Phishing Techniques and Detection Approaches
Info: 7735 words (31 pages) Dissertation
Published: 11th Oct 2021
Tagged: Cyber Security
ABSTRACT
With the current continuous growth of data and the increasing access to internet, people are always thinking of ways to gain data from other people usually through the internet. One of the most common ways of stealing information is Phishing. Phishing is a kind of online fraudulent exercise where people use several ways with the aim of acquiring vital information like credit card information from other people. With the rise of internet, phishing is now a big threat to many individuals and organizations, as new techniques are developed to combat phishing, new ways also evolve to steal information. For the past years, many methods have been developed to either prevent or detect phishing, people are now associated with a whole lot of risks as there are always new ways of phishing emanating from different kinds of people and places. Methods associated with the prevention and detection of phishing have been presented with several advantages and disadvantages, and even though the risks associated with phishing have not been completed eliminated, it has been significantly reduced. Many used cases have been presented with their major vulnerabilities as well as the various anti-phishing techniques that were used to combat the phishing.
INTRODUCTION
Phishing attack is a fraudulent exercise carried out by criminals with the main aim of deceiving people to get them to release their personal information, this is usually done through websites and emails. These phishing methods are presented in a way that victims believe they are coming from credible brands or organizations. A research that was recently conducted by Microsoft showed that about 0.4% of people who receive emails are exploited by phishing attack [10]. In the USA, the yearly loss to phishing attack is estimated to be between $350 million and $2 billion [14,26]. With the rise in phishing attack in the world, countries are now finding ways to curb it as a result of the huge sums of monies lost. Countries are enacting laws to prosecute people who are found culpable. Organizations are also educating employees on all the forms of phishing that are evolving. Internet service providers are also not left out in the ways of managing the risk associated with phishing, as they have ways of filtering emails to block emails that are suspicious of phishing. One of the common victims are users of social media network sites. With the rise in the internet, the risk associated with phishing will always increase and criminals will always find new ways to deceive people. As phishing evolves, stakeholders will always find new ways of mitigating the risk associated with phishing, therefore the battle will be ongoing until one of the forces exerts much power to totally overcome the other.
LITERATURE REVIEW
A case study of how Malcovery Security, an Information Technology security company saved Major American Bank Company Corporation (MAB) huge sums of money was analyzed. MAB was a financial service and multinational bank. It was a reputable and one of the biggest companies in the United States according to assets. MAB adopted several methods to detect and combat phishing. Among some of the methods used by MAB to combat phishing were rigorous security training for workers, high level of security technology, web gateway blacklist, web and email client filters, internal and external takedown services and Domain Based Message Authentication, Reporting and Conformance (DMARC). Before engaging the services of Malcovery, MAB lost millions of dollars annually to phishing attack. When Malcovery was providing services, they began by providing detailed monthly report by their threat intelligence team. In the monthly report, they provided the statistics on all the phishing websites that attacked MAB’s customers and details of the top five attacks. Malcovery also made PHISHIQ portal available to MAB representatives. This portal made known to MAB all the details and information about phishing websites that attack the bank. MAB also had an abuse box where employees and customers report emails they suspected to be fraud. Malcovery then processed all these emails and adds them to the portal. During Malcovery investigations, they realized that the leading malicious spam came from Zeus Banking Trojan. The trojan had the ability to take absolute control of the computer of its victim, then steal all the sensitive banking information. In conclusion, MAB had weaknesses that phishers exploited in employees. Vulnerabilities in MAB included employees and customers inability to detect phishing emails and messages despite several trainings and weak anti-malware. Malcovery provided much education to employees and customers and provided a high and more secured tool to fight malwares.
A case study of Menlo Security and Fortune 50 Global Investment firm. Despite the high security level; anti-virus and spam, data security and encryption, firms are making huge losses from phishing. The firm was embedded with all these security layers but experienced a lot of losses. The structure of the firm was homologous to many companies. Their architecture comprise cloud, on-premises of data encryption and security, sandboxing, antispam and antivirus. Despite the fact that these solutions could combat phishing, they were receptive to spear phishing and malware exploits. The spear phishing was aimed at people with common attributes or variables in the firm. The email link is usually distinctive. The firm possessed the security system to determine phishing emails by third party data, however, the security system cannot detect email links that are distinctive and directed to specific people. End-users of the firm were then sent to fake websites where they download malwares. These malwares then steal sensitive information leading to huge payout from the phishers. This is exactly the dilemma that the firm was experiencing that led to huge financial losses. The firm, after realizing this pain employed the services of Menlo security Isolation Platform (MSIP) to solve the phishing problem. The major security plan of Menlo was isolation. This provided protection to users from leading them to phishing sites and harmful email links. With isolation, firm users could use input-field restrictions to view sites without harm. Extra corporate training on phishing attack was also given to employees. Isolation can be compatible with mail servers and does not require any software. The main vulnerabilities are weak antimalware and insufficient training which makes employees unable to detect some phishing emails.
