol must be carefully taken into consideration to ensure reliable and secure communications. Networks are infrastructure-based, ad-hoc or some combination of both based on the desired topology [3]. In an infrastructure-based swarm network, UAVs do not communicate within the swarm rather they communicate with a ground control station (GCS). UAVs are organized in a star topology. The swarm are dependent on this central authority for coordination. If the communication between the swarm with the GCS is compromised because a cyber-attack or a failure of the GCS, the swarm will fail to operate reliably. Communication range is also limited as all robots need to be in proximity of the GCS. Ad hoc networks do not rely on existing infrastructure or a central authority and individual robots directly communicate with each other independently. Ad-hoc networks utilize a mesh topology which means if one node fails, data can be routed through another path, thereby enhancing robustness. Most research related to UAV swarm communication has been done using one of two communication networks: Flying ad-hoc network (FANET) and Mobile ad-hoc network (MANET) [3]. FANET is a hybrid swarm communication architecture that relies on a lead node to communicate with the GCS and to relay information to the rest of the swarm [4]. In this architecture, UAVs can communicate with each other directly but only the lead node can communicate with the GCS. This only partially solves the problem of distributed decision making in infrastructure-based swarm architectures because severed communication between the GCS and the lead node can still result in swarm failure. Another problem is that the UAV lead has to be in close range of the GCS. Fig. 1 illustrates how communication is done in FANET. MANET is an ad hoc network where UAVs communicate with each other without the need for a central authority [3]. Because it is decentralized, decision making is distributed, as shown in Fig. 2. Compared to FANET, this type of architecture presents some advantages in term of security. Attacking a UAV in this architecture does not significantly impact the overall swarm security.
|
|
|
Fig. 1: Communication in FANET Fig. 2: Communication in MANET
For both architectures, signals which are exchanged through wireless communication are affected by noise, path loss, and shadowing. Thus, UAV swarm communication is associated with limited bandwidth, high power consumption, and low communication range. The most common wireless technologies for swarms are Bluetooth, Wi-Fi, radio frequency, and Zigbee. Bluetooth signals function up to 100 meters with a high data rate. It can be used either indoor or outdoor; however, the bandwidth is limited to 24Mbps. Wi-Fi signals can travel up to hundreds of meters with a high data rate in the presence of many access points. Wi-Fi bandwidth is comparatively higher than that of Bluetooth, with speeds of up to 54Mbps. Zigbee is yet another communication technology that is used for systems which specifically need low power consumption, a longer battery life, and low data rates [5]. Table 1 gives a comparison of the aforementioned wireless technologies in terms of coverage, bandwidth, and environment. As we can see Wi-Fi presents longer coverage and higher bandwidth than both Zigbee and Bluetooth; thus, this spectrum is band is more suitable for long distance swarm missions.
TABLE 1: Comparison of three wireless communication technologies for UAV Swarms.
|
Technology |
Frequency Band/Channel |
Coverage |
Bandwidth |
|
Bluetooth |
2.4 GHz |
100 meters |
2-24 Mbps |
|
Wi-Fi |
2.4 GHz/5.8 GHz |
>100 meters |
54 Mbps |
|
Zigbee |
2.4 GHz |
10-20 meters |
250 Kbps |
- Security
A few research papers related to UAV security have been published. However, these approaches do not fully apply to UAV swarms because of the added complexity with UAVs connected through a network. Cyber-attacks that target UAV swarms attack each individual UAV as well as the communication between UAVs.
1. Types of Attacks on UAV Swarms
The authors of [6] provided an extensive list of possible threats to a UAV communication network. This list includes attacks by humans and systems. The classification is done according to the three security requirements for systems which are confidentiality, integrity, and availability. Confidentiality deals with sets of rules to ensure unauthorized users do not have access to protected data. The most common method for testing confidentiality is using authentication processes to ensure that users who request access to protected data are in fact authorized. Integrity involves methods to ensure that data is genuine, accurate, and protected from unauthorized user access and modification. Data must remain unchanged when stored as well as when data is being transported. Availability ensures that information is accessible to authorized users when needed. This means that the communication channels, security measures, and systems that store information must all be functioning correctly for information to be available. In Table 2, we describe the most important attacks that target UAV swarm networks, the target security requirement impacted, and the impacts of the attack on the swarm, GCS, and airspace.
