Title: Smart Homes and the Internet of Things
Info: 18592 words (74 pages) Dissertation
Published: 13th Dec 2019
Tagged: TechnologyInternet of Things
List of Figures
Figure 1: An equation for the Internet of Things
Figure 2: IoT Google search popularity growth
Figure 3: 2014 Gartner hype cycle
Figure 4: TCP 3 way handshake
Figure 5: TCP/IP protocol stack
Figure 6: Encapsulation and De-capsulation process
Figure 7: Public and Private IP address ranges
Figure 8: ARM model
Figure 9: C-IoT Architecture layers
Figure 10: 5 Layer Architecture approach
Figure 11: 4 Layer Architecture approach
Figure 12: A layered architecture specifically for smart homes
Figure 13: Smart home system architecture using Wi-Fi
Figure 14: Smart home architecture using Bluetooth
Figure 15: Z-wave system architecture
Figure 16: Security risk analysis on a Smart Home System Architecture
Figure 17: Remote user, Home Automation system framework within a smart home
Figure 18: Remote user, Home Automation system architecture
Figure 19: The Arduino Yun microcontroller
Figure 20: Arduino Yun architecture including the Bridge connecting the Linux and Arduino environments
Figure 21: Home data collection and alert system that utilizes the Arduino Yun
Figure 22: Smart home control centre using an Arduino Yun
List of Tables
Table 1: History of the Internet and the internet of things from 1832 – 2013
Table 2: Commonly used Application layer protocols
Table 3: 4 layer Approach
Table 4: Design considerations for layered Architecture
Table 5: Smart home API’s
Table 6: Smart Home Energy Management Goals
Table 7: Identified security threats during security analysis
Chapter 1
- Introduction
1.1 The internet of things definition
There are many different descriptions to describe “the Internet of things” (IOT), so the first thing to accomplish is to get a clear understanding of what the Internet of things means.
Research by (European IoT research group) [1] tasked with identifying and coordinating the potential of the IoT sector in Europe developed “The Internet of things Strategic Research Roadmap”. In this paper they outline the following vision for the future of the Internet:
- It will be based on universal common communication protocols.
- Computer networks will be merged via the internet including areas such as, things/objects, people, energy, media, services into one common platform supporting networked smart devices.
- They describe the internet in the future as having IoT integrated into it.
- Network infrastructure will be dynamic with the capability to self-configure.
- Devices (Physical or virtual) will have an identity as well as virtual persona’s and physical attributes.
- These devices (Things) will use intelligent interfaces and have the ability to integrate seamlessly to the existing information network.
- The devices (Things) will become part of our everyday personal and business life where they will have the ability to send/receive data which they have sensed around them to themselves and to the people around them and also working independently from human interaction or control.
(The oxford dictionary, 2016) [2] Offers a more simplified description as “a proposed development of the Internet in which everyday objects have network connectivity, allowing them to send and receive data”
(The International Data Cooperation (IDC) 2016) [3] Defines the Internet of things as a “network of networks of uniquely identifiable endpoints (or “things”) that communicate without human interaction using IP connectivity”
(McEwen and Cassimally, 2014: 19) [4] In the book “Designing the Internet of Things” [4] characterizes IoT as connecting a physical object with a computer built into it and using the internet to complete the communication. This concept is illustrated in figure 1 below, an equation for the Internet of Things.

Figure 1 Source:(McEwen and Cassimally, 2014) [4]
1.2 History of the Internet and the internet of things
Table 1 below from (www.postscapes.com) [5] summaries the main historical dates from 1832 to 2013 and corresponding events which have contributed to the Internet and the Internet of things.
| Date | Event |
| 1832 | The Russia scientist Baron Dchilling invented the Electromagnetic telegraph. Also in 1833 a code was invented to communicate over distances up to 1.2km by Friedrich Gauss and Wilhelm Weber from Germany. |
| 1844 | The first ever Morse code message was sent from Washington to Baltimore in the USA. |
| 1926 | During an interview by Colliers magazine, Nikola Tesla suggest the then telephone systems which were very cumbersome will become obsolete in the future and that a more simplified system wireless system will be adopted along with mobile phones. |
| 1950 | The Oxford Mind Journal publishes an article by Alan Turing named “Computing Machinery and Intelligence”. In the article he discusses the possibility of teaching machinery to understand and speak English. |
| 1966 | A German pioneer in computer science, Karl Steinbuch suggests that in 20 years computers will become a normal part of all industrial products. |
| 1969 | A basic packet switching network was developed called ARPANET which stands for Advanced Research Projects Agency Network. |
| 1974 | Early TCP/IP networks were developed |
| 1984 | The DNS which stands for Domain Name System was developed |
| 1989 | The world wide web (www) is proposed by Tim Berners-Lee |
| 1990 | A toaster was developed by John Romkey which is considered the 1st Internet device. The toaster could be controlled over the Internet. |
| 1991 | Tim Berners-Lee who 1st proposed the WWW creates the first web page. |
| 1991 | An article called “The computer for the 21st Century” was written by Mark Weiser’s. In the article he suggests the best technologies that are invented are those that bed in seamlessly and are not noticed in every day life. |
| 1993 | The Trojan room coffee pot was developed in University of Cambridge by Paul Jardetzky and Quentin Stafford-Fraser. Every 3 minutes an image of the pot levels was updated and sent to the buildings server. |
| 1994 | A wear cam is developed by Steve Man |
| 1995 | Ebay and Amazon open for business – Online purchasing begins |
| 1997 | A innovative look at sensor is presented by Paul Saffo’s article called ‘Sensors:The wave of infotech Innovation’ |
| 1998 | The search engine Google starts up. |
| 1998 | 3 researchers from MIT, Scott Brave, Andrew Dahley and Hiroshi Ishii present a project called ‘intouch’ which explored new forms of communication between people through touch. |
| 1998 | Before Mark Weiser died he developed a water fountain which had the ability to mimic price and volume trends of the stock market. |
| 1999 | The Term “Internet of things” is first used by executive director of the Auto-ID Centre Kevin Ashton during a presentation to Procter and Gamble. The presentation linked the Internet and RFID technology. |
| 1999 | Neil Gershenfeld from MIT spoke about how the expansion of the world wide web and the growth of “things” using the internet in his book “When things start to think”. |
| 1999 | The Electronic Product Code (EPC) is developed by Auto-ID Labs. The EPC is a RFID identification system used globally and it was developed to replace the UPC bar code. |
| 1999 | In a business week visionary article, Neil Gross suggests that in the century that the internet will be used to connect millions of devices across the world. |
| 2000 | Plans for an Internet enabled fridge are announced by LG. |
| 2002 | The Ambient Orb which alters colour depending on the changing parameters of the Dow Jones is created and released by David Rose. |
| 2003 – 2004 | The term “Internet of things” is present in many publications such as Scientific American and the Boston Globe and it is also used in Book titles. |
| 2003 – 2004 | The US department of defensive begin to use RFID in a massive way and along with commercial companies such as Walmart. |
| 2005 | The International Telecommunications Union (ITU) produced its first ever document on the topic. In it they described IoT as a new dimension to the world of information and communication technology (ICT) due to the limitless connectivity possibilities. |
| 2005 | A rabbit which had built in Wi-Fi was developed by Rafi Haladjian and Olivier Mevel. The Rabbit had the capability to speak and notify users about stock market reports and news headlines. |
| 2006 – 2008 | The EU hold their first ever IoT conference. |
| 2008 | The IPSO Alliance which incorporates companies such as Cisco and google is formed to promote the use of Internet Protocol within networks utilising smart devices. |
| 2008 | The use of “white space” spectrum is approved by the FCC. |
| 2008 – 2009 | The Cisco Internet Business Solutions Group (IBSG) state that the “Internet of things” is born between 2008 and 2009 as more “things” were connected to the internet at this time than people.
12.5 billion devices compared to 6.8 billion people. |
| 2008 | The Internet of things is described as a disruptive civil technology by the US national intelligence council. |
| 2010 | Large investments are made in the area by China |
| 2011 | IPv6 is launch to the public. There are 2128 possible addresses available. This extension anticipates considerable future growth of the Internet. |
| 2011 | Many companies develop educational and marketing initiatives on the topic including IBM and Cisco. |
| 2011 | Arduino prototype boards are developed to enable DIY enthusiasts build their own IoT projects. |
| 2011 | IoT start-up companies like Pachube are acquired due to the expanding Iot sector. |
| 2013 | Europe continues to support IoT with initiatives such as ICT-FP7 Programme, digital future and IoT-A The Chinese continue to support the IoT sector via funding and research. Global Standards Initiative is created. Its vision is of a collective approach for development of standards which enable the Internet of Things across the globe. |
Table 1 Source: (www.postscapes.com) [5]
1.3 The continued growth of the Internet of things platform
Figure 2 illustrates the growth in popularity of the term “The Internet of Things”. The graph form (www.google.com/trends) [6] shows how the number of google searches for “Internet of things” has risen over the last 5 years. The data represents worldwide searches and is not region specific.
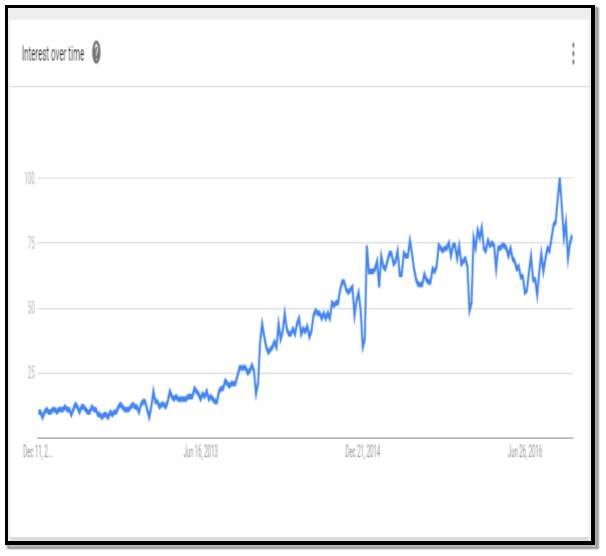
Figure 2 Source: (www.google.com/trends) [6]
According to the (International Data corporation, 2016) [3] IoT sector will grow to double in size to close to 50 billion things by 2020 which will equate to a $1.7 trillion market. In this document the IDC states that IoT market ‘continues to gain momentum as vendors and enterprises begin to embrace the opportunities this market presents’. The document goes on to state that the sector ‘will grow from $655.8 billion in 2014 to 1.7 trillion in 2020 with a compound annual growth rate of 16.9% and that devices, connectivity and IT services will make up the majority of the IoT market in 2020’. The report gives a breakdown of 31.8% of the total value represented by devices (modules/sensors) and that by 2020, it predicts that IoT sector will gain increased revenue due to its purpose-built IoT platforms and application software been delivered as a service.
The “Internet of Things” term was also added to the Gartner Hype Cycle report in 2011. (www.gartner.com) [7] Gartner use this to track the life cycles of new and emerging technologies from “technology trigger” to “plateau of productivity”. Gartner Inc. is a world leader in information technology research. They supply this technology information to clients to allow them to make informative decisions on a daily basis. The Hype Cycle itself shows technology trends which are developing. The internet of things was at the Hype Cycle’s summit of inflated expectations in 2014 which is shown in the graph in figure 3. In the graph the X axis represents expectations and Y axis represents time factors.
