Software Development Life Cycle
| ✓ Paper Type: Free Assignment | ✓ Study Level: University / Undergraduate |
| ✓ Wordcount: 2483 words | ✓ Published: 12 Aug 2019 |
A Software Development Life Cycle (SDLC) is refers to the process, steps or phases taken in formulating a model in the development of software or life cycle management. This process is initiated during the software design phase and focuses on quality development standards that result in timely and cost-effective delivery against requirements. In the development of any software its intended final purpose is considered. The actual development of given software involves a lot of computation and processing. Most software development methodologies have common phases. Generally, the software development life cycle (SDLC) consists of the following ones: planning, analysis, design and prototype, implementation (coding), testing and integration, and maintenance.
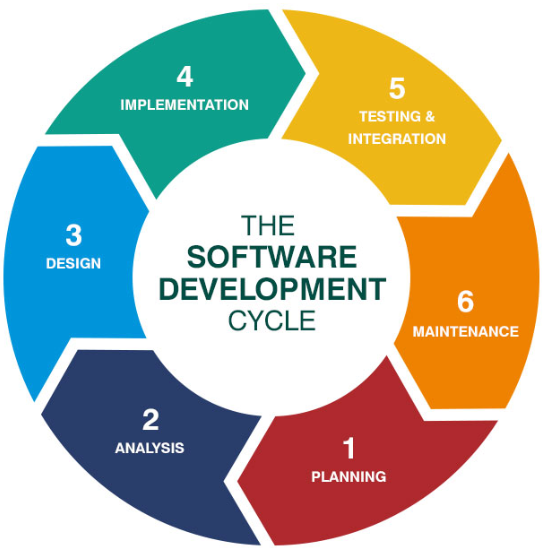
Figure 1, Basic Stages of Software Development Cycle. Source: https://online.husson.edu/software-development-cycle/
There are many types of software development methodologies for basic software development task. Different organizations use different methodologies. But in order to be more effective it is recommended that organizations use a standard software development methodology. The different types of software models are:
Waterfall Software Development
It is very simple to understand and use. In this model, each phase must be completed before the next phase can begin and there is no overlapping in the phases. It has six phases and is known for not re-visiting the previous stage. Practically it may not be feasible to work independently on each phase, however it is required, to revisit previous steps based on changes to the functional requirements or the need for improvements. The waterfall model is mostly used in the development of large enterprise software systems. Typical waterfall models are depicted below.
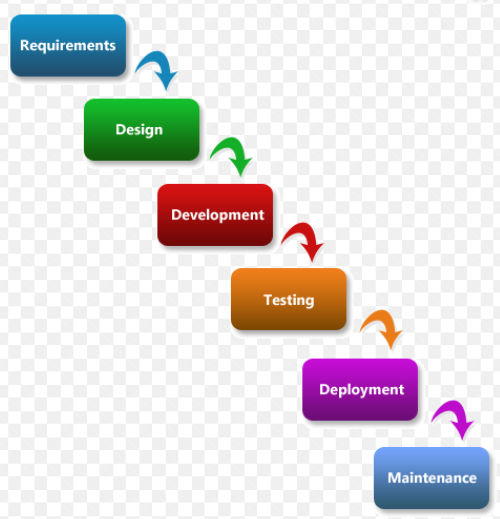
Figure 2, Waterfall model. Source: https://castellansystems.com/Waterfall.cshtml
Agile Software Development
It is a model that create and respond to change in order to succeed in an uncertain and turbulent software development environment. Like other methodologies, it considers the customer’s requirements, feedback, and satisfaction of the project. The major difference is that the agile development process does not explicitly state the end result of the software from its inception. Instead of planning tasks or expectations for phases, prototypes are tested regularly during each phase of the project to demonstrate the application’s functionality. At those points, the customer’s feedback can be considered, so that the end product satisfies the customer. Unlike other this model has the lowest cost associated with changes to the scope (often called “scope creep”). Therefore, this methodology can result in greater efficiency and functionality, creating tailored software most suited to the customer’s needs. Below is the diagram:
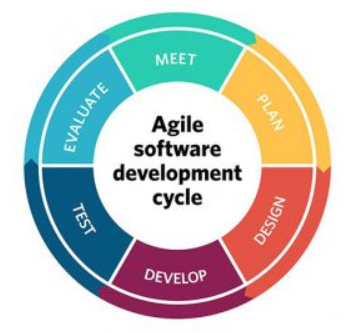
Figure 3, The Agile model. Source: https://project-management.com/10-key-principles-of-agile-software-development/
Rapid Application Development (RAD)
It is similar to agile software development model. The key benefit of a Rapid Application Development (RAD it is going to be referenced “RAD” in this paper) approach is fast project turnaround, making it an attractive choice for developers who likes to work in fast paced software development environment. This fast pace is made conceivable by RAD’s emphasis on limiting the arranging stage and amplifying model advancement. By lessening arranging time and underscoring model emphases, this model permits venture supervisors and partners to precisely gauge advance and convey progressively on developing issues or changes. This outcomes in more prominent effectiveness, quicker advancement, and powerful correspondence..