Another case study of Org 10, a financial service provider and large multinational firm. Customers began notifying Org 10 of their infected computer system as a result of phishing emails and their loss of money through fraud. Investigations showed that the mail server of Org 10 was infected, and the infection was transmitted to the computer system of customers through emails. The emails were analyzed, and an attachment was found, this attachment was identified to be a malicious trojan. After careful analysis, they found that emails were not from Org 10 but from third party mail server. other details found were web application vulnerabilities from Org 10 company website. This is how the phishers were able to get the emails of customers in order to send the trojan attachment. The email file name was Statement_Jan_2015.zip. The trojan had ability to steal sensitive information from the customers. The trojan extricated data ranging from login credentials and banking information. Even though Org 10 had antivirus which was updated frequently, the malware writers alter the structure of the malware making it easy to get customer information whenever necessary. Vulnerabilities identified were web application vulnerabilities and insufficient communication between Org 10 and the customers.
A case study of the Royal Bank of Scotland (RBS) and Wombat Security. The bank had consistently received a lot of phishing emails for several years and it is estimated that a major phishing email has the potential to make the bank incur approximately $250000. The bank started carrying out investigation into the phishing emails that was received for several years. The major vulnerability discovered was employee reaction. Apart from the fact that employees had in a difficulty in detecting phishing emails, they saw it as the mandate of RBS alone to combat phishing emails. They believed combating phishing emails had nothing to do with employee roles and responsibilities. After considering several security companies to combat phishers, RBS finally settled on Wombat Security because of their formidable security systems and exceptional customer service. Wombat had a Learning Management System that was built for particular objectives and Anti-Phishing Training Suite that provided an exceptional training to 80000 employees. Employees were consistently tested with phishing emails and those who could not detect phishing emails by clicking on them received additional training. In the long run RBS had a 78% reduction in phishing vulnerability.
Lastly a case study of Northeastern US College and Wombat Security. The college had approximately 1400 staff and faculty members and 7500 students. Even though school authorities will send emails of phishing alert intermittently, there was no formal or official training for students and staff on phishing alert. This created a gap phishing email detection. A phisher at a point in time sent a phishing email to staff instructing them on the new amendment in staff positions and policies and the message was cloned to appear from the new Dean’s office. This caused a lot of confusion and college quickly employed the services of Wombat Security to address security concerns in the college using their Learning Management System. This successfully led to 90% downsizing in effective attacks. This is a result of the good training provided by Wombat Security.
Table 1
| MAJOR VULNERABILITIES IN THE CASE STUDIES | |
| 1. | Weak antimalware |
| 2. | Employees and customers inability to detect phishing emails and messages |
| 3. | Insufficient communication between management organizations and employees or customers |
PLANNING PHISHING ATTACK
Phishers, like most criminals, have certain factors that they consider before they launch an attack. During planning there are major factors that they consider before they launch an attack. The major factors that phishers consider before launching an attack are cost of launching an attack, difficulty of launching an attack, user base of the institution, security measures of the institution and the net worth of the clients.
Cost of Launching an attack
Just like every other business that performs cost benefit analysis, phishers also assess the cost involved in launching an attack, first, they try to determine if they have sufficient funds to undertake that specific project, this is because sometimes they must team up with other hackers or malware writers to successfully launch the attack. However, this might also depend on the benefits to be derived from the attack including the importance of the information to be stolen.
Difficulty of launching an attack
During the planning stage, phishers put a lot of things into consideration, this includes the magnitude of difficulty in launching the attack. For instance, if it requires that the phisher teams up with a very good hacker, this becomes a problem if the phisher might go through a lot to find a good hacker that can write a specific malware for the attack. If they feel they might go through a lot of difficulty to launch an attack, they might abandon the project for a much easier project.
User base of the institution
If an institution has a wide user base, then there is a higher probability that a lot of people might be using the services of the institution. This implies that sending phishing emails to a larger household might have a higher chance of deceiving people because they might think the message is from the institution of which they are subscribed to. For instance, if 90% of Americans have an account with Wells Fargo, sending phishing emails based on Wells Fargo have a higher chance of deceiving many households because they might believe it’s from Wells Fargo. This is quite different from the situation where emails are sent to a specific group of people.
