CHAPTER 1: INTRODUCTION
- Problem Summary
The main goal of our system is to make an India free to speak against anti-social activity without any kind of fear. In our system admin take the complaint from user about anti-social activity that happening nearing to his/her. The complaint is provided to the headquarter by using internet and to the police commissioner of the city by using SMS gateway then police will take some action on that and send the taken action on complaint to the admin. Admin provide taken action to the complainer as well as store it in it’s own database .If the police does not take any action against complaint then it is forwarded to higher level or inform to it to the media so that the media can telecast about complaint, also NGO will be connected with our web application so that they can take better care of the victim. If the complaint is found fake by police then the admin provide the detail of complainer for take action on that person.
- Objectives of Project
There is no online system available for uploading of crime and solving it. So, we are generating the online system for “
Http Web Solutions”. There are main objective of this system are following:
- The system allows the Admin to manage all kind of categories and maintain users
- Provides online Donation transaction using PayPal system.
- A Mission Rising India is a web application designed to make it easy for non-technical users to register complain and search complain in a user friendly interface much like Microsoft word.
- Provide Security for whole System and user or member.
- Reduce Time Maintenance.
- Increased transparency and efficiency.
- Also provide Online Web services for public, and online help related to crime.
- Problem Specification
- In current system, the some system provide only upload of complaints while some are just represent the crime ratio and other activities.
- Some web application only accept complaint in particular form like only in text.
- The current system is also not user friendly and it is also tedious to search a particular detail on web application.
- No complaint upload without log in with social media like face book
- No location provided of crime place
- No connection with media and NGO
- Need more time
- Less performance
- No contact with emergency services
- No complaint verifier
- No logic for fake complainer
- Literature Survey
- Child abuse and neglect by parents and other caregivers
Publish Year: April 2015
Author name: WORLD REPORT ON VIOLENCE AND HEALTH
Abstract:
Types Of Abuse:-
1)Physical Abuse
2)Sexual Abuse
3)Emotional Abuse
4)Neglect
| Types Of Punishment |
Incidence(%) |
|
Chille |
Egypt |
India_a |
Philippines |
USA |
| Severe Physical Punishment |
| Hit the child with an object
(not on buttocks) |
4 |
26 |
36 |
21 |
4 |
| Kicked the child |
0 |
2 |
10 |
6 |
0 |
| Burned the child |
0 |
2 |
1 |
0 |
0 |
| Beat the child |
0 |
25 |
_b |
3 |
0 |
| Threatened the child with a knife
or gun |
0 |
0 |
1 |
1 |
|
| Choked the child |
0 |
1 |
2 |
1 |
0 |
| Moderate Physical Punishment |
| Spanked buttocks (with hand) |
51 |
29 |
58 |
75 |
47 |
| Hit the child on buttocks (with object) |
18 |
28 |
23 |
51 |
21 |
| Slapped the child’s face or head |
13 |
41 |
58 |
21 |
4 |
| Pulled the child’s hair |
24 |
29 |
29 |
23 |
_b |
| Shook the child_c |
39 |
59 |
12 |
20 |
9 |
| Hit the child with knuckles |
12 |
25 |
28 |
8 |
_b |
| Pinched the child |
3 |
45 |
17 |
60 |
5 |
| Twisted the child’s ear |
27 |
31 |
16 |
31 |
_b |
| Forced the child to kneel or stand in an
uncomfortable position |
0 |
6 |
2 |
4 |
_b |
| Put hot pepper in the child’s mouth |
0 |
2 |
3 |
1 |
_b |
| a Rural areas.
b Question not asked in the survey.
c Children aged 2 years or older. |
Table 1:-Rates of harsh or moderate forms of physical punishment in the previous 6 months as reported by mothers, World SAFE study
| Verbal or psychological punishment |
Incidence(%) |
|
Chille |
Egypt |
India_a |
Philippines |
USA |
| Yelled or screamed at the child |
84 |
72 |
70 |
82 |
85 |
| Called the child names |
15 |
44 |
29 |
24 |
17 |
| Cursed at the child |
3 |
51 |
_b |
0 |
24 |
| Refused to speak to the child |
17 |
48 |
31 |
15 |
_b |
| Threatened to kick the child out of
the household |
5 |
0 |
_b |
26 |
6 |
| Threatened abandonment |
8 |
10 |
20 |
48 |
_b |
| Threatened evil spirits |
12 |
6 |
20 |
24 |
_b |
| Locked the child out of the
Household |
2 |
1 |
_b |
12 |
_b |
| a Rural areas.
b Question not asked in the survey. |
Table 2:-Rates of verbal or psychological punishment in the previous 6 months as reported by mothers, World SAFE study
| Non-violent discipline |
Incidence(%) |
|
Chille |
Egypt |
India_a |
Philippines |
USA |
| Explained why the behavior
was wrong |
91 |
80 |
94 |
90 |
94 |
| Took privileges away |
60 |
27 |
43 |
3 |
77 |
| Told child to stop |
88 |
69 |
_b |
91 |
_b |
| Gave child something to do |
71 |
43 |
27 |
66 |
75 |
| Made child stay in one place |
37 |
50 |
5 |
58 |
75 |
| a Rural areas.
b Question not asked in the survey. |
Table 3:-Rates of non-violent disciplinary practices in the previous 6 months as reported by mothers, World SAFE study
| Type |
Causes |
| Physical |
Abdominal/thoracic injuries
Brain injuries
Bruises and welts
Burns and scalds
Central nervous system injuries
Disability
Fractures |
| Sexual and reproductive |
Reproductive health problems
Sexual dysfunction
Sexually transmitted diseases, including HIV/AIDS
Unwanted pregnancy |
| Psychological and behavioral |
Alcohol and drug abuse
Cognitive impairment
Delinquent, violent and other risk-taking behaviors
Depression and anxiety
Developmental delays
Eating and sleep disorders
Feelings of shame and guilt
Hyperactivity
Poor relationships
Poor school performance
Poor self-esteem
Post-traumatic stress disorder
Psychosomatic disorders
Suicidal behavior and self-harm |
| Other longer-term health consequences |
Cancer
Chronic lung disease
Fibromyalgia
Irritable bowel syndrome
Heart disease
Liver disease
Reproductive health problems such as infertility |
Table 4:-Health consequences of child abuse
Conclusion:-
Child abuse is a serious global health problem. Although most studies on it have been conducted in developed countries, there is compelling evidence that the phenomenon is common throughout the world. Much more can and should be done about the problem. In many countries, there is little recognition of child abuse among the public or health professionals. Recognition and awareness, although essential elements for effective prevention, are only part of the solution. Prevention efforts and policies must directly address children, their caregivers and the environments in which they live in order to prevent potential abuse from occurring and to deal effectively with cases of abuse and neglect that have taken place. The concerted and coordinated efforts of a whole range of sectors are required here, and public health researchers and practitioners can play a key role by leading and facilitating the process.
- CYBER CRIME AND SECURITY
Publish Year: International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 ISSN 2229-5518
Author name: YAShIkA ARoRA
TANU ShREE
ShIlpA YADAV
Abstract:
The Internet is one of the fastest-growing areas of technical infrastructure development. E-mails have displaced traditional letter, online web presentation is now a days more important for businesses than printed publicity materials; and Internet-based communication and phone services are growing faster than landline communications. Online fraud and hacking attacks are just some examples of computer-related crimes that are committed on a large scale every day. Cyber security plays an important role in the ongoing development of information technology, as well as Internet services. Enhancing cyber security and protecting critical information infrastructures are essential to each nation’s security and economic well-being. Making the Internet safer (and protecting Internet users) has become integral to the development of new services as well as government policy. At the national level, this is a shared responsibility requiring coordinated action related to prevention, preparation, response and recovery from incidents on the part of government authorities, the private sector and citizens.
| Sr No:- |
Type |
| 1. |
Financial fraud |
| 2. |
Sabotage of data and other networks |
| 3. |
Theft of proprietery information |
| 4. |
System penetration from outside |
| 5. |
Denial of service |
| 6. |
Unauthorised access by insiders |
| 7. |
Employee use of internet service privileges |
| 8. |
Viruses |
Table 5:- Types of Cyber crime
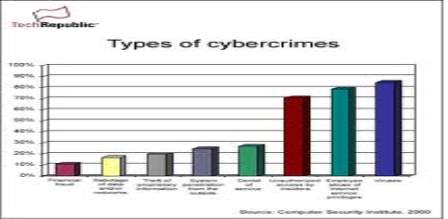
Figure 1.1:- Type of crimes and the threat percentage of these crimes-
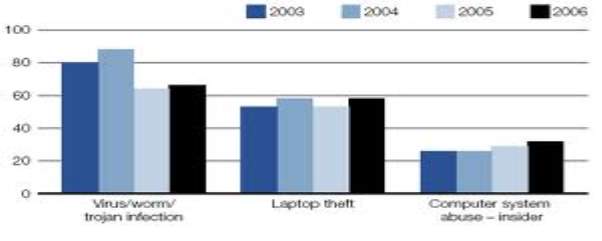
Figure 1.2:- Statistics of the cyber crime-
- Virus/Worm/Trojan Infection
- Laptop Theft
- Computer System Abuse-Insider
Conclusions-
The cyber crime as a whole refers to Offences that are committed against individuals or groups of individuals with a criminal motive to intentionally harm the reputation of the victim or cause physical or mental harm to the victim directly or indirectly, using modern telecommunication networks such as Internet and mobile phones. Such crimes may threaten a nation’s security and financial health. A computer can be a source of evidence. Even when a computer is not directly used for criminal purposes, may contain records of value to criminal investigators.so the network must be secure as no one can access the information of the computer.
3.Review Research Paper Domestic Violence:
The Dark Truth of Our Society
Publish Year: J Indian Acad Forensic Med. Jan-March 2013, Vol. 35, No. 1 ISSN 0971-0973
Author name: Pankaj Chhikara, Jitender Jakhar,Anil Malik,Kamal Singla, S. K.Dhattarwal
Abstract:
Domestic violence can be defined as a pattern of behavior in any relationship that is used to gain or maintain power and control over an intimate partner. Domestic violence, also known as domestic abuse, spousal abuse, battering, family violence, intimate partner violence (IPV), is defined as a pattern of abusive behaviors by one partner against another in an intimate relationship such as marriage, dating, family, or cohabitation. Domestic violence affects people of all socioeconomic backgrounds and education levels.
| No:- |
Name |
Detail |
| (1) |
Physical Abuse |
It includes hitting, slapping, punching, choking, pushing, burning and other types of contact that result in physical injury to the victim. It also include behaviors such as denying the victim of medical care when needed, depriving the victim of sleep or other functions necessary to live, or forcing the victim to engage in drug/alcohol use against his/her will. If a person is suffering from any physical harm then they are experiencing physical abuse. |
| (2) |
Sexual Abuse and Marital Rape |
Sexual abuse is any situation in which force or threat is used to obtain participation in unwanted sexual activity |
| (3) |
Emotional Abuse |
Emotional abuse (also called psychological abuse or mental abuse) can include humiliating the victim privately or publicly, controlling what the victim can and cannot do, withholding information from the victim, deliberately doing something to make the victim feel diminished or embarrassed, isolating the victim from friends and family, implicitly blackmailing the victim by harming others when the victim expresses independence or happiness, or denying the victim access to money or other basic resources and necessities. |
| (4) |
Economic Abuse |
Economic abuse is a form of abuse when one intimate partner has control over the other partner's access to economic resources. |
Table 6:- Types Of Domestic Violence
| No:- |
Cause |
| 1 |
Psychological |
| 2 |
Jealousy |
| 3 |
Behavioral |
| 4 |
Social Stress |
| 5 |
Mental Illness |
| 6 |
Marital Conflict Disorder |
Table 7:- Effects Of Domestic Violence
| No:- |
Name |
Effect |
| (1) |
Physical |
Bruises, broken bones, head injuries, lacerations, and internal bleeding are some of the acute effects of a domestic violence incident that require medical attention and hospitalization |
| (2) |
Psychological |
high amounts of stress, fear, and anxiety, Post-Traumatic Stress Disorder (PTSD) |
| (3) |
Financial |
Due to economic abuse and isolation, the victim usually has very little money of their own and few people on whom they can rely when seeking help. This has been shown to be one of the greatest obstacles facing victims of domestic violence, and the strongest factor that can discourage them from leaving their perpetrators. |
Table 8:- Causes of Domestic Violence
| No:- |
Consequence |
| (1) |
Medical Response |
| (2) |
Law Enforcement |
| (3) |
Counseling for Person Affected |
| (4) |
Counseling for Offenders |
Table 9:- Consequences of Domestic Violence
Conclusion:-
Despite efforts made by various sections of society and the Government to curb the menace of domestic violence against women, there is a rise in domestic violence.
This can be curbed by:
Educating women about her rights.
Community screening for domestic violence.
Providing adequate assistance to the victim.
By offering safe shelters, crisis intervention, advocacy, and
education and prevention programs.
Provision of strict laws and punishment for offence of domestic
violence.
To conclude it is therefore necessary that every society must contribute to ensure a violence free life for every woman.
4. A Study of Incidence of Alcohol Use In Fatal Road Traffic Accidents
Publish Year: J Indian Accad Forensic Med. Jan-March 2015, Vol. 37, No. 1 ISSN 0971-0973 12
Author name: Adyta Madhya Borah
Rituraj Chaliha
Abstract:
Road Traffic accidents (RTAs) are a leading killer in India snatching valuable human resources resulting in undefined economic and social loss. A leading cause for this malady is alcohol consumption and subsequent misadventure on the road which not only harms him but also the poor ones on the road.
Majority of the victims were lowly educated and were pedestrians or riders of two wheelers.
Aims & Objective:-
- To evaluate the causes and other contributing factors leading to death in Road traffic incidents with alcohol consumption.
- To study the level of alcohol present in body by analysis of blood.
| Total RTA‟s Cases |
Cases with evidence of Alcohol consumption (%) |
| 952 |
188(19.75) |
Table 10:- Alcohol and RTA involvement
| Sex |
Cases |
Percentage |
| Male |
186 |
98.94 |
| Female |
2 |
1.06 |
| Total |
188 |
100 |
Table 11:- Sex wise Distribution
| Age (Yrs) |
Cases |
Percentage |
| 0-9 |
0 |
0 |
| 10-19 |
13 |
6.91 |
| 20-29 |
72 |
38.30 |
| 30-39 |
60 |
31.91 |
| 40-49 |
36 |
19.15 |
| 50-59 |
5 |
2.66 |
| above 60 |
2 |
1.06 |
Table 12:- Age wise Distribution
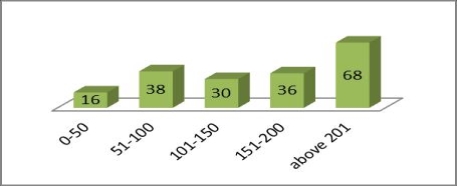 Figure 1.3: BAC of Victims
Figure 1.3: BAC of Victims
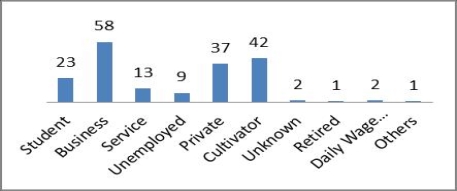 Figure 4:- Occupation of the Victims
Conclusion:
Figure 4:- Occupation of the Victims
Conclusion:
Drunk driving is a major problem in India and other developing regions of the world. Strict reinforcement supplemented with education is one of the most powerful tools to tackle the problem in low. Other measures like increasing the legal drinking age, restricting the availability of alcohol by limiting timings.
5. Research paper on Case laws of Fraud, forgery and Corruption in Banks and Financial Institutions in India
Publish Year: IOSR Journal of Economics and Finance (IOSR-JEF) e-ISSN: 2321-5933, p-ISSN: 2321-5925.Volume 3, Issue 6. (May-Jun. 2014), PP 53-57 www.iosrjournals.org
Author name: Hari Ram Anthelia,
M.A.(Poles.) , LL.M, (NET) CAIIB, (PhD)
Abstract:
Corruption is very bad disease in recent time. It is very harmful for our society. It is opposite to democracy and social order. Corruption also affect the economy of country and its cultural heritage. The purpose of this study is get rid from fraud and corruption committed by the criminals, outsiders customers and employees of the banks and financial institutions and other State, Central and Local bodies, public and private sectors.
Objective:-
The main objectives of this research paper are as under:
- To study the information’s of law relating to fraud and corruption in banks and financial institutions is essential.
- To examine the nature of evil of fraud and corruption in the banks and financial institutions which is increasing in spite of implementation of various law?
- To study dimensions of fraud and corruption in earlier and modern time.
- To identify and examine the role played by the C.B.I., Central Vigilance Commission, Police and other agencies with regard to fraud and corruption in the banks and financial institutions..
- To study the law and policies in India for prevention of fraud and corruption in Banks and financial institutions.
To study the need to strengthen and harmonize the law and policies regarding fraud and corruption in banks and financial institutions while ensuring its compliance with international law.
| No:- |
Name |
Problem |
Fact |
| (I) |
N.V. Subarea v. State of Andhra Pradesh. |
wrongful loss to the Bank as well as to the purchasers
Bank Scam/Criminal conspiracy/embezzlement/forgery |
Departmental Enquiry was conducted against the Bank Manager and accordingly he was dismissed from the services however the attention of the Court was drawn to a decision in State Bank of Hyderabadv.P.Kota Rao 17and State of M.P.v.SheetlaSahai18but was not helpful and court held that offence of criminal conspiracy can also be proved by circumstantial evidence. |
| (II) |
Gurgaon Gramin Bank v.Khazani |
Harassment to the gramin borrower |
That Smt. Khazani availed buffalo loan from appellant bank and was insured for Rs.15000/- for period from 6,2,01 to 6.2.04 vide animal tag NIA/03170 WITH New India Assurance Com Ltd 2nd respondents and premium was paid Rs.759/- vide receipt No.170612 dt, 5.0.01. The buffalo was unfortunately died on 27.12.01. She lodged claim for insurance money through bank and supplied them ear tag. No step was taken by the Bank or Insurance Company. She served notice dated 30.07.03 but yielded no result.
The Bank was dissatisfied and filed an appeal before the State Commission23, Haryana, Panchkula , Admittedly tag No 03170 and post mortem report.
The Bank and Insurance Company denied. Field Officer reported that when the buffalo died there was no tag and tag was not sent to opposite party.
Appeal is dismissed with cost of Rs.10000/- to be paid by bank to first respondent within a period of one month resultantly bank has to spend Rs. 25930/ for claim of Rs. 15000/- |
| (III) |
M/s Piara Singh Cold Storage v. Canara Bank and Anothers |
Misuse of Loan by the borrowers, Dishonour of Cheques, Debt Recovery Tribunal, Constitutional Law.
the agriculture loan as the cold storage was converted into marriage palace |
Accordingly petition is dismissed with cost of Rs.5000/- which shall be paid by petitioner to High Court Legal Services Committee within 15 days. |
Conclusion:-The criminal personswho commit fraud, forgery and corruption in the banks and financial institutions must be given life imprisonment and sent behind the bar so that coming generation may not commit any fraud and forgery which case huge loss to the government revenue and cause great problems to Banks, Financial Institution because after committing fraud and corruption the role of police department, Central Bureau of Investigation, Central Vigilance Commission started as per the quantum of fraud and forgery.
6.  Publish Year:
Publish Year: This online publication is based upon
Identity Theft Literature Review, by Graeme R. Newman and Megan M. McNally, final report to the National Institute of Justice, July 2005,
| NCJ 210459, referred to throughout this publication as “the full report.” Access the report online at http://www.ncjrs.gov/App/Publications/abstract.aspx?ID=210459. July 2007 |
Author name:  Abstract:
Abstract:
What did the researchers find?
• Although anyone is potentially vulnerable to theft of credit card-related information, individuals are more likely to be victimized by persons who have access to their identifying information, such as family members and persons with whom they share living quarters.
• Identity theft generally involves three stages: acquisition, use, and discovery. Evidence suggests that the longer it takes to discover the theft, the greater the loss incurred and the smaller the likelihood of successful prosecution. Older persons and those with less education are less likely to discover the identity theft quickly and to report it after discovery.
Research address the three main areas of vulnerability to identity theft—
1. Practices and operating environments of document-issuing agencies that allow offenders to exploit opportunities to obtain identity documents.
2. Practices and operating environments of document-authenticating agencies that allow offenders access to identity data, subsequently used for financial gain, avoiding arrest, or remaining anonymous.
3. The structure and operations of the information systems involved with the operational procedures of agents in (1) and (2).
| 1 |
Check fraud |
| 2 |
Plastic card fraud (credit cards, check cards, debit cards, phone cards, etc.) |
| 3 |
Immigration fraud |
| 4 |
Counterfeiting. |
| 5 |
Forgery |
| 6 |
Terrorism using false or stolen identities |
| 7 |
Theft of various kinds (pick pocketing, robbery, burglary, or mugging to obtain the victim's personal information) |
| 8 |
Postal fraud |
Table 13:- Crime Include Identity Theft
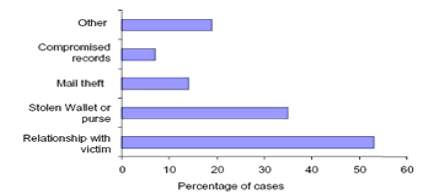 Figure 5:- How personal information is obtained
Figure 5:- How personal information is obtained
| No:- |
Types Of Identity Theft |
| 1 |
Exploiting weakness in specific technologies and information systems |
| 2 |
Financial scams |
| 3 |
As a motive for other crimes (e.g., bribing employees to provide passwords). |
| 4 |
Facilitating other crimes |
| 5 |
Avoiding arrest |
| 6 |
Repeat victimization ("classic" identity theft) |
| 7 |
Organized identity theft |
Table 14:- Broad Types Of Identity Theft
| No:- |
Name |
Activity/Intentions/Effects |
| Stage 1 |
Acquisition |
theft, computer hacking, fraud, trickery, force, redirecting or intercepting mail, or even by legal means (e.g., purchasing identifying information on the Internet) |
| Stage 2 |
Use |
for financial gain or to avoid arrest or otherwise hide one's identity from law enforcement or other authorities |
| Stage 3 |
Discovery |
Evidence suggests that the longer it takes to discover the theft, the greater the loss incurred by the victim, who may or may not involve law enforcement. |
Table 15:- Stages Of Identity Theft
| No:- |
Activity |
| 1) |
Local Level Prevention |
| 2) |
Certifying Identity |
| 3) |
Interventions |
Table 16:- Identity Theft Prevention
Conclusion:-
This study not only identified the available research on identity theft, it also identified in great detail the many areas where research is still needed. The researchers discuss the nearly inconceivable specter of having to handle 9 million identify theft cases within the criminal justice system and suggest that the best approach to the problem is prevention.
7. Pattern of Homicidal Deaths
Publish Year: J Indian Acad Forensic Med, 32(3) ISSN 0971-0973 194
Author name: Dr. Basappa S. Hugar
Dr Girish Chandra
Dr. S. Harish
Dr Jayanth SH
Abstract: Killing of an individual is the highest level of aggression found in all Cultures. Maximum homicides took place at victim‘s residence (31.5%) and street (29.75%). Acquaintances were involved in 47% of cases. The main motive was revenge (26.5%). Sharp weapon injuries (33.25%) were the commonest pattern followed by blunt weapon injuries (28%) and 82.5 % of victims died on the spot.
| Sr. No. |
Age group (yrs) |
No. of Males (%) |
No. of Female (%) |
Total No. (%) |
| 1 |
0-9 |
4 (7) |
4 (7) |
8 (14) |
| 2 |
10-19 |
1 (1.75) |
1 (1.75) |
2 (3.5) |
| 3 |
20-29 |
20 (35) |
8 (14.25) |
28 (49.25) |
| 4 |
30-39 |
6 (10.5) |
1 (1.75) |
7 (12.25) |
| 5 |
40-49 |
4 (7) |
0 (0) |
4 (7) |
| 6 |
50-59 |
4 (7) |
1 (1.75) |
5 (8.75) |
| 7 |
60 and above |
2 (3.5) |
1 (1.75) |
3 (5.25) |
| Total |
41 (71.75) |
16 (28.25) |
57 (100) |
Table 17:- Distribution of victims based on age and sex
| Sr. No. |
Motive |
No. (%) |
| 1 |
Argument |
8 (14) |
| 2 |
Revenge |
15 (26.5) |
| 3 |
Financial Conflicts |
10(17.5) |
| 4 |
Property gain |
2 (3.5) |
| 5 |
Mental illness of offender |
0 (0) |
| 6 |
Infidelity |
2 (3.5) |
| 7 |
Others |
11 (19.25) |
| 8 |
Not known |
9 (15.75) |
| Total |
57 (100) |
Table 18:- Distribution of homicides based on motive
| Sr. No. |
Survival Period |
No. of Cases (%) |
| 1 |
Spot death(<1/2 hr) |
47 (82.5 ) |
| 2 |
½ hr-1 day |
6 (10.5) |
| 3 |
1-7 days |
2 (3.5) |
| 4 |
>7 days |
3(3.5) |
| Total |
57 (100) |
Table 19:- Distribution of victims based on survival period
Conclusion:-
Maximum number of homicides occurred in the age group 20-29 years in both sexes. Maximum homicide took place at the victim‘s residence and street Most of the homicides took place in the evening and late night . The main motive behind the homicide was revenge. Maximum numbers of homicides were committed by acquaintances. Most of victims died on the spot.
8. Development and validation of crime behavior factor battery
Publish Year: International Journal of Psychology and Counselling Vol. 3(8), pp. 137-153, November 2011
Available online at http://www.academicjournals.org/IJPC
ISSN 2141-2499 ©2011 Academic Journals
Author name: R. A. Animasahun
Abstract:
| No:- |
Factor |
Detail |
| 1 |
Biological |
Genetic factors and neurological abnormal-lities |
| 2 |
Psychological |
Moral development, social learning and personality factors. |
| 3 |
Sociological |
Social factors, societal factors, socio-structural factors, ecological or environmental factors, sub-cultural, socio-control factors and macro social factors. |
| 4 |
Economic |
Poverty, unemployment, etc |
| 5 |
Behavioral |
- |
| 6 |
Cognitive |
- |
| 7 |
Phenomenological |
- |
| 8 |
Humanistic |
- |
| 9 |
Existential |
- |
Table 20:-The motivational factors for committing crime
| Zone Name |
State |
| Zone A |
Lagos and Ogun States |
| Zone B |
Kaduna, Katsina, Jigawa and Kano States |
| Zone C |
Bauchi, Gombe, Adamawa, Borno and Yobe States |
| Zone D |
Imo, Abia, Akwa Ibom, Cross River, Rivers and Bayelsa States |
| Zone E |
Oyo, Osun, Ondo and Ekiti States |
| Zone F |
Edo, Anambra, Delta, Ebonyi and Enugu States |
| Zone G |
Benue, Kogi, Taraba, Plateau and Nasarawa States |
| Zone H |
Niger, Kwara, Kebbi, Zamfara and Sokoto States |
Table 21:- Prison formation in Nigeria
| Sr No:- |
Factor |
Details |
| 1. |
Personal factor |
-Lack of self control
-Smoking marijuana |
| 2. |
Family/Parental factor |
-Born by indiscipline parents
-Brought up by non-challant and care free parents |
| 3. |
School based factor |
-Engaging in recreational activities during school hours
-Taught by highly indiscipline teachers |
| 4. |
Social factor |
-Living with siblings with criminal records
-Living in slums and ghettos |
| 5. |
Economic factor |
Poverty and inability to provide basic needs for family
High rate of unemployment |
| 6. |
Societal factor |
-Respect for superficial wealth irrespective of source
-Inadequate reward for hard work, honesty and integrity |
| 7. |
Political factor |
-Presence of people with high track record of deviant behaviors in power
-Government officials sponsor many cases of murder in this country |
| 8. |
Religious factor |
-The fear of God has become a thing of the past.
-Religious leaders aid and abet crime for money and fame. |
| 9. |
Peer group factor |
Association with peers known for criminal records and deviant behaviors.
Associating with peers who smoke, drink alcohol or use drugs . |
| 10. |
Media factor |
-Observation of crime related films teach advanced techniques in crime.
-Youths learn bad dressing and all sorts of crime from internet |
| 11. |
Career related factor |
-A wrong choice of career can influence an individual into crime.
-Being unemployed able for lack of necessary skills predisposes one to commit crime |
Table 22:- Different Factors
Conclusion:-
Based on all the evidences provided in this paper, the Crime Behavior Factor Battery (CBFB) could be said to be a valid and reliable instrument to measure crime.
1.5 Work Plan
| MILESTONES |
PROJECT ACTIVITY |
DURATION |
| Requirement Analysis |
Specification Functional requirement |
1 month |
| Design Database |
Database of all the details |
24 days |
Design Diagram
- ER Diagram
- Use Case Diagram
- Data Flow Diagram
- Class Diagram
- Sequence Diagram
- Activity Diagram
|
Design Flow diagram for related system |
14 days |
| Coding |
Coding of all details in system & its testing |
11 days |
| Documentation |
Make Report |
5 day |
Table 1.5: Project Plan
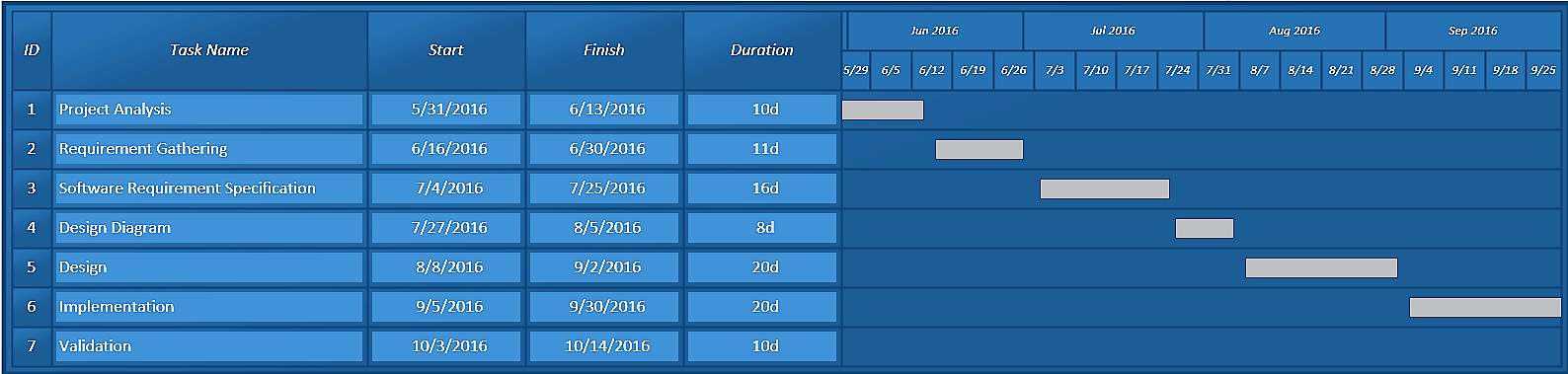
- Schedule Representation
|
June-Aug |
Aug-Oct |
Oct-Feb |
Feb-May |
| Jun |
Jul |
Aug |
Sep |
Nov |
Oct |
Dec |
Jan |
Feb |
Mar |
Apr |
May |
| Requirement
Analysis |
|
|
|
|
|
|
|
|
|
|
|
|
| System
Design |
|
|
|
|
|
|
|
|
|
|
|
|
| Forms
Designing |
|
|
|
|
|
|
|
|
|
|
|
|
| Implementation/
Coding |
|
|
|
|
|
|
|
|
|
|
|
|
| Testing/Debugging |
|
|
|
|
|
|
|
|
|
|
|
|
| Project-Report Preparation |
|
|
|
|
|
|
|
|
|
|
|
|
Table 1.2 Gantt Chart
1.6 Software And Hardware Requirement
- User Interface Requirement
- Computer/Laptop
- Android Smart Phone
- Software Interface Requirement
- Net beans
- Wamp server
- Android studio
- Android operating system
- Windows 7 and later
- Microsoft office
- Hardware Interface Requirement
- Windows compatible processor
- 512 MB RAM
- 104 keyboard
- Mouse
- Communication Interface Requirement
- Internet
- SMS Gateway
- Payment Gateway
Chapter 2: SYSTEM ANALYSIS AND DESIGN METHODOLOGY
2.1 Specification Requirement
In our web application the common man notice any anti-social activity. He / She take picture or video or audio message or text message and send it to the admin. Admin notice the detail and give it to the nearest police station to take some action by both online and also by SMS gateway. Police give reply to admin after taking action on particular complaint. Then the complaint with taken action is provided to the complainer. But suppose police had not taken any action on particular complain in particular time limit, the admin provide complaint to the media and also send it to NGO if it needed. The final complain detail will be provided to the admin & admin provide this detail to the complainer as well as stored in database for future purpose. If the complaint is found fake by police then the admin provide the detail of complainer for take action on that person.
Proposed System – Rising India Web application performs different type of fundamental operations to get complains, analysis it and if neededthen we redirect the complain to particular media and police station.
Web application provide the best security level to the members of the site for authenticate members online.
Web application provides a different type of platform to post and search complains to the people.
Web application provides facility to Admin who can add, update & delete new pages, menus, crime categories, news, events and web services as per requirement. Web application also provides the facility to member to upload complains and images or videos etc. Admin have overall control of Web application.
System provide online payment system using PayPal money transaction.
System is not dependant on any other system, it means it is independent. System need common requirement to run efficiently like smart phone. It means the system is useful for general people without buying or any kind of special requirement
System provide facilities like;
- Upload complaint with media
- Action Report
- Tracking complainer
- Reporting
Before using system the user must have to know that he/she must have to register him/her self in system. The user must have the primary knowledge of how to use internet and how to upload media in system.
Constraints, Assumption and Dependency:
- Hardware Requirement:
- PC with min 512 MB ram.
- Android smart phone with 1GB MB RAM.
- 250 GB Hard-disk.
- Processor 1.7 GHZ.
- Safety and Security Consideration:
- Only ADMIN can edit the details of user and update the images and videos so, details of company or any product are secured under the eyes of system ADMIN.
- The interface is very easy no more requirement for search or browse.
- Without login user, can’t access the application.
- Assumption and Dependency:
- We assume that the window operating system (window 7) is available at consultants desktop.
- The computer must have installed browser like Firefox, Chrome or internet explorer.
- We also assume that all user has android smart phone with fast internet connection.
- Failure occurred in system because of internet problem and also scarcity of memory in system.
- External Interface Requirement:
- User Interface Requirement:
•Login facility to admin at Website.
•Login facility to client on website.
For user interface the system require a display device like CRT monitor,LCD,etc.The screen format of the system may be any resolution between 800*600 and 1280*800. Also, requires Android mobile with minimum 4.0 size.
- Software Interface Requirement:
This system can be run on operating system of windows XP, windows VISTA, windows 7, windows 8, etc.
The system required front end tools as android and back end as MS-SQL server 2008 and SQL Lite. It required Microsoft office 2013 as documentation tools.
- Hardware Interface Requirement:
This system provides a facility for monitoring the stored area, so for the monitoring the ram system required display device like CRT monitor, LCDmonitor, LED monitor,etc.This phase of the software development process deals with the brief study of different hardware used in the making the use of proposed system.
•Android smart phone with 512 MB RAM.
•Pc with 2GB RAM
- Communication Interface Requirement:
For maintain and updating the record this interface are required.
•Pc with Internet
•Android smart phone with Internet
R1 Log in
Input:-User name and password
Output:-Login Successful else try again.
R2 Registration
Input:- User details and password
Output:- Provide unique user id with password
R3 Upload complaint
Input:-Upload complaint in form of images/video/audio/text
Output:- Complaint uploaded successfully
R4 Action report
Input:- Upload of taken action on a particular complaint
Output:- Action report received successfully
- It require minimum 1GB RAM.
- It require 4 GB Hard Disk.
- Smart android phone.
- It require 1.70 GHZ Processer
- Non-Functional Requirement:
- Portability: As the application is build using Unity it can be portable to windows, mac, android etc. The system should be developed in such a way that it will be portable to run on any machine.
- Security: The security is provided to the system by authorizing system users. The unauthorized users can’t easily log in to the system without required credentials.
- Efficiency: The system is very efficient user just have to focus on particular and the system will show related object or video within a second. There is problem only when new package is upgrading.
- Usability: This system can be operated by anyone who have knowledge of android mobile and cameras and using this system is really easy, you just have to focus your camera on particular image the application will automatic find object or video related to the image and we can interact with those objects and videos too.
2.2 ER Diagram
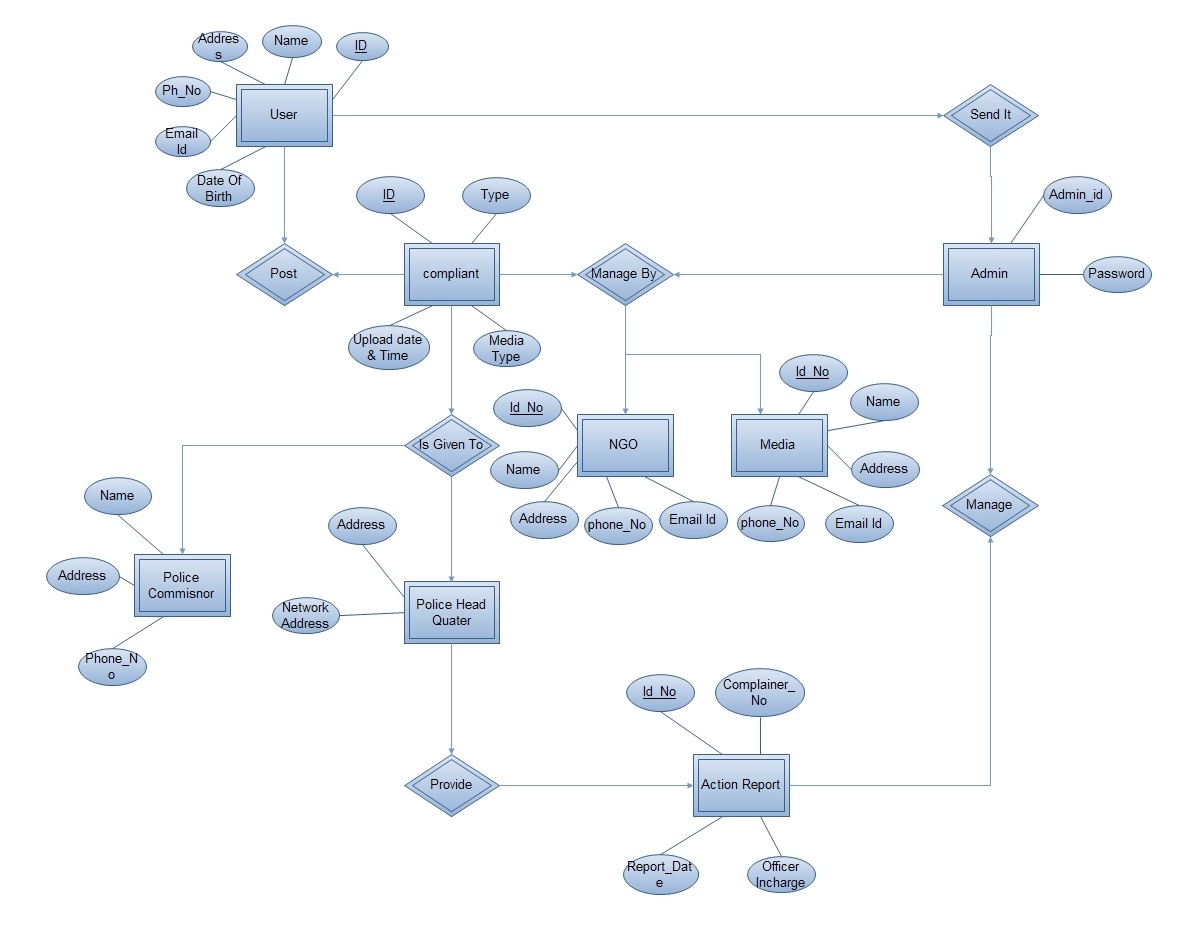 Fig. 2.1 ER Diagram
2.3 Use Case Modeling
2.3.1 Use Case diagram for admin:-
Fig. 2.1 ER Diagram
2.3 Use Case Modeling
2.3.1 Use Case diagram for admin:-
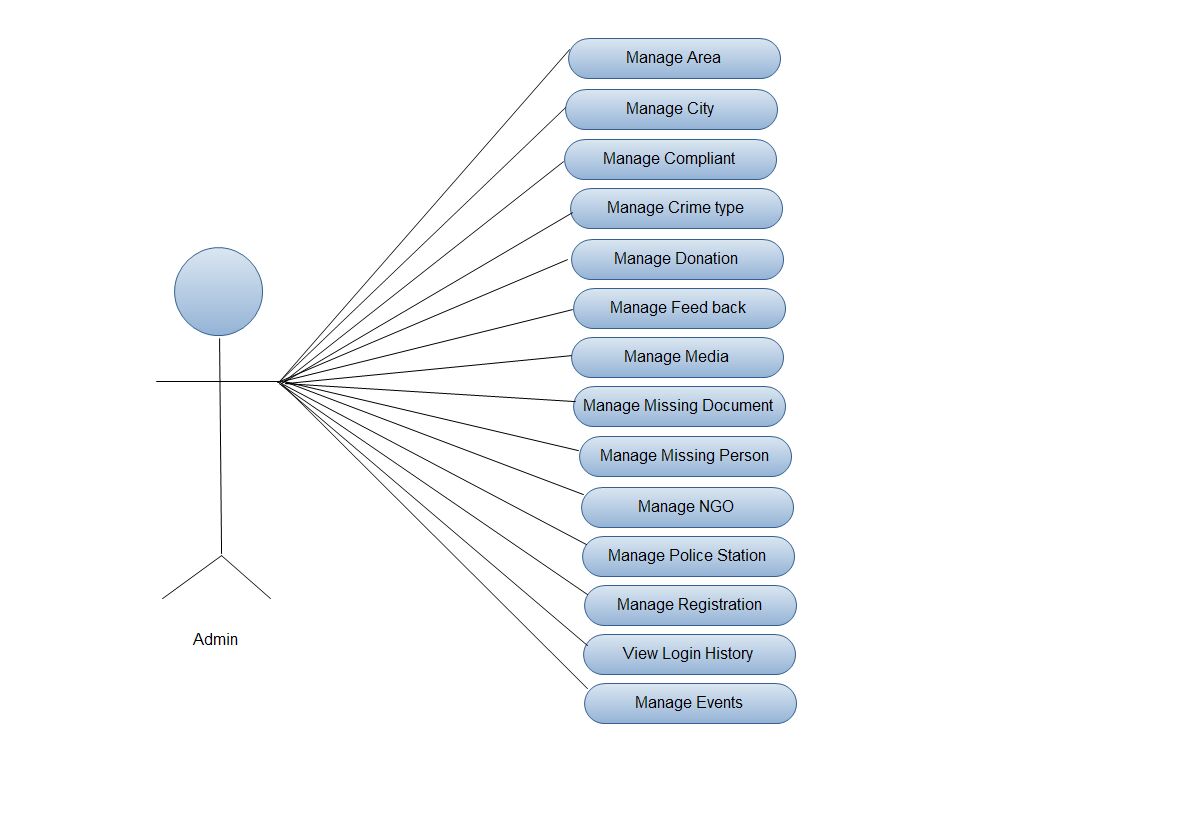 Fig. 2.2 Use Case Diagram for admin
Fig. 2.2 Use Case Diagram for admin
- Use Case diagram for user:-
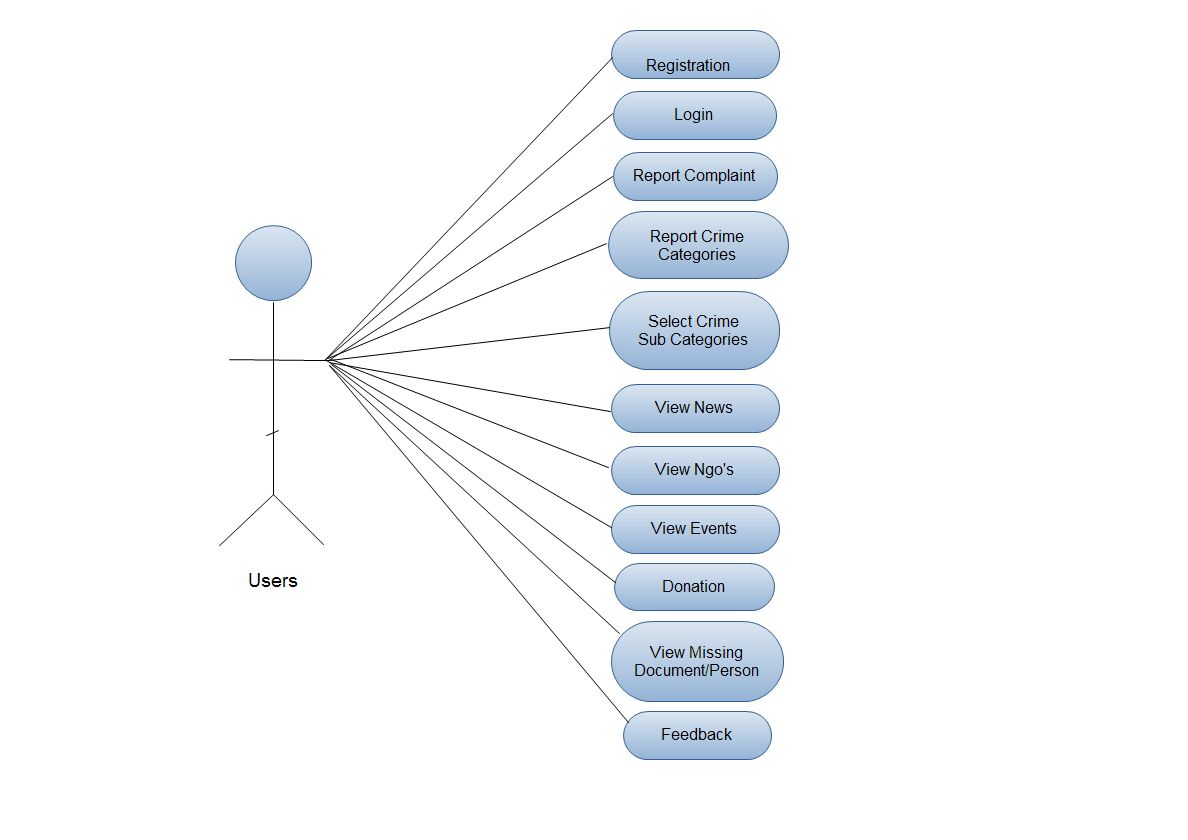 Fig. 2.3 Use Case Diagram for user
2.4 Functional Modeling
2.4.1 Data Flow Diagram
Fig. 2.3 Use Case Diagram for user
2.4 Functional Modeling
2.4.1 Data Flow Diagram
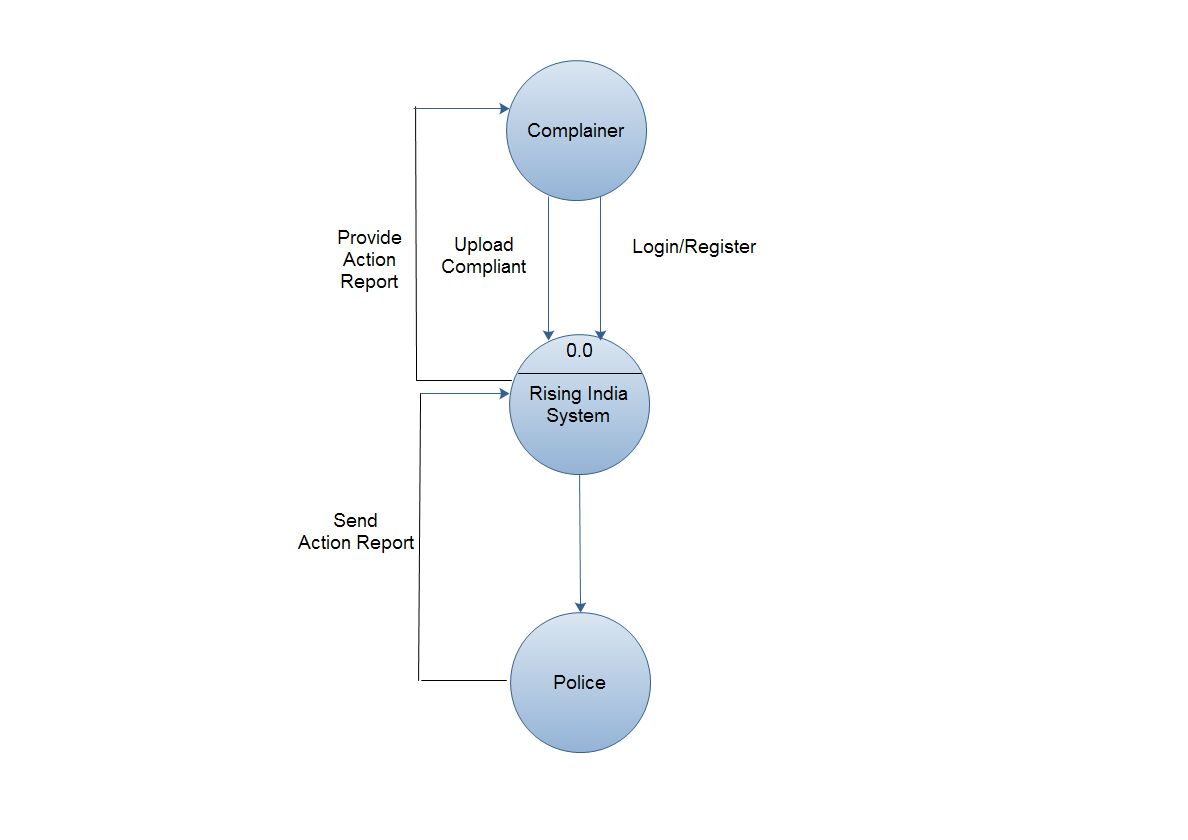 Fig. 2.4 Context Level Data Flow Diagram
Fig. 2.4 Context Level Data Flow Diagram
- Level-1DFD:-
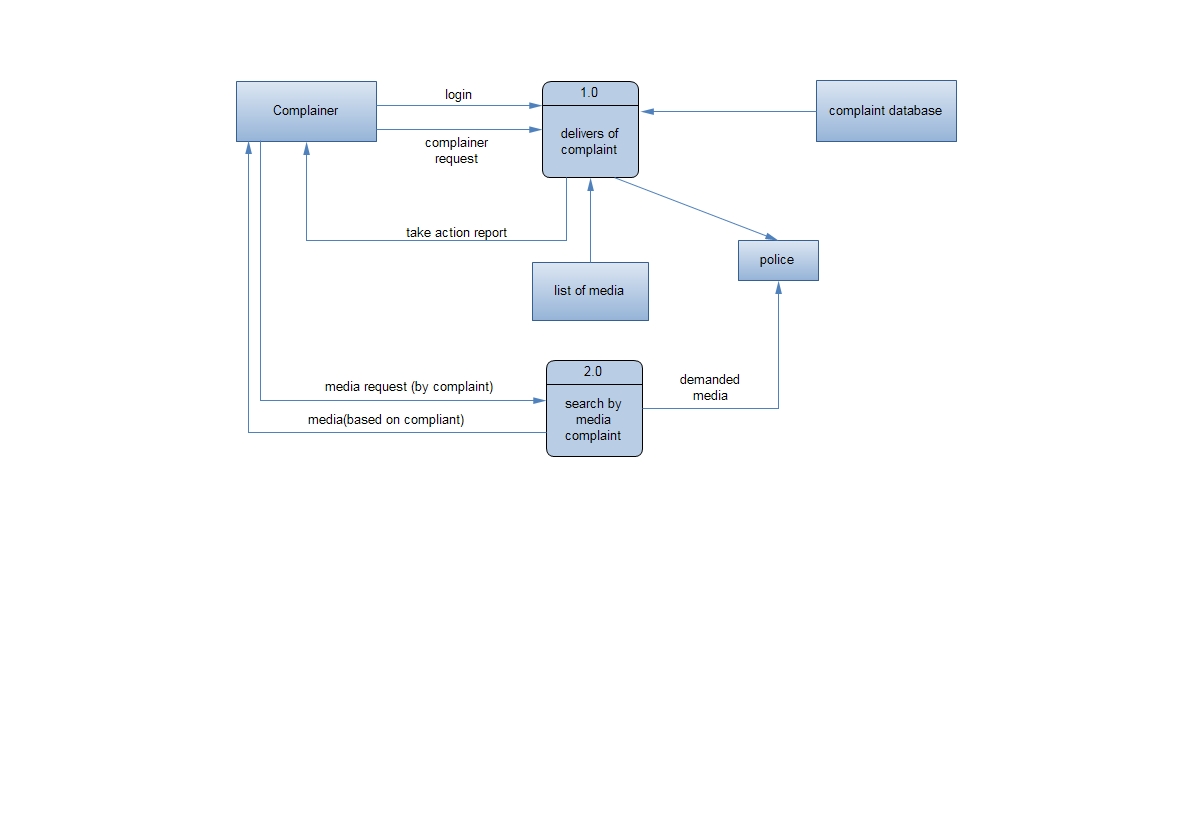
Fig 2.5 level 1 dfd diagram
2.5 Class Diagram
Introduction
- The class diagram is a static diagram.
- A class model captures the static structure of a system by characterizing the objects in the system, the relationship between the objects, and the attributes and operations for each class of objects.
- The class diagram can be mapped directly with object oriented languages.
- The class model is the most important among the three models.
- Class diagram provide a graphical notation for modeling classes and their relationship.
- They are concise, easy to understand, and work well in practice.
- Class diagrams are the backbone of almost every object-oriented method including UML.
- They describe the static structure of a system.
Purpose
- Analysis and design of the static view of an application.
- Describe responsibilities of a system.
- Base for component and deployment diagrams.
When to use : Class Diagram
Useful for Forward and Reverse engineering.
Class diagrams are useful both for abstract modeling and for designing actual programs.
Developer uses class diagram for implementation decision.
Business analysts can use class diagrams to model systems from the business perspective.
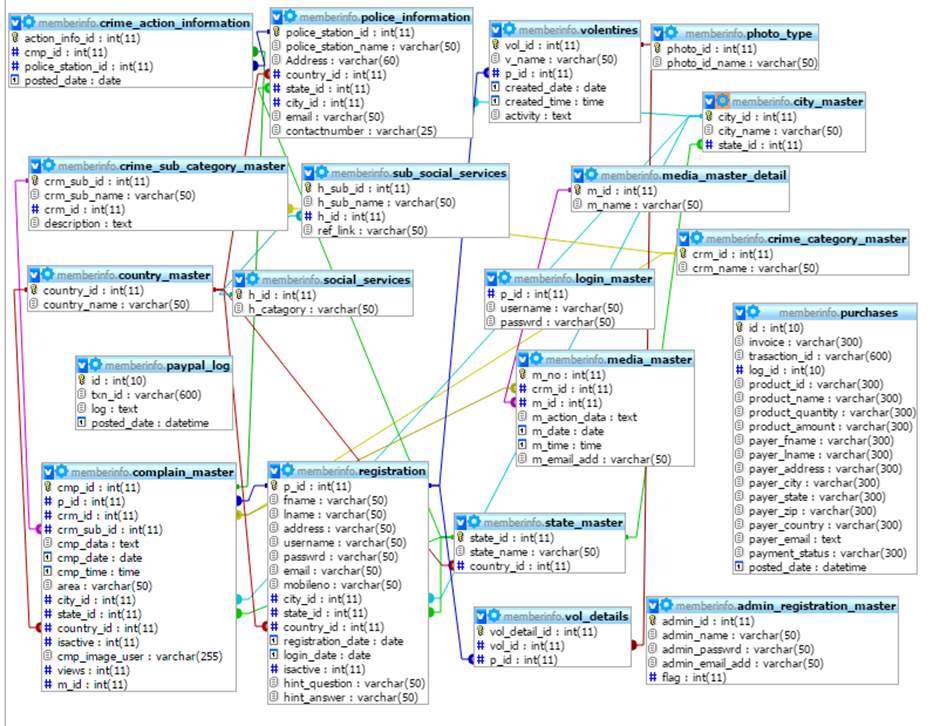 Fig. 2.6 Class Diagram
2.6 Activity Diagram
Fig. 2.6 Class Diagram
2.6 Activity Diagram
An activity diagram shows the sequence of steps that make up a complex process, such as an algorithm or workflow.
An activity diagram shows flow of control, similar to a sequence diagram, but focuses on operation rather than one objects.
Activity diagrams the early stages of designing algorithms and workflows.
Activities:-
The steps of an activity diagram are operations, specially activities from the state model.
The purpose of an activity diagram is to show the steps within a complex process and the sequencing constraints among them.
Some activities run forever until an outside event interrupts them, but most activities eventually complete their work and terminate by themselves.
e.g.:- Execute order, debit account
Branches:-
If there is more than successor to an activity, each arrow may be labelled with a condition in square brackets.
e.g.:- [failure]
Initiation and Termination:-
A solid circle with an outgoing arrow shows starting point of a activity diagram. When control reaches a bull’s-eye, the execution is completed or terminated.
Concurrent Activities:-
Unlike traditional flow charts, organizations & computer system can perform more than one activity at a time. The place of activity can also change overtime.



