Development of an Internet-based Web Application for an Electronic Voting System
Info: 10554 words (42 pages) Dissertation
Published: 22nd Dec 2021
Tagged: Information TechnologyPolitics
Abstract
This report outlines the process undertaken in developing an internet-based web application for an electronic voting system including the techniques and methods involved. The report discusses evidence-based approach in providing a solution to the voting process that is sufficiently secure and can be trusted by the electorate, in this case, the students. With the rise of the need for such systems in the internet technology evolving world this report outlines e-voting is best realised through the use of a web application.
Table of Contents
Click to expand Table of Contents
Introduction
Academic Question
Aims
Objectives
Artefact
Chapter Two: Literature Review
History
Benefits
Problems
Security
Voter related security issues
Server Side Security Concerns
Connection Security Issues
Verifying Electronic Voting
Chapter Three: Development of the Artefact
Overview of the Artefact Basic Structure and Working
Software Development Life Cycle
Research and selection of the Artefact
Artefact Development Tools – programming languages
PHP and MySQL
HTML 5 AND CSS 3
Elements in the Artefact
Artefact Design and Implementation
Login Page
Registration page
Voting page
Vote tab
Result tab
Testing of the Artefact
User Errors
Vulnerabilities testing
Injection
Broken Authentication
Sensitive data exposure
XML External Entities
Broken Access control
Security Misconfiguration
Cross Site Scripting, XSS
Insecure Deserialization
Using components with known vulnerabilities
Insufficient logging and Monitoring
Chapter Five: Conclusions
Evaluation of the product
Self-reflection
Introduction
Academic Question
The academic question this report thrives on answering is how to stop security threats in electronic in electronic voting systems. In answering the academic question, there are aims and objectives to help navigate through the report and project implementation.
Aims
- Finding the basic requirements an electronic voting system accessed online requires.
- Developing an HTML based website to implement the requirements needed for such a system.
- Database development to manage the information related to the voter, the candidate and the system administrator.
- Finding and developing measures to secure the online electronic voting system.
Objectives
- Based on evidence investigate the acceptable standards to implement the e-voting system.
- Understanding the technical requirements of an electronic voting system and develop using HTML 5 and CSS 3.
- Understanding the security considerations for the e-voting platform.
- To test the web application using the appropriate test application using for security vulnerabilities.
- Understanding the threats to the security of the database and develop using PHP and MySQL.
- Understanding the procedures put in place to handle suspicious behaviour in the voting system.
Artefact
The artefact developed is a web application which the users use to vote. The web application provides for the users to register that creates an account. The user is then allowed to login into the system using the details provided during the registration and proceed to select their preferred candidate after which they are eligible to check the results in the form of a pie chart. Enhanced features are included during the development to ensure that the system is as secure as possible. The web application can be used in any web browser that supports the languages and tools used to develop the application; such browsers include the Microsoft Edge, Safari, Mozilla Firefox, Google Chrome etc.
Most of the methods applied here are as a result of extensive research into scholarly works that had been done before. The scholarly works are sourced from the internet sources such as e-books, e-journals, academic and enterprise web pages. The technical development knowledge used to develop the artefact is derived from experience in using the knowledge in programming and web development.
This report bases it structures concerning chapters. The first chapter is the introduction covering the aims and objectives of the project, the academic question, the basic artefact and methodology used.
Chapter two covers the literature review, the benefits and security-based literature of the electronic system.
Chapter three outlines the development of the artefact it is broken down into sections to cover the process followed to come up with the secure voting system.
Chapter four covers the security-based design and implementation.
Chapter five covers the conclusions.
Chapter Two: Literature Review
Studies on computing technologies used to improve electronic voting systems emphasize on the need for caution while using such systems primarily due to software challenges, network vulnerabilities, and auditing challenges (Kohno, Stubblesfield, Rubin, & Wallach, 2004). It is possible for system users to manipulate the system and this compromises its integrity. The correctness, security and strength of any electronic voting system are the key considerations in the development of an electronic voting system. In addition, since the first electronic system was developed, the trend has been developing a system that guarantees voters’ anonymity as way of protecting the voters. The system needs to be tamper-proof to ensure that the results reflect the voters’ will. Also, the system needs to be usable by all parties involved in election. Creating an electronic voting system with the above features has been an engineering challenge and relevant literature is discussed in the following sections.
History
Neil McClure and Kermit Lohry obtained the patent for electronic voting system in 1997 (McClure & Lohry, 1997). The system defined in the patent contains a main unit with multiple mobile memory units (MMUs). Data could be shared between the main unit and the MMUs. The MMUs had flash memories that allowed single writing and multiple reading operations. The system defined could store ballot images that could be accessed from multiple locations for authentication and verification. Each voting station could read the ballot, and ensure that right ballot style was being used. The main unit communicated to the precinct units on the status of the system, whether in storage mode or deployed mode. The initial patent had a remote sensing terminal and speech converter for disabled persons. Since its invention in 1997, the electronic voting system has been used in several countries.
The electronic voting Machines (EVMs) that have been on the use record votes to replace ballot papers and boxes used in the traditional voting system. It is a standalone system with robust programming that enhances its security (McClure & Lohry, 1997). To ensure reliability, many EVMs have batteries that act as secondary power source. The system has a control unit, that controls the system, and a ballot unit. The control unit has a microchip that contains a program that controls the system. The control program cannot be read, copied or modified once burnt into the microchip. The system uses dynamic coding to encode data transmission between the control unit and the ballot unit. Some of the improved EVMs can record real-time input of data, whenever a user presses any key. Once voting is complete, the system operators can press the close button to mark the end of the exercise. At the touch of the “total” button, the total number of votes is displayed. Any system faults such tampers are detected by the control unit and displayed on the monitor.
The United Kingdom used electronic voting system first in May 2002 (Kumar & Walia, 2011). The systems incorporated various technological enhancements such as touch-screen voting machines, interactive voice response, mobile phone short message service (SMS), and PC-based voting service. Voters could vote from kiosks in shopping centres. An analysis of the UK e-voting system proved that the system did not have security issues and privacy violations. India, the world’s largest democracy, deployed the first e-voting system in 2004 elections. As of 2004, India had 668 million electorates (Kumar & Walia, 2011). The system had over one million EVMs. The EVMs comprised a control unit for the polling staff and a voters’ unit for electorate use. Voters had to press a button next to their preferred candidate’s name, and control unit recorded the exercise as a casting vote. Once a voter completed the exercise, the polling officer pressed the switch button to mark a complete vote and allow the next voter in queue. The system allowed five votes within one minute.
The first fully electronic voting in Brazil was conducted in 2000 when the government deployed 400,000 kiosk style machines (Kumar & Walia, 2011). For each election post, the system displays all contestants and asks the voter to select his/her choice. Data entry and display into the system is through an integrated keyboard and screen. A voter selects a candidate by pressing the keyboard number assigned to the candidate in the system, and the candidate’s picture appears on the screen. Voters need to confirm, reject or select a different candidate. The Brazilian system is unique in that after voting, the system tallies the votes and produces both printed and digital results. Other countries that have successfully used e-voting systems include Italy, Belgium, Spain, Australia, Argentina, Panama, Costa Rica, Panama and USA (Kumar & Walia, 2011). In countries that use e-voting, only Brazil uses paper trail audits, where the system allows the voter to see printout their vote, and the overall results can be printed at the end of voting. In all countries where e-voting has replaced conventional voting, the systems were introduced at sub-national level on trial basis. The EVMs used in Australia and Brazil allow the casting of blank votes or invalid votes. The Indian e-voting system does not permit blank votes owing to the fact that the system was introduced to limit invalid votes which were relatively higher than valid votes.
Benefits
Forward-thinking commissions have adopted electronic voting systems since such systems are auditable. Election stakeholders including voters, electoral commissions, and observer missions can audit each stage of the election. Most electronic voting systems incorporate voter-verified paper audit trail (VVPAT) that enables printing of a paper receipt as evidence of a vote cast (Smartmatic, 2018). Such trails are important during recounting and auditing exercises thereby enhancing transparency. The electronic voting system is considered secure especially with the use of VVPAT technology, and the system protects the voters’ privacy. In case a hacker succeeded hacking into the system and cast a dubious vote, the system would not produce a paper receipt, and hence there would be a discrepancy in cast vote. To ensure the security of modern e-voting systems, 256-bit encryption and redundancy is used for both data storage and encryption. Redundancy ensures that data is held in multiple locations in case of security breach.