Security measures of the institution
It is more difficult for a phisher to succeed in an institution with higher security measures. This is because institutions with robust security measures makes it difficult for the emails to penetrate the system, it will be filtered and blocked. Phishers usually carry out a background check on institutions to know the degree of their security measures. They rely on their history with previous hackers or fishers and information from the media.
Net worth of clients
The main goal of phishers is to make money. They are always motivated by money and knowing that clients have a higher net worth, they are ready to do anything to deceive them to get everything they need from them. They are always ready to launch attack on clients with high net worth irrespective of the controls that they have in place.
TYPES OF PHISHING ATTACK
Phishing was earlier seen in emails, then it migrated to diverse areas including social networking sites, SMS, instant messaging, multiplayer games and VOIP (Voice over internet protocol). Phishing can be classified into different categories and this includes clone, spear, phone, DNS-based phishing and man in the middle attack.
Clone phishing
Is a type of phishing attack that have websites that are usually used by victims imitated by phishers. The real website is imitated by the clone and requests users for login information. When the user provides their login information, this gives an opportunity to the phisher to keep these information on his own server in a database record, after saving all the required information, these criminals then takes the users to the authentic website. A common example are websites that mimic companies that offer online sales like Amazon, Walmart etc.
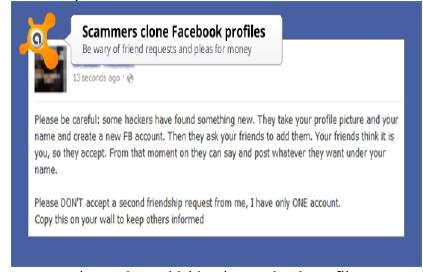
Fig 1: Clone phishing in Facebook profiles [3]
Spear Phishing
Just as the name suggests, it is directed to a particular person or a group of people. So, it is not like clone, where criminals cast a wide net to lure anyone who visits the website but rather emails are sent to some selected people, it could be an entire organization or institution. Usually the selected people have a common variable. An example is students in a university receiving emails from criminals in order to gain access to their credentials.
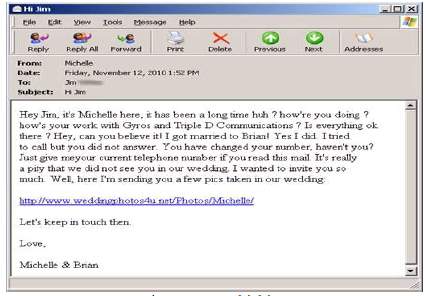
Fig 2: Spear phishing [2]
Phone Phishing
Is a type of phishing where victims are deceived on phone either by SMS or voice telephone system. This usually takes different forms, for SMS, victims can receive a message about a service that they initially endorsed to, then the message tells them to be directed to a website in order to confirm an order. It is during this visit that their credentials are tampered with. With the voice calling, sometimes victims receive calls from the criminals and informs them that they have received a grant and they need to provide social security or pay money in order to gain access to the money. Sometimes they are directed to their bank accounts or credit cards and vital information is siphoned from them.
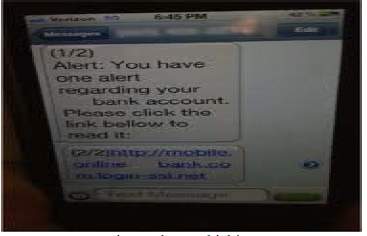
Fig 3: Phone phishing [28]
DNS-Based Phishing
This phishing is also known as Pharming. It involves criminals tampering with the domain name of an authentic website, they then to swap the domain name of the authentic website to their fake website. Since the DNS is responsible for converting the alphabets of the Internet Provider to numeric, when is tampered, it directs you to the new domain name and subsequently directs you to the fake website. At this point they are able to get access to all your credentials that you provide on the fake website.
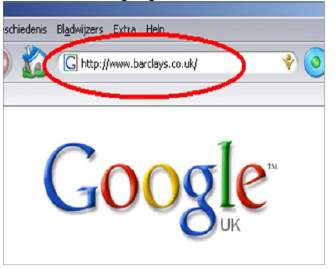
Fig 4: DNS-Based Phishing [20]
Man-in-the-middle-attack
Just as the name suggests, this refers to the kind of attack where the phisher interrupts a message that is sent between two channels. These channels are often referred to as the sender and receiver. The hacker secretly obstructs the electronic message that is transmitted between the sender and receiver. The hackers alter the message after gaining access to the message. The hackers usually use trojan horse for the obstruction of the message.