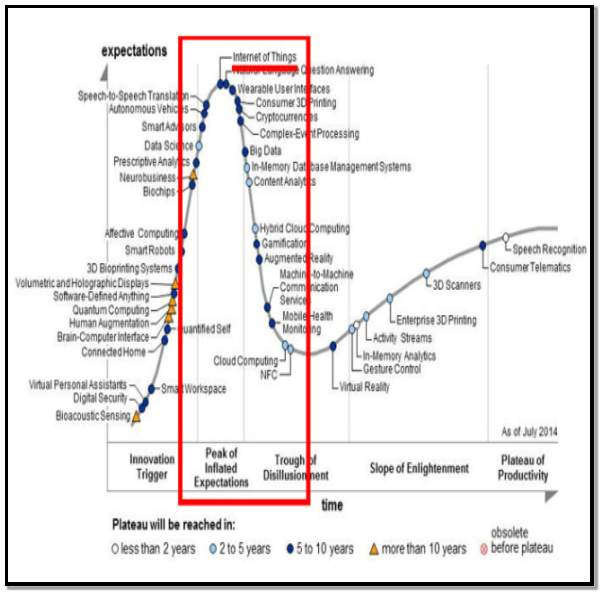
Figure 3 Source: (www.gartner.com) [7]
1.4 Internet of Things, Why now?
One of the main reasons everyday objects can now be made with internet connectivity capabilities is due to the relative low cost of microchips and associated electronics. (McEwen and Cassimally, 2014: 14) [4] In the book “Designing the Internet of Things” the authors discuss the reasoning why the right time is now to embed objects or appliances with computing power that are network enabled from a cost point of view. They suggest that when the Internet moved away from academia and the military in the 1980’s with the arrival of the first commercial internet service providers (ISPs) that the cost of a computer was approximately £1500, but today a Microchip with the equivalent power would only cost £0.50. This fast rise in processing power and the parallel decrease in cost is known as Moore’s law who was one of the founders of Intel. This term has become the bell-weather for micro processer development which says that the no. of transistors you can fit on a silicon chip will double every 18 months. They continue to say that we have reached the “sweet spot” for performance v’s price which means the cost of adding computing and network capabilities to objects has fallen to a level equivalent to choosing what type of material or finish to use on a piece of furniture. Also internet connectivity is cheaper and much more accessible, compared to the old dial up connections of the 1990’s. The authors state that in the United Kingdom up to 76% of adults have broadband subscription which provides always on connectivity to the internet and with most home network routers having Wi-Fi this removes the need for physically connecting devices via cables.
1.5 Smart Home
The concept of home automation first came around in the late 1970s. The expectation of what a home automation system should provide has also changed a great deal since the 1970’s with the huge leaps in technology. Home automation refers to the control of electrical appliances and home features such as security cameras by local networking or by remote control. Home automation systems are gaining popularity due to their numerous benefits and untapped potential.
Homes today are places of comfort and safety which enable families and people to relax after a long day of work and get a good night’s sleep. These homes have comfortable furniture, lights, and electrical appliances which help them to run efficiently and effectively. Although homes today are reasonably user friendly and do their job well, there is always room for improvement and the capacity to become more efficient and do their jobs better. The homes of the future will optimize home security, energy usage and comfort. These homes will be better, smarter, and more connected. These homes will be smart homes which will have the ability to control lighting, heating and electronic devices locally or remotely by smartphone or computer.
Research by (Moser et al, 2014) [8] [5] list the main reasons to utilize smart home technology as:
- Comfort
- Energy Saving
- Efficiency
1.6 Smart homes and the Internet of Things
The Internet of things is considered the next stage in the evolution of wireless networks and connected devices due to smaller networked and connected sensors in everyday objects. This leads to great opportunities in the area of Smart homes. A flavour of IoT in smart homes is given by (McEwen and Cassimally, 2014: 8) [4] in the book “Designing the Internet of Things”
‘In your kitchen, a blinking light reminds you it’s time to take your tablets. If you forget, the medicine bottle cap goes online and emails your doctor to let her know’.
‘Your chair might collect information about how often you sit on it and for how long, while the sewing machine reports how much thread it has left and how many stitches it has sewn’.
‘The alarm rings. As you open your eyes blearily, you see that it’s five minutes later than your usual wake-up time. The clock has checked the train times online, and your train must be delayed, so it lets you sleep in a little longer’.
In all of the above cases the internet was used to send, receive and communicate data or information and more importantly the device to complete this action was not a smart phone or a computer but a thing within the home. Therefore the concept of a smart home utilizing IoT means that instead of having one or two powerful computing devices (laptop or smart phone) in the home there will be a large amount of devices which are less powerful but have the ability to receive inputs, interpret them and send them over the internet. Also if we take the chair in the above example, the fact that it collects information like, when and for how long you sit on it must not take away or hinder it original use or function, i.e. You sit on it!
(Moser et al, 2014) [8] present the idea that a considerable issue surrounding home automation is that the majority of ‘Things’ that are employed are designed and manufactured by a diverse range of companies which leads to problems integrating these devices with each other due to conflicting protocols and standards. The authors suggest that because the vast amount of ‘Things’ have the ability to connect and communicate with the internet that the optimum way to withstand this issue of incompatibility was to connect all these devices through the internet instead of connecting them directly to each other.
Chapter 2
2.0 LITERATURE REVIEW
2.1 Internet fundamentals
2.1.1 Protocols
A protocol is a common set of rules which are used to govern the exchange of data between a transmitter and receiver of the data on a communication link. Efficient communication between devices requires the devices to agree on a common format for the data. These rules include:
- Rates of data transmission (in baud/bps)
- Both Synchronous or asynchronous transmission types
- Data that is transmitted in half or full duplex mode.
- Protocols are implemented into hardware by been built into modems.
There are several other protocols which can complement the standard protocols by adding extra functions such as error detection, data compression and file transfer functions.
2.1.2 Internet Protocol (IP)
The IP protocol (www.Cisco.com) [9] works by sending data from a device to another device via a packet. This packet contains a destination and source address and contains the information you want to send in a format known as a protocol. These packets can be sent via wireless or wired networks, for example using phone lines or a satellite link.
It is known as the principle communication protocol when exchanging data between 2 electronic devices across a network. It uses the Internet protocol suite which is known as TCP/IP. The Internet Protocol suite has 4 different layers:
- Application Layer
- Transport Layer
- Internet Layer
- Link Layer
The job of the IP layer is the reliable delivery of packets to another host. This is done by adding a source and destination address to the packets during the encapsulation process.
2.1.3 User Datagram Protocol (UDP)
UDP (www.Cisco.com) [9] is a transport layer protocol. It manages communication for multiple applications. It is a very simple protocol; it provides only basic transport layer capabilities and is a connectionless protocol. It sends data as “best effort” with no guarantee of delivery and lost datagrams are not resent. It has faster rates compared to TCP. For these reasons it is suited to applications like video steaming and VoIP as the need for reliability is not important.
2.1.4 Transmission Control protocol (TCP)
TCP (www.Cisco.com) [9] is built around the IP protocol but it has extra features such as sequence numbers, acknowledgements and the capability to retransmit packets if required. This means that messages which are sent using TCP are bigger but they have the extra assurance that they will be delivered to the sender in one piece. It is a connection oriented protocol (3 way handshake) and used for applications such as Web browser (HTTP), E-mail (SMTP) and file transfer (FTP).
2.1.5 TCP and IP combination
As the combination of TCP and IP complement each other, multiple services are built around them, E.g. Email and HTTP protocol which are used to transmit information on the World Wide Web. (www.Cisco.com) [9] TCP is a connection orientated protocol as it establishes a connection via a three way handshake with the users before data transfer seen below in figure 4. This connection provides reliable, in order delivery of packets which are suitable for file transfer or Email. TCP breaks the data into components that the IP protocol can manage. IP protocol transmits the data across the network, it takes the data that TCP protocol has broken into components and sends it across the network. IP protocol on its own does not guarantee delivery or correct order delivery. TCP h.as error checking capabilities and data will not be delivered unless it passes error checks and any lost packets are re transmitted. IP uses protocol numbers to identify transport protocols and TCP uses port numbers to identify a particular host application.
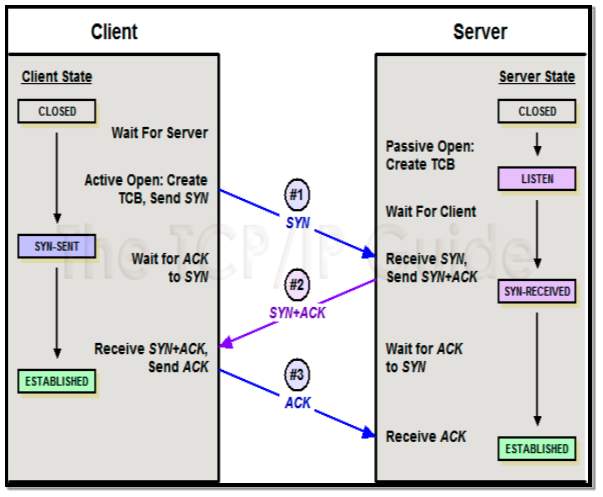
Figure 4 Source: TCP/IP Guide [10]
2.1.6 The Protocol Suite (TCP/IP)
The TCP/IP suite is known as a stack of protocols which are layered on one another, with each layer building on and complementing the previous layer. Figure 5 below illustrates the TCP/IP protocol suite. The function of each layer is as follows:
- Application Layer: Represents the data to the user and provides encoding and dialog control. It contains protocols that can get Web pages (HTTP) and send emails (SMTP).
- Transport Layer: Supports communication between various devices across a diverse network. It has the TCP and UDP protocol in this layer. Depending on the needs of the application been used the transport layer will use either TCP or UDP.
- Internet Layer: Determines the best path through the network and employs methods and structures for putting address information within datagrams.
- Network Layer: Controls the hardware devices and media on the network. It manages the exchange of bits across a network between 2 hosts. The link can be in many forms such as wired Ethernet, Wi-Fi, telephone network or by standards used in Personal Area Networks (PAN) such as IEEE 802.15.4.
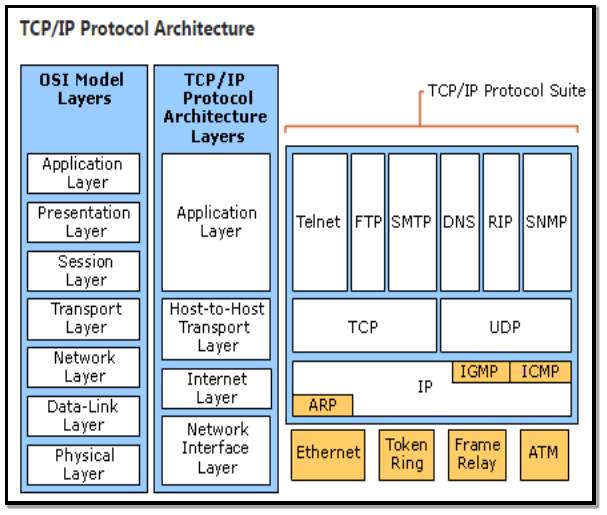
Figure 5 Source: (Microsoft Technet) [11]
2.1.7 Open Systems Interconnection (OSI) model
Figure 5 above shows the OSI model layers, The OSI Model is the International Standards Organization (ISO) model which incorporates the following attributes. It is designed to establish data-communications standards that promote multivendor interoperability. The model is a conceptual one which is used to standardisation and characterisation of the functions of communication between electronic devices. Its main goal is to have a common set of standard protocols across the varied methods of communication. It separates the communication process between 2 hosts into distinct layers. There are 7 layers in total with each layer complementing the layers above and below it. The layers are as follows:
- Application Layer: Provides multiple network processes and also services to different applications. It will identify and establish if communication partners are available and it also synchronizes applications (programs) that are communicating between two hosts.
- Presentation Layer: It ensures that data is readable by the destination. It is responsible for data representation, data encryption and decryption. It also is used for file compression and file decompression.
- Session Layer: It starts and ends sessions between 2 hosts and manages sessions between 2 hosts. It logically keeps communication sessions separate.
- Transport Layer: responsible for the reliable data transport between 2 end nodes. It establishes, maintains and ends virtual circuits (a logical connection between 2 hosts). It uses windowing, sequencing and flow control to provide reliable delivery of data. It divides data into chunks called segments and it defines all known services using port numbers.
- Network Layer: It is responsible for network addressing and selecting the optimum path through a network. The optimum path selection describes the process a router uses to select the best path across a network to a destination host. It packages data into packets and provides IP addressing (logical addressing). A router is considered a layer 3 device.
- Data link Layer: It is responsible for how computers access the physical media and provides physical addressing (MAC addressing), network topology and error notification. It also provides flow control, media access. The data link layer formats data into frames. Bridges and switches are used at this layer.
The data link layer links together the software and hardware layer
- Logical link control – It frames the network layer packets and then selects the network layer protocol to be used.
- Media access control – It addresses the frame and then adds the beginning and end of the frame.
- Physical Layer: This layer provides access to the physical media and converts the frames/packets into binary electrical signals. It sends and receives data over the network media. Physical media such as cables, connectors, repeaters and hubs are used on this layer.
2.1.8 Encapsulation and De-capsulation Process
Application data, e.g. an Email, is sent down the protocol layers on its way to be transmitted over the network to a destination host. At each layer protocols add various information.