Fig 2.7 Activity Diagram of Complain Registration
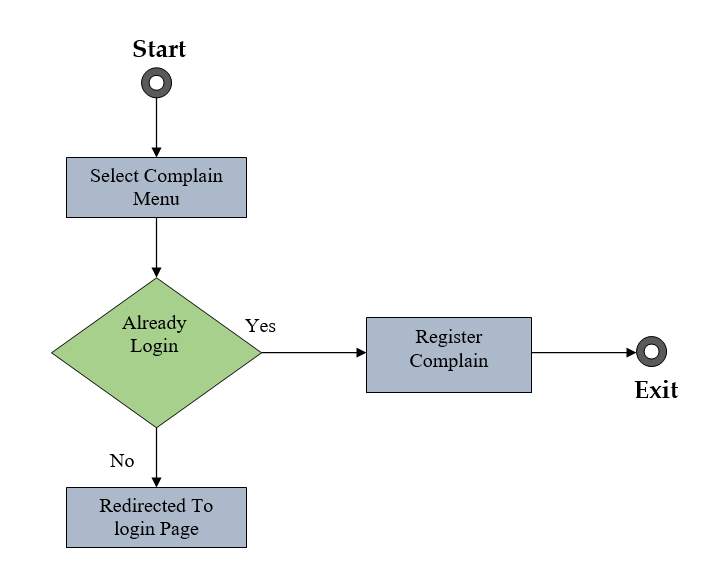
Fig 2.8 Activity Diagram of Complain Searching
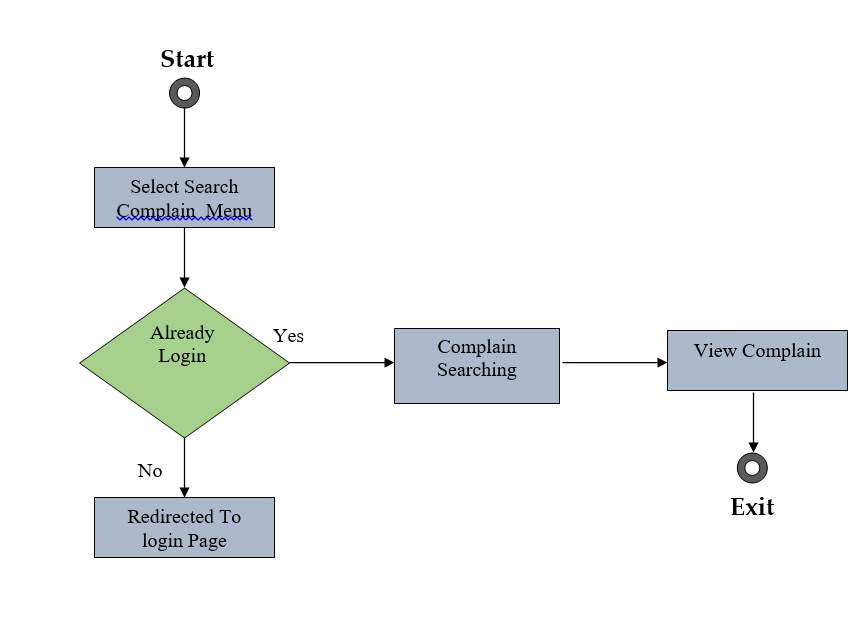
Fig 2.9 Activity Diagram of Manage Menu