Electronic voting increases accessibility, and this makes it possible for all eligible voters to cast their votes including disabled people. The use of electronic voting system increases voter engagement and turnout since essential voting processes such as voter registration and education are enhanced with technology. The fast pace of processing results enables citizens and stakeholders to know results within a couple of hours unlike in the previous system where the process of vote counting took weeks, and it was prone to human errors.
Problems
It is difficult to guarantee voter privacy, system security and accuracy in the complex electronic voter systems (Kohno, Stubblesfield, Rubin, & Wallach, 2004). Such requirements complicate the design of the voting systems. For example, the direct recording electronic (DRE) voting system is composed of a touch-screen where the voters select their candidates, main memory and removable memory card for storing data. The display unit can display many formats of ballot layouts and provide complex accessibility features such as hearing aids. The primary challenge with such a system is ensuring that it accurately captures the voter’s intentions since the system produces records that are not verifiable by the voter. An audit of the system is not possible, and therefore accuracy is estimated through relative measures such as pre-election canvassing results, software code reviews, and pre-election tests of software accuracy.
It is difficult to evaluate errors in electronic voting systems due to their complexity. As such, the security and accuracy of electronic voting systems cannot be guaranteed (Rivest, 2008). An error in commands can cause unexpected results, and also provide a vulnerability loophole. Troubleshooting a large system is constrained by financial and time demands. Many elections have cost prohibitive budgets and this further limits extensive software testing of the electronic voting system. In electronic voting systems that are software-dependent, one can only assume that the software is accurate. Questions related to results authenticity cannot be verified, and there is no recourse for vote recount, and a dissatisfied party is forced to assume that the system recorded the votes accurately. With such challenges, it is necessary to develop a system that ensures the integrity of the election exercise
Security
Voter related security issues
In the modern internet environment, there are infinite malicious programs and configurations, collectively known as payload (Kohno, Stubblesfield, Rubin, & Wallach, 2004). Trojan horses, viruses and bugs have been used in the past to cause unimaginable damage. Although antivirus programs have been developed as a solution to virus intrusion, such programs work based on a comparison of signatures. The antivirus program is just a list of signatures provided by the vendor, and a malicious attacker can introduce a new signature not recognised by the antivirus, and this makes a computer including the voting window, prone to attack. It is possible for an attacker to introduce a malicious payload and its signature without detection by the antivirus programs. To counter such a threat, one needs to use trusted software from trusted vendors, and check all digital signatures. However, such a move is unsustainable since each component of the software will need to be checked and signed. The current software market lacks hardware and software that can support such thorough verification.
Software such as Back Orifice 2000 can be used to control a computer remotely (Prosser & Krimmer, 2004). An attacker can use such software to manipulate a target computer. Back Orifice 2000 is an open source program, and an attacker can change its code so that it operates in stealth mode due to the new signature. An attacker can manipulate the voting decision without detection even by expert system administrators. The election date in many countries is known in advance, and this can allow the planning and successful execution of malicious software. The Chernobyl virus of 1999 modified the BIOS program such that the computers could not boot. If an attacker targets a particular demographic with a similar attack then the election outcome will be affected.
Voting through the internet can be prone to attack since there may be malicious payload installed in the PC through CDs, flash disks and memory sticks thereby infecting the computers (Prosser & Krimmer, 2004). Emails have used to distribute malicious programs through attachments. In some cases, the email recipient does not need to open the attachment since previewing the email is equally devastating. The modern trend in web attacks is the use of buffer overflows. A process running on a computer, such as Mozilla, assigns additional data than the programmer sends to a memory location. The additional data is usually a malicious code that is executed. Buffer overflows are frequently executed through web browsers and servers. ActiveX controls can be used to execute dangerous programs since they primarily reside on web server. Web browsers that allow automatic execution of ActiveX controls can unknowingly download Trojan horses and the attack can be launched on the election day (Prosser & Krimmer, 2004). It is common for people to use ActiveX controls as browser plugins and calendars etc. In addition to spoofing, ActiveX controls provide means of launching a successful attack. Common software vendors, such as Microsoft Word, can modify software and configuration during the setup process. A rogue programmer can embed the desired code on the given software program to affect the computer where the software is installed. During the election day, the changes affect the voting process on the modified computer.
It is possible for a voter to select candidate A, and a malicious code changes the voter in favour of candidate B. The malicious code displays the candidate that the voter intended to vote but changes the vote and sends it to the card reader (Prosser & Krimmer, 2004). Without a dedicated display on the card reader for proofreading then the voter is fooled. To enhance the security of the card readers it is necessary to incorporate expensive displays for proofreading. Mobile phones can be implemented in place of PCs, but their limitations include display area, text input capabilities, and resolution. With the above voter side issues, no country has rolled a system where the voters can cast voters from their computers full of compromised software with downloaded programs from the internet. Modern polling sites are carefully scrutinised and audited before the election day, and all stakeholders ensure the integrity of the system through the audits.
Server Side Security Concerns
Denial-of-service (DOS) attacks affect servers in the electronic voting system by preventing legitimate users from accessing the system. It is possible to coordinate multiple attacking machines to launch a joint attack on a system on what commonly known as distributed DOS (DDOS) attack (Kohno, Stubblesfield, Rubin, & Wallach, 2004). In DDOS, an attacker controls multiple computers known as slaves by spreading a worm or virus. The slaves respond in a manner dictated by the attacker. DDOS attacks occur in two forms: the adversaries clog the target network with useless data thereby preventing any traffic through the network. An example of this attack is the SYN flood attack. The second form of DDOS involves the adversaries overloading the server resources with junk data as a way of keeping the server busy. Overloading the server’s computational capacities is common in SSL-protected websites since the recipient has to perform slow cryptographic task, often RSA private-key computation.
Voters can be disenfranchised in case of DDOS attack, and this cuts them from the internet. Also, a DDOS attack can target a regional server thereby isolating a certain geographical area. Currently, there is no known preventive mechanism against DDOS attacks. Attacks can launch a relatively easier known as the ping of death attack that targets a computer and makes it crash. DRE voting systems can counter DDOS attacks by allowing a voter to vote, and be sending the vote once service is available.
Connection Security Issues
It is possible for attackers with political motivations to target a geographic region and paralyse the network with the goal of ensuring the candidate with the majority vote in the region is denied victory. The election process is disenfranchised through such attacks. Attackers target the Domain Name Service (DNS), which is used to manage IP address mapping between computers and domain names. In the past, attackers have attacked DNS successfully. In 2002 during an American election, attackers infiltrated DNS servers with DDOS, and this ensured that the servers were fully loaded (Washington Post, 2002). Many voters were unable to cast their votes since the DNS servers were not available. A voter needed to know his/her IP address to access the voting server.
DNS spoofing enables overriding of an actual IP address with a fake one. As such, it becomes nearly impossible to control the DNS root servers especially with the use of DNS caching. Some of the solutions that have been developed to DNS spoofing include protocol DNSSec although its impact has been negligible (Prosser & Krimmer, 2004). In case a voter is victim of spoofing, he/she follows the instructions for voting on the domain name but he gets a wrong IP address and the attacker succeeds in initiating communication with the voter. The attacker might lead the voter to a page that resembles the voting page. After establishing the communication link between the voter end and the control unit, the attacker can abolish votes. An attacker can use the similar approach during the registration process. By establishing a conversation with unsuspecting eligible voters, the attacker misleads them to believe that they registered successfully for the election. The voters are not registered on any legitimate registration server, and hence they are excluded during the voting process.
Attackers can use social engineering with malicious intentions of breaching the target computers. The attacker sends spoofed emails to voters. Many people would trust such emails if they look authentic. Although digital securities used in antivirus can be used to address such a security concern, the concepts of SSL connections and certificates is new to many people, and hence they are unable to discover the malicious intentions of such emails. Internet router connection is used in relay IP packets between the server and internet. A DDOS attack can render IP routers dysfunctional, and this may affect a target demographic region (Prosser & Krimmer, 2004). There are electronic systems, such as in Brazil, where the EVMs produce a voting receipt as evidence of a vote cast. The receipt also contains the voter’s decision. Such a system does not sufficiently address the issue of integrity since it is possible to change the vote on a computer in the voting system or even in the server side. Similarly, many DREs do not have means of providing a voter-verified audit trail. Voters cannot be confident that their votes were counted in the overall tally.