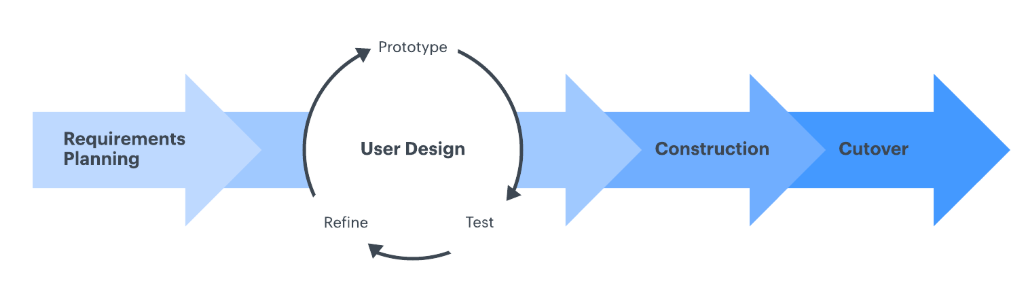
Figure 4, The RAD model. Source: https://www.lucidchart.com/blog/rapid-application-development-methodology
Recommended SDLC Model for Office of Personnel Management (OPM)
Office of Personnel Management (OPM it will be referred in this paper) serves as the main HR organization and work force approach administrator for the Government. OPM coordinates HR and representative government employees, administrate their personal information, controls retirement benefits, oversees medicinal services and protection programs, supervises justify based and comprehensive enlisting into the common administration, and gives a safe work process
It is highly recommended that OPM apply the Waterfall software development methodology, since the organized advancement cycle authorizes discipline, each stage has a characterized begin and end point, and advancement can be convincingly recognized (using developments) by both merchant and customer. The accentuation on necessities and configuration before composing a solitary line of code guarantees negligible wastage of time and exertion and lessens the danger of timetable slippage, or of client desires not being met.
Getting the prerequisites and configuration off the beaten path first likewise enhances quality; it’s substantially less demanding to get and redress conceivable imperfections at the plan arrange than at the testing stage, after every one of the parts have been incorporated and finding particular blunders is more unpredictable. At last, on the grounds that the initial two stages end in the generation of a formal determination, the cascade model can help productive information exchange when colleagues are scattered in various areas.
The 7 Step Software Development Life Cycle Model
The seven step software development life cycle involves the following steps:
Planning: The first step involves outlay of the concept of the project. It involves aspects of project and product management. The output of the arranging stage include: venture designs, plans, cost estimations, and obtainment prerequisites. “Ideally, Project Managers and Development staff collaborate with Operations and Security teams to ensure all perspectives are represented” (Swersky, 2018).
Requirement: The second step in the SDLC and involves defining the intended function and features of the requirements are gathered from business stakeholders and Subject Matter Experts. “During this phase, the customer states the expectations of the project including who will use the product, how the customer will use the product, and the specific information included with any special customer requirements related to the software” (A, 2018)
Analysis and design: The next step involves the definition of the structure of the software and its major aspects. When the necessities are comprehended, programming planners and engineers can start to structure the product. The structure procedure utilizes set up examples for application design and programming improvement. “Developers use proven Design Patterns to solve algorithmic problems in a consistent way. This phase may also include some rapid prototyping, also known as a spike, to compare solutions to find the best fit. The output of this phase includes” (Swersky, 2018).