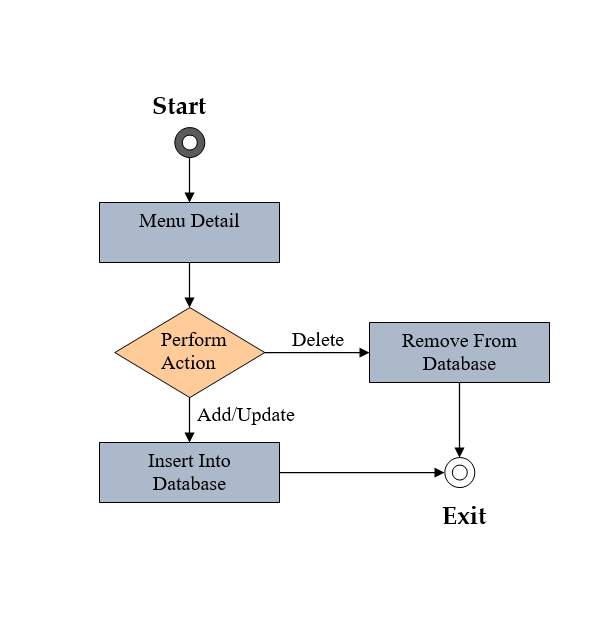
Fig 2.10 Activity Diagram of Manage Crime Category