Verifying Electronic Voting
Although numerous efforts have been made to improve the integrity of the EVMs, it all narrows down to voters trust on the system. If voters feel the results computed by the system are not factual then it is impossible to argue that the results represent the voters’ choice. A voter-verified paper ballot has been proposed as a possible solution since an audit will enable a comparison of the two results. Since in most cases a vote is usually a voter’s secret, the electronic voting system needs to guarantee this. As such, it is possible for a program flaw or tampering to change votes and the overall results without detection. Voter-verifiable audit trail (VVAT) has the solution since it contains a permanent record of each voter (Prosser & Krimmer, 2004). The use VVAT in all election equipment is likely to boost the integrity of electronic voting systems, and if the system fails, it is possible for a manual recount of the elections.
Electronic voting systems such as Diebold voting system are prone to tampering (Kohno, Stubblesfield, Rubin, & Wallach, 2004). The codes used by the EVMs are available to the public. Even in case of public uproar, the machines design, as well as data secrecy, remain hidden. However, Diebold published its source code in its website, and keen scrutiny revealed that anyone with access to its database could change the election results undetected. A similar security breach could happen through a hack executed over the internet. With paper backups in electronic voting systems, it is possible to verify the integrity of the EVMs since computerised voting can facilitate malicious control of the voting exercise.
Chapter Three: Development of the Artefact
Overview of the Artefact Basic Structure and Working
To realise the secure online voting system, a web application that is used by students in the voting activity is developed. The web application welcomes the user to a login page on first visit or whenever the user queries for the URL in their web browser. The login page prompts the user for their e-mail address and their corresponding password. The login page also has a button for registration or sign up to users whose details are not yet captured in the database. This button when clicked leads to a page where the user enters his/her details to start using the system. Upon filling up the details required for the registration in the sign-up page, a verification code is sent via short message service (SMS) to the users messaging app on their mobile phones. On input of this code on the given field the user is permitted by the app to a redirected login page where they will be able to vote but is only eligible to vote once.
In the login page, once the user enters the authentication details, that is, the e-mail address they used to register and the password they set and the details verified to be true by the app through a database backend, they are sent to a voting page. In the voting page the user is allowed to choose by selecting through radio buttons one of the three candidates or names in the dashboard tab. Upon selecting the choice and clicking the vote button the voter is taken to the results tab on the voting page. Here in the results tab the voter views the results displayed in the form of a chart showing the relative area covered by each of each of the candidates as the voting continues. Each candidate has a distinct colour assigned to make it easy for the user to distinguish one candidate from the other. The choice of colour is very sensitive in helping the voters in identify and have a good visual view of each candidate’s score as the voting process progresses. That is the reason for using the very contrasting colours in the web application to aid the voter in having a better visual picture without strain. Compatibility of the colours is also important, especially to the voter with special considerations such as colour blindness conditions. On satisfaction with viewing the result the voter the user can opt to log out from the My Account button at the top right corner of the voting page where from the drop down option the voter selects the logout option. This page redirects the user back to the login page; this is the home page. From the login in page the voter is allowed to login in but this time they can only view the result from the result tab on the voting page. As before the results are displayed in form a chart and as more result come in the voter can refresh the page to update their view.
Software Development Life Cycle
The phases of development used here are based on the Software Development Life Cycle, SDLC as shown by the figure below. The SDLC is adapted as below to now include the requirements research and selection, design and implementation are integrated and so is the testing and deployment section.
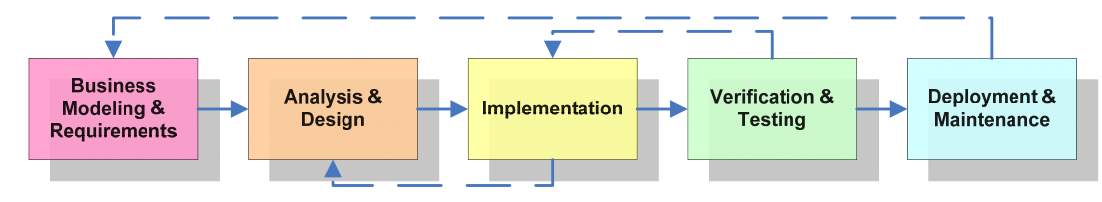
Figure 3.1. The SDLC
Research and selection of the Artefact
Of great concern to the voter is security of the process used to make their choices (Wernick, 2017). Therefore, in trying to find a solution this concept was the main basis of reference. It is clear from the open web application security project that security of a web application is just as vital or sometimes even more important as the security of other components making up the web application such as the network (Owasp.org, 2017). As shown in the comparison figure below illustration the unbalanced spending on security is still a great setback in dealing with security threats. Organisation spends a lot on securing their network whereas it the web application that needs to be more secure as close to two-thirds of web applications are vulnerable to attacks (Owasp.org, 2017). Therefore, with focus on securing the web application my design and implementation concentrated on choosing to develop a web application with features that make it secure thus boosting the voters’ confidence and trust. This features and adjustments make the site to mitigate vulnerabilities list in the organisation on web application security project, OWASP top 10 (Owasp.org, 2017).
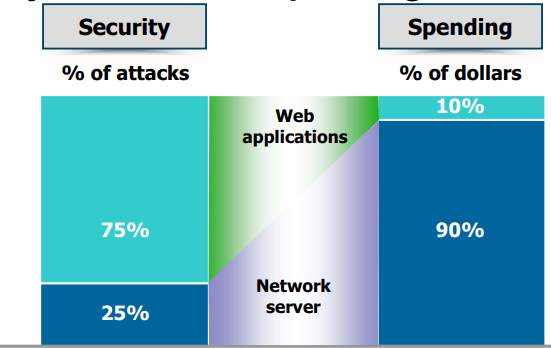
Figure 3.2 Comparison on the network and web application spending and security risks
The government through the data protection act stipulates that a great care should be taken when dealing with data involving the population (Woulds, 2004). Online voting system falls in the target group for this act since it involves collecting and handling the voter data. Thus, to abide by this act, the application developed has to be secure enough to ensure the users data is handled with care. It is through that spirit that the project focuses on developing a web application that can be able to enforce measures to prevent data security breaches.
The Equality Act in sections 20 and 29(7) provides for necessary modifications by service providers to make it possible and easy for people with disabilities to be able to access services (Taylor, Haggerty, Gresty, & Lamb, 2011). Since the E-voting system provides voting services to a large population comprising of different individuals among of which are disabled persons it is only right to develop a system that will cater for them just as easy as it is for people with no disabilities. It is through this that it became the most viable fit to develop a web application that not only conforms with the mentioned sections of the Equality Act but also goes a step further to offer unnoticeable ease to all voters, even those with difficulty in understanding the system by providing a simple client side.
Since budget considerations becomes a great deal in developing the Electronic voting machines, system developers and designers must include it as among the most critical factors (Okoro, 2016). The student needs a simple, most efficient and secure system. But to wrap all this, the realisation of the system with this kind of features has to be cost-effective. It is based on this that I selected to use a web application that will offer all these desirable features but at a lower cost compared to the other systems in existence.
Artefact Development Tools – programming languages
PHP and MySQL
PHP stands for Hypertext Pre-processor. It a scripting language embedded in hypertext mark-up language, HTML. It derives from other known languages such as Perl, Java, C and C++. It aids developers quickly generate dynamic web pages. Its developers make a certainty that the result of its use in web development vulnerability proof. On the official site https://www.php.net, the new release is referred as the secure release, adding that several bugs have been fixed in the new release. It first came to be in 1994, being the work of developer Rasmus Lerdorf (Welling & Thomson, 2003). Since then it has been used widely with the most recent evaluation putting its use at eighty percent of websites and application in the web showing the might of its prowess in the development world. The PHP language is open source, which is no licence is required to use it in your application, this is one of the reasons it is used widely.
PHP language usually communicates server side (Cui, Huang, & Liang, 2009). Whenever a user types in the address bar of their web browser a uniform resource locator, URL, it is like asking for a web page from URL entered from the server. From the server the file is sent which translates as a web page on the web page of a web browser. All this is possible because of PHP. This is manifested as most web pages in the address bar have their URL ending in .php extension. This shows that PHP is installed in that application (Scott & Sharp, 2002). Clicking a link such as a button in the web page constitutes asking for that particular page from the web server of the application.
Whenever the server receives a request to process a file for the web browser, the statements are transferred from the server in HTML format (Knuth, 2012). The PHP software processes the requested statements before they are sent to the server. This is the reason the PHP statements are not visible in the web browser of the user. The implementation used PHP because it comes with various advantages over options available in the field. To start with, the language has several developers who thrive to share the know how to learners, making it pretty easy to use. PHP is also open source and available to many platforms and users. The only difficulty that comes from using PHP is that for developers who have basic knowledge, the sites they develop using PHP may have security risks because the PHP have many libraries which makes it confusing to select the right and secure one. But for programmers with enough knowledge on the language, it comes in handy as they can develop easily as PHP is a scripting language hence can navigate through the development cycle with ease to bring out an application to communicate easily with the server.