Software building (Development): The fourth step is coding of the software or software development. This is the programming activity where the developed designed is turned into a form executable by the computer. It also involves the creation of the software’s database. “Business stakeholders should be engaged regularly, to ensure that their expectations are being met” (Swersky, 2018). The output of this phase is testing.
Testing: Testing phase of the SDLC is one of the most important. It is difficult to convey quality programming without testing. There is a wide assortment of testing important to gauge quality. Testing can be done manually or automatically. The output of the testing phase is software deployment or ready for production.
Implementation (Deployment): This is the next step and involves that now software is deployed and the instant it is ready. Implementation to production, acquisition/purchase of the necessary software/hardware is conducted in this phase. Once the software has been installed, the end users are trained on the operation of the software
Operation and Maintenance: This is the last step in the seven steps of SDLC model. It takes an overall focus on the entire life cycle of the model. In this progression programming must be observed always to guarantee legitimate activity. Bugs and deformities found Underway must be accounted for and reacted. This includes necessary updates and guarding the system from future compromise such as infiltration, hacking or introduction of bugs.
Security Principles
Security enhancement should be included in every phase we have, however depth security features needed from the design phase onwards. In planning and requirement gathering phase information fetching mostly happen between user and developer due to that need of security level will be less. Apart from the user collecting information should be trust worthy as well as valid information should be taken for the system development. In analysis phase, the information’s what we obtain from the requirement phase that will give to the analysis phase. Collected information will be analysis used some valid documents materials, white papers, existing methods, etc.
In the analysis phase itself we have to estimate what kind of security requirements need for our system. Security elements and features should be included in every aspect of the system like user, data, module, design, testing, etc. Developers need to realize secure programming plan standards and how they are utilized in the structure of versatile and reliable frameworks. Two essential concepts of design include abstraction and decomposition of the system using the architecture and constraints to achieve the security requirements obtained during the requirements phase.
Abstraction is a process for reducing the complexity of a system “It enables the intent of each event to be instantly identified, allowing organizations to deploy the best security particles with the relevant capabilities to handle the threat” (Chesla, 2017). Decomposition is the process of describing the generalizations that compose an abstraction. One method, top-down decomposition, involves breaking down a large system into smaller parts.
For designs, the progression would be like application, module, class, method and etc. Other secure software design principles are detailed in a multitude of books, white papers, web portals, and articles. Some techniques to improve security in the design phase, minimizes the number of users in the system granted high levels of privilege, and the amount of time any user holds onto its privileges. Ensures that no single entity should have all the privileges required to modify, delete, or destroy the system, components and resources. Separation of domains makes separation of roles and privileges easier to implement.
Elements of Capability Maturity Model
The constant procedure enhancement depends on numerous little transformative advances as opposed to bigger progressive developments. The Capacity Development Display (CMM) gives a system to sorting out these transformative strides into five development levels that establish progressive frameworks for consistent process enhancement. This approach is at the core of most administration frameworks which are intended to enhance the nature of the improvement and conveyance all things considered and benefits.
The five development levels characterize a scale for estimating the development of an association’s product procedure and for assessing the ability of these procedures. They additionally help an association needs its enhancement endeavors. Every development level involves an arrangement of process objectives that, when fulfilled, settle an imperative part of the procedure. Accomplishing each level of development system sets up an alternate segment in the product procedure, bringing about an expansion in the process ability of the association.
The five Software Capability Maturity levels have been defined as:
- Initial: It is the first level that the software process. It is portrayed as specially appointed, and incidentally even confused. Hardly any procedures are characterized, and achievement relies upon individual exertion and commitment. “In spite of this ad hoc, chaotic environment, maturity level 1 organizations often produce products and services that work; however, they frequently exceed the budget and schedule of their projects” (McKay, 2011) .
- Repeatable: Fundamental task administration forms are set up to track cost, calendar, and usefulness. The important procedure discipline is set up to rehash before triumphs on activities with comparable applications “Process discipline helps ensure that existing practices are retained during times of stress. When these practices are in place, projects are performed and managed according to their documented plans” (McKay, 2011).
- Defined: The product procedure for both administration and designing exercises is recorded, institutionalized, and incorporated into all procedures for the association. “All projects use an approved version of the organization’s standard software process for developing and maintaining software” (McKay, 2011).
- Managed: Point by point proportions of the product procedure and item quality are gathered. Both the product procedure and items are quantitatively comprehended and controlled. “At maturity level 4, the performance of processes is controlled using statistical and other quantitative techniques, and is quantitatively predictable” (McKay, 2011) .