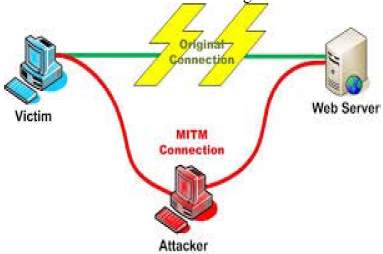
Fig 5: Man-In-The-Middle-Attack Phishing [23]
PHISHING DETECTION APPROACH
There is no way that phishing can be mitigated or controlled without detection. The first stage in controlling phishing is detection. The approaches in detection can be classified into two broad categories, User and System approach.
User Approach
In this approach, end-users are giving numerous trainings on the nature of phishing, trainings include all the elements of phishing attack, how attackers present phishing and the new forms of phishing. Training enables users to differentiate phishing from non-phishing messages because it improves their ability to recognize phishing attacks. Hackers have learnt to change the ways they present phishing always. Phishing is evolving, and organizations must train employees every year in order to be able to detect the new techniques of phishing. It is imperative to take notice that user approach is not the same as the preventive approach but a detection approach which subsequently leads to mitigation approach.
System Approach
System approach refers to any method that is used to detect phishing attacks without including the end-users. This refers to the configuration of a computer software, computer components or peripherals that are part of the computer system to detect phishing attacks.
DNS Service: One way is the use of a DNS that is customized. The job of the DNS is to convert the alphabetical Internet Provider address into a numerical one that is recognized by the internet. When the DNS server is customized, it’s only able to provide the IP address of the authentic websites as it blocks all the bogus websites. Some DNS can filter certain websites based on what they display in their content.
Browser phishing list: The new versions of browsers are now equipped with unique features that includes some specific phishing list. When you visit a phishing site, which is part of the phishing list in the browser, a list of messages are presented to warn you that the site you are visiting is not safe.
ASSESSING AND MEASURING THE SEVERITY OF PHISHING
Over the years, phishing attacks has significantly grown over the internet. It has allured computer users to visiting corrupt and illegal websites and influencing them to enter confidential information on the sites. Phishers (as they are popularly called) make these sites visibly alike to real websites to trick the users. Awareness of Phishing messages among users has increased, but so has the sophistication of these messages (Jagatic, Johnson, Jacobsson, & Menczer, 2007). Hackers design phishing messages today to affect basic human emotions e.g. fear, greed, and altruism) and often targets specific groups to exploit their specific needs. (Goel et al 2017). How critical is this attacks on the users of Information Technology (IT) infrastructure? Are the right elements considered in the security awareness of the organization? (The right elements in the context of users (employees). Do we have the right employees assuming the right position with the right roles and responsibilities? Are the technologies in place user friendly, up to date and installed appropriately to perform the security features? What processes are outlined and implemented to manage the use of technology by the users? Are the Policies comprehensively interpreted to achieve the security goals of the organization? All of these will be assessed in measuring the severity of Phishing attacks.
One of the mistakes most companies make leaving them vulnerable to the attack is not putting the right tools in place and refusal to train users (employees) on their responsibilities in information security. These employees has all it takes and the knowledge that is judgmental to the success of infringing the company’s security. Phishers are fully aware of these facts and therefore exploit the weakness of the user.
Companies also fall victim of phishing attacks as a result of incautious and inexperience surfing the internet. Web users tend to visit websites that are not secured thereby falling prey of phishers. Companies are supposed to formulate policy that will prevent specific sites from being accessed as this could reduce the probability of the company’s security being compromised.
Phishers take advantage of the outdated systems anti-virus, anti-spam to launch their attack. They are always on the lookout for vulnerabilities in the security of companies. The more reason why companies should not be slack in their roles to preventing the attacks. Passwords of employees should be changed regularly and made difficult to guess. . The technology provided to employees should be user friendly because if otherwise, phishers are given edge to launch their attacks on the employees because of their inability to work through the systems.
High-risk security performance displayed by computer users has the prospective of leaving the device susceptible to agreement. There are so many security tools available which are designed to assist users in safeguarding themselves against prospective Phishers. However, the so called tools cannot deter the users from engaging in the act but will at least enlighten them. What constitutes risky behavior is not necessarily obvious to all end-users and can be difficult to recognize. There are multiple examples of behavior which could be perceived as risky in the context of a browser-based environment, e.g. creating weak passwords or sharing passwords with colleagues (Stanton et al 2005, Payne and Edwards, 2008), downloading data from unsafe websites (Fetscherin 2009) or interacting with a website containing coding vulnerabilities. (Hadnagy 2011). What are the potential threats of this behavior? As computer users surf the internet, there are lots of security issues they are prone to. Downloading unlawful files place the system at risks because the downloaded file may contain malwares.