The use of PHP is particularly witnessed in this project report in the various pages from the login page to the result page. The scenarios are seen when the user clicks the login button they are taken to the voting page. The browser sends a request to the web server through PHP requesting for the voting page, which is displayed in response.
MySQL is a query language used to issue query command to the database. The database is where passwords, e-mail addresses are stored. Whenever the web application request for such information the MySQL ensure it is made available. This way the server, database and web application work together.
HTML 5 AND CSS 3
HTML 5 stand for HyperText Markup Language version 5. HTML is a language use to create and view website. Using a tags <> edited using an editor the result of each standard tags displays as a web page in a supported web browser. The contents are viewable to users in the format specified. Example of content include; images, text and video. The latest version that is 5 has additional features as with every version release comes improved adjustments to security and design techniques.
HTML 5 detects in debugging the tags and codes used in the web application in real time. In addition, it has heading fonts, that is heading 1, 2, 3, 4 and 5 which help in styling the web page and help the world wide web in displaying the contents of the web page. This comes in handy when the page is queried in the search engine of the user, such as Google, the pages are displayed based on the heading tags used. In terms of compatibility with older and most recent versions, HTML 5 has a feature to add new tags and can eliminate ones from older versions used in to develop a web application.
Each and every page of the voting application uses HTML to display the contents. In details and using the Sign Up page, the use of HTML forms is employed to bring out the fields to input the name, email and password fields and the register button acting as a submit button. Sectionalizing the voting page to include the results and user panes are the works of HTML using the tags.
CSS is cascading style sheets in full and is used for styling the elements of HTML used in the application. This works to give a better display and enhance interaction of the user with the web application. The latest version of CSS is CSS 3. Information and all tags relating to HTML tags and CSS are found in the site https://www.w3schools.com. The is used to align the text, choose colour for significant areas of the web page such as the background colour and the text colour, design the pictures layout, select the font scheme for each web page or division etc. I used the CSS to come up with the different colours of the elements and pages as seen in the web application.
To aid simplicity, each page of the application is put in its HTML file. The CSS styling is edited using an editor and stored in one document where each element is styled using class and id attributes of CSS. This helps to distinguish and make it easy to style a number of tags just in one style file.
Elements in the Artefact
The web application was developed based on the various basic feature each web application and website has.
Choice of colours: the background colour used in the voting page is grey while the login page and Sign Up page both have a background image that spans the whole page. Grey colour in the background offers a friendly impression to the user. The colours for each element varies with blue and orange used for buttons in the Sign Up page and Voting page respectively.
Font: I chose to use the Calibri font. It has simplicity to all users, hence no character can confuse the voter when they are interacting with the web application. Each user can read the font with most ease as its displays are clear and basic.
Chart: the chart is used to show the comparative result of the three candidates whenever a voter wished to see the results after voting. The chart has different colours for each candidate to aid in comparison when viewing the results. The chart is easier to see the relative popularity of each candidate as the voting continues.
Stored procedures: these procedures are stored in the server in the form of standard query language, SQL statements to be used by the application whenever in the need to. This makes it easy for the web application from different end of user to communicate with its server and saves time since it is a centralised approach. It however to be noted that in no any part of the application the SQL statements been used. This as is explained in the sections a below minimise the vulnerabilities associated with the statements mostly injection attacks on the SQL.
Artefact Design and Implementation
In developing the web application, I decided to use a simple design that include a login page which is also the Home page, Sign Up page and Voting page which has vote tab and a results tab. Navigation through the pages is simple since there are not many pages to confuse the user in any way. The bulk of sophisticated code is to the developer, while simplicity is offered to the user. The designs give an overview and guidance when developing the application. For each page there is a link to another of the pages making it easy for the users to move to the page they want just like a guided tour. Once the voter is in the home page they can go to any other page with an exception made to voters who has voted note to access the vote tab of the voting page by revoking their privileges. The breakdown of each page is provided in the subsections below.
Login Page
This is the home page, that is the page the application refers the user to on the first visit or as a default. It is simple as shown in the figure below. The background is an image and the font is Calibri font. To proceed from this page, the user has two options. The first option is to provide the correct details in the e-mail address and the password field and then click the orange login button at the bottom the page. Upon clicking this button, the user is taken to the voting page discussed below.
The second option the user has is to use the sign up link in blue at the bottom right of the page to register as a new user. When the user clicks this they are redirected to the registration page where they will provide details and redirected to the login in page to proceed to vote. The colours used in this page are contrasting to aid the user especially the ones who need visual enhancements to identify quickly what they are supposed to input or click. This page is interactive enough to notify the user of an invalid password and invalid e-mail address. The screenshot of this page is shown in the figure below.
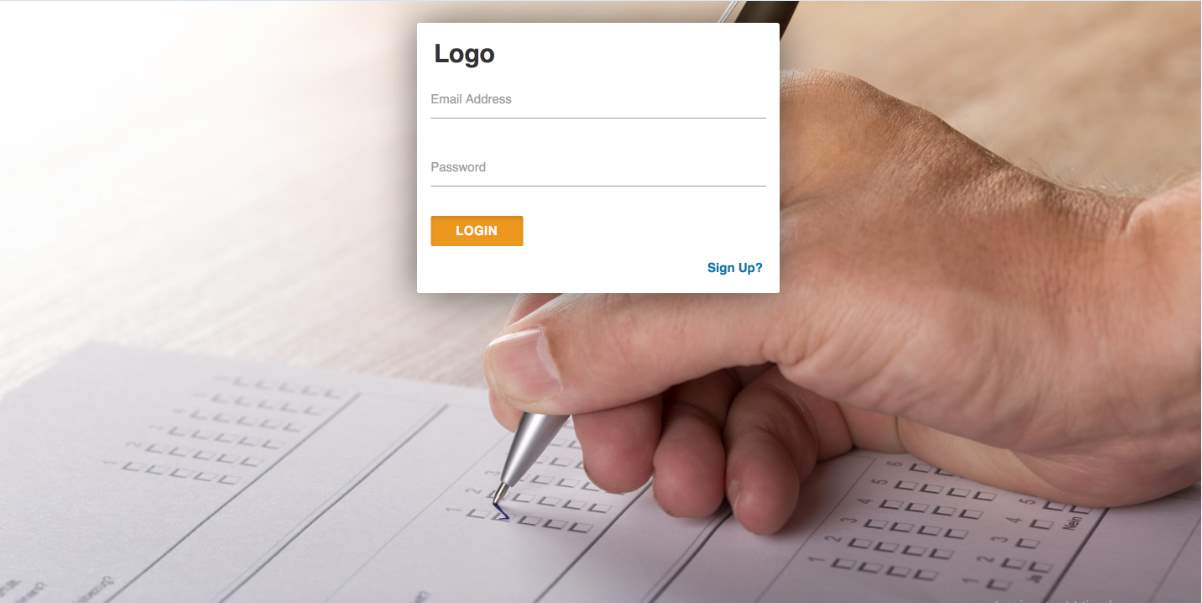
Figure 3.3 The login page.
Registration page
This is the page a new user is taken to when they click the sign-up link from the home page. It has the same picture background that has friendly contrast to the user. Here the user enters the details making him/her eligible to vote. The page has field for First name, Last name, e-mail address, password and password confirmation. Once the user fills out all the fields with valid data and checking the check box confirm their agreement to the document they click on the register button in orange at the bottom of the page. For users who find themselves in this page for any reason having registered are prompted to click the Already a member? Link in the bottom right of the page. On clicking the link, they are taken back to the login page. In the case the user enters a wrong password in the confirm password field an error message as the one shown in the screenshot in the testing section is displayed. The figure below shows the layout of the registration page.