- Optimizing: Nonstop process enhancement is empowered by quantitative criticism from the procedure and from steering inventive thoughts and advances. “The effects of deployed process improvements are measured and evaluated against the quantitative process-improvement objectives” (McKay, 2011).
Finally Capability Maturity Model Integration (CMMI) is made up of a number of maturity models into one integrated capability maturity model. Originally it was originated to meet the needs of improving and managing the quality of the services in organization. CMMI helps to guide process improvement across a project, a program, or Enterprise wide. The CMMI structure and the Software CMM structure are similar with respect to maturity levels, key process areas, goals, and practices, however CMMI offers two representations of the maturity of the processes. “CMMI offers a staged representation with five maturity levels just like the Software CMM and a continuous model where each process area has its own maturity level” (McKay, 2011). It is very important to understanding the CMM model for any long term service improvement, strategy and effective processes.
References
A, J. (2018, 01 31). Requirement Gathering & Analysis Phase in SDLC. Retrieved from study.com: https://study.com/academy/lesson/requirement-gathering-analysis-phase-in-sdlc.html
Acquisti, R. G. (2005, 11). Information revelation and privacy in online social networks. In Proceedings of the 2005 ACM workshop on Privacy in the electronic society (pp. 71-80). ACM.
Britt, Phil. (2017, March 30). Cybersecurity Risk Management: Finding and Fixing Your Security Vulnerabilities. Retrieved from https://www.esecurityplanet.com/network-security/cybersecurity-risk-management.html.
Chesla, A. (2017, 01 09). Understanding the Benefits of Security Abstraction. Retrieved from Security Week: https://www.securityweek.com/understanding-benefits-security-abstraction
DeFranco, J. (2013). What every engineer should know about cyber security and digital forensics.
Deibert, R. P. (2008). Access denied: The practice and policy of global internet filtering. Mit Press.
Francen, E. (2015, JULY 29). Information security and compliance. Information security and compliance explained. Retrieved from https://frsecure.com/blog/information-security-and-compliance-explained/
McKay, V. (2011). What is the Capability Maturity Model? (CMM). Retrieved from Select Business Solutions: http://www.selectbs.com/process-maturity/what-is-the-capability-maturity-model
Megan Burns. (1999). Recommendations for Anonymous Remailer Policy at Oberlin College. Retrieved from http://www.cs.cmu.edu/~burnsm/remailers.html
Pabrai, A. (2016, April 11). ESTABLISHING AN ENTERPRISE CYBERSECURITY STANDARD. Retrieved from ISACA: http://www.isaca.org/cyber/cyber-security-articles/Pages/establishing-an-enterprise-cybersecurity-standard.aspx
Quarterman, J. (2006). Risk management solutions for Sarbanes-Oxley section 404 IT compliance. Retrieved from http://common.books24x7.com.ezproxy.umuc.edu/toc.aspx?bookid=12456
Scarfone, M. P. (2008, 09 30). Technical Guide to Information Security Testing and Assessment. Retrieved from NIST: https://www.nist.gov/publications/technical-guide-information-security-testing-and-assessment?pub_id=152164
Swersky, D. (2018, 05 31). Raygun. Retrieved from The SDLC: 7 phases, popular models, benefits & more: https://raygun.com/blog/software-development-life-cycle/
Symantec employee. (2016). Emerging Threats: What is the Difference Between Black, White and Grey Hat Hackers? Retrieved from Norton by Symantec: https://us.norton.com/internetsecurity-emerging-threats-what-is-the-difference-between-black-white-and-grey-hat-hackers.html
T. Peng, C. L. (2004, 05). Proactively detecting distributed denial of service attacks using source IP address monitoring. In International Conference on Research in Networking (pp. 771-782). Springer, Berlin, Heidelberg.
Technology, N. I. (2014, February 12). Framework for Improving Critical Infrastructure Cybersecurity. Cybersecurity Framework, 1. Retrieved from https://www.nist.gov/cyberframework
The Foreign Intelligence Surveillance Act of 1978. (n.d). Justice Information Sharing. (n.d.). Retrieved from https://it.ojp.gov/PrivacyLiberty/authorities/statutes/1286
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this assignment and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