Interaction with websites featuring coding vulnerabilities is also risky and users are generally unaware of such flaws (14). Phishing attacks are also traced to drawbacks of technology. Often, users divulge too much information about themselves on social networking sites (1). For instance, a person’s location can be tracked from a Facebook or twitter account just to establish the movements. Often times, users misuse their password for account online which can be directly or indirectly linked to their personal information. There can be a tradeoff between the level of security of a password provides and its usability (Payne and Edwards 2008). Passwords that are not strong as a result of being short are less secured. On the part of the users, it is easier for them to remember but vulnerable to hacking. Some even share their passwords on trust. (Stanton et al 2005) interviewed 1167 end-users in devising a taxonomy of risky behaviors, it was found that 23% of those interviewed shared their passwords with colleagues, 27.9% of participants wrote their passwords down.
The vulnerability of human to deceit is determined by an intellectual factor. However, some research work has focused on establishing these factors as they relate to phishing. Different individuals have a different propensity to becoming victims of phishing attacks based on behavioral traits, demographic characteristics, personality, and habituation; we discuss these individual differences in this section. Moody, Galletta, Walker, and Dunn (2011) extensively investigated individual differences in susceptibility to phishing. They examined disposition to trust and distrust, curiosity, entertainment drive, boredom proneness, lack of focus, risk propensity, and level of Internet usage, attachment to the Internet, and Internet anxiety as the traits related to susceptibility. They found that several of the traits were good indicators of susceptibility to phishing, most notably trust, curiosity, boredom proneness, and risk propensity.
Sheng, Holbrook, Kumaraguru, Cranor, and Downs (2010) focused on demographic characteristics (gender, age, and education level) as predictors of phishing susceptibility. They found that women were more susceptible to phishing than men and that the 18- to 25-year-old individuals formed the most susceptible age group. Flores, Holm, Nohlberg, and Ekstedt (2015) examined cultural differences and personal determinants (e.g., intention to resist social engineering, security awareness, and training) of phishing. In contrast to (Sheng et al. (2010), they did not find a significant correlation between phishing behavior and age or gender in their study. They found significant positive correlations between employees’ observed phishing behavior and intention, security awareness, and training; however, the strength of correlations differed across different cultures (i.e., US, India, and Sweden). Correlations of both intention and security awareness to phishing behavior were not significant for American and Indian individuals but were for Swedish individuals. The correlation between training and phishing behavior was stronger for the American individuals compared to Swedish individuals and non-significant for Indian individuals.
Halevi, Lewis, and Memon (2013) used the five-factor model of personality to examine the relation between personality and vulnerability to phishing. The five behavior traits in this model are neuroticism, extroversion, openness, agreeableness, and conscientiousness. The authors sent a sample of 100 college students (83% male; ages 17-21) (benign) phishing emails with a malicious link. Specifically, they sent the sample an email that promised a prize of an Apple product to test the individuals’ susceptibility to phishing, and the authors considered that they had phished the participants if they clicked on the embedded link. Results showed that females were significantly more likely to be “phished” than men and that students high in neuroticism were more susceptible to the phishing attacks. While interesting, the research does not delve into the psychological reasons of the susceptibility or compare different motivators in susceptibility to phishing.
EFFECTS OF PHISHING ATTACKS ON ORGANIZATIONS
- Thefts of Intellectual Property: The images, reputations and websites of organizations is stolen and used for malicious acts. Phishers having succeeded in deceiving the users and captured sensitive information of the organization goes ahead and begin to use it against the policies and regulations of the company to get the attention of the clients of the organization.(Epsilon, a widely regarded marketing service frim, lost a considerable amount of proprietary data for over 50 customers.( https://www.truethreat.com/impacts-of-phishing-attacks)
- Loss of Confidential Employee and Customer Data: Org 10 as one of the case studies analyzed above, it was seen that customers were losing funds through fraud as a result of an email attachment that contains malicious Trojan that has the ability of getting the login credentials of the customers. Employees’ lack of privacy with their passwords brings about the organization loosing confidentiality in the employees.
- Decreased Revenues and Lower Market Share: an organization that has fallen victim of phishing attack will experience decrease in its revenue because its clients after being tricked loses interest in patronizing the company which in turn affects its return on investment. It could as well lead to the management resigning their appointments.