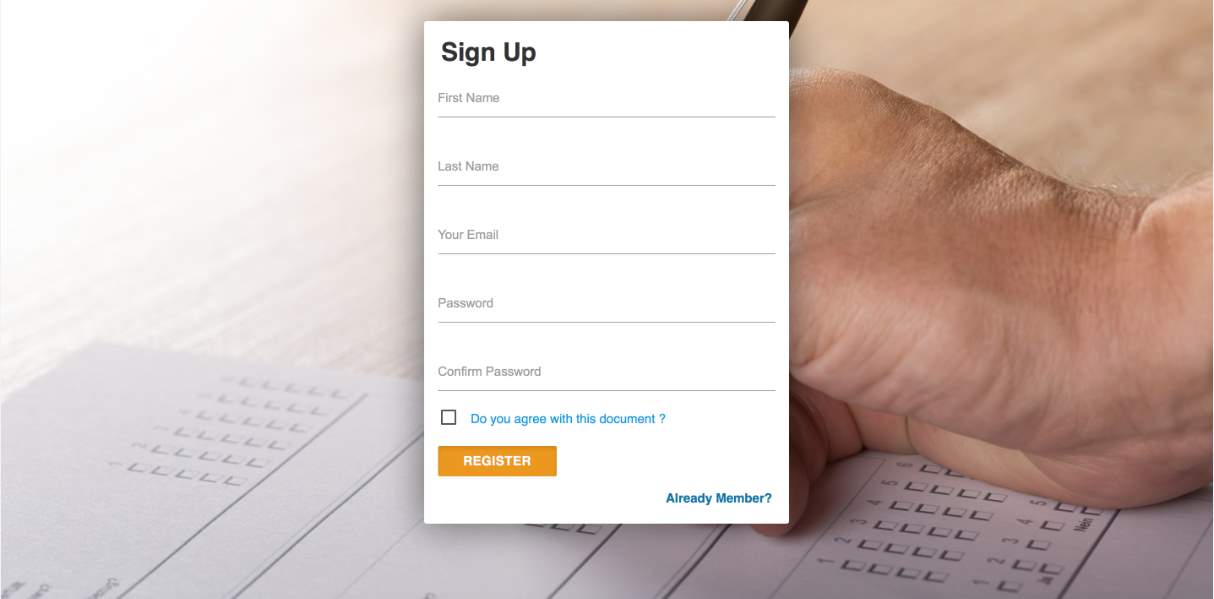
Figure 3.4 The registration page
Voting page
This page has to tabs and links to the home page. A voter who has not yet voted has the option to use the vote tab after which they can use the results tab.
Vote tab
Here a list of candidates is provided with radio buttons used to select the preferred candidate to the user. The voter then clicks on the vote tab to affirm the choice. If the voter had already voted as shown by the screenshot in the testing section below the user can only view the results. The results button is adjacent to the vote button. The figure below is a screenshot of the vote tab.
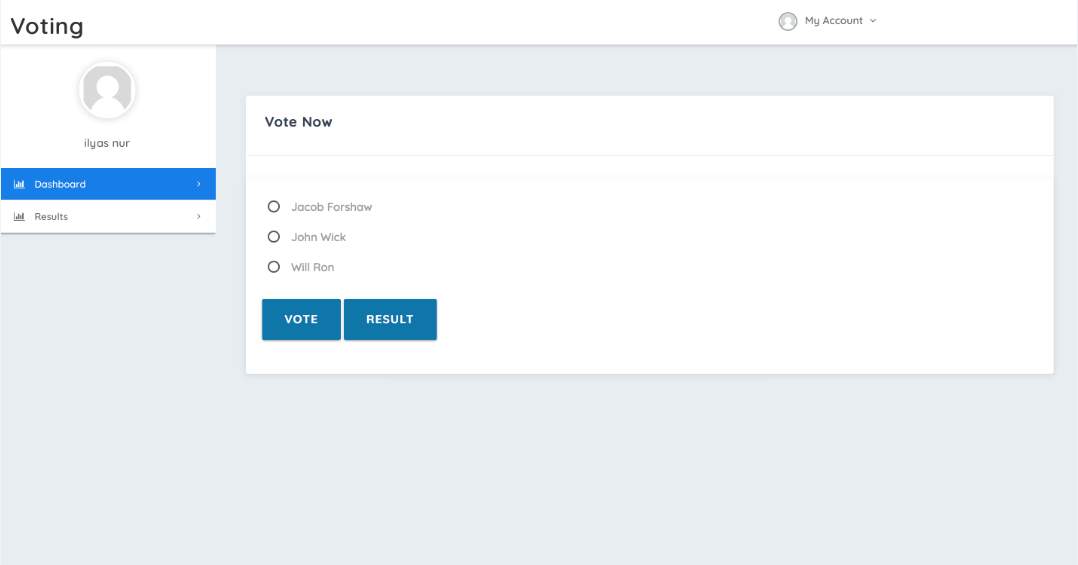
Figure 3.5The vote tab
Result tab
The voter can end up here by selecting the results from the left pane or from the results button from the vote tab. Here the results are shown in a pie chart. The colour of each candidate is distinct as in, blue, red and green. This is a proper tool for comparison of the candidate’s votes as the voting goes on. The figure below shows the results tab.
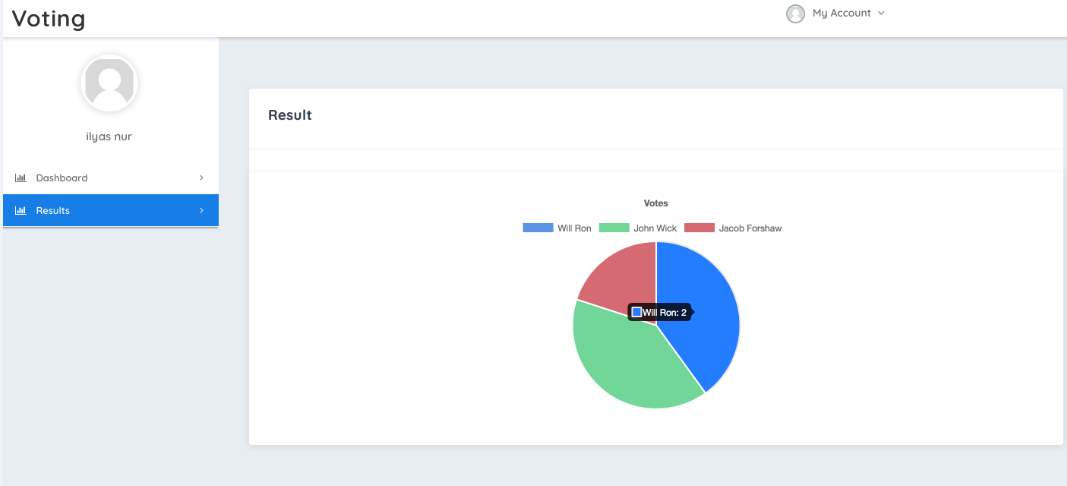
Figure 3.6 The results tab.
Testing of the Artefact
To curb failure possibility and hence save the input invested in the project it is always right to conduct various test before releasing the product for use (Blattberg, Kim, & Neslin, 2008). These tests are done to implicate the user and see how the application works or responds to various errors or to see the vulnerabilities that exist within the web application as this is the application based security approach. To ensure the end product is of the desired quality these tests are as necessary as the design and implementation phase of the development cycle. The tests are outlined in the subsections below.
User Errors
To outline the kind of response and therefore the interactive ability of the web application used for voting, the developer entered the wrong password in the confirm password field in the registration page and it responded by notifying through an error response that the password is not the same as the developer provided in the field prior. The second test was trying to vote again after my vote choice had been captured by the system in the results tab of the voting page. The page responded by displaying the response shown in the screenshot below. This means that the database has already updated that the developer voted therefore any attempt to do so again is a cheat to the process. This ensures that the integrity of the system is maintained all the time. The tests are shown in the screenshots below.
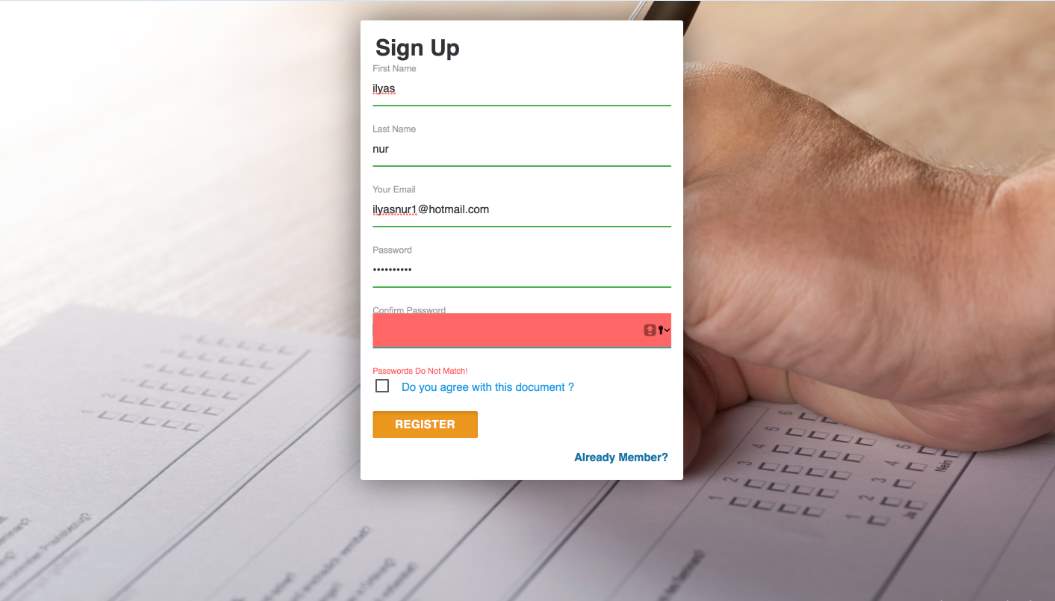
Figure 3.7 Error in the registration page.