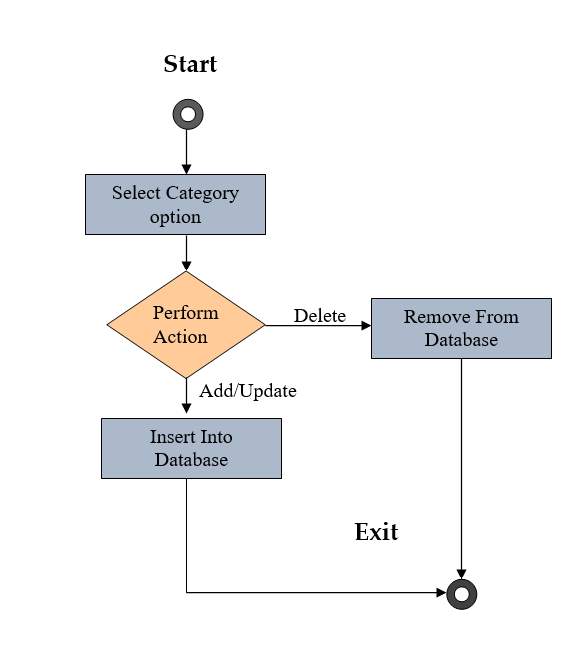
Fig 2.11:- Activity Diagram of Manage Sub-Category
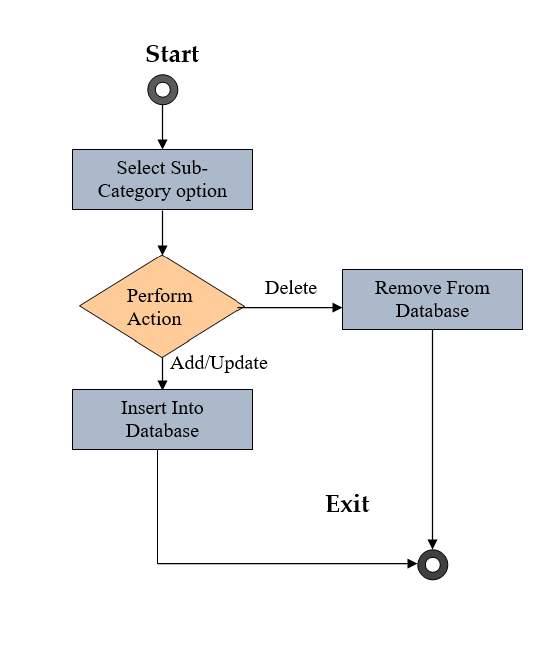