Application dats is assembled at the application layer and passed down through the presentation and session layers as a data stream. At the transport layer the stream of data is divided into segments. Information to get the data reliably to its destination is added in the form of a transport header. In the network layer a header is added to each segment and it becomes a packet. The header contains information like the IP address of the source and destination hosts. In the data link layer a header frame and trailer frame are added to the packet and it becomes a frame and in the physical layer the packet is converted into binary electrical signals and is then transmitted in binary format 1’s and 0’s. The de-capsulation process works in reverse order when a host receives the data. Figure 6 below illustrates the process as it passes through the OSI layers.
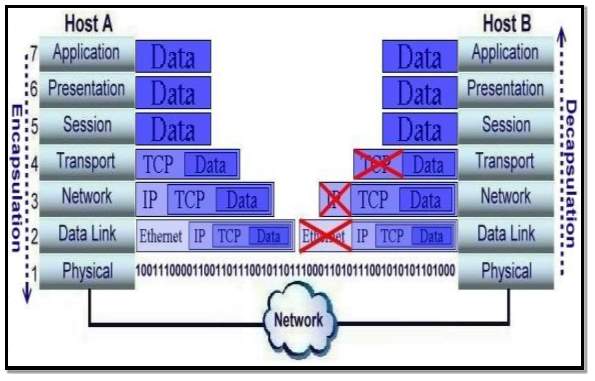
Figure 6 Source: (Networking layer-x) [12]
2.1.9 What is an IP Address?
IPv4
The Internet Protocol knows the IP address of the source and destination devices when data is been sent. An IP address is a set of binary numbers which uniquely identifies networked devices to enable them to send and receive data to each other on a TCP/IP network. There are 232 = 4,294,967,296 possible addresses available. An IP address is written as a four 8 bit numbers which are separated by dots (0.0.0.0 to 255.255.255.255) which are more readable by humans. Every networked connected device will have its own IP address. IP addresses are managed by service providers and a central allocation system.
IPv6
IPv6 uses 128-bit addresses which are displayed as eight groups of 4 hexadecimal digits (0000.0000.0000.0000.0000.0000.0000.0000 – FFFF.FFFF.FFFF.FFFF.FFFF.FFFF.FFFF.FFFF). There are 2128 = 340282366920938463463374607431768211456 possible addresses available. This extension anticipates considerable future growth within the Internet with the arrival of the Internet of things revolution and provides breading space for what is perceived as an insufficient of amount of network addresses.
2.1.10 Types of IP Address
There are private IP addresses, public IP addresses and also static IP addresses, and dynamic IP addresses.
Static IP Address:
- Is permanently given to your device by an internet service provider (ISP).
- Static IP addresses are usually assigned to servers hosting websites and providing services such as Email.
- A static IP address can also be assigned to public organizations which require the same IP address every time.
- Devices using static IP addresses will have to be manually configured.
- ISPs generally charge additional fee for static IP addresses.
Dynamic IP address:
- The address is dynamically given to your device by an ISP.
- Each time a connection is made to the network by a device the ISP will give a different IP address using Dynamic Host Configuration Protocol (DHCP) protocol.
- When a device joins or leaves an IP-based network, DHCP will automatically renew or release an IP address.
Private and Public addresses:
Public Address:
- This is an address which is assigned to a networked device so it has direct access over the Internet.
- Candidates for a public address would be servers used for email and the web.
- It is a unique address which is only assigned to a single device.
Private Address:
- These addresses are assigned to organisations so they can create private networks within their organisations.
- Three IP blocks exist for private use, These are as follows:
- Class A is used for large companies or governments.
- Class B is used for medium sized companies.
- Class C is used for all other devices.
- Electronic devices within your home network and PC’s within companies would be assigned a private IP address.
- To ensure that only a home owner could access a networked printer within the home a private IP address would be assigned to it to prevent an external source gaining access to it. If an external source wanted to gain access to the printer it would have to communicate via the home routers public IP address.
Figure 7 below illustrates the ranges of public and private IP addresses
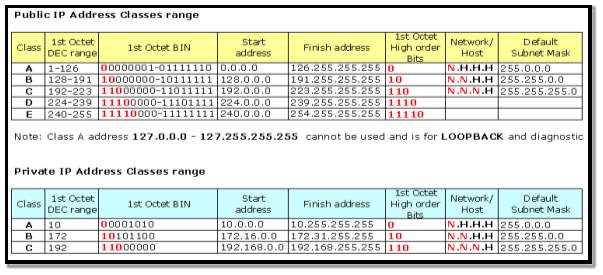
Figure 7 Source:(IC-IMS) [13]
2.1.11 Domain Name System (DNS)
The DNS helps to make the internet user friendly and easier to navigate. We are all familiar with DNS names such as:
- rte.ie
- google.com
- bbc.co.uk
(McEwen and Cassimally, 2014: 47) [4] Discuss how the domain name will have a top level domain like .ie, .com or .co.uk. This top level domain will know how to find details regarding the domain. E.g. .ie will know where to locate rte.ie. This gives the domains the information required so that they know where to direct calls to individual machines and services. For example, the DNS records for .google.com will know where to locate the following:
- www.google.com
- mail.google.com
- calendar.google.com
2.1.12 Media Access Control (MAC) Address
All network connected devices also need to have a MAC address. A MAC address is used to differentiate between devices on a common physical network to allow them to send and receive packets to each other. The address is uniquely assigned to network devices to enable then to communicate at the data link layer. A MAC address is used as a network address for the vast majority of IEEE 802 network technologies, such as Ethernet and Wi-Fi. The MAC address itself is a 48 bit number and it is written as 6 groups of 2 hexadecimal digits which are separated by colons. E.g. 03:AE:23:83:BC:FF
2.1.13 TCP and UDP ports
When a message is sent over the internet using TCP/IP it is essential you send it to the correct port. Port numbers range from 0 – 65535.
- 0 – 1023 are well known ports which are reserved for services like HTTP (80) and SMTP (25).
- 1024 – 49151 are registered ports which are given to user processes or applications.
- 49151 – 65536 – are dynamic or private ports which are assigned to client applications when starting a connection.
(McEwen and Cassimally, 2014; 53) [4] Use the following example to explain the importance of port numbers. When HTTP page is requested by a browser, it will generally use port 80. The web server replies to the request as it is ‘listening’ to that specific port. But if a HTTP page is requested by the browser to a different port, the following will occur.
1) A RST packet will be sent back in reply as nothing is listening to the port. This will reset the TCP/IP connection.
2) The firewall allows the request to hang for a period of time instead of sending a reply. This method is to prevent online external attacks from requiring information about the device or computer.
2.1.14 Application Layer Protocols
Source and destination devices use application layer protocols to facilitate the sending of data to the programs running on each device.Application Layer protocols govern the following tasks:
- Message type (sending or receiving).
- Message type syntax style.
- Field information and meaning.
- Rules for governing the sending and receiving of messages.
The below table gives an explanation of some of the more commonly used application layer protocols including the port number and explanation of the function of each from (www.techopedia.com) [14].
| Protocol | Port Number | Function |
| HTTP (Hypertext Transfer Protocol):
|
80 |
|
| SMTP (Simple Mail Transfer Protocol) | 25 |
|
| TELNET (Terminal Network) | 23 |
|
| FTP (File Transfer Protocol) | 21 |
|
Table 2 Source: (www.techopedia.com) [14]
- IoT Architecture Layers
One issue with IoT revolution is that it is that there is no standard architecture been used. Factors like scalability, interoperability, reliability, Quality of Service need to be addressed to enable IoT. Since IoT will connect everything and everyone, the data flow and storage capacity within a network will also have to expand to meet this demand. So it is important to facilitate the future growth of IoT that progress in technology and innovative network architecture models are designed. (European IoT research group) [1] In their paper they discuss that an open architecture is required by devices in the internet of things sector. This is required to augment interaction between diverse systems and resources which are spread across a wide and varied range of platforms from human beings to smart devices. Architecture standards should have data models, interfaces and protocols which are well defined and abstract as well as working well with more common services such as web services to be able to support the biggest range of operating systems and programming languages. A summary of the vital aspects of IoT architecture is as follows:
- The architecture needs to be distributed and open with end to end capabilities.
- The capability to interact with diverse systems and error recovery is important.
- Architectures should be decentralised.
- Cloud computing technology, event-driven architectures, disconnected operations and synchronization.
- Use of market mechanisms for increased competition and
participation.
(European FP7 research project IoT-A, 2013) [15] Developed the Architectural Reference Model (ARM) for the Internet of things. The IoT-A project achieved the following:
- It developed a reference model to be used as a guide for IoT architecture encompassing the interoperability of the varied range of platforms and it gives guiding principles when protocols, interfaces and algorithms are been designed.
- Apparatus for the structured amalgamation into the services layer.
- Innovative infrastructure which is resolute and scalable.
- Innovative platform items.
- The developed architecture most be implemented in tangible cases.
Figure 8 illustrates the ARM architecture concept graphically.
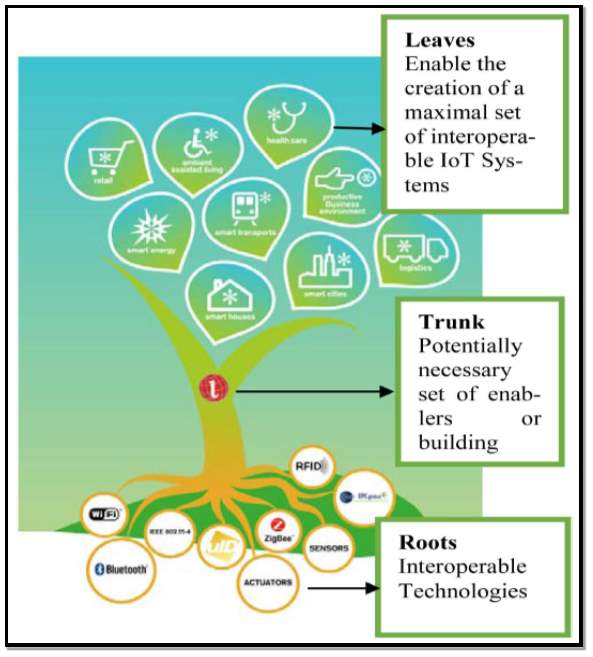
Figure 8 Source: (European FP7 research project IoT-A, 2013) [15]
(Fawzi Behmann & Kwok Wu, 2015) [16] Proposed the following IoT architecture model in their book Collaborative Internet of Things. This is illustrated below in graphical form in figure 9. The graph depicts 3 layers, Sensing Layer, Gateway/Aggregation Layer and the Service Layer. A description of each layer is outlined below:
Sensing Layer: The service layer is used to integrate devices or objects that are normally passive. When these passive objects are consolidated into the service layer they can then produce data and information that can be utilized by different sectors be it business or on an individual basis.
Gateway/Aggregation Layer: This layer is used to facilitate data stream movement between the different levels of architecture.
Service Layer: The service layer gives the data which has been gathered from the layers the vision and insight required to translate it into useable services for business and individuals alike.
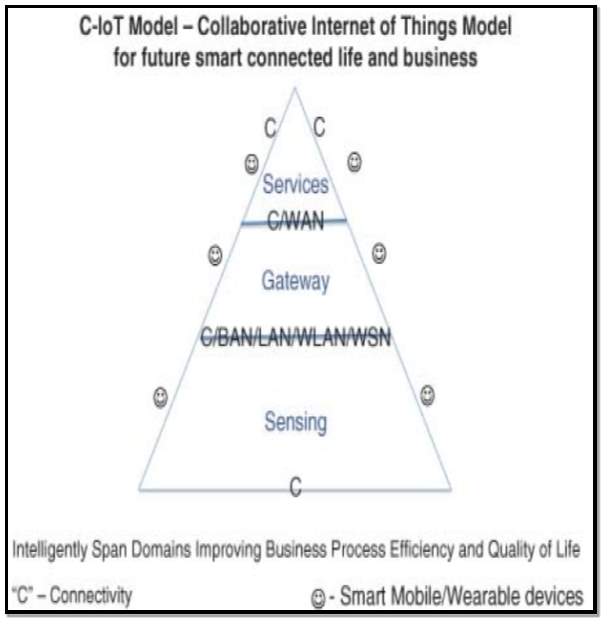
Figure 9 Source: (Fawzi Behmann & Kwok Wu, 2015) [16]
(Khan et al, 2012) [17] Proposes a five layer IoT architecture structure as shown in Figure 10 below. These layers are described briefly below:
Perception Layer: (Device Layer) this layer contains of the physical things and sensor devices. The collected information for this layer is then forwarded to the Network layer where it is securely transmitted to a data processing scheme.
Network Layer: (Transmission Layer) Information is transferred securely in this layer. Various transmission mediums can be used including wired or wireless and technology such as Wi-Fi or ZigBee. Information in the network layer is received from the perception layer and then transferred to the middleware layer.