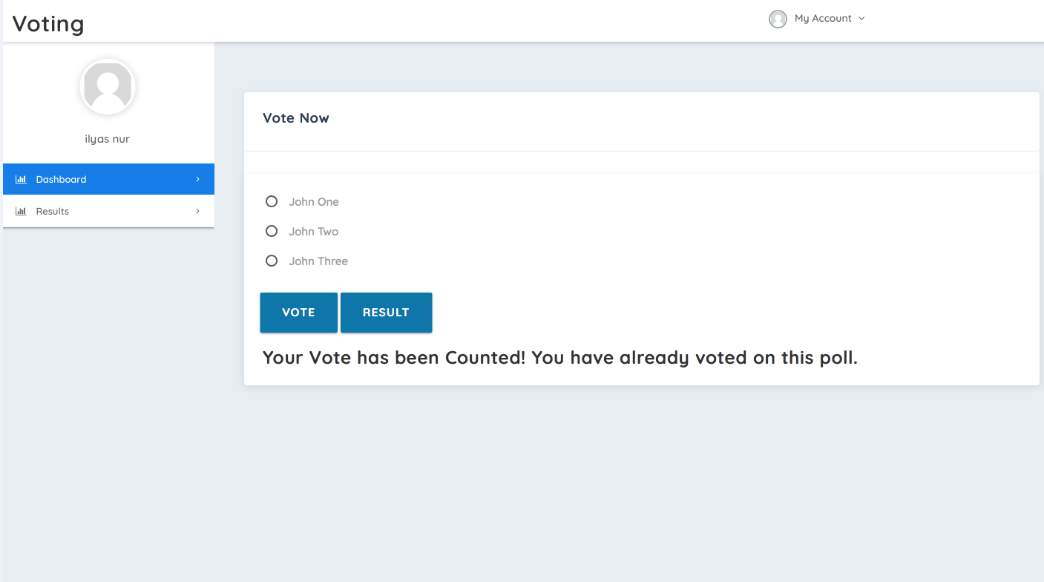
Figure 3.9 the error in Vote tab of the Voting page.
Vulnerabilities testing
Vulnerabilities in a web application is a concern for any application as they are the entry sites for attackers who would not hesitate to take advantage whenever any exists (Bozic & Wotawa, 2014). For this testing I used an application called ZAP. It is an application used for penetration testing of web applications. It offers a good user interface that can easily be used by many developers. Its output are the vulnerabilities found in the system.
Procedure for testing using ZAP.
- The application is available for download from GitHub at https://github.com/zaproxy/zaproxy/wiki/downloads. Once the download is complete it is installed into the personal computer.
- The application is launched just like the many desktop applications where it takes the user to the user interface.
- To begin the testing a URL of the web application is typed into the Quick Start button.
- The clicking the attack button starts the penetration testing.
- The ZAP application attacks the web application to find the vulnerable sections and then displays the vulnerabilities found in the alerts tab.
- With each vulnerability clicked the URL that was attacked is displayed.
- More comprehensive details on the vulnerability is found by clicking the URL. The information on how to handle the vulnerability is also shown.
The figures below show the screenshots of the ZAP application before and after running and correcting the URLs where there were vulnerabilities.
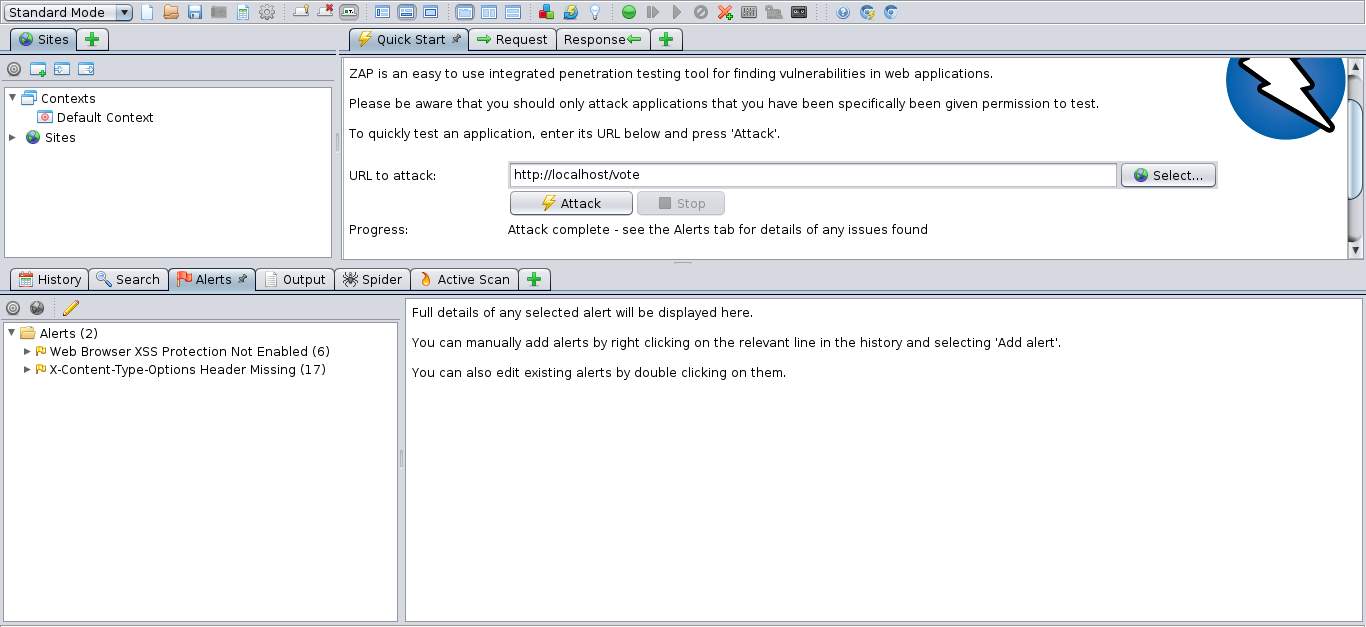
Figure 3.9 the ZAP application for testing
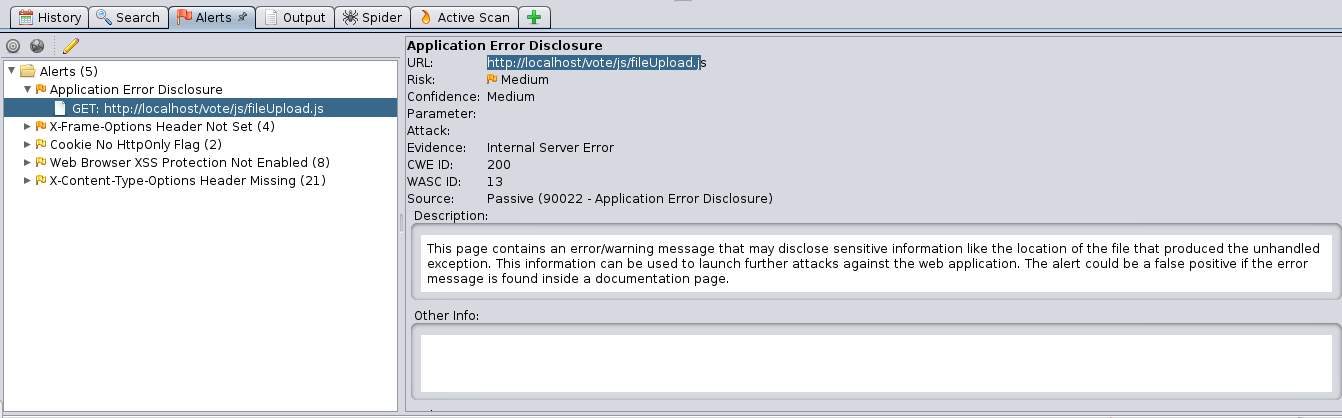
Figure 3.10 ZAP application showing vulnerabilities.