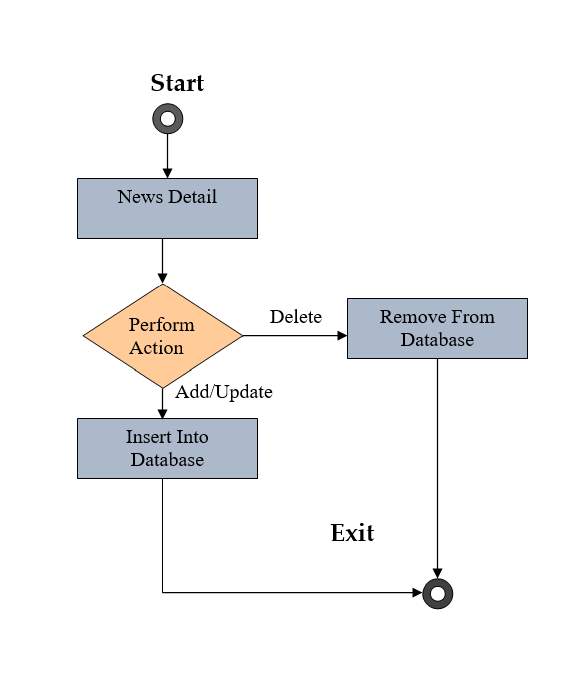
Fig 2.12 Activity Diagram of Manage News