Middleware Layer: this layer is owns service management aspects and is linked to the database. It gets the data from the Network layer and then stores the data in the database. Ubiquitous computation and data processing tasks are completed within this layer and depending on the results informative decisions are completed.
Application Layer: depending on the type of information processed and received from the middleware layer the application layer will manage the data uniquely. Applications used by IoT can be smart home, smart health, etc.
Business Layer: The overall IoT system is managed within this layer. Depending on the information received from the application layer it can produce models, graphs, etc. of the data. This data can then be used to complete strategic business decisions in the future.
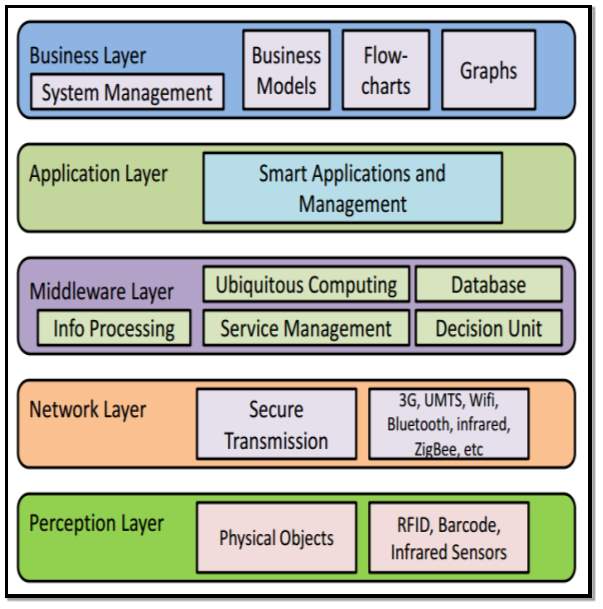
Figure 10 Source: (Khan et al, 2012)[17]
Further IoT architectures have been proposed including (M. C. Domingo, 2012) [18] and (X. Jia et al, 2012) [19] who based their design to cater for the requirements of particular technologies. They proposed to segment the IoT architecture into three distinct layers:
- The perception layer
- The network layer
- The service layer also known as the application layer.
(L. Atzori et al, 2010) [20] also developed an IoT architecture which had 3 layers, these were:
- The application layer
- The network layer
- The sensing layer.
(Wu He and Shancang Li, 2014) [21] Put forward the idea of a 4 layer approach to IoT architecture shown in figure 11 and table 3 below. Also table 4 shows the design considerations required when selecting IoT architecture.
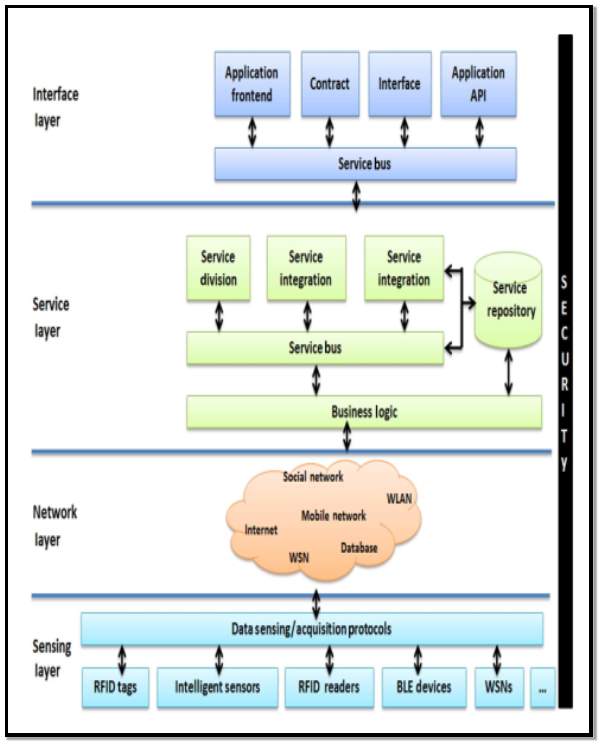
Figure 11 Source: (Wu He and Shancang Li, 2014)[21]
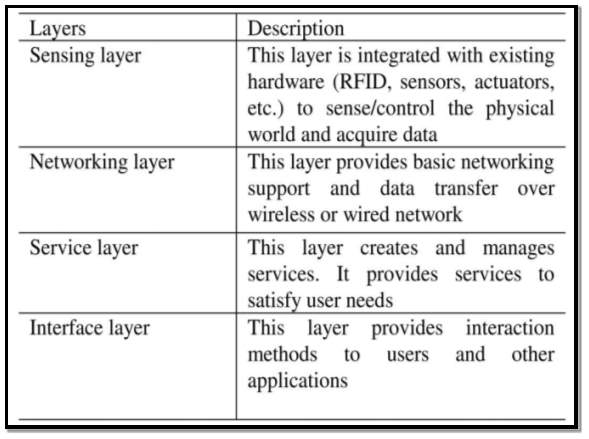
Table 3 Source: (Wu He and Shancang Li, 2014)[21]
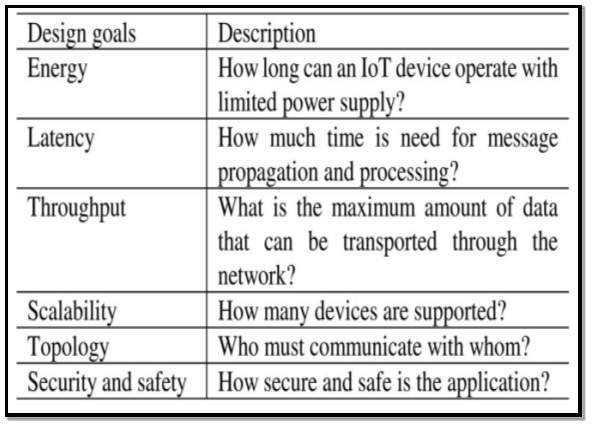
Table 4 Source: (Wu He and Shancang Li, 2014)[21]
Further research by (Wu He and Shancang Li, 2014) [21] discuss that the most important aspects of architectural design in the IoT environment and that it should be interested with the following elements:
- Efficient networking and communication capabilities.
- Enabling smart objects.
- Web services and applications
- Business models and corresponding processes.
- Cooperative data processing
- Security
Also the important elements to be considered from a technology point of view are:
- Network scalability
- Network modularity
- Interoperability between diverse systems
- An adaptive and dynamic architecture is required to support moving objects
- IoT Smart Home Architecture Layers
(Chong et al, 2011) [22], (Bing et al, 2011) [23] and (Pranay P. Gaikad et al, 2015) [24] all propose a layered architecture approach specifically for smart homes based on the Internet of things. This is illustrated in figure 12 below and includes the following layer:
Perception Layer: The perception layer is at the lowest level. Both physical and logical sensors are used to ensure that household things or devices can accomplish accurate real-time monitoring within the smart home. Sensors can include:
- Environmental monitoring sensor such as temperature and humidity sensors
- household devices control such as remote lighting
- security cameras
- GPS
The information gathering and handling technology that the authors use at the perception layer is Zigbee, this is a wireless sensing technology. A mesh network is also employed.
Home Gateway: This layer is used to connect the perception layer and the network layer. Information is collected at the perception layer and passed to the network layer.
Network Layer: This layer consists of multiple types of wired and wireless communication networks including:
- WLAN (Wireless Local Area Network)
- Mobile cellular network
- Internet
The information collected at the perception layer is processed and transmitted at the network layer.
Application Layer: It acts as the interface between the users and the smart home. It has elements that support application platforms. The connections between the layers require devices with varied functions to facilitate applications that are complex and intelligent.
Application Support Platform: The application support platform gives some typical supports for a smart home application. To enable access to applications and to employ network resources and capabilities it implements open interfaces to them.
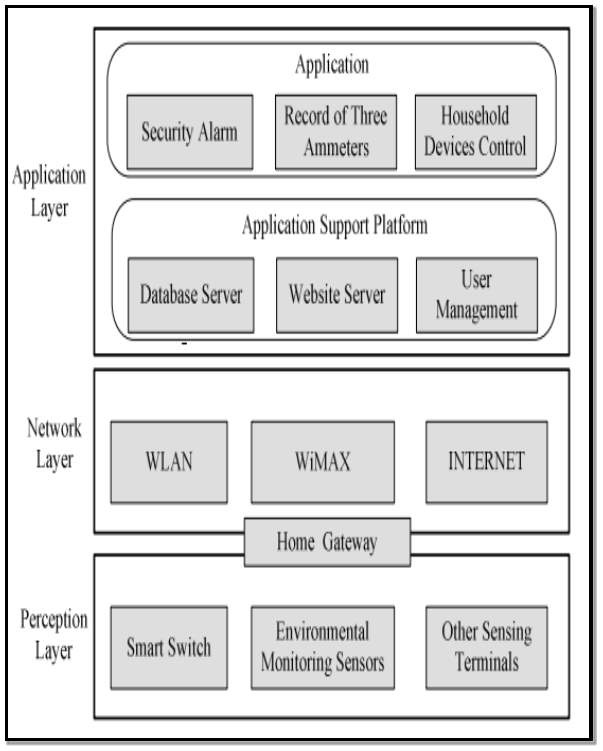
Figure 12 Source: (Chong et al, 2011) [22]
2.4 Internet of things Enabling Technologies
2.4.1 Radio Frequency Identification (RFID)
RFID is known as an identification and tracking technology. It is one of the foundational technologies for IoT, it works by enabling microchips to send the identification information to a reader via wireless communication. Objects which have a RFID tag attached can be tracked, monitored and identified. This technology is also relatively in-expensive so it has an important part to play in the future of IoT.
Research by (Divyan M. Konidala et al, 2011) [25] in the smart home environment discusses how RFID technology could be used to track items in a refrigerator. The fridge would be enabled with a RFID reader and as each item is placed in the fridge it is scanned by the reader. The contents of the fridge can then be displayed on a screen with information like food type, food ingredients and the items expiry date. This information can then be used by the home owner to decide what items are required from the supermarket. Further research to this application of RFID technology could lead to the fridge automatically adding items that are used to a shopping list or ordering the items for the supermarket.
(S. Kim et al, 2013) [26] completed research on RFID technology and examined how it could be used within the living environment; they proposed a universal healthcare system which was called U-healthcare. RFID technology was used to precisely locate and also monitor in real-time the location of elderly people. The information which was collected was used to ascertain the elderly person’s movements and activity patterns; this data was then used as a guide to determine the person’s overall health. The authors also state that RFID technology can now be incorporated into wireless sensor networks; this improves its ability of track moving objects.
2.4.2 Wi-Fi
Wi-Fi is a wireless networking technology which uses radio frequencies (RF) to give high speed internet and network connection without the need for physical wires or cables. It works by using this RF technology to transmit information across a network to other devices. Wi-Fi is based on the IEEE 802.11 standards and it uses the 2.4 GHz Ultra High Frequency and 5 GHz Super High Frequency ISM radio bands. Electronic devices like personal computers, video-game consoles, smartphones, digital cameras, audio players and printers connected to a network all have the ability of using Wi-Fi technology. These devices are connected to the Internet via wireless access points which have a range of approximately 20 meters. To protect the wireless network from potential hackers, Wi-Fi has adopted various encryption technologies including:
- Wired Equivalent Privacy (WEP)
- Wi-Fi Protected Access (WPA, WPA2)
- Wi-Fi Protected Setup (WPS).
WPS is the most widely used encryption method today. Wi-Fi can be used for data intensive communication such as streaming media content, and to connect the smart mobile phone to a television or gaming console etc. Although it provides good connectivity, it has access to the appliances which is limited to the range of the wireless signal in the house.
Research by (Serbulent Tozlu et al, 2012) [27] states that the vision of future Internet of Things requires connectivity not only to home appliances and consumer electronics, but also to small devices that are powered by batteries which can’t be recharged. Devices like sensors or actuators within the smart home will need function over a long period on the original battery supply. In their research they illustrate a smart home using the IEEE 802.11 standard wireless technologies for connectivity and readily available microchips; they validate the usefulness of low-power Wi-Fi technology to enable IP connectivity of battery powered devices within the smart home environment. This concept is shown in figure 13.
(Prof. R.S. Suryavanshi et al) [28] Completed further research on this topic and designed a project with the goal of saving energy by using Wi-Fi technology as a link between a smart phone using Android and a variety of sensors including relays to control lighting.