|
Attack |
Description |
Target Security Requirement Impacted |
Impacts |
|
Injection |
Injects messages similar to those exchanged by UAVs |
Integrity |
UAVs become prone to collision |
|
GPS Spoofing |
Broadcasting fake GPS signals or retransmitting legitimate GPS signals |
Integrity |
UAVs become unable to estimate their position or communicate with GPS Receiver |
|
Identity Spoofing |
Impersonating another user in the network |
Confidentiality |
Misleads UAVs in the swarm and enables access to confidential data |
|
Jamming |
Broadcasting signals to stop any communication |
Availability |
UAVs cannot transmit or receive data Denial of service |
|
Flooding |
Overflows the network with large amounts of traffic |
Availability |
UAVs cannot transmit or receive data Denial of service |
|
Keylogging |
Monitoring the operations of GCS and UAVs |
Confidentiality |
Leaks data to unauthorized users |
|
Eavesdropping |
Listening to the communication between UAV swarm and GCS |
Confidentiality |
Leaks data to unauthorized users |
2. Impact of Attacks on UAV Swarms
A few studies have been done to investigate the impacts of attacks on UAV swarm networks. For example, a simulation test bed for cyber security analysis of UAV networks was created by authors of [7]. It allows user to set different parameters for a network, its hosts, and attacks in order to resemble real-world scenarios of various attack attempts on a UAV system. Authors were able to evaluate the impact of jamming attacks against UAV networks to show the effectiveness of this testbed. The authors of [6] conducted a threat analysis and modeled attacks on a UAV communication network through a simulation testbed. They found that security measures lower the likelihood of an attack, but the impact of an attack does not change. Authors of [8] investigated the impact of injection attacks on the security of airspace. Their results show that this type of attack can lead to airspace disturbance and collisions.
3. Detection Techniques
Detection techniques aim at detecting attacks on each UAVs as well as on ground control stations. A few papers have been published in this area. For instance, the authors of [9] proposed a framework for testing the resiliency of a UAV swarm network by using position, range, encryption methods, network requirements, and resource constraints to test whether a network is safe from cyberattacks or not. It also determines which UAVs are vulnerable in the swarm, which can be ordered to move in order to make the network safe. In addition, it also determines which UAV makes the network vulnerable by being unavailable. The authors concluded that their framework can secure UAVs by relocating those vulnerable in the swarm network. The authors of [19] provided an overview of detection techniques for cyber-attacks targeting aircraft networks, specifically aircraft carrying Automatic Dependent Surveillance-Broadcast (ADS-B) devices.
4. Countermeasure Techniques
Several countermeasure techniques have been proposed in the literature. In [10], the authors proposed a beaconing-based architecture to secure positioning in a UAV swarm. This architecture uses a UAV wireless card to measure the distance between a UAV and a set of verifier nodes closest to it. An authority manages all the cryptographic keys through a secure channel over a cellular network. The authority runs a multi-lateration verification procedure to check the position of the UAV and each UAV must prove its position from the authority by confirming its position from the other UAVs in the swarm. This position is estimated using an RSSI-based (Received Signal Strength Indication) distance estimation architecture for securing positioning in UAV swarms. Authors found that this architecture had lower accuracy than distance-bound protocol, but it is less complex to implement so it is more practical for small UAS swarms. In [11], the authors proposed a robot swarm communication security model for aerial, ground, and aquatic robots where individual robots function as nodes and functions inside each robot act as modules. These modules were categorized into two or more taxonomies based on criticality. Each module is secured with modern cryptographic algorithms and whenever there is a request for communication between modules, they must undergo an authentication protocol. The authors of [12] also analyzed the efficiency of several cryptographic algorithms in securing communications in a large fixed-wing UAV swarm, including AES, GCM, CCM, and ChaCha20-Poly1305. They also measured the impact of these encryption techniques on network capacity and processor performance and found that ChaCha20-Poly1305 outperform the other investigated methods in terms of speed and minimizing hardware complexity for securing swarm communication if classified data is not being handled or created. However, this algorithm is not secure enough for classified data. The authors recommend AES or Triple Data Encryption Standard (3DES) for encrypting classified data. However, it is well known that 3DES is slower and less secure then AES.