 4.6 Sequence Diagram
4.6 Sequence Diagram
A sequence diagram shows the participants in an interaction & a sequence of message among them.
It shows interaction of a system with its actor to perform all or part of use case.
Each actor as well as a system is represented by a vertical line called a lifetime.
There are two kinds of sequence models
o Scenarios
o Structure Format Sequence diagram
Scenarios:-
A scenario is a sequence of events that occurs during one particular execution of the system such as for a use case.
The scope of the scenario can vary; it may include all events in the system or it may include only those events in the system.
It impinging on or generated by certain objects. a scenario can be the historical record of executing an actual system or a thought experiments of executing a proposed system.
A scenario can be displayed as a list of text statements. A scenario contains messages between objects as well as activities performed by objects.
2.7 Sequence Diagram
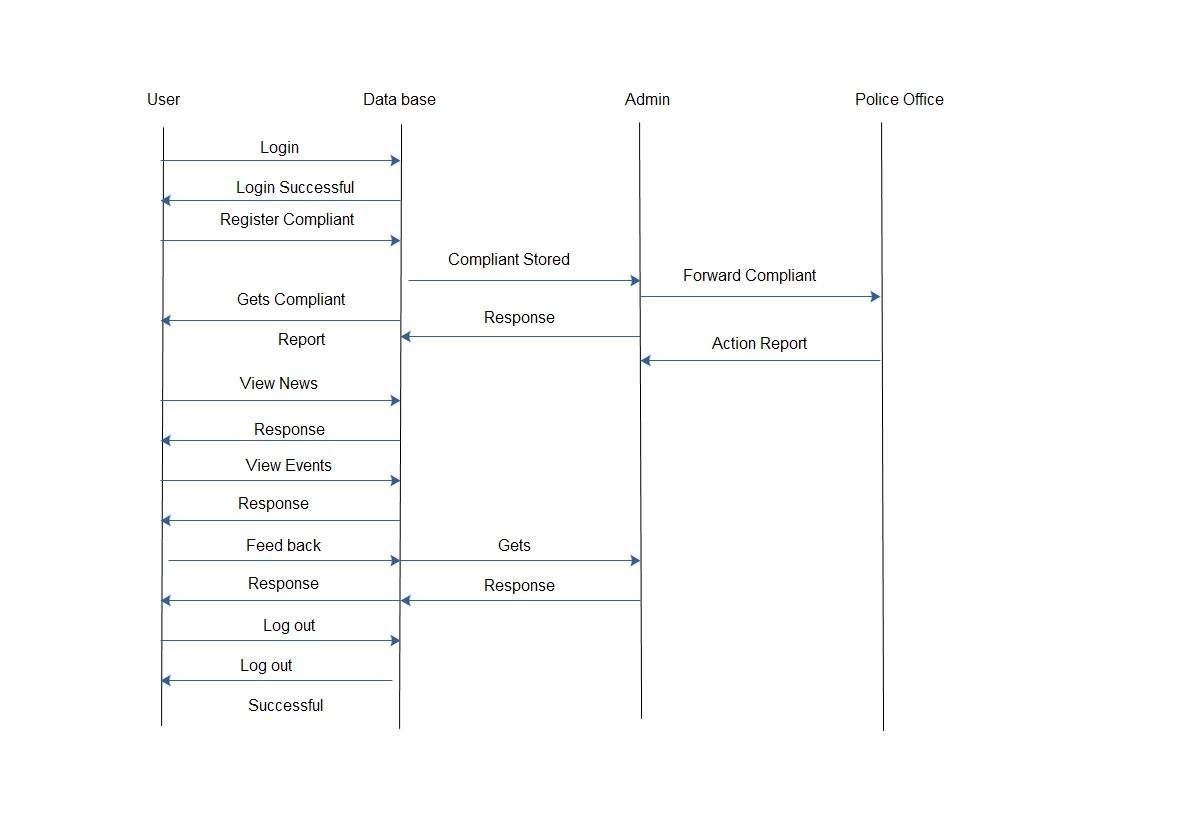 Fig. 2.13 Sequence Diagram
2.9 Input Output and interface design
Login:
Input:-
Fig. 2.13 Sequence Diagram
2.9 Input Output and interface design
Login:
Input:-
 Login
Login


Username:
Password:
Forgot password?
Output:-

Login successful……
Fig 2.14 login
Registration:-
Input:-
 Registration
Registration

User name:

Password:

First name:

Last name:

Address:

City:

State:

Date of birth:



Securityquestion:
Answer:

SUBMIT
Fig 2.15 Registration
Output:-

Registration successful……
2.10 Canvas Explanation
2.10.1 Observation Matrix
 AEIOU Summary:
AEIOU Summary:
Fig. 2.16AEIOU Summary Canvas
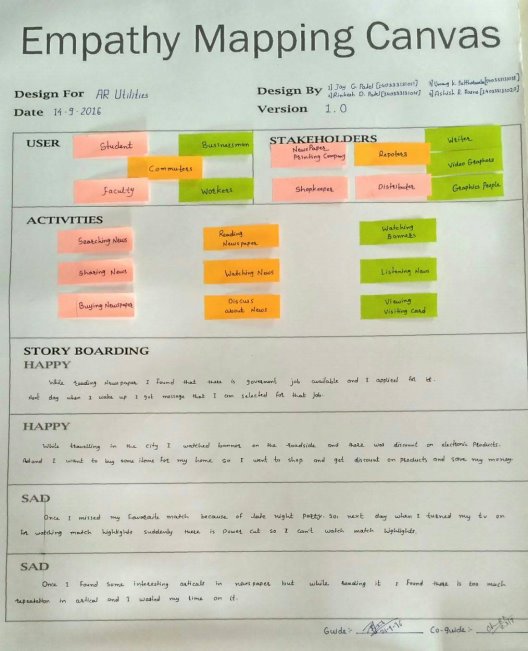 Fig 2.17 Empathy MappingCanvas
Fig 2.17 Empathy MappingCanvas
- Ideation Canvas:
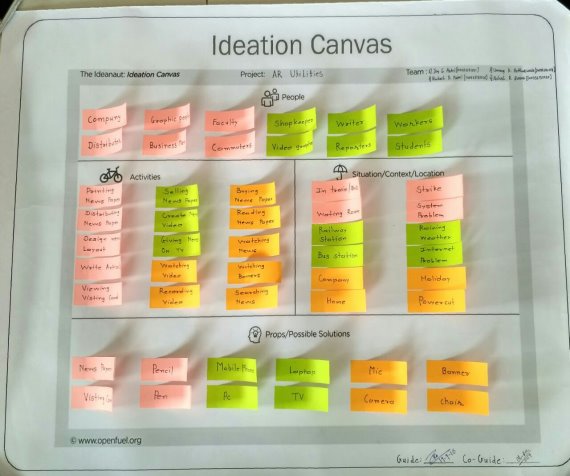 Fig 2.18 Ideation Canvas
Fig 2.18 Ideation Canvas
- Product Development Canvas:
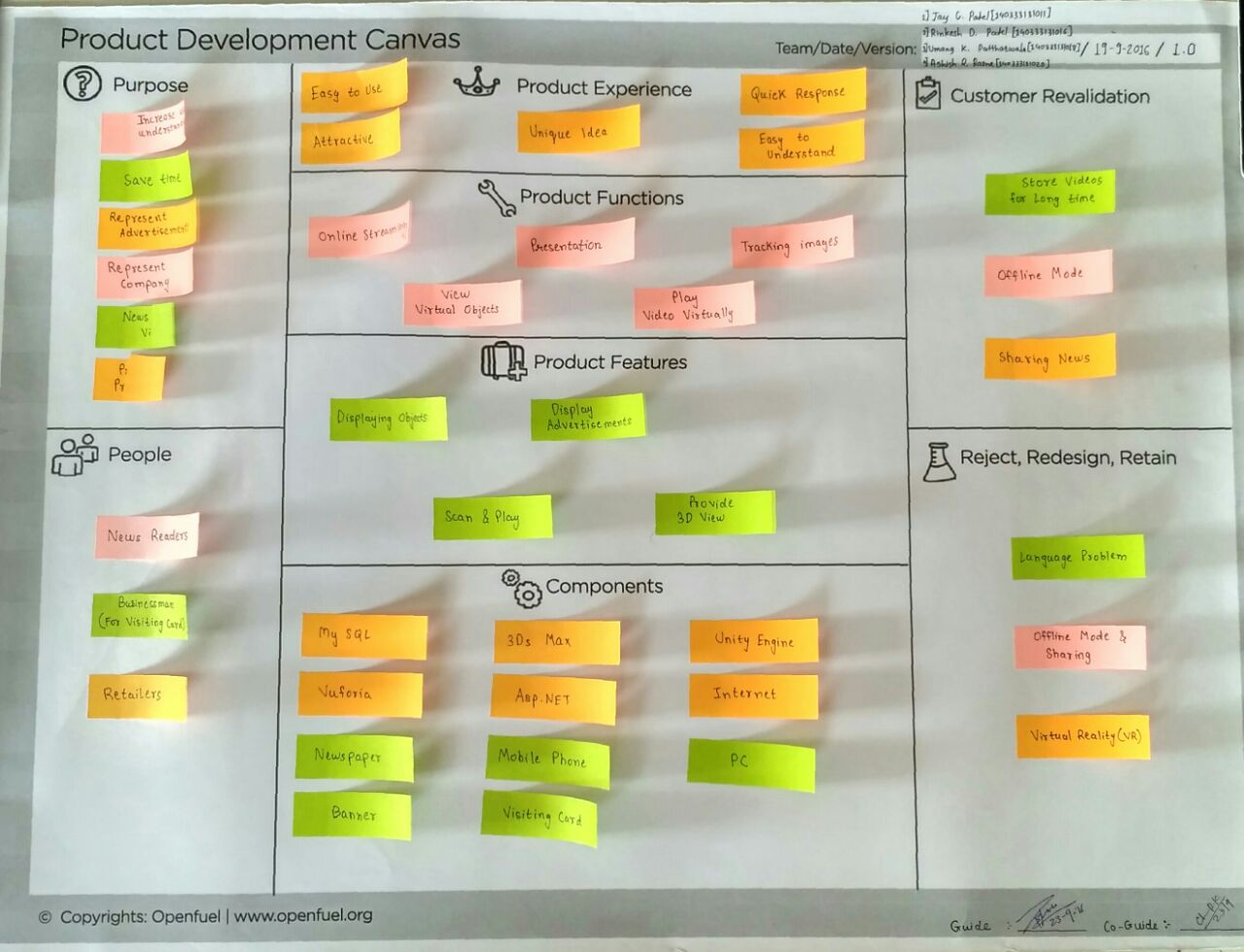 Fig 2.19 Product Development Canvas
Fig 2.19 Product Development Canvas
Chapter 3: Implementation
3.1 Screenshots
3.1 Add Area Page
3.2 Add City Page
3.3 Add Crime Type Page
3.4 Add Crime Sub –Type Page
3.5 Add Donation Page
3.6 Add Event Page
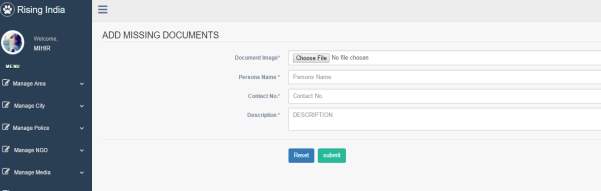
3.7 Add Missing Documents Page
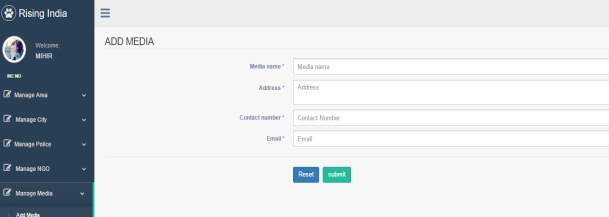
3.8 Add Media Page
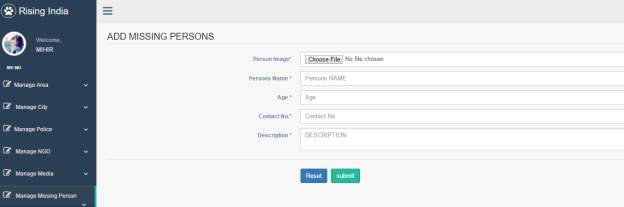
3.9 Add Missing Person Page
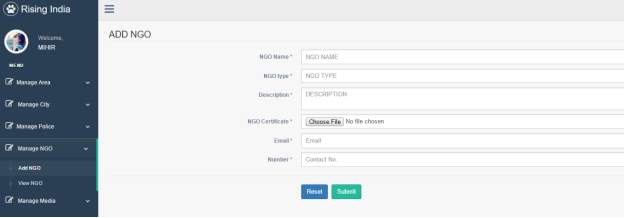
3.10 Add NGO Page
3.11 Add Police Station Page
3.12 Add Registration Page
3.13 View Area Page
3.14 View City Page
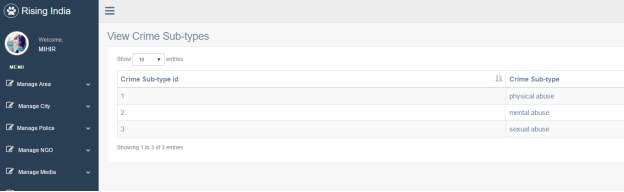
3.15 View Crime Sub-Type Page
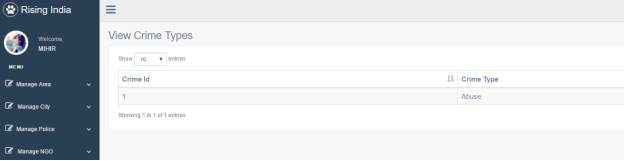
3.16 View Crime Types Page
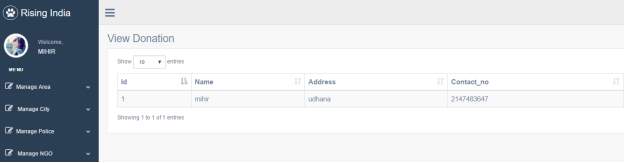
3.17 View Donation Page
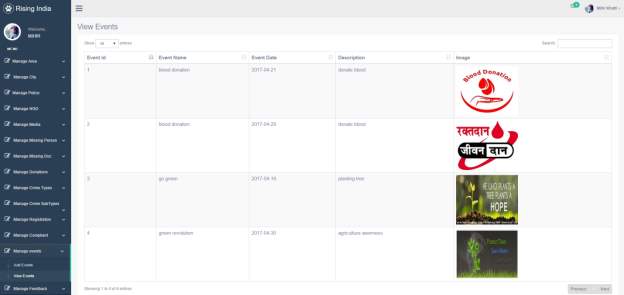
3.18 View Events Page
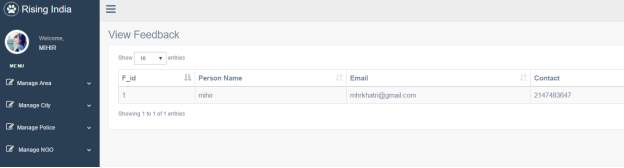
3.19 View Feed Back Page
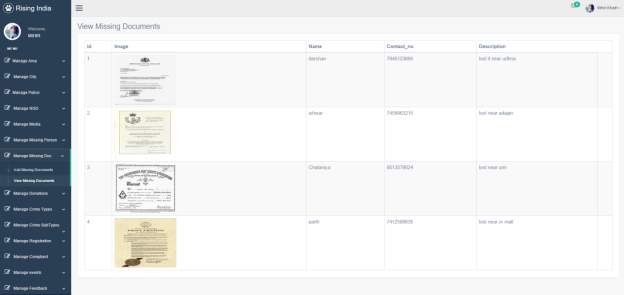
3.20 View Missing Documents Page
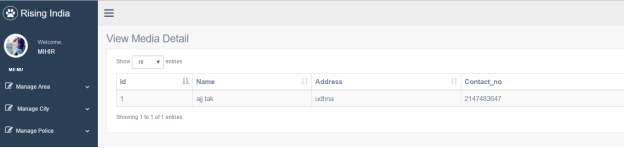
3.21 View Media Detail Page
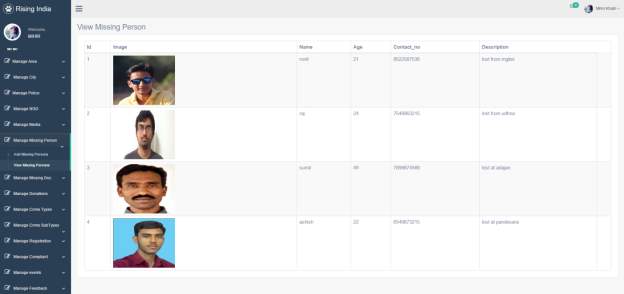
3.22 View Missing Person Page
3.23 View NGO Page
3.24 View Police Station Page
3.25 View Registration Page
Client Side
3.26 Compliant Page
3.27 Missing Person Page
3.28 Home Page
3.29 Home Page 1