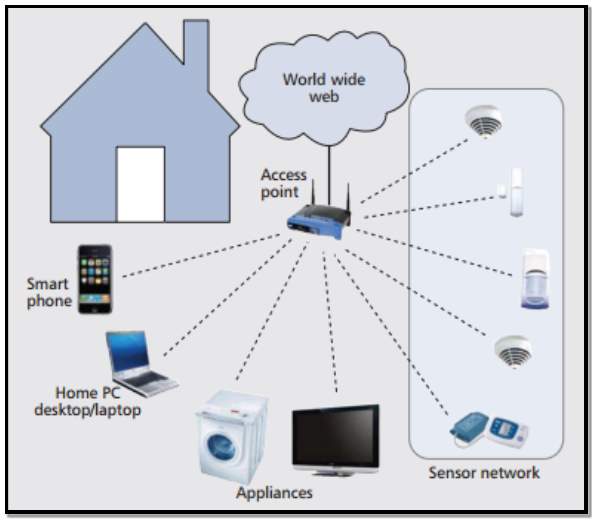
Figure 13 Source: (Serbulent Tozlu et al, 2012) [27]
2.4.3 Bluetooth
Bluetooth is another wireless technology. It employs Ultra High Frequency radio waves which are in the Industrial Scientific Medical band and operate within the 2.4 to 2.485 GHz frequency range. It is a short distance range, typically approximately 10 metres and has slower data rates compared to Wi-Fi. It is used to connect wired devices, mobile devices and personal area networks (PANs). Bluetooth is managed and controlled by the Bluetooth Special Interest Group (SIG).
(Sriskanthan and Karand, 2002) [29] Presented an application of Bluetooth Technology in the Home Automation environment. Bluetooth was utilized for achieving a wireless home
automation system. Multiple home appliances including air conditioners, temperature sensors and a mobile phone are connected together via Bluetooth wireless technology. They were successful in creating a viable Bluetooth Personal Area Network in Home Environment which is used to monitor the temperature within the home and also to remotely control the air conditioning system. They use a Bluetooth module to manage the communication between the various client modules and the host module. To improve the quality of communication between the host and client modules a home automation was developed. The protocol maintained the efficient exchange of data and it allows the network to add/remove devices, this gave the system the ability to easily grow if required. This system also was relatively inexpensive compared to a wired system as it eliminated the need for physical wires to connect sensors and devices.
(Pawar et al, 2016) [30] Proposed a low cost and user friendly smart home system which uses Bluetooth to connect a smart phone or PC wirelessly to a control board controlling humidity/Temperature sensors as well as home appliance. They suggest that the system enhances traditional home automation systems as it improves the ability of the user to monitor and control sensors and devices in the home.
(Abd El-Latif Mowad et al, 2014) [31] Discuss the main fields for a smart home system and classify these as:
- Home automation – appliance control
- Remote monitoring
- Environmental monitoring – humidity, temperature, fault tracking and management
- Health monitoring
Their system is designed around the Microcontroller MIKRO C software, various passive and active sensors. Bluetooth is used for the communication between a smart phone and controller module. The Bluetooth module receives information serially in RS232 format from the controller and then transmits it to a wireless network. The smart home system was supported by remote access control system and the wireless Bluetooth technique is used to monitor and control appliances.
Research by (Kumar Mandula et al, 2015) [32] proposed a smart home automation system which was supported by a Arduino micro-controller and an Android mobile app on a smart phone. The communication between the Arduino and smart phone was enabled by a Bluetooth wireless connection. In this case a Arduino Mega coupled with a Bluetooth shield was utilized. Once the appliances were connected to Arduino board, they were controlled using any Bluetooth enabled smart phone inside a smart home. The smart home architecture is illustrated in figure 13.
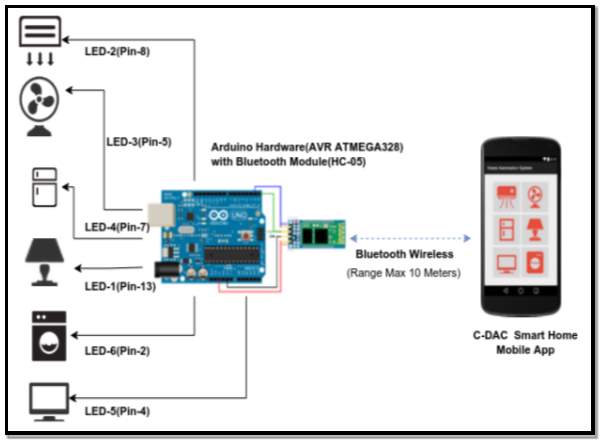
Figure 14 Source:(Kumar Mandula et al, 2015) [32]
2.4.4 ZigBee
ZigBee is a wireless technology which was designed with an open global standard to cater for the particular demands of inexpensive, low-power wireless machine to machine networks. The ZigBee standard functions on the IEEE 802.15.4 physical radio spec and it runs in unlicensed bands which include 2.4 GHz, 900 MHz and 868 MHz frequency ranges. This spec is a packet-based radio protocol intended for inexpensive and battery powered devices.
Various network configurations can be used with this protocol and it enables extended battery life on sensors. A big advantage of Zigbee is its ability to support mesh networks which facilitates numerous path ways and the interconnection between network nodes. These changing connections (devices joining and leaving the network) can be efficiently controlled by means of a mesh routing table. Mesh Networks have no central control node, each node has the ability to connect and disconnect to the network, when nodes disconnect the network the mesh configuration enables the remaining nodes to alter their routing paths in line with the current network layout which provides cohesion to the overall network.
Research by (Kelly et al, 2013) [33] proposed a method of providing an inexpensive and manageable system solution for incorporating Internet of things with a home monitoring system. They suggest that the remote monitoring and controlling of household devices via the Internet can be controlled by using ZigBee communication protocols along with specific network topologies. They state that the advantages of their system are that it has increased control of routing of packets (security and customization) and also that the network can operate within a dynamic environment. They reported a 97% accuracy of the data from temperature, humidity and light sensors which was transmitted and collected during the experiment.
(Chong et al, 2011) [22] and (Bing et al, 2011) [23] proposed a system which implements 3G and ZIGBEE to surmount the drawbacks of the then present smart home systems. The ZigBee module was used to enable wireless communication of devices within the home network. These included a microprocessor controller and home monitoring sensors and security equipment. The system operated within the ZIGBEE protocol via a XBEE- PRO ZigBee radio frequency module. The module required little power to operate and provided reliable delivery of data across the network.
2.4.5 Z-wave
This is another wireless technology which enables smart devices to communicate to one another. Elements of a home can be enhanced to become smart devices with Z-wave technology incorporated into them. These can include thermostats for heating systems, home lighting and security locks on external doors. Z-wave technology adds network connectivity and enables devices like these to communicate with each other and the outside world via the internet. Devices also can be controlled or monitored remotely via smart phones or smart device over the internet. Z-wave technology has low energy consumption rates and it operates extremely efficiently. The majority of devices within a network which is utilizing Z-wave operate on batteries for power. Some devices which control AC appliances or lighting are connected directly to the mains via a plug outlet. These devices are used to make the home more efficient and to decrease the overall energy consumption. Z-Wave radio operates within the 900 MHz Industrial Scientific Medical bands. Transmission rates of between 9.6 and 40 kb/s can be achieved. The latest Z-Wave 400 series single chip within the 2.4 GHz band can achieve transmission rates of 200 kb/s.
(Bani Yassein et al, 2016) [34] Research discusses how Z-wave is implemented in a home area network (HAN) within a smart home. Devices are monitored and controlled remotely using the Z-Wave wireless protocol. The authors state that this wireless protocol has many advantages over other protocols such as ZigBee wireless protocol as it gives enhanced reliability, low radio rebirth, easy to implement and operate and easy Interoperability. Z-Wave includes four main layers: MAC layer, Transport layer, Application layer and Routing layer. They discuss how Z-wave technology can be implemented in security applications within the home such as remote door locking and lights.
Research by (Wei et al, 2015) [35] expand on the concept of using Z-wave as a wireless transmission technology to design and implement a smart electronic locking system due to its low power consumption that it can provide longer battery life of devices. The system architecture is illustrated in figure 15.
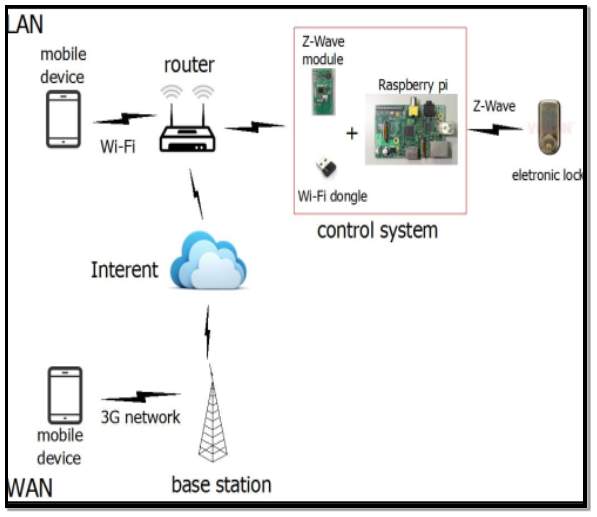
Figure 15 Source: (Wei et al, 2015) [35]
2.4.6 Connectivity Challenges in IoT-Smart Home
(Tripathi et al, 2014) [36] and (Agrawal and Lal Das, 2013) [37]set out the key challenges with the IoT smart home environment as communications standardization, device identification, Privacy, Access control/Authentication, Security, Application integration, data Storage and network Self organization.
(Samuel, 2016) [38] Research highlights connectivity challenges due to the different protocols and multiple companies with different standards and technologies within the smart home market. The following is a list of the network and device smart home key challenges from his research Interoperability, Self-Management, Maintainability, Signalling reliability, Bandwidth and Power consumption.
2.4.7 Application Programming Interfaces (API’s)
API’s are best described as a group of rules that control how one software application speaks or communicates to another software application. The following in table 5 is a list of just some of the API’s which are used in smart home applications.
| API | Description |
| Nest API | Nest is a smart heating control system used in homes. It can adjust the temperature automatically by learning the habits of the people in the home. The Nest API enables users to control the range of Nest function. Other developers can also use the API to incorporate Nest into their own applications. |
| Google Chromecast API | Chromecast is used to display TV programs on media platforms such as TV’s on laptops. The API is used to interact between the sender and receiver of the programs been transmitted. |
| Amazon Alexa Smart Home API | This is a smart home system which allows users to control devices in the home via speech recognition. The API is used to interpret user’s commands and translating them into usable functions within the smart home. |
Table 5 Source: (https://www.programmableweb.com/api/) [39]
Temboo
(www.Temboo.com) [40] Temboo is a company which allows developer’s access to over 100 API’s and over 2000 choreographies. These enable programmers to connect with online services like Dropbox, Amazon and Twitter. It has a partnership with Arduino which allows users to complete their prototypes more efficiently.
IFTTT
(www.IFTTT.com) [41] IFTTT stands for “If This Then That”. It is an internet orientated company that enables the end user to generate actions or notifications which are dependent on changes in over 160 internet cloud based services such as Dropbox or Gmail. It uses Applets to setup and control these actions or notifications. For example when a new picture is uploaded to Dropbox, an Applet can be created and programmed to send an email to a particular Gmail account.
Python
(www.python.com) [42] Python is a programming language which enables faster programming and allows the effective integration of multiple systems. Research by (Rao and Uma 2015) [43] presented an inexpensive and adaptable system for controlling, monitoring and accessing devices remotely within a home. They use a Python program as it is a simple and instinctual programming language as the interface between the devices been controlled and a Raspberry pi microcontroller to manage the various user interface controls. To do this they programme the client and the server application using Python. (Koenka et al, 2014) [44] Present Instrumentino which is an open source GUI that is used to interface with the outputs of an Arduino system for interactive control. They use Python to eliminate complex Arduino programming. The Python program communicates with the Arduino microcontroller via a sketch called controlino.
2.5 Smart Home Energy management Systems
Research by (Moser, Harder and Koo, 2014) [8] suggests that one of the main reasons for automating homes and making them smart is to help conserve natural resources such as water and to reduce the usage of fossil fuels been burned to provide energy. Water and home heating energy is wasted unnecessarily due to lack of awareness by home owners and the poor monitoring and inefficient systems been utilized for home heating and ventilation. They gave an example of how a smart home can be equipped with an adaptive lighting and heating system to sense if people are present in the house, it turns lights off when not thing is detected. The system has the ability learn the occupant’s daily movements and only turns on heating accordingly. It has also the ability to monitor the homes water and electricity usage to increase the home owner’s awareness.