Chapter Four: Security Centred Design and Implementation
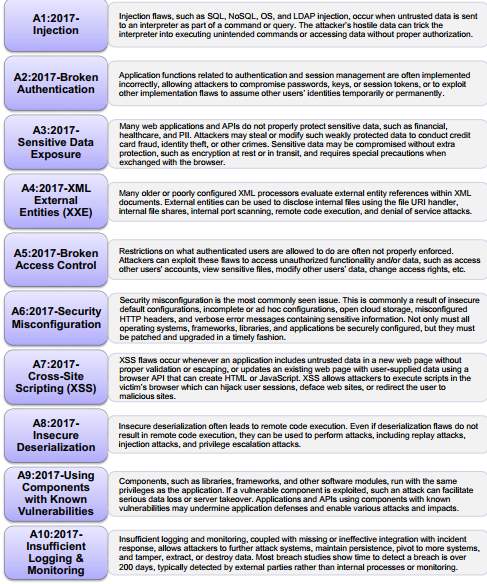
The integration of security into the SDLC is vital before testing the application (Ruparelia, 2010). In an effort to answer the research question, reference to the requirements based on the research and drawing from capabilities of the artefact and the tested result is the basis to which such a response starts. The design and implementation of a secure electronic voting system through a web application should centre on the security of the application from my perspective. For this reason, I referred to open web application security project, OWASP top 10 list for the most recent vulnerabilities and how to mitigate the threats coming from such threats (Owasp.org, 2017). The organisation releases new security risks in a three-year interval with the most recent being the one for 2017. This design and implementation is as outlined below. The screenshot in appendix 1 shows the OWASP top 10 for 2017.
Injection
It an attack targeted through injection in the SQL or the operation system. The implication is execution of commands whose source is untrustworthy by the interpreter or accessing unauthorised data in the application. To prevent such exploitation SQL is not used in the application hence the voting system is safe from attacks of this nature from the application side (Fonseca, Vieira, & Madeira, 2013). Prepared statements are used in the web server to prevent this type of attack.
Broken Authentication
This targets the parts of the application that handle the authentication of users. Such things as passwords, security keys and session are at risk of being compromised (Huluka & Popov, 2012). To prevent the user from assuming the identity of an eligible voter, the system must be protected from such exposure. To prevent this the login pages, have no default credentials such as e-mail that can be exploited. Strong password policy is also put in place where login attempts are counted in each 2-hour period during the election process. In the case where the user attempts to login five times without success the account is locked upon notification to the system administrator. Scripts attempting to access the session ID after issuance of a new one after login are blocked.
Sensitive data exposure
Unencrypted sensitive are at the risk of a sensitive data exposure (Wichers, 2013). The attacker can use such sensitive data to do crime such as identity theft on behalf of the user therefore has to be prevented. The only sensitive data of the user dealt with in the application are e-mail addresses which are encrypted in transit between the users’ browser and the web server. Caching for sensitive data responses is also prohibited in the application. Passwords are encrypted using md5 encryption which is a non-reversible algorithm-based data encryption mechanism.
XML External Entities
This gives way for a denial of service, DoS attack and sharing of internal files (Anjali & Raj, 2012). To prevent this the operating system in use has its XML processors and libraries upgraded to the latest version.
Broken Access control
This is where users can exploit vulnerabilities to enable the use the account of other users or even use the administrator functions (Hack2Secure.com, 2018). This needs to be handled as can lead to some voters voting for unsuspecting users and even manipulate the results in extreme cases. The system is set alert the admin on multiple logins in attempts and metadata are not displayed for any user.
Security Misconfiguration
From misconfiguration in key elements of the application such as the server, error and operating system from whose browser the web application is run (Vicente, 2018). There is need to prevent such as attackers can use such flows to obtain information that they use to coordinate attacks on the application. For the voting application the unused components are disabled. Furthermore, the error message from the application does not provide unnecessary information that can be exploited.
Cross Site Scripting, XSS
This kind of vulnerabilities target the user’s browser when a new page opens with minimal validation measures (rapid7.com). The attacker takes advantage of this to redirect the user a site of their preference or even hijack the current session of the user by executing scripts in the browser. For the voting application this can lead to result manipulation through hijacked voting. Untrusted HTTP requests are automatically escaped to prevent this attack in the web application.
Insecure Deserialization
This leads to codes being executed remotely in the web application (acunetix.com, 2017). They can additionally lead to other attacks exploiting the privileges assigned to different types in the voting system and attacks from injection. The password policy included accepts only a specific type with at least eight characters and a digit.
Using components with known vulnerabilities
This risk involves the use of components such as libraries that can be exploited easily hence compromising the application (Owasp.org, 2018). To prevent attacks on the server or even loss of sensitive data this risk types should be taken care. The only content with libraries used the e-voting application is the PHP language which has regular updates to prevent the security risks exploitation. Monitoring the common vulnerabilities and exposures, CVE and national vulnerabilities database, NVD lists in the future is also a planned activity to get ahead of this vulnerabilities.
Insufficient logging and Monitoring
The security risk arising from this targets the system inability to detect persistence logging attempts in the application. It takes several days to detect this type of exploit and in most cases takes an external party to realise. This type of attack is dangerous for the e-voting application hence must be handled prior. All login failures are monitored closely every two hours and failures recorded such that attempts failing more than five times leads to blocking of the user from using the application until verified and cleared by the administrator(s).
In addition to the list other measures, ensure the security of the server and application that are rather assumed are put place to maintain the security and integrity of the system. This additional measures including using cookies to store session IDs enhance the integrity of the whole system. This restricts the session id s from being accessed by attackers. The voters cannot get voter more than once. This ensures that each voter has a right for a single vote as stipulated in many similar systems (Van De Velde, 2017). Scripts attempting to access session ids are blocked immediately. The following measures ensure that the application is secure to most threats to do with the application or the technical side of the system.
Chapter Five: Conclusions
To ensure that an election process is transparent, free and fair the process requires the use of efficient system, one that is easy to trust (Norris, 2013). It is possible to realise such kind of a system as illustrated in this report. The focus to ensure that such a system is secure enough for the use it is intended for the tools used are simple and effective. The web application to be used for voting has been developed using HTML 5 and CSS 3 for the client side, PHP and MySQL for the database server side. Most of the aims have been met using such a system as it is easy to use, secure while at the same time cost-effective. The system uses skills that require only personal level training hence easy to realise. The system can be used by the students effectively since they are few compared to the number in the national elections hence the traffic is not much of an issue. Unless in extreme cases like where the personal computer of the user breaks down, the web application can stand any threat involved in the election.
From this report, the security risks and how to mitigate are outlined. There is sufficient evidence to conclude that the threats to the system mostly revolve around the user end and when this is handled properly as illustrated by the report, the system is threatened by very few factors. However much the security of the system is an issue that can be dealt, some threats are beyond the systems capabilities. One such case is the influence of voters from social media sites to sway to a particular or creating of news whether fake or real on candidates mostly compromising news as alleged in the recent United States of America, USA elections (Masya, Prastiawan, & Putri, 2017). The artefact outlined in this report is a working and secure application that is ready for use to conduct an election.