3.30 Home Page 3

3.31 Home Page 4
3.32 Missing Document Page
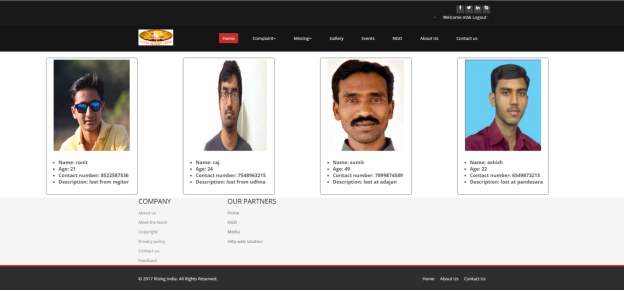
3.33 Missing Person Page
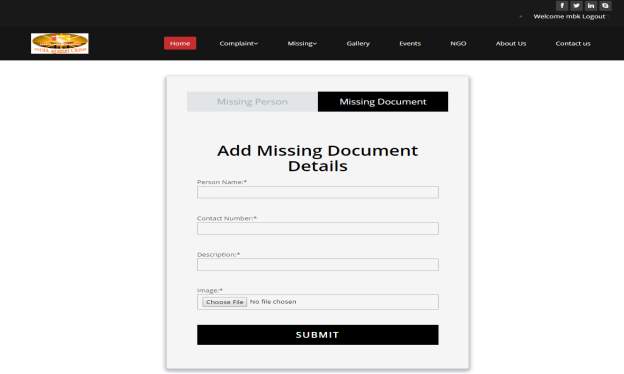
3.34 Add Missing Documents Detail Page
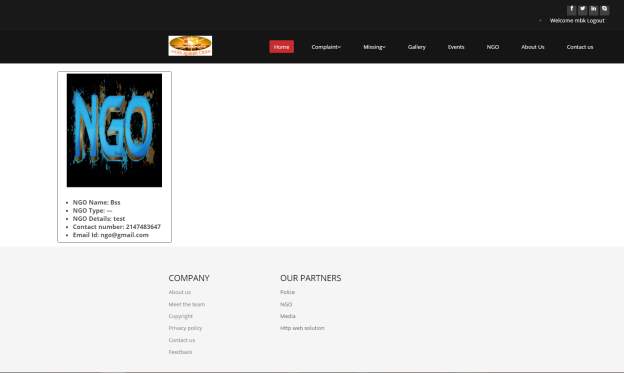
3.35 NGO Page


3.36 (Home Page)
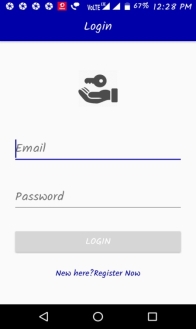
3.37 Login Page

3.38 Registration Page
3.39 User Profile Page
3.40 Upload Complaint Page
3.41View Complaint Page

Missing Person Page

3.42 Missing Document Page

3.43 NGO Page
3.44 Donation Page
3.45 Feed back Page
3.46 Rating page
3.2 Sample Code
Add complain api:
<?php
class addcomplian {
public $count ="";
public $status = "";
public $message="";
// public $img = "";
}
class ac
{
public $image="";
public $compdate="";
public $area="";
public $city="";
public $crime="";
public $crimesub="";
public $description="";
}
header('Content-type : bitmap; charset=utf-8');
if(isset($_POST["image"])){
$path = "../admin/production/images/missingdoc/";
$imagename = time().".jpg";
$encoded_string = base64_to_jpeg($_POST["image"], $path.$imagename);
$compdate = $_POST["date"];
$area = $_POST["area"];
$city = $_POST["city"];
$crime = $_POST["crime"];
$crimesub = $_POST["crimesub"];
$description = $_POST["desc"];
include '../connection.php';
$sql = "insert into tbl_complain_regi values('','" . $_SESSION['user_id'] . "','$imagename','$compdate','$area','$city','$crime','$crimesub','$description')";
$result = $con->query($sql);
$addcomplian = new addcomplian();
$addcomplian->status = true;
$addcomplian->message="Record insert sucessfully";
if($result == 0){
$addcomplian->status = false;
$addcomplian->message="Record not insert sucessfully";
}
$addcomplian->count=$result;
$data=json_encode($addcomplian);
echo $data;
}
function base64_to_jpeg($base64_string, $output_file) {
$ifp = fopen($output_file, "wb");
$data = explode(',', $base64_string);
fwrite($ifp, base64_decode($data[1]));
fclose($ifp);
return $output_file;
}
?>
Registration api:
<?php
class registration {
public $count ="";
public $status = "";
public $message="";
// public $img = "";
}
class regi
{
public $image="";
public $firstname="";
public $lastname="";
public $email="";
public $phone="";
public $username="";
public $password="";
public $address="";
public $birthdate="";
public $city="";
public $date="";
public $question="";
public $answer="";
}
header('Content-type : bitmap; charset=utf-8');
if(isset($_POST["image"])){
$path = "../admin/production/images/missingdoc/";
$imagename = time().".jpg";
$encoded_string = base64_to_jpeg($_POST["image"], $path.$imagename);
$fname = $_POST["fname"];
$lname = $_POST["lname"];
$email = $_POST["email"];
$phone = $_POST["phone"];
$uname = $_POST["uname"];
$pass = $_POST["pass"];
$add = $_POST["add"];
$bday = $_POST["bday"];
$city = $_POST["city"];
$date = $_POST["date"];
$ques = $_POST["ques"];
$ans = $_POST["ans"];
include '../connection.php';
$sql = "insert into tbl_registration values('','$fname','$lname','$email','$phone','$uname','$pass','$add','$bday','$city','$date','$ques','$ ans','$imagename')";
echo $sql;
$result = $con->query($sql);
$registration = new registration();
$registration->status = true;
$registration->message="Record insert sucessfully";
if($result == 0){
$registration->status = false;
$registration->message="Record not insert sucessfully";
}
$registration->count=$result;
$data=json_encode($registration);
echo $data;
}
function base64_to_jpeg($base64_string, $output_file) {
$ifp = fopen($output_file, "wb");
$data = explode(',', $base64_string);
fwrite($ifp, base64_decode($data[1]));
fclose($ifp);
return $output_file;
}
?>
Login api:
<?php
class Login {
public $count ="";
public $status = "";
public $result = array();
}
if(isset($_GET["username"])){
$username = $_GET["username"];
$password = $_GET["password"];
include '../connection.php';
$sel = "select * from tbl_registration where user_name='$username' and password='$password'";
$res = $con->query($sel);
$login = new Login();
$login->status = true;
$num = 1;
$count = 0;
while ($row = $res->fetch_assoc()) {
$login->result[] = $row;
$count++;
}
if($count == 0){
$login->status = false;
}
$login->count = $count;
echo json_encode($login);
}
?>
<?php
include 'phead.php';
?>
<style>
.form-controla
{
width: 950px;
height:auto;
padding: 7px 12px;
border-color: #f2f2f2;
box-shadow: none;
}
</style>
<?php
include './connection.php';
$insert = "insert into tbl_action_report values(0,'" . $_POST['txtno'] . "','" . $_POST['txtoff'] . "','" . $_POST['txtdate'] . "','" . $_POST['txtpre'] . "','" . $_POST['txtevent'] . "','" . $_POST['txtaction'] . "','" . $_POST['txtevent'] . "')";
$result = $con->query($insert);
?>
<section id="contact-page">
<div class="container">
<div class="center">
<h2>Police Action Report</h2>
</div>
<div class="row contact-wrap">
<form id="main-contact-form" class="contact-form" method="post" action="sendemail.php">
<div class="col-sm-5 col-sm-offset-1">
<div class="form-group">
<label>Case No *</label>
<input type="text" name="txtno" class="form-control" required="required">
</div>
<div class="form-group">
<label>Reporting Officer *</label>
<input type="text" name="txtoff" class="form-control" required="required">
</div>
</div>
<div class="col-sm-5">
<div class="form-group">
<label>Date *</label>
<input type="date" name="txtdate" class="form-control" required="required">
</div>
<div class="form-group">
<label>Prepaired By *</label>
<input type="text" name="txtpre" class="form-control" required="required">
</div>
</div>
<div class="col-sm-5 col-sm-offset-1">
<div class="form-group">
<label>Detail of Event *</label>
<textarea name="txtevent" required="required" class="form-control" rows="10"></textarea>
</div>
</div>
<div class="col-sm-5">
<div class="form-group">
<label>Action Taken *</label>
<textarea name="txtaction" required="required" class="form-control" rows="10"></textarea>
</div>
</div>
<div class="col-sm-5 col-sm-offset-1">
<div class="form-group">
<label>Summary *</label>
<textarea name="txtevent" required="required" class="form-controla" rows="3"></textarea>
</div>
<div class="form-group" align="right">
<input type="submit" name="sbtnok" class="btn btn-primary btn-lg" required="required">
</div>
</div>
</form>
</div><!--/.row-->
</div><!--/.container-->
</section><!--/#contact-page-->
<?php
include 'pfoot.php';
?>
Complaint page code:-
<?php
include 'phead.php';
?>
<style>
.profile
{
height: 550px;
width: 300px;
border: 2px;
border-radius: 5px;
margin: 20px 0px 10px 150px;
float: left;
}
</style>
<?php
include './connection.php';
$select = "select complain_media,complain_date,area_name,city_name,crime_type,crime_subtype,description from tbl_complain_regi";
$result = $con->query($select);
if(isset($_POST['btnok']))
{
header('Location: report.php');
}
?>
<div>
<form action="report.php" method="post">
<div class="x_content">
<table>
<th>
<div>
<?php
while ($row = $result->fetch_assoc()) {
?>
<div class="profile">
<center><img loading="lazy" src="./images/compmedia/<?php echo $row["complain_media"]; ?>" id="element-imagepro-cb49a4e0-de9e-461c-888f-3a9fa61fbd05-1" alt="Image" width="250" height="300"></center>
<br/>
<ul>
<li><strong>Complaint date:</strong><?php echo $row["complain_date"] ?></li>
<li><strong>Area: </strong><?php echo $row["area_name"] ?></li>
<li><strong>City: </strong><?php echo $row["city_name"] ?></li>
<li><strong>Complaint type: </strong><?php echo $row["crime_type"] ?></li>
<li><strong>sub-type: </strong><?php echo $row["crime_subtypes"] ?></li>
<li><strong>Description </strong><?php echo $row["description"] ?></li>
<a href="report.php">Action report</a>
</ul>
</div>
<?php
}
?>
</div>
</th>
</table>
</form>
</div>
<?php
include 'pfoot.php';
?>
View Police Station:-
<?php
include 'phead.php';
include './connection.php';
$select = "select * from tbl_policestation";
$result = $con->query($select);
?>
<div class="container">
<div class="center">
<h2>Police Stations</h2>
</div>
<div class="row contact-wrap">
<form id="main-contact-form" class="contact-form">
<div class="col-sm-5 col-sm-offset-1">
<table class="table table-striped table-bordered">
<thead>
<tr>
<th>Police Station Name</th>
<th>Address</th>
<th>Contact No.</th>
<th>Email</th>
<th>Area</th>
<th>City</th>
</tr>
</thead>
<tbody>
<?php
while($row=$result->fetch_assoc()) {
?>
<tr>
<td><?php echo $row["ps_name"] ?></td>
<td><?php echo $row["address"] ?></td>
<td><?php echo $row["contact_no"] ?></td>
<td><?php echo $row["email_id"] ?></td>
<td><?php echo $row["area_name"] ?></td>
<td><?php echo $row["city_name"] ?></td>
</tr>
<?php
}
?>
</tbody>
</table>
</div>
</form>
</div>
</div>
<?php
include 'pfoot.php'; ?>
3.3 Testing and Verification
Table 3.1 Test Case
| Test case Id |
Activity |
Expected Result |
Actual Result |
Rest Case Status |
Comments |
| 01 |
Registration |
Registration
Error |
Registration
Fail |
Fail |
Display error message |
| 02 |
Registration |
Allow Registration |
Registration
Successfully |
Pass |
Display Registration page |
| 03 |
Login |
Login Error |
Login Fail |
Fail |
Display Error message |
| 04 |
Login |
Allow Login |
Login Successfully |
Pass |
Display Login page |
| 05 |
Upload Compliant |
File not Specified |
Upload image fail |
Fail |
Error Message Provided |
| 06 |
Upload Compliant |
Allow Uploaded |
Image Uploaded |
Pass |
Display Image Uploaded |
| 07 |
View Compliant |
Incorrect Details |
Incorrect Details |
Fail |
No valid Details |
| 08 |
View Compliant |
Data fetched |
Data fetched |
Pass |
Display data fetched successfully |
| 09 |
Uploading Missing |
Missing upload fail |
Missing upload fail |
Fail |
No data inserted |
| 10 |
Uploading missing |
Missing uploaded successfully |
Data fetched |
Pass |
Display data fetched successfully |
| 11 |
Events upload |
Upload fail |
Upload fail |
Fail |
Upload unsuccessful |
| 12 |
Events upload |
Upload success |
Upload success |
Pass |
Upload successful |
| 13 |
Add NGO |
Upload error |
Fail to upload |
Fail |
NGO not uploaded |
| 14 |
Add NGO |
Upload success |
Successfully upload |
Pass |
Display NGO data |
| 15 |
Add Police |
Upload unsuccessful |
Upload unsuccessful |
Fail |
Details uploaded unsuccessfully |
| 16 |
Add Police |
Upload successful |
Upload successful |
Pass |
Display uploaded successfully |
| 17 |
View missing |
View successful |
View successful |
Pass |
Display successfully |
| 18 |
Add gallery |
Upload fail |
Upload fail |
Fail |
Display unsuccessful |
| 19 |
Add gallery |
Uploads success |
Uploads success |
Pass |
Display successful |
| 20 |
Add feedback |
Feedback unsuccessful |
Feedback unsuccessful |
Fail |
Display unsuccessful |
| 21 |
Add feedback |
Feedback successful |
Feedback successful |
Pass |
Display successful |
| 22 |
Update Profile |
No Profile selected |
No Profile selected |
Fail |
Display Profile Update unsuccessful |
| 23 |
Update Profile |
Updates selected Profile |
Updates selected Profile |
Pass |
Profile Updated |
| 24 |
Upload Donation |
No data inserted |
No data inserted |
Fail |
Display unsuccessful |
| 25 |
Upload Donation |
Data inserted |
Data inserted |
Pass |
Data inserted |
Chapter 4: ADVANTAGES AND LIMITATION
- Easy to Use
- Better Understanding
- Helps clients to directly upload their files to the ADMIN so they can embed their data to our application.
- Without any fear common man can complaint against any anti-social activity
- Police can easily take action on the particular complaint with the help of complaint detail
l
- The identity of complainer is hide and only known by admin so it provide security to the complainer against the warning and also without any kind of interrogation
- With the help of complaint police can also locate the exact place by using GPS and location provide by Admin with complaint
- System also help the person to find out the missing document as well as person of someone
- NGOs connected with our system will help to take better care of special persons like the small kids, other mental patients
- Android Phone with good specification is mandatory for running the application efficiently
- It requires internet connection to access the system
- Registration must required
- The media can’t be stored for longer time because of storage limits
- Contact with NGO
- Identity of User is hidden MGITER\CSE\2016-17
- Blocking of fake user
- Perform donations
 Figure 1.1:- Type of crimes and the threat percentage of these crimes-
Figure 1.1:- Type of crimes and the threat percentage of these crimes-
 Figure 1.2:- Statistics of the cyber crime-
Figure 1.2:- Statistics of the cyber crime-
 Figure 1.3: BAC of Victims
Figure 1.3: BAC of Victims
 Figure 4:- Occupation of the Victims
Conclusion:
Drunk driving is a major problem in India and other developing regions of the world. Strict reinforcement supplemented with education is one of the most powerful tools to tackle the problem in low. Other measures like increasing the legal drinking age, restricting the availability of alcohol by limiting timings.
5. Research paper on Case laws of Fraud, forgery and Corruption in Banks and Financial Institutions in India
Publish Year: IOSR Journal of Economics and Finance (IOSR-JEF) e-ISSN: 2321-5933, p-ISSN: 2321-5925.Volume 3, Issue 6. (May-Jun. 2014), PP 53-57 www.iosrjournals.org
Author name: Hari Ram Anthelia,
M.A.(Poles.) , LL.M, (NET) CAIIB, (PhD)
Abstract:
Corruption is very bad disease in recent time. It is very harmful for our society. It is opposite to democracy and social order. Corruption also affect the economy of country and its cultural heritage. The purpose of this study is get rid from fraud and corruption committed by the criminals, outsiders customers and employees of the banks and financial institutions and other State, Central and Local bodies, public and private sectors.
Objective:-
The main objectives of this research paper are as under:
Figure 4:- Occupation of the Victims
Conclusion:
Drunk driving is a major problem in India and other developing regions of the world. Strict reinforcement supplemented with education is one of the most powerful tools to tackle the problem in low. Other measures like increasing the legal drinking age, restricting the availability of alcohol by limiting timings.
5. Research paper on Case laws of Fraud, forgery and Corruption in Banks and Financial Institutions in India
Publish Year: IOSR Journal of Economics and Finance (IOSR-JEF) e-ISSN: 2321-5933, p-ISSN: 2321-5925.Volume 3, Issue 6. (May-Jun. 2014), PP 53-57 www.iosrjournals.org
Author name: Hari Ram Anthelia,
M.A.(Poles.) , LL.M, (NET) CAIIB, (PhD)
Abstract:
Corruption is very bad disease in recent time. It is very harmful for our society. It is opposite to democracy and social order. Corruption also affect the economy of country and its cultural heritage. The purpose of this study is get rid from fraud and corruption committed by the criminals, outsiders customers and employees of the banks and financial institutions and other State, Central and Local bodies, public and private sectors.
Objective:-
The main objectives of this research paper are as under:
 Publish Year: This online publication is based upon Identity Theft Literature Review, by Graeme R. Newman and Megan M. McNally, final report to the National Institute of Justice, July 2005,
Publish Year: This online publication is based upon Identity Theft Literature Review, by Graeme R. Newman and Megan M. McNally, final report to the National Institute of Justice, July 2005,
 Abstract:
What did the researchers find?
• Although anyone is potentially vulnerable to theft of credit card-related information, individuals are more likely to be victimized by persons who have access to their identifying information, such as family members and persons with whom they share living quarters.
• Identity theft generally involves three stages: acquisition, use, and discovery. Evidence suggests that the longer it takes to discover the theft, the greater the loss incurred and the smaller the likelihood of successful prosecution. Older persons and those with less education are less likely to discover the identity theft quickly and to report it after discovery.
Research address the three main areas of vulnerability to identity theft—
1. Practices and operating environments of document-issuing agencies that allow offenders to exploit opportunities to obtain identity documents.
2. Practices and operating environments of document-authenticating agencies that allow offenders access to identity data, subsequently used for financial gain, avoiding arrest, or remaining anonymous.
3. The structure and operations of the information systems involved with the operational procedures of agents in (1) and (2).
Abstract:
What did the researchers find?
• Although anyone is potentially vulnerable to theft of credit card-related information, individuals are more likely to be victimized by persons who have access to their identifying information, such as family members and persons with whom they share living quarters.
• Identity theft generally involves three stages: acquisition, use, and discovery. Evidence suggests that the longer it takes to discover the theft, the greater the loss incurred and the smaller the likelihood of successful prosecution. Older persons and those with less education are less likely to discover the identity theft quickly and to report it after discovery.
Research address the three main areas of vulnerability to identity theft—
1. Practices and operating environments of document-issuing agencies that allow offenders to exploit opportunities to obtain identity documents.
2. Practices and operating environments of document-authenticating agencies that allow offenders access to identity data, subsequently used for financial gain, avoiding arrest, or remaining anonymous.
3. The structure and operations of the information systems involved with the operational procedures of agents in (1) and (2).
 Figure 5:- How personal information is obtained
Figure 5:- How personal information is obtained