(Al-Sumaiti et al, 2014)[45] Present the idea of a Smart Home Energy Management System (SHEMS) which can use energy from the grid and also from renewable sources such as PV solar panels on the house. This system allows the home occupiers and the utility company supplying the home to monitor, control and preserve energy. The SHEMS can transform home appliances into ‘smart devices’ and incorporates them into a networked system which can determine when each device is been used and home much energy it is using. These devices can also be controlled remotely via the internet. The SHEMS has the following elements:
- Central Unit: Equipped with a GUI to adjust sensors/actuators in individual rooms to control energy usage.
- Monitoring Unit: Sensors measure and monitor items like temperature and movement.
- Control Unit: Controls the system and allows the home owner’s to reduce electricity bills and CO2 emissions.
- Communication unit: Communicates with the grid.
The authors state that the SHEMS Goals are as follows:
| Stake Holder | Goal |
| Customer | Reduction in Electricity bills |
| Utility provider | Reduction in the required load Peak |
| Environment | Reduction in greenhouse gas emissions by reducing the quantity of fossil fuels which are burned and encouraging alternative green methods of electricity generation. |
| EMS devices | Optimized and efficient power consumption of smart devices |
Table 6 Source: (Al-Sumaiti et al, 2014) [45]
2.6 Security and Access control
One of the biggest challenges to achieving universal smart homes is security. Homes are progressively becoming automated and controlled via the internet. Devices such as smart TV’s and SMEMS can be vulnerable to cyberattacks.
Research by (Jacobsson et al 2014) [46] performed an extensive review of security within a smart home. They present a Smart Home Automation system Architecture shown in figure 16 and then perform a security risk analysis on it. In the system sensors and actuators measure and present data such as CO2 levels and indoor temperature in degrees Celsius. The devices operated independent from one another and run as part of a mesh network employing Zigbee to communicate. The home gateway operates using Liniux and can transfer data remotely to cloud storage via a cloud server. Data from the sensors is only uploaded to cloud storage if their values drift from pre-set thresholds. Applications use an API access point to connect with the various sensors within the smart home. Security features like a cloud server firewall and a one level authentication with the mobile app are utilized. The 6 elements of the SHAS that were scrutinized are:
1. Connected sensors/devices (S).
2. In-house gateway (GW).
3. Cloud server (CS).
4. API (API).
5. Mobile device (MD).
6. Smartphone apps (App).
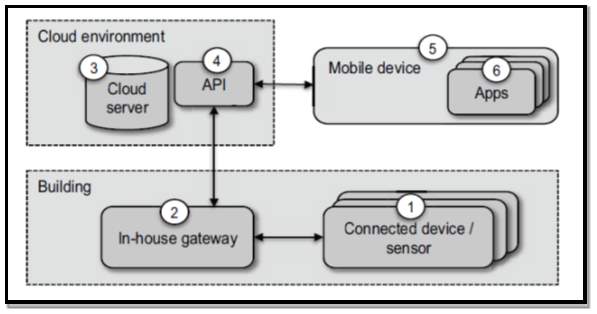
Figure 16 Source: (Jacobsson et al 2014) [46]
Table 7 illustrates the security threats which were identified during the analysis under the headings software, hardware, Information/data and network communication. From the analysis it can be seen that the largest threats comes from the software segment particularly the from the APP’s and API categories.
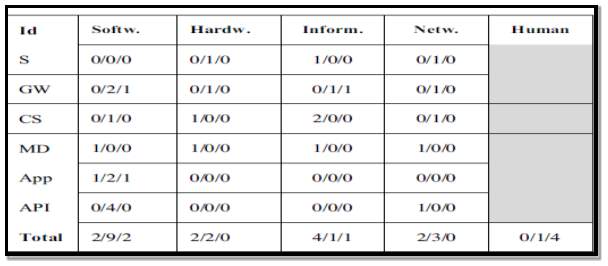
Figure 17 (Jacobsson et al 2014) [46]
(low = <5/Medium = 6-9/High = >10)
The following is a summary of the main threats from figure 17:
- Hardware: Theft, tapering due to poor physical security.
- Software: Low security authentication and logging on settings and systems.
- Information/data: Poor or no access control systems
- Network communication: Weak authentication and confidentiality settings within sensors and the gateway.
The authors state that the greatest risk is from humans who want to maliciously attack or obtain information. If devices that are connected to the internet such as security cameras are compromised they could have severe consequences due sensitive material been accessed and if energy consumption data was accessed, the home owners daily habits could be determined. The authors ask the question about the boundaries of public and private data and who can access it without diminishing security.
Research by (Godha et al, 2014) [47] focused on the controlling the type of access a device gets when connecting to a smart home network by using a tagging technique. Seven access level privileges choices are available from ‘no access’ to ‘full read/write and internet access’ and can be assigned to devices using a authentication mechanism.
(Gill et al, 2012) [48] divided the various aspects of home automation security into the following categories:
- Confidentiality: Only the users involved in message transfers should be able to view or access its content to avoid a third party using the information illicitly.
- Integrity: if a third party maliciously changes the contents of a message the genuine users must be able to detect it.
- Authentication: The source of a message should be easily validated via a receipt.
- Access Control: Users should be able to have different levels of authorized access depending on their needs.
- Availability and fairness: An attacker should not have the power to prevent a service from working as it should.
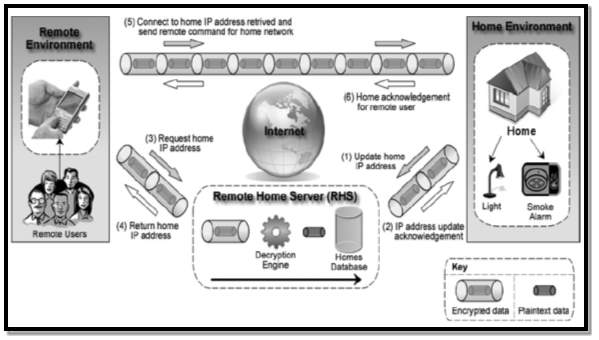
Figure 17 Source: (Gill et al, 2012) [48]
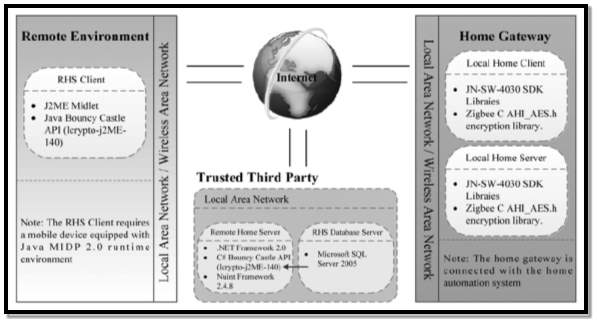
Figure 18 Source: (Gill et al, 2012) [48]
They propose a system for allowing remote access to a home safely and securely. The system is called the RHS approach (Remote user, Home Automation system). Figure 16 depicts the RHS framework within a smart home and Figure 17 depicts the RHS system architecture. The proposed system greatly increases the security as it controls the smart homes dynamic IP address and also has a server and client master key for remote access. The advantages of this type of security system are as follows:
- End to End security: Only the home automation system and the client accessing the system remotely can read messages.
- Reduced ciphertext availability: The quantity of ciphertext at the RHS is low due to the direct communication between the remote user and the RHS.
- Service availability: If the RHS fails for some reason, a connection can still be made due to the remote user storing previous IP address of connections.
- Reduced connection time: The average connection speed is reduced.
- Increased trusted third party performance: A single RHS is able to supply an increased number of devices within the smart home due to the reduced burden on third party machines.
- Distribution of internet traffic: Reduce risk of congestion.
- Reduction in bandwidth wastage: bandwidth is saved as the server is not always connected to the RHS.
Research by (Alberca et al, 2016) [49] presents a comprehensive security analysis on an Arduino Yun which is one of the most popular devices on the market for prototyping IoT projects. The Arduino Yun consists of two distinct layers in its system architecture:
- Lower layer = ATmega32u4 chip
- Higher layer = Atheros processor Linux chip
They illustrate how there is inadequate security measures in place to prevent a multitude of attacks, particularly in the lower layer. They suggest that due to the low cost style of this type of platform, robust security features are not incorporated.
- Arduino Yun Microcontroller
Research by (Alberca et al, 2016) [49] describe the Arduino platform as one of the most prominent used by developers and that the Arduino Yun in particular is one of the best for prototyping IoT applications. The Arduino Yun is an open adaptable microcontroller due to its uncomplicated architecture. It has two separate layers within its architecture, the lower layer which uses the ATmega43u4 processor and the higher layer which uses the Atheros processor which supports Linino. Linino is a Linux distributed operating system and based on Open Wrt called Open Wrt-Yun. The board provides network connectivity via a Wi-Fi support and an Ethernet connection. Other features include a micro-SD slot and a USB port. Figure 19 below illustrates the Arduino Yun microcontroller with its various features highlighted.
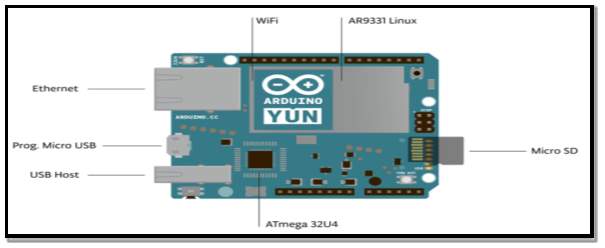 Figure 19 Source: (Alberca et al, 2016) [49]
Figure 19 Source: (Alberca et al, 2016) [49]
The distinguishing factor of the Arduino Yun board compared to other Arduino platforms is that it has the ability to support progressive communication functions via its Linux distribution. With these capabilities, developers can create their own shell and python scripts for communications between API’s and the Arduino Yun. A logical bridge is used to connect both processors. It aids communication between the Arduino and Linux architecture and also allows the Arduino programs or sketches to run shell scripts, network interface communication and receive data from the Linux environment. Figure 20 illustrates the Arduino Yun architecture including the Bridge connecting the Linux and Arduino environments.
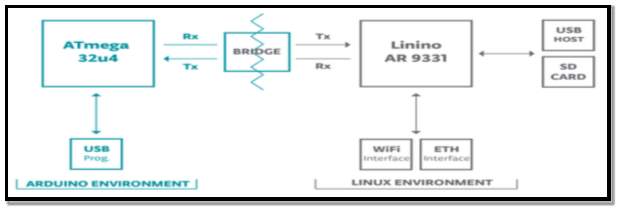 Figure 20 Source: (Alberca et al, 2016) [49]
Figure 20 Source: (Alberca et al, 2016) [49]
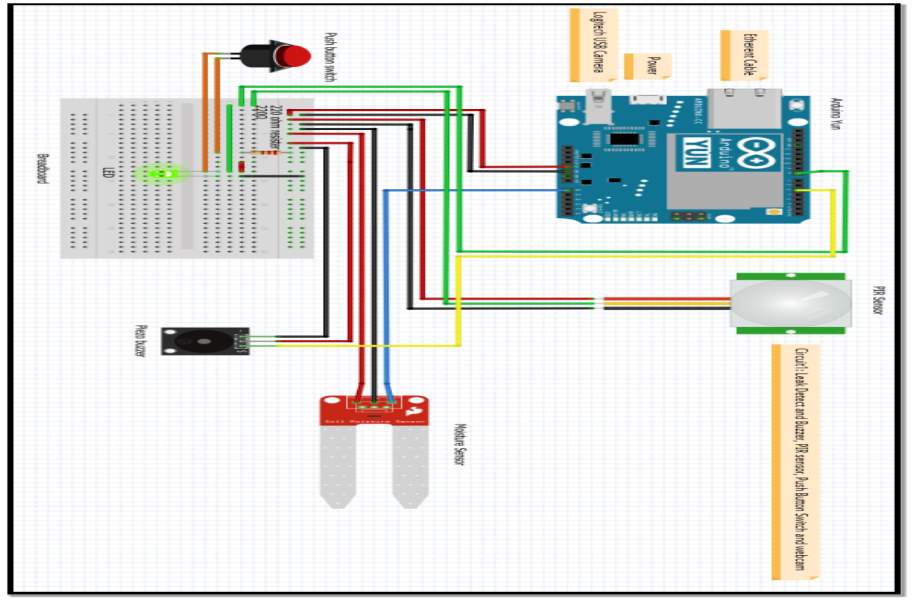
(Sandhya and Krishna Kanth, 2015) [50] developed a home data collection and alert system taht utilizes the Arduino Yun. The system uses a temperature and humidity sensor (DHT111 sensor) and a PIR motion detection sensor to measure and collect data. The data is then sent to a cloud storage facility (google documents) were it can be analysed. The Arduino sketch calls on a python script which is stored in the Arduino Yun micro-SD card to link the Yun with google documents and to allow the data to be transferred efficiently. When the motion sensor is activated an alert is generated in the Google cloud console to signal that activity has been detected.