- Damage to Reputation and Trust: Phishing is one of the causes of security violation, therefore organizations must strive to guide against this threat as the goal of every organization is to protect its reputations and earn the trust of customers and its clients as good relationships increase sales and returns. In spite of that, an organization can lose its goodwill as a result of breach of security. Customer expects companies to take relevant measures to protect their data.
TECHNIQUES OF REDUCING PHISHING ATTACK
The height of Phishing problem has demanded researchers to help reduce the vulnerabilities of users. According to Purkait 2012, Anti-phishing techniques can be classified into the following:
WHAT WE KNOW
- Stop Phishing at the e-mail level
- Security and password management toolbars
- Visually differentiate the Phishing site
- Anti-Phishing training
- Legal Solutions
- Visual Based Similarity
- Baitalarm
WHAT WE DON’T KNOW OR STRUGGLING WITH
- Strong Antimalware
- Communication between parties involved
- Phishing Incident Management Policy
WHAT WE KNOW
STOP PHISHING AT THE E-MAIL LEVEL
The most popular means phishers adopt to trick the end-users is by sending e-mails across the internet and asking for web user’s bank account login details. These mails are sent with the intention of making it look legal in the sight of the users and making them believe it is from a trusted sites. The users are simply asked to visit a fake websites where they will be asked to input their login credentials and thereafter reap them of their financial benefits. As this is done, there is an approach that can be taken to stop these mails from getting to the users. According to Viswanath et al. (2011) the more e-mails that one receives, the more likely he is to be deceived. The risk is comparatively higher for the ones who not only receive but also respond to a large volume of e-mails. Organizations have responsibilities in protecting customers and employees (Users) by setting up spam filters that would categorize the emails into illegal and legal. With this kind of tool(spam filters), suspicious phishing e-mails are prevented from getting to their destinations(users).A lot of people has proposed means by which fraudulent emails can be stopped.(Garfinkel et al 2005 also suggested that internet users should adopt digitally signed mail as countermeasures for phishing e-mails. These digitally signed emails is encrypted and and uniquely identifies the sender.
SECURITY AND PASSWORD MANAGEMENT TOOLBARS
Passwords are meant to protect the accounts of users, but unfortunately most users give them away easily. Some users just because they don’t want the headache of putting so many passwords in mind, decides to use a passwords for multiple account which makes it easier for phishers. Gouda et al 2007 proposed anti-phishing single password protocol that allows a user to securely use a single password across multiple servers and also prevents phishing attacks. The users’ computers may contain some software based protection that manages the users’ passwords but they ignorantly disregard the functionality due to lack of knowledge.
VISUALLY DIFFERENTIATE THE PHISHING SITES
To help users differentiate between legal and illegal site, a dynamic security skins (DSS) a new class of human interactive proofs (HIPs) was proposed (Liu et al 2006). (Dhamija and Tygar,2005). DSS allows a remote web server to prove its identity in a way that is easy for a human user to verify and difficult for attacker. The user is able to identify its personal image and only inputs password when the image displays. If users fails to differentiate between an HTTP and a HTTPs session either due to ignorance, the proposed method is defeated.
ANTI-PHISHING TRAINING
This is the center of it all as it actively protect users from phishing threats. It is evident that phishing attacks is getting advanced even to the nearest future. Organizations needs to educate their employees on the potential risks of phishing. As technology increases, and become more universal, human remains the most vulnerable target for phishers. Training users on how best to respond to phishing attacks can reduce the success rate of the phishers. These trainings should be continuous as users tend to forget over time and the need to get updated to phishing techniques. Although educating user seem effective it cannot completely cure phishing attacks
LEGAL SOLUTION
Since Phishing has become part of the society and technology advancement, it is recommended that necessary legislation be put to place. Mcnealy 2008 examines the existing state laws in US aimed at stopping phishing attacks and the proposed federal legislation. He concluded that proper legal solutions would enable severe punishment on those caught phishing. By this, phishers are careful in their attacks. Victims of phishing attacks are also allowed to claim damage.
VISUAL BASED SIMILARITY
This operates on the principle of Visual Similarity Based Phishing Technique (VSBPT). Fishers usually like to imitate genuine websites that a lot of victim usually visit. During this process they try as much as possible for complete resemblance. The techniques they usually use are the font size, text and how the images of the genuine website appear. In as much as fishers are able to imitate the genuine website, sometimes there are no complete resemblance. With this the fake website is usually uses the same characteristics used by the phishers to imitate the original and when the slightest difference is spotted, then the user is given a warning that the website is a phishing website.
BAITALARM
Baitalarm is similar to Visual Based Similarity, it also analyzes the content, font and text to detect the phishing website. It evaluates both the content and the images of the websites. It is more reliable and has a better performance rate that the Visual Based Similarity because it goes further and compares the Cascading Style Sheets (CSS) of the two websites. This actually goes to compare the whole HTML elements that appears on the screen and therefore it is easier to detect a phishing website. This technique is more trusted than the VSBPT. Organizations and individuals prefer this because of the rate of performance as compared to all the techniques that operate on the basis of visual appearance of the content, font, text of all the two websites.
WHAT WE DON’T KNOW OR STRUGGLING WITH
STRONG ANTI-MALWARE
Anti-malware is now common in almost all organizations as it is used mainly in controlling phishing attack. However, most organizations have either weak antimalware or ones that are not up-to-date. Malware writers keep on altering the structure of the malware therefore antimalwares are either rewritten or updated regularly to combat the new types of malwares that are written consistently.
COMMUNICATION BETWEEN PARTIES
Most organizations have clients or customers whom they provide services to especially the financial institutions. Phishers are usually motivated by money and therefore they tend to attack financial institutions usually their clients. It is important that these institutions have consistent communication with their clients so that if one person gets attacked, they can get the information quickly and get to warn or pass the message to the other clients to prevent an extensive damage. This can also be done by the Abuse system where clients report all phishing mail to the organization and the other clients.
PHISHING INCIDENT MANAGEMENT POLICY
A phishing incident management policy should be provided by all organizations. This should be made known to users and customers. They should be trained and educated on the specific responsibilities that will be expected from them. The policy shall be updated regularly because as technologies are changing, phishing is also taking a different trend always. It should be a comprehensive management policy that can address all the problems associated with phishing including those encountered and those not encountered. This policy shall be made ready at all times and tested regularly. It is important to test the policies regularly to detect vulnerabilities so that when the controls are not effective it shall be made known and changed.
OTHER IMPORTANT TECHNIQUES
- Users should be educated on the deception of phishers by the use of pop-ups. Phishers have adopted a way of using pop-ups to deceive victims to steal their information. Organizations should train employees on which pop-ups are genuine. If possible, they should avoid it to make it easier for employees to detect that it is a phishing pop-up.
- Abuse box should be provided in all organizations so that phishing is detected at the early ages. When someone suspects that a particular email is a phishing email, he must send it to the abuse box so that it’s sent to everyone to prevent people from falling prey to that phishing email.
- People should be told that organizations will never ask for your credentials to confirm whether it’s right or wrong or to unsubscribe to a specific opportunity. When this happens whenever they see those emails or messages then they know it’s not authentic.
REFERENCES
1. Banu, M. N. and Banu, S. M. 2013. “A Comprehensive Study of Phishing Attacks,” International Journal of Computer Science and Information Technology (4:6), pp. 783-786.
2. Bimal Parmar, Faronics, “Protecting against spear-phishing”, Retrieved from: http://www.faronics.com/assets/CFS_2012-01_Jan.pdf
3. Clone Phishing – Phishing from Wikipedia, Retrieve from http://en.wikipedia.org/wiki/Phishing
4. Case Study: Attack Type – Phishing with Malware. Retrieved from: https://www.mwrinfosecurity.com/assets/Whitepapers/Case-Study-Phishing-with-Malware.pdf
5. Case Study: Fortune 50 Global Investment Firm Counters Phishing Threats With Isolation. Retrieved from: https://www.menlosecurity.com/phishing-isolation-case-study
6. Case Study: Royal Bank of Scotland Reduces Phishing Susceptibility for more than 78%. Retrieved from https://www.wombatsecurity.com/hubfs/Wombat%20Images/Resources/Case%20Study/Wombat_Print_RoyalBankScotlandCaseStudy_Feb2018.pdf
7. Case Study: Successful Phishing Attacks at a Northeastern US College Drop by 90%. Retrieved from https://info.wombatsecurity.com/hubfs/Case_Studies/Wombat_CaseStudy_NortheasternCollege_90PhishingReduction_Nov2017.pdf?t=1516133798154
8. Dhamija, R. and Tygar, J. D. 2005a. “Phish and HIPs: Human interactive proofs to detect Phishing attacks,” Proceedings of the 2nd International Workshop on Human Interactive Proofs (HIP), Human Interactive Proofs, Lecture Notes in Computer Science, (3517), pp. 127-141
9. Fetscherin, M. 2009. “Importance of cultural and risk aspects in music piracy: A cross-national comparison among university students,” Journal of Electronic Commerce Research (10), pp. 42-55
10. Florencio, D. and Herley, C. 2007. “ Evaluating a Trial Deployment of Password Re-use for Phishing Prevention,” Proceedings of the e-Crime Researchers Summit (New York, NY, USA, 2007), ACM Press, pp. 26–37.
11. Flores, W. R., Holm, H., Nohlberg, M. and Ekstedt, M. 2015. “Investigating Personal determinants of Phishing and the effect of national culture”, Information and Computer Security (23:2), pp. 178-199
12. Garfinkel, S. L., Margrave, D., Schiller, J. I., Nordlander, E. and Miller, R. C. 2005. “How to make secure e-mail easier to user”, Proceedings of the ACM Conference on Human Factors in Computing Systems, Portland, USA. Pp. 701-710
13. Gartner 2007. Retrieved from http://www.gartner.com/it/page.jsp?id=565125.
14. GARTNER RESEARCH. Number of Phishing E-Mails Sent to U.S. Adults Nearly Doubles in Just Two Years. Press Release, 2006. http://www.gartner.com/it/page.jsp?id=498245.
15. Hadnagy, C. 2011. “Social Engineering: The Art of Human Hacking,” Wiley Publishing; Indianapolis, USA. pp. 23-24
16. Halevi, T., Lewis, J. and Memon, N. 2013. “Phishing, Personality traits and Facebook” ArXIV Preprint arXiv:1301.7643v2
17. How a Major Bank Battled its Phishing: A Real World Case Study. Retrieved from: http://cdn2.hubspot.net/hub/241665/file-498740176 pdf/Malcovery_MAB_CaseStudy_(4).pdf?t=1391390748000
18. Imperva. Cross-Site scripting. Retrieved from http://www.imperva.com/Resources/Glossary?term=cross_site_scipting.
19. Jagatic, T., Johnson, N., Jakobsson, M. and Menczer, F. 2007. “ Social Phishing,” Communications of the ACM (50:10), pp. 94-100
20. John, “DNS-Based Phishing Attack in Public Hotspots”
21. Kaspersky Lab, Kaspersky security bulletin 2013. Retrieved from http://media.kaspersky.com/pdf/KSB_2013_en.pdf
22. Liu, W., Deng, X., Huang, G. and Fu, A. Y. 2006. “An anti-phishing strategy based on visual similarity assessment”, IEEE internet Computing (10:2) pp. 58-65
23. Mattias Eriksson, “An Example of a Man-in-the-middle Attack Against Server Authenticated SSL-sessions”
24. Mcnealy, J. 2008. “Angling for Phishers: Legislative responses to deceptive e-mail”, Communication Law and Policy (13:2), pp. 21-28
25. Moody, G., Galletta, D.F. Walker, J. and Dunn, B. K. 2011. “Which Phish get caught? An exploratory study of Individual Susceptibility to Phishing.” Proceedings of the International Conference on Information Systems
26. Moore, T., and Clayton, R. 2007. “ Examining the Impact of Website Take-down on Phishing,” Proceedings of the 2007 e-Crime Researchers Summit (New York, NY, USA, 2007), ACM Press, pp. 1–13
27. Payne, B. E. 2008. “A brief Introduction to usable security,” IEEE Internet Computing (12), pp. 13-21
28. Phone spoofing From Wikipedia, the free encyclopedia
http://en.wikipedia.org/wiki/Phishing#Phone_phishing
29. Sanjay, G., Kevin, W. and Ersin, D. 2017. “Got Phished? Internet Security and Human Vulnerability,” Journal of the Association of Information Systems (18:1), pp. 22-44
30. Sheng, S., Holbrook, M., Kumaraguru, P., Cranor, L. F. and Downs, J. 2010. “Who falls for Phish? A Demographic Analysis of Phishing Susceptility and Effectiveness of Interventions.” Proceedings of SIGCHI Conference on Human Factors in Computing Systems, pp. 373-382.
31. Shepherd, L. A., Archibald, J. and Ferguson, R. I. 2012. “Reducing Risky Security
Behaviours: Utilising Affective Feedback to Educate User,” Future Internet (6), pp. 760-772.
32. Stanton, J. M., Staim, K. R., Mastrangelob, P. and Jolton, J. 2005. “Analysis of end user security behaviours,” Computer Security (24), pp. 124-233.
33. Swapan, P. 2012. “ Phishing Countermeasures and their effectiveness- Literature review,” Information Management and Computer Security (20:5), pp. 382-420
34. Viswanath, A., Herath, T., Chen, R., Wang, J. and Rao, H. R. 2011. “Why do people get phished? Testing Individual differences in Phishing vulnerability within an integrated, Information Processing Model”,Decision support Systems (51:3), pp. 576-586
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