 Fig. 2.1 ER Diagram
2.3 Use Case Modeling
2.3.1 Use Case diagram for admin:-
Fig. 2.1 ER Diagram
2.3 Use Case Modeling
2.3.1 Use Case diagram for admin:-
 Fig. 2.2 Use Case Diagram for admin
Fig. 2.2 Use Case Diagram for admin
 Fig. 2.3 Use Case Diagram for user
2.4 Functional Modeling
2.4.1 Data Flow Diagram
Fig. 2.3 Use Case Diagram for user
2.4 Functional Modeling
2.4.1 Data Flow Diagram
 Fig. 2.4 Context Level Data Flow Diagram
Fig. 2.4 Context Level Data Flow Diagram

 Fig. 2.6 Class Diagram
2.6 Activity Diagram
Fig. 2.6 Class Diagram
2.6 Activity Diagram


 Fig 2.7 Activity Diagram of Complain Registration
Fig 2.7 Activity Diagram of Complain Registration
 Fig 2.8 Activity Diagram of Complain Searching
Fig 2.8 Activity Diagram of Complain Searching
 Fig 2.9 Activity Diagram of Manage Menu
Fig 2.9 Activity Diagram of Manage Menu





 Fig 2.10 Activity Diagram of Manage Crime Category
Fig 2.10 Activity Diagram of Manage Crime Category





 Fig 2.11:- Activity Diagram of Manage Sub-Category
Fig 2.11:- Activity Diagram of Manage Sub-Category




 Fig 2.12 Activity Diagram of Manage News
Fig 2.12 Activity Diagram of Manage News





 4.6 Sequence Diagram
4.6 Sequence Diagram
 Fig. 2.13 Sequence Diagram
2.9 Input Output and interface design
Login:
Input:-
Fig. 2.13 Sequence Diagram
2.9 Input Output and interface design
Login:
Input:-
 Login
Login

 Username:
Password:
Forgot password?
Output:-
Username:
Password:
Forgot password?
Output:-
 Login successful……
Fig 2.14 login
Registration:-
Input:-
Login successful……
Fig 2.14 login
Registration:-
Input:-
 Registration
Registration
 User name:
User name:
 Password:
Password:
 First name:
First name:
 Last name:
Last name:
 Address:
Address:
 City:
City:
 State:
State:
 Date of birth:
Date of birth:


 Securityquestion:
Answer:
Securityquestion:
Answer:
 SUBMIT
Fig 2.15 Registration
Output:-
SUBMIT
Fig 2.15 Registration
Output:-
 Registration successful……
2.10 Canvas Explanation
2.10.1 Observation Matrix
Registration successful……
2.10 Canvas Explanation
2.10.1 Observation Matrix
 AEIOU Summary:
AEIOU Summary: Fig 2.17 Empathy MappingCanvas
Fig 2.17 Empathy MappingCanvas
 Fig 2.18 Ideation Canvas
Fig 2.18 Ideation Canvas
 Fig 2.19 Product Development Canvas
Fig 2.19 Product Development Canvas
 3.1 Add Area Page
3.1 Add Area Page
 3.2 Add City Page
3.2 Add City Page
 3.3 Add Crime Type Page
3.3 Add Crime Type Page
 3.4 Add Crime Sub –Type Page
3.4 Add Crime Sub –Type Page
 3.5 Add Donation Page
3.5 Add Donation Page
 3.6 Add Event Page
3.6 Add Event Page
 3.7 Add Missing Documents Page
3.7 Add Missing Documents Page
 3.8 Add Media Page
3.8 Add Media Page
 3.9 Add Missing Person Page
3.9 Add Missing Person Page
 3.10 Add NGO Page
3.10 Add NGO Page
 3.11 Add Police Station Page
3.11 Add Police Station Page
 3.12 Add Registration Page
3.12 Add Registration Page
 3.13 View Area Page
3.13 View Area Page
 3.14 View City Page
3.14 View City Page
 3.15 View Crime Sub-Type Page
3.15 View Crime Sub-Type Page
 3.16 View Crime Types Page
3.16 View Crime Types Page
 3.17 View Donation Page
3.17 View Donation Page
 3.18 View Events Page
3.18 View Events Page
 3.19 View Feed Back Page
3.19 View Feed Back Page
 3.20 View Missing Documents Page
3.20 View Missing Documents Page
 3.21 View Media Detail Page
3.21 View Media Detail Page
 3.22 View Missing Person Page
3.22 View Missing Person Page
 3.23 View NGO Page
3.23 View NGO Page
 3.24 View Police Station Page
3.24 View Police Station Page
 3.25 View Registration Page
Client Side
3.25 View Registration Page
Client Side
 3.26 Compliant Page
3.26 Compliant Page
 3.27 Missing Person Page
3.27 Missing Person Page
 3.28 Home Page
3.28 Home Page
 3.29 Home Page 1
3.29 Home Page 1
 3.30 Home Page 3
3.30 Home Page 3
 3.31 Home Page 4
3.31 Home Page 4
 3.32 Missing Document Page
3.32 Missing Document Page
 3.33 Missing Person Page
3.33 Missing Person Page
 3.34 Add Missing Documents Detail Page
3.34 Add Missing Documents Detail Page
 3.35 NGO Page
3.35 NGO Page

 3.36 (Home Page)
3.36 (Home Page)
 3.37 Login Page
3.37 Login Page


 3.38 Registration Page
3.38 Registration Page
 3.39 User Profile Page
3.39 User Profile Page
 3.40 Upload Complaint Page
3.40 Upload Complaint Page
 3.41View Complaint Page
3.41View Complaint Page
 Missing Person Page
Missing Person Page
 3.42 Missing Document Page
3.42 Missing Document Page

 3.43 NGO Page
3.43 NGO Page
 3.44 Donation Page
3.44 Donation Page
 3.45 Feed back Page
3.45 Feed back Page
 3.46 Rating page
3.2 Sample Code
3.46 Rating page
3.2 Sample Code