- Security Challenges and Research Directions
Despite the technological advances in the design and development of UAV swarms, problems related have been fully investigated and are several challenges and open research problems still exist. The authors of [14] classified robot swarm security challenges in to two categories: security, privacy, and trust related challenges and performance and energy consumption challenges. Other authors [15] identified nine different security challenges in a swarm environment: resource constraints, physical capture and tampering, control, communication, swarm mobility, identity and authentication, key management, intrusion detection, and learning management.
References
[1] Brambilla, Manuele, Eliseo Ferrante, Mauro Birattari, and Marco Dorigo. “Swarm robotics: a review from the swarm engineering perspective.” Swarm Intelligence 7, no. 1 (2013): 1-41. Navarro et al.
[2] Navarro, Iñaki, and Fernando Matía. “An introduction to swarm robotics.” Isrn robotics 2013 (2012).
[3] Campion, Mitchell, Prakash Ranganathan, and Saleh Faruque. “UAV Swarm Communication and Control Architectures: A Review.” Journal of Unmanned Vehicle Systems ja (2018).
[4] Bekmezci, Ilker, Ozgur Koray Sahingoz, and Şamil Temel. “Flying ad-hoc networks (FANETs): A survey.” Ad Hoc Networks 11, no. 3 (2013): 1254-1270.
[5] Zahugi, Emaad Mohamed H., S. V. A. V. Prasad, and T. V. Prasad. “ADVANCED COMMUNICATION PROTOCOLS FOR SWARM ROBOTICS: ASurvey.” Power 1 (2012): 100.
[6] Javaid, Ahmad Y., Weiqing Sun, Vijay K. Devabhaktuni, and Mansoor Alam, “Cyber security threat analysis and modeling of an unmanned aerial vehicle system,” IEEE Conference on Technologies for Homeland Security (HST), pp. 585-590, 2012.
[7] Javaid, Ahmad Y., Weiqing Sun, and Mansoor Alam. “UAVSim: A simulation testbed for unmanned aerial vehicle network cyber security analysis.” In Globecom Workshops (GC Wkshps), 2013 IEEE, pp. 1432-1436. IEEE, 2013.
[8] Manesh, Mohsen Riahi, and Naima Kaabouch. “Analysis of vulnerabilities, attacks, countermeasures and overall risk of the Automatic Dependent Surveillance-Broadcast (ADS-B) system.” International Journal of Critical Infrastructure Protection 19 (2017): 16-31.
[9] Jakaria, A. H. M., and Mohammad Ashiqur Rahman. “Formal Analysis of k-Resiliency for Collaborative UAVs.” In 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), pp. 583-592. IEEE, 2018.
[10] Yokoyama, Roberto Sadao, Bruno Yuji Lino Kimura, and Edson dos Santos Moreira. “An architecture for secure positioning in a UAV swarm using RSSI-based distance estimation.” ACM SIGAPP Applied Computing Review 14, no. 2 (2014): 36-44.
[11] Pigatto, Daniel Fernando, Leandro Gonçalves, Guilherme Freire Roberto, Julio Fernando Rodrigues Filho, Natássya Barlate Floro DaSilva, Alex Roschildt Pinto, and Kalinka Regina Lucas Jaquie Castelo Branco. “The HAMSTER data communication architecture for unmanned aerial, ground and aquatic systems.” Journal of Intelligent & Robotic Systems 84, no. 1-4 (2016): 705-723.
[12] Thompson, Richard B., and Preetha Thulasiraman. “Confidential and authenticated communications in a large fixed-wing UAV swarm.” In Network Computing and Applications (NCA), 2016 IEEE 15th International Symposium on, pp. 375-382. IEEE, 2016.
[13] Akram, Raja Naeem, Konstantinos Markantonakis, Keith Mayes, Oussama Habachi, Damien Sauveron, Andreas Steyven, and Serge Chaumette. “Security, privacy and safety evaluation of dynamic and static fleets of drones.” In Digital Avionics Systems Conference (DASC), 2017 IEEE/AIAA 36th, pp. 1-12. IEEE, 2017
[14] Gupta, Lav, Raj Jain, and Gabor Vaszkun. “Survey of important issues in UAV communication networks.” IEEE Communications Surveys & Tutorials 18, no. 2 (2016): 1123-1152.
[15] Higgins, Fiona, Allan Tomlinson, and Keith M. Martin, “Survey on security challenges for swarm robotics,” IEEE Autonomic and Autonomous Systems Conference, pp. 307-312. IEEE, 2009.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal