Computer Intrusion and Intrusion Detection Systems
Info: 8216 words (33 pages) Dissertation
Published: 9th Dec 2019
CHAPTER ONE
LITERATURE REVIEW
- Computer Intrusion and Intrusion Detection Systems
Computer intrusion which is a process of illegitimately obtaining unauthorized access to a computer system is a huge problem in the current day and age. Numerous examples of major loss due to computer intrusion are published on a regular basis. This has over the years led to computer intrusion being one of the key research areas in the aspect of computer security and computer science in general. Intruders may exist in one of two ways ; internal intruders and external intruders. Internal intruders [32] are users who legitimately have access to the system or network and are trying to illegitimately increase their privileges in other to gain access to privileges they are not authorized to. When this happens, it is known as an ‘insider attack’. External intruders on the other hand are outside the network and have no privileges or user roles whatsoever but try to gain illegitimate unauthorized access to the computer network or system from outside the network.
The Ashley Madison hack[1] was one of the biggest cases of cyber intrusion that happened in 2015. About 9.7GB containing personal data and bank card information records of over 37 million people were exposed and dumped on the internet by a group of cyber criminals known as ‘Impact team’. This attack could approximately cost Ashley Madison about £1.2 billion in compensation in the U.K. alone. Between 2013 and 2015, an unknown group of cyber criminals attacked various cash machines across about 30 different countries and were able to get away with approximately $1billion. This was reported as the biggest bank robbery of 2015 by the UK business insider. Many other cases of intrusion were reported in 2015 including the breach of system of Anthem; a health insurer, exposing about 80 million personal records and some others as shown in Table 1.
In 2015 alone, the amount of computer related crime that occurred led to a loss of over $3 billion approximately and a leak of over 300 million data records.
| S/N | Target | Effect |
| 1. | Ashley Madison | Personal information and bank details of about 37 million people got exposed. |
| 2. | Cash Machines | About $1 billion of cash stolen from over 100 banks in over 30 countries. |
| 3. | Anthem Insurer | Nearly 80 million personal records were exposed |
| 4. | The White House | Intrusion into white house systems let to the access to unclassified white house documents and state department emails. Q |
| 5. | Experian | Information of about 15 million T-Mobile customers were stolen. |
| 6. | CIA Director John Brenan | Personal email hacked. Led to the leak of very sensitive documents. |
| 7. | VTech | Leak of records on about 4.8 million parents and over 6.8 million kids |
Table 1.1: Major attacks in 2015 [1]
While in this current day and age, it is quite a challenge to protect computer systems and data and provide secure information systems. Apart from computer hackers, there are also computer worms, computer viruses and Trojans which can be used in the implementation of covert channels and other type of means by which data can be stolen pose even as much security risks as computer hackers.
1.1.1 Intrusion Detection Systems
Intrusion Detection Systems are security tools that like other measures such as antivirus software, firewalls and access control schemes are intended to strengthen the security of information and communication systems. More specifically, intrusion detection systems aim at detecting attacks against computer systems and networks or in general, against information systems. While it is rather almost impossible to assure the 100% confidentiality and protection of systems, networks and data probably due to legacy or operational constraints, intrusion detection systems have the duty of monitoring the usage of systems to detect any apparition of insecure states. They detect attempts and misuse of legitimate user privileges in information systems or external parties to abuse privileges or exploit vulnerabilities. In general, a typical IDS comprises of sensors , an analysis engine and a reporting system. The task of the sensors is to collect data either from the network or host, depending on where the IDS is being deployed, such as traffic statistics, file-system changes, service requests, operating system calls and various other types of logs depending on the use of the system and configuration of the IDS. The analysis engine then receives the collected data from the sensors and analyses it to detect possible intrusions. If any intrusion is detected by the analysis engine, an alert is generated by the reporting system for the network or system administrator [33].
As shown by Khan and Jain and Suruna et al. in [18], [19] respectively, very many approaches of Intrusion detection systems have been proposed for various computing systems and networks. Morshedur [14] proposed an advanced hybrid intrusion detection system to detect malicious nodes in wireless sensor networks using fuzzy logic. In the paper, AHIDS makes utilization of cluster-based engineering with improved LEACH convention that plans to lessen the level of vitality utilization by the sensor nodes. AHIDS utilizes anomaly discovery and privilege abuse recognition in view of fuzzy control sets alongside the Multilayer Perception Neural Network. The Feed Forward Neural Network alongside the Backpropagation Neural Network are used to coordinate the detection results and show the diverse sorts of attackers. While this is an advancement in the field of detecting intrusion in wireless sensor networks, the method was only designed for and tested to work against hello flooding, wormhole and Sybil attacks in wireless network sensors.
Wenchao in [16] uses the K-nearest neighbour (KNN) classification algorithm for Wireless sensor networks. In this approach, the framework can separate strange or abnormal nodes from typical nodes by watching their unusual practices after which they examine parameter determination and blunder rate of the interruption discovery framework. The paper expounds on the plan and usage of the discovery framework. This framework achieved proficient, fast intrusion detection by enhancing the wireless, specially appointed on-request distance vector routing protocol (Ad hoc On-Demand Distance the Vector Routing, AODV).
While some researchers have attempted to utilize Bayesian strategy to take care of the interruption location issue. The primary thought behind this approach is the novel component of the Bayesian philosophy. For a given outcome, utilizing the likelihood calculations, Bayesian strategy can move back in time and discover the reason for the events. This element is appropriate for finding the purpose behind a specific anomaly in a system behaviour. Utilizing Bayesian calculation, frameworks can by one means or another move back in time and discover the reason for the events. The Bayesian algorithm is in some cases also utilized clustering purposes. [6, 7,8] are examples of this method.
More advanced work has been carried out on intrusion detection using various methods over the years. Other notable systems proposed also include [14, 15, 4,5] and very many others.
- Description and Architecture of Intrusion Detection Systems
The initial step to securing a network or information system is to have the capacity to identify an attack. An attack can be characterized as a succession or sequence of operations, events or occurrences that puts the security of a framework or system at risk. Regardless of the possibility that the detection framework can’t keep the attacker from getting into the framework, seeing the interruption will give the security officer or anyone in charge significant data. The intrusion discovery can be viewed as the main line of safeguard for any security framework. An intrusion detection system gets data about an information system or network on which it is deployed to play out a finding on the security status of the information system or network, as the case may be. The objective is to find ruptures of security, endeavoured breaks, or open vulnerabilities that can prompt potential security. The major functions of an IDS are:
- Data collection
- Data Analysis
Data collection in this sense might refer to data or system logs, network traffic, etc. and its analysis might be in form of pattern matching, information mining, measurable statistical investigation or analysis, etc. An IDS can be depicted at an extremely plainly visible level as a detector that processes data originating from the information system to be ensured. This detector can likewise dispatch tests to trigger an audit procedure. It utilizes three sorts of data: long-term data identified with the strategy used to identify intrusions, configuration information about the present condition of the information system and audit information depicting the events that are occurring on the system.
In 1998, the Defence Advanced Research Projects Agency (DARPA); an agency of the United States of America Department of Defence responsible for the development of new technology for the military created a working group; “Common Intrusion Detection Framework” (CIDF) whose main objective was to create a common framework for the intrusion detection system (IDS) field. In 2000, the group now named “Intrusion Detection Working Group” (IDWG) characterized a general IDS engineering considering four sorts of practical modules (also shown in Figure 1):
- E blocks (“Event-boxes”): This sort of block is made up of sensor components that screen the target system, therefore procuring information events or occurrences to be examined by other blocks.
- D blocks (“Database-boxes”): These are components planned to store information from E-blocks for future processing by A boxes and R boxes.
- A blocks (“Analysis-boxes”): Preparing modules for analysing events and identifying potential abnormal behaviour, so that some sort of alert will be generated if necessary.
- R blocks (“Responsive-boxes”): The primary job of this kind of block is the execution. If any intrusion happens, its work is to prevent the intruder from successfully achieving it’s aim.
Depending on the type of information system source i.e the E-boxes, an intrusion detection system may either be host based or network based. A host based intrusion detection system
investigates events basicly in relation to the Operating System information for example, system calls and process information. A network based intrusion detection system on the other hand investigates events related to the network say for example, IP addresses, protocol usage, etc. Depending on what type of analysis is carried out by the analysis block, intrusion detection systems can be classified as ‘signature-based’, ‘anomaly-based’ or ‘specification-based’.
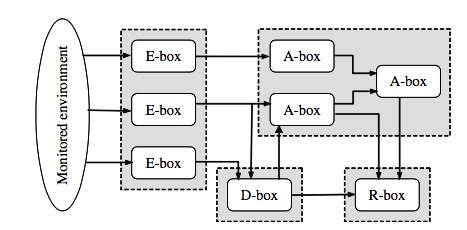
Figure 1: CIDF framework for IDS Systems (Garcia-Teodoro,[66])
- Signature Based , Anomaly Based and Specification Intrusion Detection System:
Signature based intrusion detection systems (also called misuse based) look for characterized examples or marks, inside the investigated information. As soon as a novel attack is propelled, the attack pattern is deliberately considered and studied, and a signature is characterized for it. The signature can be a name inside the body of the attack code, the resources targeted by the attack or the way in which these resources are attacked. By examining the attack patterns, security authorities can outline a barrier against it. Later on, utilizing the proposed defence technique, the IDS is refreshed as needs be to perceive the new attack patterns and to react to them. They apply the information amassed about particular attacks and system vulnerabilities. This sort of IDS contains data about these vulnerabilities and searches for endeavours to exploit them. At the point when such is identified, an alarm is raised. As it were, any activity that is not unequivocally perceived as an intrusion or attack is viewed as adequate and acceptable. In this way, the accuracy; which is the proper detection of attacks and the absence of false alerts, of this sort of IDS is considered good. Notwithstanding, the property of the IDS to recognize any attacks relies on upon the general update of information about attacks.
Signature based IDS give great detection results for specific, well known attacks. Be that as it may, they are not fit for identifying new, new intrusions, regardless of the possibility that they are worked as least variants of definitely known attacks. Many researchers have used this method to carry out various experiments and propose solutions for various problems. Notable is [9] which used this method to propose a centralized control signature-based firewall and statistical-based network intrusion detection system (NIDS) in software Defined Networks (SDN). Signature based IDS is an effective and simple method to detail known attacks and they also detail contextual analysis. While more research has been made to improve the strength of signature based IDS by very many researchers, such as [10] and[11] , more work is still needed in that aspect as the overall development has not really changed much. Overall, This kind of identification is extremely compelling against known attacks, and it relies on upon the accepting of customary updates of examples and will be not able identify obscure past dangers or new discharges.
The benefits of the signature based methodologies are that they have, in principle, low false-alert rates, and that the logical examination or better still, contextual analysis proposed by the IDS is point by point, making it less demanding for the security officer utilizing this IDS to understand the issue and to make preventive or remedial move. It is additionally the most straightforward yet exceptionally successful strategy to distinguish known attacks.
The downsides of the signature based IDS however include the trouble of collecting the required data about known attacks and staying up with the latest vulnerabilities and environments. Upkeep of the learning base of the IDS requires careful investigation of every vulnerability and is hence a tedious and time-consuming job. Signature-based methodologies likewise need to confront the speculation issue. Learning about attacks emphatically relies on upon the working framework, operating system, rendition and application. The subsequent IDS is consequently firmly attached to a given environment. Likewise, detection of insider attacks including an abuse of privileges is considered more difficult on the grounds that no vulnerability is really exploited by the malicious user. The signature based IDS also has little understanding to states and protocols. [28,29,30] show various implementations of signature based IDS in various ways.
Expert Systems [12] are essentially utilized by signature-based IDS methods. This framework contains an arrangement of standards and rules that portray attacks. Audit events are then converted into actualities conveying their semantic implication in the expert system, and the inference engine makes determinations and conclusions utilizing these rules. Rule-based languages [13] are a natural tool for modelling the information that specialists have gathered about attacks. This approach permits an efficient perusing of the audit trail, looking for proof of endeavours to take advantage of known vulnerabilities. They are additionally used to check the best possible utilization of the security approach of an organization. Others that fall in this category are description languages and the finite-state-machine (FSM)
An anomaly can be described as a deviation from a known pattern or behaviour. Defining it from the viewpoint of security however, it can be defined as a suspicious event. In anomaly based intrusion detection systems, intrusions are detected by observing the deviation from the normal behaviour of a user or system at runtime. The model of usual or normal conduct is generally gotten from reference data gathered by different means usually by machine learning; by observing standard activities, host or clients over a timeframe, etc. The IDS then compares this pattern with the current scenario or activity. One of the major pros of the anomaly based detection system is its ability to detect new vulnerability exploits. Apart from their less dependency on operating-system-specific-mechanisms, they can also detect insider attacks or privilege abuse that do not necessarily involve any vulnerability exploitation. . The advantage of anomaly based IDS is that they can detect new forms of intrusions and maliciousness since they do not look for anything specific. Anomaly based IDS are however very prone to high false positives. Hall et al. in [26] researched an anomaly based method that turned out to with 100% false positives.
A lot of research work has been done in the area of intrusion detection using anomaly based methods basically because they are very flexible and they have the ability to adapt on their own. Chandola et al.[27] is a survey of anomaly based intrusion detection that cut across several applications and areas. [20],[21],[22],[23],[24] also how several uses of different types of machine learning techniques in detecting various types of intrusions in several areas and aspects of life.
Specification Based intrusion detection systems are quite unique. As described by Brutch in [25], they look for unusual performances in system levels. This is quite different from anomaly based intrusion detection since anomaly based are more consigned with data flows and user profiles. One of the pros of this type is its very low false positives. Only incidences that deviate from what has been previously defined usually by a human expert as proper system behaviour will generate alerts. Another key advantage is that there is no training or profiling of any form required hence the system is effective immediately. Specification based IDS however requires a lot of effort in generating its formal specification. They are also not very useful in defending against external intrusions because their specifications are only application specific hence, they can be used to defend against only actions that can be taken by insiders. Puri in [31] presents atypical use of specification based IDS.
- Role Based Access Control
Access control restricts what a user can do specifically, and in addition what programs executing for the user are permitted, by following laid down rules and configured settings. by doing this, access control aims at counteracting any action that could prompt a break of security [34]. There are three primary types of access control; Discretionary Access Control (DAC), Mandatory Access Control (MAC), and Role-Based Access Control (RBAC).
In the Discretionary Access control, the owner of an object in the system (for example a file) has complete authority over who my gain access to it. As evident in Loscocco [35] these kinds of systems are nearly impossible to secure. Systems with discretionary access control are open to various forms of abuse and misconfigurations. A perfect example of this system is the Access Control Lists [36].
In Mandatory Access control, owners of an object are not permitted to have a say in who or what processes have access to it. The rights to access an object is left to the operating system and can not be adjusted by any user. It typically groups all users and assigns them labels which establish security guidelines and then permit them to gain access to it depending on what clearances are stated on their labels. It is a way by which access to objects are restricted based on sensitivity. Loscocco’s argument in [35] is that since the mandatory access control is implemented in the operating system level, it is impossible to tamper with or change, hence it provides better security.
Role Based Access control(RBAC) which is also called non-discretionary access control [37], [38] are one of the best, most secure and successful technologies in access control. This is in short, confirmed by [39]. RBAC is basically an extension of mandatory access control but is not based on any multi-level security requirement unlike the MAC. In most organizations where security is taken seriously, control and access to different parts of the entire system is often based on employee functions. Decisions about access control are frequently controlled by the roles users are employed for in an organization. This incorporates the detail of obligations, duties and capabilities in making its decision.
A role can be described as a group of transactions that a particular user or set of users are given permission to perform within an organization. These transactions are allotted to roles only by the system administrator which itself is a role. For instance, the roles an individual related with a university can be assumed to include lecturer, head of department, dean, vice chancelor, student, registrar, Liberian, IT administrator. Roles can likewise apply to hospitals such as doctors, nurses, pharmacist, accountant. A RBAC policy constructs access control decisions based on what functions a user is permitted to perform inside an organisation. The users can’t pass access permissions on to other users at their discretion. This is the fundermental distinction amongst RBAC and DAC. It should be noted however, that a role is not given simply at the discretion of an Administrator but solely determined by the user’s function in an organization.
In several applications of it’s use, RBAC is connected to function’s access. An is [41]. In a RBAC, the basic aim is to protect the integrity of information: “Who can perform what on information”.
RBAC is widely used in but not limited to commercial and military systems. Schaad et al. [40] describes a role based access control system for a European bank. Hansen and Oleshuhk [42] also discuss the application of role-based access control in wireless healthcare information systems. Silva et al. [43] also proposes a self-adaptive role based access control for business process.
- Formal Description of RBAC
The original formal description of RBAC given by Ferraiolo and Kuhn [44] is presented as follows in Table 1.2:
| For each subject, the active role is one that the subject is currently using:
AR(s: subject) = {the active role for subject s} |
| Each subject may be authorized to perform one or more roles:
RA(s: subject) = {authorized roles for subject s } |
| Each role may be authorized to perform one or more transactions:
TA(r : role) = {transactions authorized for role r} |
| Subjects may execute transactions. The predicate exec(s,t) is true if and only if subject s can execute transaction t at a current time, otherwise it is false:
exec(s:subject, t:train)= {true iff subject s can execute transaction t}
Three basic rules are required:
s: subject, t: tran, (exec(s,t) AR(s) ). The identification and authentication process (e.g. login) is not considered a transaction. All other user activities on the system are required to have some active role.
s: subject,(AR(s) RA(s)). With (1) above, this rule ensures that users can take on only roles for which they are authorized.
s: subject, t: tran, (exec(s,t) t TA(AR(s))). |
| With (1) and (2), this rule ensures that users can execute only transactions for which they are authorized. Note that, because the conditional is “only if”, this rule allows the possibility that additional restrictions may be placed on transaction execution. That is, the rule does not guarantee a transaction to be executable just because it is in TA(AR(s)), the set of transactions potentially executable by the subject’s active role. For example, a trainee for a supervisory role may be assigned the role of “Supervisor”, but have restrictions applied to his or her user role that limit accessible transactions to a subset of those normally allowed for the Supervisor role. |
Table 1.2: Formal Description of RBAC as given by Ferraiolo and Kuhn [44]
Over the years, more research work has been done to improve effectiveness of RBAC. Silva et al. [43] introduces self-adaptation into role based access control for business processes; [45],[46],[47] and [48] proposes standard models for the implementation of RBAC; [49] carries out a cryptographic implementation of RBAC in cloud storage and [50] applies it in privacy preservation.
Role Based access control is however largely dependent on whatever parameters applied and configurations set by the by the system administrator The degree to which data abstraction is also supported will be determined by the details of implementation.
- Security Principles of RBAC
RBAC basically supports and makes use of three computer security’s well known Principles:
- Principle of Least Privilege: This is a very important principle of information integrity will be met. The principle of least privilege requires that only the permissions required to carry out a user’s tasks be assigned to the user’s role and nothing more. By using RBAC, enforcing minimum privileges on system users can be easily achieved
- Separation of Duties: Separation of duties is a useful way of preventing fraud. To complete a sensitive task, such as asking an accounting clerk and an account manager to issue a check, invoking mutually exclusive roles can be required. By separating duties in a particular set of transactions, no individual should be able to execute all transactions within the set.
- Data Abstraction: In place of the read, write and execute permissions typically provided by the operating system, abstract permissions such as credit and debit for an objuct cannot be established.
- Discrete Time Markov Chains.
According to [51], “A Markov model consists of a network of conformational states and a transition probability matrix describing the chances of jumping from one state to anotherin some small time interval.” . According to [53], A stochastic process in discrete time
n
N={0,1,2,…} is a sequence of random variables (rvs) X0, X1, X2,. . . denoted by X = {Xn :n 0} (or just X = {Xn}). The value Xn is refered to as the state of the process at time n with X0 representing the initial state. If the random variables take values in a discrete space such as the integers
Z = {. . . , -2, -1, 0, 1, 2, …} (or some subset of them), then the stochastic process is said to be discreet-valued; we then denote the states i, j and so on. Generally speaking, the collection of possible values that the Xn can take on is called the state space, is denoted by
Sand could be, for example, d- dimensional Euclideon space
Rd ,
d 1, or a subset of it.
A Stochastic process is intended to demonstrate the development or evolution of a real situation in which randomness is expected [53].
- Formal representation of Discrete Time Markov Chains
- Previous Use of Markov chains outside Intrusion Detection and Computer Security
As earlier discussed in this literature review, machine learning has been widely used for various detection and research schemes in computer science. Markov models have been used for various sorts of predictions hence a very good model that can b used for detecting anomaly. This section aims to discuss a few other research works that has been carried out using markov chains for various solutions both in information security and other life applications.
Razavi [53] combined the the markov chain model with artificial neural network to predict the trend of land use changes. Singer et al. [54] also used markov chain models of varying order to detect memory and structure in human navigation patterns. In the area of healthcare, Anderson et al. [55] designed a system to optimize hospital ward resources with patient relocation using markov chain modelling. Pandey and Hong [56] were able to design a framework to explore que behaviour in cloud buffers. Xiong et al. [57] successfully proposed a system to predict effective human promotion based on DNA structures. Rastogi et al. [58] recently also came up with a system to predict fault crack growth in nuclear piping and [59] also recently proposed a model for daily network tomography using a partially observable bivariate markov chain. Some other spectacular research done using markov chain outside the area of computer security and intrusion detection include [60,61,62,63] and [64].e
- Previous use of Markov models in intrusion detection
Yassine et al. [65] proposed a model to detetect xebsite vulnerabilities by using markov chains. Their method applied propabilistic approach for an intelligent IDS whose major job was to tell which pages of aa website are most likely to be attacked and also show security weaknesses according to the real time probabilistic calculation based on Markov chains.
Although Linux systems are known to be quite safe compared to other operating systems, Zhang et al. in [67] proposed a new mechanism to detect intrusion in SELinux by integrating access control with intrusion detection by Linux Security Module (LSM) and takes into cognisance both the global behaviour characteristics and local behaviour characteristics. At the end of their research, the mechanism was able to integrate access control and intrusion detection and get a reasonable efficiency of intrusion detection.
Ariyapala et al. [68] also came up with a host and network based intrusion detection system for android smartphones. In the system, a mobile application is developed to capture host-based features such as CPU usage , battery consumption, running processes, network connections , user activity and network traffic. The monitored data were then sent to a processing server for analysis to relieve the smartphone from the processing burden. The system used netflow based clustering to identify anomalies and correlated further with a the host based features to verify malicious intrusions in android systems.
Other noteworthy intrusion detection methods using markov model include [69], [70],[71], [72]
References
- https://www.itgovernance.co.uk/blog/list-of-data-breaches-and-cyber-attacks-in-2015-over-275-million-leaked-records/?source=aw&awc=6072_1494604880_7ed6bff7621a9806d165d26735e71768&utm_source=AffWin&utm_medium=78888&utm_campaign=0
- Zarpelão, B. B., Miani, R. S., Kawakani, C. T., & de Alvarenga, S. C. (2017). A Survey of Intrusion Detection in Internet of Things. Journal of Network and Computer Applications.
- Jagrati sharma, Ishika saraf, Nishima puri, Bhavna Navin, Jayesh Surana, “A Survey On Intrusion Detection System”, International Journal of Engineering Development and Research (IJEDR), ISSN:2321-9939, Volume.5, Issue 2, pp.960-965, May 2017, Available at :http://www.ijedr.org/papers/IJEDR1702161.pdf
- Feng, W., Zhang, Q., Hu, G., & Huang, J. X. (2014). Mining network data for intrusion detection through combining SVMs with ant colony networks. Future Generation Computer Systems, 37, 127-140.
- Ashfaq, R. A. R., Wang, X. Z., Huang, J. Z., Abbas, H., & He, Y. L. (2017). Fuzziness based semi-supervised learning approach for intrusion detection system. Information Sciences, 378, 484-497.
- Xiao, L., Chen, Y., & Chang, C. K. (2014, July). Bayesian model averaging of bayesian network classifiers for intrusion detection. In Computer Software and Applications Conference Workshops (COMPSACW), 2014 IEEE 38th International (pp. 128-133). IEEE.
- Muda, Z., Yassin, W., Sulaiman, M. N., & Udzir, N. I. (2016). K-Means Clustering and Naive Bayes Classification for Intrusion Detection. Journal of IT in Asia, 4(1), 13-25.
- Xu, J., & Shelton, C. R. (2014). Intrusion detection using continuous time bayesian networks. arXiv preprint arXiv:1401.3851.
- Mantur, B., Desai, A., & Nagegowda, K. S. (2015). Centralized Control Signature-Based Firewall and Statistical-Based Network Intrusion Detection System (NIDS) in Software Defined Networks (SDN). In Emerging Research in Computing, Information, Communication and Applications (pp. 497-506). Springer India.
- Kruegel, C., & Toth, T. (2003, September). Using decision trees to improve signature-based intrusion detection. In International Workshop on Recent Advances in Intrusion Detection (pp. 173-191). Springer Berlin Heidelberg.
- Haagdorens, B., Vermeiren, T., & Goossens, M. (2004, August). Improving the performance of signature-based network intrusion detection sensors by multi-threading. In International Workshop on Information Security Applications (pp. 188-203). Springer Berlin Heidelberg.
- Liao, S. H. (2005). Expert system methodologies and applications—a decade review from 1995 to 2004. Expert systems with applications, 28(1), 93-103.
- Vianu, V. (1997). Rule-based languages. Annals of Mathematics and Artificial Intelligence, 19(1-2), 215-259.
- Morshedur, H. (2013). Network Intrusion Detection System Using Genetic Algorithm and Fuzzy Logic. In International Journal of Innovative Research in Computer and Communication Engineering, 1(7) (pp. 1435-1445)
- Dawle, Y. (2017). Database Security Using Intrusion Detection System. In International Journal of Latest Engineering Research and Applications, 2(3) (pp. 1-6)
- Wenchao ,L et al (2014). A New Intrusion Detection System Based on KNN Classification Algorithm in Wireless Sensor Network,” Journal of Electrical and Computer Engineering, Article ID 240217, 8 pages
- Singh, R., Singh, J., Singh, R. (2017). “Fuzzy Based Advanced Hybrid Intrusion Detection System to Detect Malicious Nodes in Wireless Sensor Networks”, Hindawi Wireless Communications and Mobile computing, Article ID 3548607, 14 pages
- Khan,J., Jain, N., (2016). “A Survey on Intrusion Detection Systems and Classification Techniques)”, International Journal of Scientific Research in Science, Engineering and Technology, 2(5) (pp. 202-208)
- Surana, J., Sharma, J., Saraf, I., Puri, N., Navin, B. (2017). “ A Survey on Intrusion Detection System”, International Journal of Engineering Development and Research , 5(2), (pp. 960-965)
- Ford, V., Siraj, A., & Eberle, W. (2014, December). Smart grid energy fraud detection using artificial neural networks. In Computational Intelligence Applications in Smart Grid (CIASG), 2014 IEEE Symposium on (pp. 1-6). IEEE.
- Van Vlasselaer, V., Bravo, C., Caelen, O., Eliassi-Rad, T., Akoglu, L., Snoeck, M., & Baesens, B. (2015). APATE: A novel approach for automated credit card transaction fraud detection using network-based extensions. Decision Support Systems, 75, 38-48.
- Vidyasagar, M. (2015). Identifying predictive features in drug response using machine learning: opportunities and challenges. Annual review of pharmacology and toxicology, 55, 15-34.
- Jokar, P., Arianpoo, N., & Leung, V. C. (2016). Electricity theft detection in AMI using customers’ consumption patterns. IEEE Transactions on Smart Grid, 7(1), 216-226.
- Sharma, C., Sabharwal, S., & Sibal, R. (2014). A survey on software testing techniques using genetic algorithm. arXiv preprint arXiv:1411.1154.
- Brutch, P., & Ko, C. (2003, January). Challenges in intrusion detection for wireless ad-hoc networks. In Applications and the Internet Workshops, 2003. Proceedings. 2003 Symposium on (pp. 368-373). IEEE.
- Hall, J., Barbeau, M., & Kranakis, E. (2005, August). Anomaly-based intrusion detection using mobility profiles of public transportation users. In Wireless And Mobile Computing, Networking And Communications, 2005.(WiMob’2005), IEEE International Conference on (Vol. 2, pp. 17-24). IEEE.
- Chandola, V., Banerjee, A., & Kumar, V. (2009). Anomaly detection: A survey. ACM computing surveys (CSUR), 41(3), 15.
- Han, H., Lu, X. L., & Ren, L. Y. (2002). Using data mining to discover signatures in network-based intrusion detection. In Machine Learning and Cybernetics, 2002. Proceedings. 2002 International Conference on (Vol. 1, pp. 13-17). IEEE.
- Foo, B., Wu, Y. S., Mao, Y. C., Bagchi, S., & Spafford, E. (2005, June). ADEPTS: Adaptive intrusion response using attack graphs in an e-commerce environment. In Dependable Systems and Networks, 2005. DSN 2005. Proceedings. International Conference on (pp. 508-517). IEEE.
- Lin, Y., Zhang, Y., & Ou, Y. J. (2010, April). The design and implementation of host-based intrusion detection system. In Intelligent Information Technology and Security Informatics (IITSI), 2010 Third International Symposium on (pp. 595-598). IEEE.
- Puri, A., & Sharma, N. (2017). A NOVEL TECHNIQUE FOR INTRUSION DETECTION SYSTEM FOR NETWORK SECURITY USING HYBRID SVM-CART.
- Colombe, J. B., & Stephens, G. (2004, October). Statistical profiling and visualization for detection of malicious insider attacks on computer networks. In Proceedings of the 2004 ACM workshop on Visualization and data mining for computer security (pp. 138-142). ACM.
- Debar, H. (2000). An introduction to intrusion-detection systems. Proceedings of Connect, 2000.
- Sandhu, R. S., & Samarati, P. (1994). Access control: principle and practice. IEEE communications magazine, 32(9), 40-48.
- Loscocco, P. A., Smalley, S. D., Muckelbauer, P. A., Taylor, R. C., Turner, S. J., & Farrell, J. F. (1998, October). The inevitability of failure: The flawed assumption of security in modern computing environments. In Proceedings of the 21st National Information Systems Security Conference (Vol. 10, pp. 303-314).
- Shalabi, S. M., Doll, C. L., Reilly, J. D., & Shore, M. B. (2011). U.S. Patent Application No. 13/311,278.
- Suhendra, V. (2011, December). A survey on access control deployment. In International Conference on Security Technology (pp. 11-20). Springer Berlin Heidelberg.
- Park, S. H., Han, Y. J., & Chung, T. M. (2006, September). Context-role based access control for context-aware application. In International Conference on High Performance Computing and Communications (pp. 572-580). Springer Berlin Heidelberg.
- Sahafizadeh, E., & Parsa, S. (2010, May). Survey on access control models. In Future Computer and Communication (ICFCC), 2010 2nd International Conference on (Vol. 1, pp. V1-1). IEEE.
- Schaad, A., Moffett, J., & Jacob, J. (2001, May). The role-based access control system of a European bank: a case study and discussion. In Proceedings of the sixth ACM symposium on Access control models and technologies (pp. 3-9). ACM.
- Griffin, P., Cole, G., & Wilson, G. (2001). U.S. Patent Application No. 09/864,392.
- Hansen, F., & Oleshchuk, V. (2003, June). Application of role-based access control in wireless healthcare information systems. In Scandinavian Conference in Health Informatics (pp. 30-33).
- da Silva, C. E., da Silva, J. D. S., Paterson, C. A., & Calinescu, R. C. (2017). Self-Adaptive Role-Based Access Control for Business Processes. In 12th International Symposium on Software Engineering for Adaptive and Self-Managing Systems (SEAMS 2017). IEEE.
- Ferraiolo, D., Kuhn, D. R., & Chandramouli, R. (2003). Role-based access control. Artech House.
- Sandhu, R., Ferraiolo, D., & Kuhn, R. (2000, July). The NIST model for role-based access control: towards a unified standard. In ACM workshop on Role-based access control (Vol. 2000, pp. 1-11).
- Bertino, E., Bonatti, P. A., & Ferrari, E. (2001). TRBAC: A temporal role-based access control model. ACM Transactions on Information and System Security (TISSEC), 4(3), 191-233.
- Ferraiolo, David F., Ravi Sandhu, Serban Gavrila, D. Richard Kuhn, and Ramaswamy Chandramouli. “Proposed NIST standard for role-based access control.” ACM Transactions on Information and System Security (TISSEC) 4, no. 3 (2001): 224-274.
- Joshi, J. B., Bertino, E., Latif, U., & Ghafoor, A. (2005). A generalized temporal role-based access control model. IEEE Transactions on Knowledge and Data Engineering, 17(1), 4-23.
- Zhou, L., Varadharajan, V., & Hitchens, M. (2014). Secure administration of cryptographic role-based access control for large-scale cloud storage systems. Journal of Computer and System Sciences, 80(8), 1518-1533.
- Abdella, J., Özuysal, M., & Tomur, E. (2016). CA‐ARBAC: privacy preserving using context‐aware role‐based access control on Android permission system. Security and Communication Networks, 9(18), 5977-5995.
- Bowman, G. R., Pande, V. S., & Noé, F. (Eds.). (2013). An introduction to Markov state models and their application to long timescale molecular simulation (Vol. 797). Springer Science & Business Media.
- Sigman, K., (2009). Discrete-time Markov Chains.
- Razavi, B. S. (2014). Predicting the trend of land use changes using artificial neural network and markov chain model (case study: Kermanshah City). Research Journal of Environmental and Earth Sciences, 6(4), 215-226.
- Singer, P., Helic, D., Taraghi, B., & Strohmaier, M. (2014). Detecting memory and structure in human navigation patterns using markov chain models of varying order. PloS one, 9(7), e102070.
- Andersen, A. R., Nielsen, B. F., & Reinhardt, L. B. (2017). Optimization of hospital ward resources with patient relocation using Markov chain modeling. European Journal of Operational Research, 260(3), 1152-1163.
- Pandey, S. R., & Hong, C. S. (2016). Exploring Queue Behavior in Local Cloud Buffer Using Markov Chain. 한국정보과학회학술발표논문집, 1039-1041.
- Xiong, D., Liu, R., Xiao, F., & Gao, X. (2014). ProMT: Effective Human Promoter Prediction Using Markov Chain Model Based on DNA Structural Properties. IEEE transactions on nanobioscience, 13(4), 374-383.
- Rastogi, R., Ghosh, S., Ghosh, A. K., Vaze, K. K., & Singh, P. K. (2017). Fatigue crack growth prediction in nuclear piping using Markov chain Monte Carlo simulation. Fatigue & Fracture of Engineering Materials & Structures, 40(1), 145-156.
- Rastogi, R., Ghosh, S., Ghosh, A. K., Vaze, K. K., & Singh, P. K. (2017). Fatigue crack growth prediction in nuclear piping using Markov chain Monte Carlo simulation. Fatigue & Fracture of Engineering Materials & Structures, 40(1), 145-156.
- Khan, A. J., Rafique, R., Zafar, W., Shah, C., Haffty, B. G., Vicini, F., … & Zhao, Y. (2017). Nation-Scale Adoption of Shorter Breast Radiation Therapy Schedules Can Increase Survival in Resource Constrained Economies: Results From a Markov Chain Analysis. International Journal of Radiation Oncology* Biology* Physics, 97(2), 287-295.
- Suzuki, T., Tani, Y., & Ogasawara, K. (2016). Behavioral Analysis of Visitors to a Medical Institution’s Website Using Markov Chain Monte Carlo Methods. Journal of medical internet research, 18(7).
- Frühwirth-Schnatter, S., Pittner, S., Weber, A., & Winter-Ebmer, R. (2016). Analysing Plant Closure Effects Using Time-Varying Mixture-of-Experts Markov Chain Clustering.
- Rezaeianzadeh, M., Stein, A., & Cox, J. P. (2016). Drought forecasting using Markov chain model and artificial neural networks. Water Resources Management, 30(7), 2245-2259.
- MOdestus, O., Nwaoha, T., Olabisi, A. I., & Benjamin, E. (2017). ACCIDENT CAUSATIVE MODEL IN THE OIL AND GAS CONURBATION USING MARKOV CHAIN. International Journal of Scientific Research in Information Systems and Engineering (IJSRISE), 2(1).
- Yassine, A., Noureddine, R., Ettifouri, E. H., Berrich, J., & Toumi, B. (2016, September). Detecting xebsite vulnerabilities based on Markov chains theory. In Multimedia Computing and Systems (ICMCS), 2016 5th International Conference on (pp. 697-700). IEEE.
- Garcia-Teodoro, P., Diaz-Verdejo, J., Maciá-Fernández, G., & Vázquez, E. (2009). Anomaly-based network intrusion detection: Techniques, systems and challenges. computers & security, 28(1), 18-28.
- Zhang, R., Liu, G., Yuan, X., Ji, S., & Zhang, G. (2016, October). A New Intrusion Detection Mechanism in SELinux. In System and Software Reliability (ISSSR), International Symposium on (pp. 53-58). IEEE.
- Ariyapala, K., Do, H. G., Anh, H. N., Ng, W. K., & Conti, M. (2016, March). A Host and Network Based Intrusion Detection for Android Smartphones. In Advanced Information Networking and Applications Workshops (WAINA), 2016 30th International Conference on (pp. 849-854). IEEE.
- Ma, Z., Liang, Y., & Zhu, J. (2017). An optic-fiber fence intrusion recognition system using mixture Gaussian hidden Markov models. IEICE Electronics Express, 14(5), 20170023-20170023.
- Song, Y., Keromytis, A. D., & Stolfo, S. J. (2016). U.S. Patent No. 9,253,201. Washington, DC: U.S. Patent and Trademark Office.
- Cha, K. H., & Kang, D. K. (2017). Experimental analysis of hidden Markov model based secure misuse intrusion trace classification and hacking detection. Journal of Computer Virology and Hacking Techniques, 1-6.
- Rahmoun, N., Saber, M., Ettifouri, E., Zeaaraoui, A., & Bouchentouf, T. (2016). A New Approach to Detect WEB Attacks Senario in Intrusion Detection System. In Proceedings of the Mediterranean Conference on Information & Communication Technologies 2015 (pp. 569-573). Springer International Publishing.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