Evaluation of the product
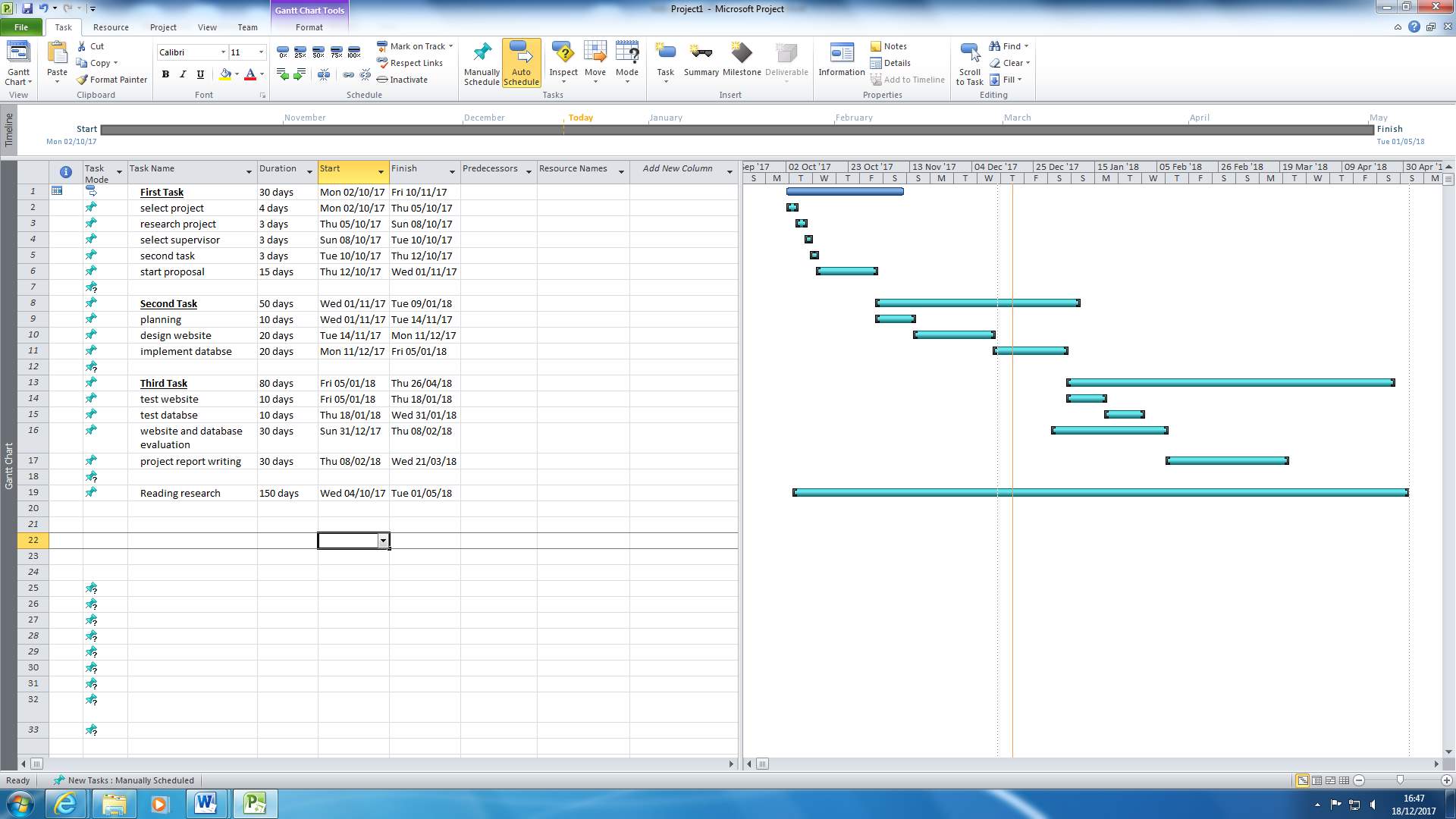
The application outlined in this report can be run in browsers of a personal computer running on any three of the major operating systems, Mac OS X, Windows and Linux. Updates the system may be included after its use in running a real election. Most of the software use such as PHP and text editors such as Sublime text were downloaded prior to the official sites. The planning chart is shown in appendix 2.
Self-reflection
From working on this project, it is evident that with the right motivation and dedication each can steer a working solution to one of the many world problems; in this case, that was developing a user-friendly and secure web application for e-voting. All this was possible through working with the application of skills and knowledge covered in the degree curriculum. Working on this project is a clear illustration that application of knowledge to solve real-life challenges can be motivational to solving even more complicated challenges.
Bibliography
acunetix.com. (2017, December 7). What is Insecure Deserialization? Retrieved from www.acunetix.com: https://www.acunetix.com/blog/articles/what-is-insecure-deserialization/
Anjali, K., & Raj, K. (2012). Web Vulnerability Detection and Security Mechanism. International Journal of Soft Computing and Engineering, 237-241.
Blattberg, R., Kim, B.-D., & Neslin, S. (2008). Why Database Marketing? . New York: Springer.
Bozic, J., & Wotawa, F. (2014). Security Testing Based on Attack Patterns. Software Testing, Verification and Validation Workshops (ICSTW), 2014 IEEE Seventh International Conference on. Cleveland: IEEE.
Cui, W., Huang, L., & Liang, L. (2009). The Research of PHP Development Framework Based on MVC Pattern. Seoul: IEEE.
Fonseca, J., Vieira, M., & Madeira, H. (2013). Evaluation of Web Security Mechanisms Using Vulnerability & Attack Injection. IEEE Transactions on Dependable and Secure Computing (pp. 440-453). IEEE.
Hack2Secure.com. (2018, January 31). Understanding Broken Access Control Risk. Retrieved from www.hack2secure.com: https://www.hack2secure.com/blogs/understanding-broken-access-control-risk
Huluka, D., & Popov, O. (2012). Root cause analysis of session management and broken authentication vulnerabilities. Internet Security (WorldCIS), 2012 World Congress on. IEEE.
Knuth, K. (2012, january 14). Security Analysis of Browser Extension Concepts. Bachelor’s Thesis. Saarland University.
Kohno, T., Stubblesfield, A., Rubin, A., & Wallach, D. (2004). Analysis of an Electronic Voting System. IEEE.
Kumar, S., & Walia, E. (2011, May). Analysis of Electronic Voting System in Various Countries. International Journal of Computer Science and Engineering (IJCSE), 3(5), 1825-1830.
Masya, F., Prastiawan, H., & Putri, D. (2017). Design and Implementation of Lecturer Evaluation System Using ELECTRE Method in Web-based Application. International Research Journal of Computer Science, 242-251.
McClure, N., & Lohry, K. (1997). Electronic Voting System. Hart InterCivic Inc .
Norris, P. (2013). The new research agenda studying electoral integrity. Electoral Studies, 563-575.
Okoro, E. (2016). A Cost-Benefit Analysis of Electronic Voting Operations and Capabilities in sub Sahara Africa. Journal of Business and Economic Policy, 22-30.
Owasp.org. (2017). Top 10-2017 Top 10 – OWASP. Retrieved May 6, 2018, from Owasp.org: https://www.owasp.org/index.php/Top_10-2017_Top_10
Owasp.org. (2018). Top 10-2017 A9-Using Components with Known Vulnerabilities. Retrieved from www.owasp.org: https://www.owasp.org/index.php/Top_10-2017_A9-Using_Components_with_Known_Vulnerabilities
Prosser, A., & Krimmer, R. (2004, July 7-9). Electronic Voting in Europe-Technology, Law, Politics and Society. Bregenz, Austria.
rapid7.com. (n.d.). Cross-Site Scripting(XSS). Retrieved from www.rapid7.com: https://www.rapid7.com/fundamentals/cross-site-scripting/
Rivest, R. (2008). On the notion of ‘software independence’ in voting systems. From computers to ubiquitous computing.
Ruparelia, N. (2010). Software development lifecycle models. ACM Digital Library, 8-13.
Scott, D., & Sharp, R. (2002). Abstracting application-level web security. Proceedings of the 11th international conference on World Wide Web (pp. 396-407). Honolulu: ACM Digital Library.
smartmatic. (2018, April 11). Benefits of electronic voting. Retrieved from smartmatic.com: http://www.smartmatic.com/voting/electronic-voting/
Taylor, J., Haggerty, J., Gresty, D., & Lamb, D. (2011). Forensic investigation of cloud computing systems. Network Security, 4-10.
Van De Velde, J. (2017). The Law of Cyber Interference in Elections. SSRN.
Vicente, G. (2018, April 10). What is Security Misconfiguration? Retrieved from hdivsecurity.com: https://hdivsecurity.com/owasp-security-misconfiguration
Washington Post. (2002). Retrieved from Washingtonpost.com: http://www.washingtonpost.com/ac2/wp-dyn?pagename=article&node=&contentId=A828-
Welling, L., & Thomson, L. (2003). PHP and MySQL Web Development. Sams Publishing.
Wernick, A. (2017, August 26). How secure are America’s voting machines? Retrieved from pri.org: https://www.pri.org/stories/2017-08-26/how-secure-are-america-s-voting-machines
Wichers, D. (2013). OWASP Top 10-2013. The Open Web Application Security Project.
Woulds, J. (2004). A Practical Guide to the Data Protection Act. London: The Constitution Unit.
Appendices
Appendix 1: OWASP top 10 2017
Appendix 2; The planning chart
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Politics"
Politics refers to the way in which decisions are made on behalf of groups of people. A politician will use their position to suggest and support the creation of new policies and laws, before a group of politicians will come together to debate the creation of such policies and laws.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