Research by (Rajurkar et al, 2016) [51] proposed a home automation control and monitoring system using the Arduino Yun. Figure 21 illustrates the system architecture used during the research. A smart phone or laptop is used for the graphical user interface, a security access code is required to gain access to the network and the Arduino Yun is used to control a relay board to facilitate data exchange between the various sensors and the internet. The authors suggest that this system operates more efficiently than traditional systems using Bluetooth or GSM as it can handle greater data rates, it has the ability to control and monitor the devices in the system remotely from anywhere in the world via the internet and the system has greater security due to the authentication access codes.
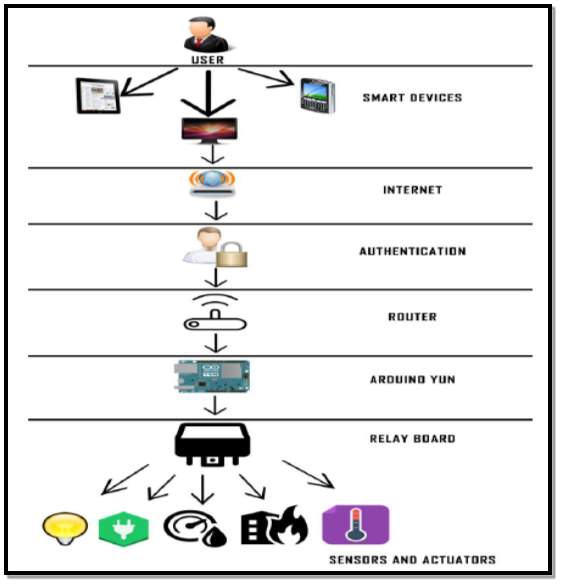
Figure 21 Source: (Rajurkar et al, 2016) [51]
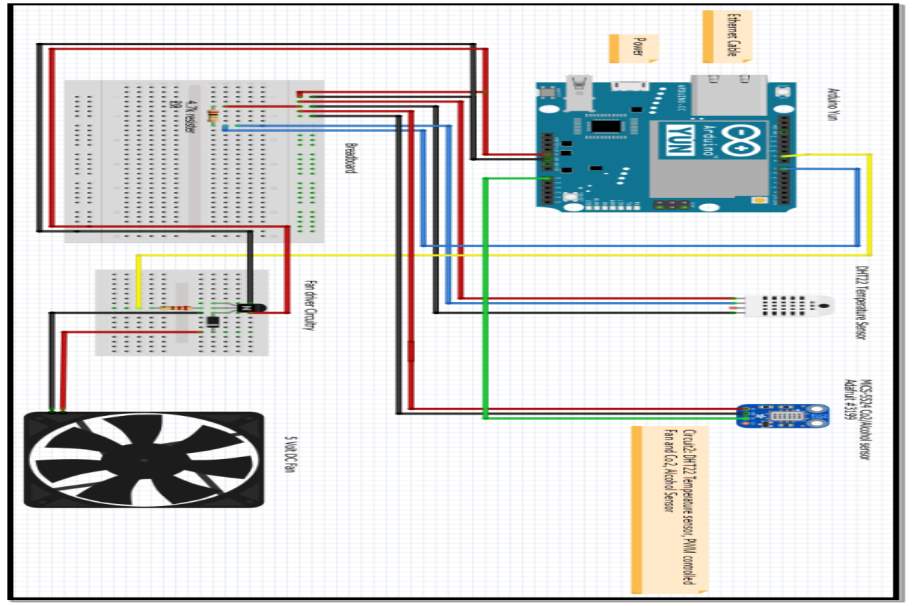
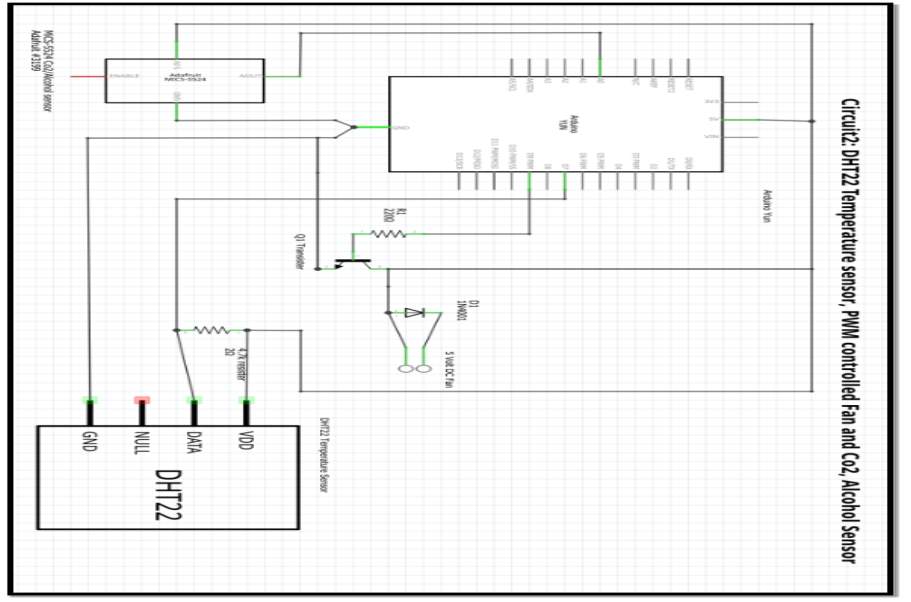
Research by (Patil et al, 2016) [52] proposed a system using IPv6 due the depletion of IPv4 caused by the IoT revolution were more and more devices are becoming smart and connected to the internet. Their system consists of a smart home control centre using an Arduino Yun to aid the IPv6 addressing and control of the smart home devices. Figure 22 shows there proposed architecture. The system includes the following functions.
- Devices connected to a relay can be switched on/off via Wi-Fi and Arduino Yun
- Lighting brightness can be manual adjusted using pulse width modulation facility on the Yun.
- Light brightness control by a light dependant sensor.
- Simulation of a fan speed control.
- Fan speed control dependant on the output of a temperature sensor.
- Light switching activated by motion detection.
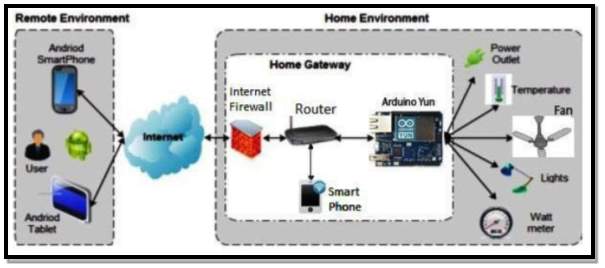
Figure 22 Source: (Patil et al, 2016) [52]
2.8 Ethical issues surrounding IoT
Research by (Zhang Jun, 2014) [53] spells out the main ethical issues that could affect the world of IoT. These are as follows:
- Security of Data: Hackers have a proven track record of been able to bypass security infrastructures. The author refers to the 2011 security attack on Sony; this affected 77 million PlayStation users when user’s personal information from their accounts was hacked. This equates to 1% of the entire population been hacked via a single platform. With the more and more devices becoming smart and connected, the possibility of personal information been obtained fraudulently increases.
- Privacy Breaches: More and more things connecting via the internet means more and more data been stored on server banks. There are serious privacy concerns regarding this information. Who owns it? Who is responsible for it? Who can access it? Personal information from a smart home could be invaluable to businesses and corporations trying to market new products etc. If a user does not want to share information on a particular application this may lead to reduced functionality, therefore the to get the full range of functions a user would be forced to hand over their privacy rights.
- Humans will become over reliant on technology: With the increase in the number of devices been connected it may be lead to humans becoming over reliant on technology. For example a smart phone has multiple functions, phone, internet, Sat Nav, calculator etc., so if we don’t have it on our person we can feel disabled.
- Machines will enslave humans: Been over reliant on IoT could lead to none or reduced choice for humans. For example if you had a smart wardrobe that could detect the weather conditions and decide the most suitable clothes for you to wear on any given day. Also in the future, with the continued advances in artificial intelligence, devices will be able to think for themselves.
Figure
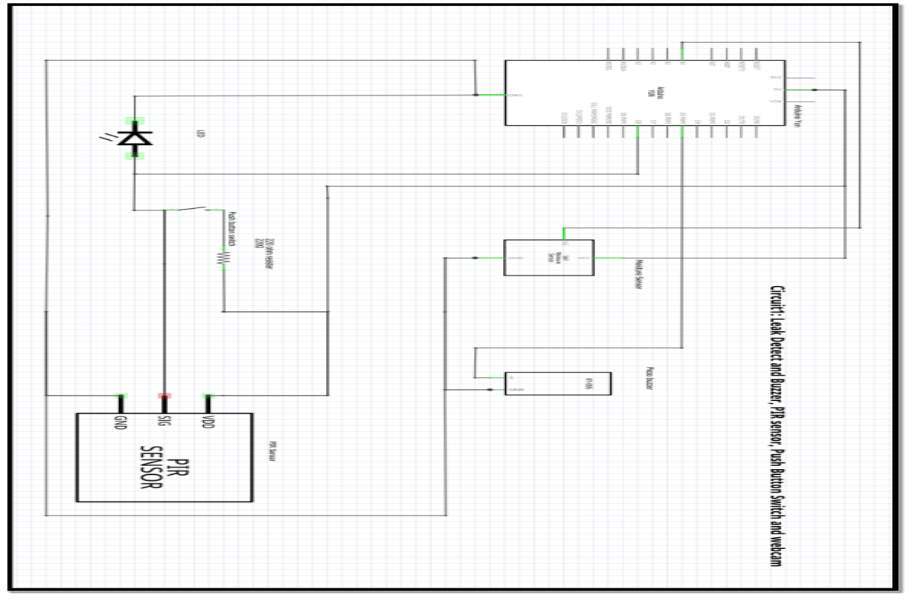
Figure 20
Figure
Figure
Capture 6
Project Management
References
[1] European Union, European IoT research group, Internet of Things Strategic Research Roadmap (2009), Brussels
[2] The Oxford Dictionary, URL: https://en.oxforddictionaries.com , Accessed November 2016
[3] International Data Corporation, (2015) “Explosive Internet of Things Spending to Reach $1.7 Trillion in 2020, According to IDC,” Press Release, June 2, 2015, http://www.idc.com/getdoc.jsp?containerId=prUS25658015, Accessed November 2016
[4] Adrian McEwen Hakim Cassimally (2014) Designing the internet of things, Publisher: John Wiley and Sons Ltd, United Kingdom
[5] Postscapes, URL: http://www.postscapes.com/internet-of-things-history/, Accessed November 2016
[6] Google Trends, URL: https://www.google.com/trends/explore?date=all&q=%22internet%20of%20things%22&hl=en-US, Accessed November 2016
[7] Gartner, URL: https://www.gartner.com, Accessed November 2016
[8] [5] Kaylee Moser; Jesse Harder and Simon G. M. Koo, (2014) Internet of things in home automation and energy efficient smart home technologies, 2014 IEEE International Conference on Systems, Man, and Cybernetics, pp.1260-1265, October 5-8, 2014, San Diego, CA, USA
[9] Cisco, URL: http://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/13769-5.html , Accessed December 2016
[10] TCP/IP Guide, URL: http://www.tcpipguide.com/free/t_TCPConnectionEstablishmentProcessTheThreeWayHandsh-3.htm, Accessed December 2016
[11] Microsoft Technet, URL: https://technet.microsoft.com/en-us/library/cc786128(v=ws.10).aspx, Accessed December 2016
[12] Networking layer-x, URL: http://networking.layer-x.com/p040200-1.html, Accessed December 2016
[13]IC-IMS, URL: http://www.ic-ims.com/informaticke_mreze/vlsm_eng/vlsm-and-subnetting-ip-address-range.png, Accessed December 2016
[14] Techopedia, URL: https://www.techopedia.com/definition/6006/application-layer, Accessed December 2016
[15] European FP7 research Project, URL: http://www.iot-a.eu/internal/resources/pr-material/illustrations/IoT-A%20Tree.png/view?searchterm=tree, Accessed December 2016
[16] Fawzi Behmann & Kwok Wu (2015) Collaborative Internet of Things, , Publisher: John Wiley and Sons Ltd, United Kingdom
[17] R. Khan, S, Khan, R. Zaheer and S. Khan (2012) Future Internet: The Internet of Things Architecture, Possible
Applications and Key Challenges, 10th International Conference on Frontiers of Information
Technology (FIT): Proceedings. (pp. 257-260).
[18] Mari Carmen Domingo (2012) A overview of the Internet of Things for people with disabilities, Journal of Network and Computer Applications 35 (2012) pp. 584–596
[19] Jia Xiaolin, Feng Quanyuan, Fan Taihua and Lei Quanshui (2012) RFID technology and its applications in Internet of Things (IoT), 2012 2nd International Conference on Consumer Electronics, Communications and Networks (CECNet)
[20] Luigi Atzori, Antonio Iera and Giacomo Morabito (2010) The Internet of Things: A survey, Computer Networks 54 (2010) pp. 2787–2805
[21] Wu He and Shancang Li (2014) Internet of Things in Industries: A Survey, IEEE TRANSACTIONS ON INDUSTRIAL INFORMATICS, VOL. 10, NO. 4, NOVEMBER 201,4 pp.2223-2243
[22] Gao Chong , Ling Zhihao and Yuan Yifeng (2011) The research and implement of smart home system based on Internet of Things, 2011 International Conference on Electronics, Communications and Control (ICECC) pp.2944-2947
[23] Kang Bing, Liu Fu, Yun Zhuo and Liang Yanlei (2011) Design of an Internet of Things-based smart home system, 2011 2nd International Conference on Intelligent Control and Information Processing, pp.921-924
[24] Pranay P. Gaikwad, Jyotsna P. Gabhane and Snehal S. Golait (2011) An survey based on Smart Homes system using Internet-of-Things, 2015 INTERNATIONAL CONFERENCE ON COMPUTATION OF POWER, ENERGY, INFORMATION AND COMMUNICATION, pp.330-335
[25] Divyan M. Konidala, Daeyoung Kim, Chan Yeob Yeun and Byoungcheon Lee (2011) Security Framework for RFID-based Applications in Smart Home Environment, Journal of Information Processing Systems, Vol.7, No.1, March 2011, pp. 111-120
[26] Soo-Cheol Kim, Young-Sik Jeong and Sang-Oh Park , RFID-based indoor location tracking to ensure the safety of the elderly in smart home environments, Personal and Ubiquitous Computing, December 2013, Volume 17, Issue 8, pp 1699–1707
[27] Serbulent Tozlu, Murat Senel, Wei Mao and Abtin Keshavarzian (2012) Wi-Fi enabled sensors for internet of things: A practical approach, IEEE Communications Magazine Volume: 50, Issue: 6, June 2012
[28] Prof. R.S. Suryavanshi, Kunal Khivensara, Gulam Hussain, Nitish Bansal and Vikash Kumar (2014) Home Automation System Using Android and WiFi, International Journal Of Engineering And Computer Science, Volume 3 Issue 10 October, 2014, pp. 8792-8794
[29] N. Sriskanthan, Tan, A. Karande (2002) Bluetooth based home automation system, Microprocessors and Microsystems volume 26 (2002) pp. 281–289
[30] Pooja N.Pawar, Shruti Ramachandran, Nisha P.Singh and Varsha V.Wagh (2016) A Survey on Internet of Things Based Home
Automation System, International Journal of Innovative Research in Computer and Communication Engineering, Vol. 4, Issue 1, January 2016, pp. 76-81
[31] Mohamed Abd El-Latif Mowad, Ahmed Fathy and Ahmed Hafez (2014) Smart Home Automated Control System Using
Android Application and Microcontroller, International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014, pp. 935-939
[32] Kumar Mandula, Ramu Parupalli, CH.A.S. Murty, E. Magesh and Rutul Lunagariya (2015) Mobile based home automation using Internet of Things (IoT), 2015 International Conference on Control, instrumentation, Communication and Computational Technologies pp. 340-343
[33] Sean Dieter Tebje Kelly, Nagender Kumar Suryadevara and Subhas Chandra Mukhopadhyay(2013) Towards the Implementation of IoT for Environmental Condition Monitoring in Homes, Sensors Journal, Volume: 13, Issue: 10, Oct. 2013, pp.3846-3853
[34] Muneer Bani Yassein, Wail Mardini and Ashwaq Khalil (2016) Smart Homes Automation using Z-wave Protocol, 2016 International Conference on Engineering & MIS
[35] Ching-Chuan Wei, Yan-Ming Chen, Chao-Chieh Chang and Chi-Han Yu (2015) The Implementation of Smart Electronic Locking
System Based on Z-Wave and Internet, International Conference on Systems, Man, and Cybernetics,
[36] Dhananjay Singh, Gaurav Tripathi and Antonio J. Jara (2014) A survey of Internet-of-Things: Future Vision,
Architecture, Challenges and Services, World Forum on Internet of Things (WF-IoT) 2014
[37] Sarita Agrawal ; Manik Lal Das (2013) Internet of Things — A paradigm shift of future Internet applications, 2011 Nirma University International Conference on Engineering
[38] S.Sujin Issac Samuel, (2016) A Review of Connectivity Challenges in IoT-Smart Home, 2016 3rd MEC International Conference on Big Data and Smart City
[39] Programmable Web, URL: https://www.programmableweb.com/api/, Accessed January 2017
[40] Tenboo, URL: www.Temboo.com, Accessed January 2017
[41] IFTTT, URL: www.IFTTT.com, Accessed January 2017
[42] Python, URL: www.python.com, Accessed January 2017
[43] P BHASKAR RAO and S.K. UMA (2015) RASPBERRY PI HOME AUTOMATION WITH WIRELESS SENSORS USING SMART PHONE, Journal of Computer Science and Information Technology, Vol. 4, Issue. 5, May 2015, pg.797 – 803
[44] Israel Joel Koenka a, Jorge Sáiz b and Peter C. Hauser (2014) Instrumentino: An open-source modular Python framework for
Controlling Arduino based experimental instruments, Computer Physics Communications 185 (2014) pp. 2724–2729
[45] Ameena Saad al-sumaiti , Mohammed Hassan Ahmed and Magdy M. A. Salama (2014) Smart Home Activities: A Literature Review, Electric Power Components and Systems, Volume 42:3-4, pp.294-305
[46] Andreas Jacobsson, Martin Boldt and Bengt Carlsson (2014) On the Risk Exposure of Smart Home Automation Systems, 2014 International Conference on Future Internet of Things and Cloud, pp. 183-190
[47] Rahul Godha, Sneh Prateek and Nikhita Kataria (2014) Home Automation: Access Control for IoT Devices, International Journal of Scientific and Research Publications, Volume 4, Issue 10, October 2014
[48] Khusvinder Gill, Shuang-Hua Yang, and Wan-Liang Wang (2012) Secure remote access to home automation networks, IET Information Security, Volume 7, Issue 2, June 2013, pp. 118 – 125
[49] Carlos Alberca, Sergio Pastrana, Guillermo Suarez-Tangil and Paolo Palmieri (2016) Security Analysis and Exploitation of Arduino device’s in the Internet of Things, ACM International Conference on Computing Frontiers, Pages 437-442
[50] Sandhya and Krishna Kanth, (2015) Sensor Network Accessing Cloud Services for Data Collection and Sharing Using Arduino Yun, INTERNATIONAL JOURNAL OF SCIENTIFIC RESEARCH, Volume: 4, Issue: 9, Sept 2015
[51] Abhijeet Rajurkar, Onkar Shinde, Vinayak Shinde, Bhushan Waghmode and Prof. Yogesh Thorat (2016) REVIEW ON SMART HOME CONTROL AND MONITOR SYSTEM, Multidisciplinary Journal of Research in Engineering and Technology, Volume 3, Issue 1, Pg.887-891
[52] Mahesh Patil, Sumathy Subramaniam and Rajendra Hegadi (2016) IPv6 Enabled Smart Home Using Arduino, International Conference on Communications, Information Management and Network Security (CIMNS 2016)
[53] Zhang Jun (2014) Internet of Things, Disruption or Destruction?; URL: http://www.academia.edu/
[1] http://internet-of-things-research.eu/pdf/IoT_Cluster_Strategic_Research_Agenda_2011.pdf
[3] https://en.oxforddictionaries.com/definition/internet_of_things
[4] International Data Corporation, “Explosive Internet of Things Spending to Reach $1.7 Trillion in 2020, According to IDC,” Press Release, June 2, 2015, http://www.idc.com/getdoc.jsp?containerId=prUS25658015
[5] Designing the internet of things by Adrian McEwen Hakim Cassimally
[6] http://www.postscapes.com/internet-of-things-history/
[7] https://www.google.com/trends/explore?date=all&q=%22internet%20of%20things%22&hl=en-US
[8] https://www.gartner.com/doc
[9] https://www.techopedia.com/definition/6006/application-layer
[10] http://www.iot-a.eu/public
[11] Collaborative Internet of Things by Fawzi Behmann & Kwok Wu
[12] http://pure.qub.ac.uk/portal/files/81384964/PID2566391.pdf Khan, R., Khan, S. U., Zaheer, R., & Khan, S. (2012). Future Internet: The Internet of Things Architecture, Possible Applications and Key Challenges
[13] https://lms.ctl.cyut.edu.tw/sysdata/22/27122/doc/571c22f5f635d883/attach/1523813.pdf
[14] http://ieeexplore.ieee.org/document/6201508/
[15] https://www.miun.se/siteassets/fakulteter/nmt/summer-university/1-s20-s1389128610001568-mainpdf
[16] https://www.researchgate.net/publication/270742269_Internet_of_Things_in_Industries_A_Survey
[17] http://ieeexplore.ieee.org/document/6066672/
[18] http://ieeexplore.ieee.org/document/6008384/
[19] http://ieeexplore.ieee.org/document/7259486/
[20] http://ocean.kisti.re.kr/downfile/volume/kips/E1JBB0/2011/v7n1/E1JBB0_2011_v7n1_111.pdf
[21] http://link.springer.com/article/10.1007/s00779-012-0604-4
[22] http://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=6211498
[23] http://www.ijecs.in/issue/v3-i10/56%20ijecs.pdf
[24] https://pdfs.semanticscholar.org/a001/5665acb00ddf1491aec436e47cfb75835b82.pdf
[25] https://www.ijircce.com/upload/2016/january/15_A%20Survey.pdf
[26] https://pdfs.semanticscholar.org/a4f6/49c50b328705540652cb26e0e8a1830ff676.pdf
[27] http://ieeexplore.ieee.org/document/7475301/
[28] http://ieeexplore.ieee.org/document/6516934/
[29] http://ieeexplore.ieee.org.ezproxy.library.itsligo.ie:2048/stamp/stamp.jsp?arnumber=7745306
[30] http://ieeexplore.ieee.org.ezproxy.library.itsligo.ie:2048/stamp/stamp.jsp?arnumber=7379483
[31] http://ieeexplore.ieee.org.ezproxy.library.itsligo.ie:2048/stamp/stamp.jsp?arnumber=6803174
[32] http://www.ijsrp.org/research-paper-0413/ijsrp-p1656.pdf
[33] http://ieeexplore.ieee.org.ezproxy.library.itsligo.ie:2048/stamp/stamp.jsp?arnumber=7460395
[37] http://www.ijcsmc.com/docs/papers/May2015/V4I5201599a70.pdf
[5] ieeexplore.ieee.org/iel7/6960119/6973862/06974087.pdf
[6] http://www.tandfonline.com/doi/pdf/10.1080/15325008.2013.832439
[7] http://ieeexplore.ieee.org/document/6984193/authors
[8] http://www.ijsrp.org/research-paper-1014/ijsrp-p3494.pdf
[9] http://digital-library.theiet.org/content/journals/10.1049/iet-ifs.2011.0303
[10] http://www.seg.inf.uc3m.es/papers/2016mal-iot.pdf
[12] http://www.mjret.in/V3I1/M10-3-1-1-2016.pdf
[13] https://www.researchgate.net/publication/309439779_IPv6_Enabled_Smart_Home_Using_Arduino
[14] Internet of Things, Disruption or Destruction? Zhang Jun
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Internet of Things"
Internet of Things (IoT) is a term used to describe a network of objects connected via the internet. The objects within this network have the ability to share data with each other without the need for human input.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




