Information Security Issues Faced by Healthcare in New Zealand
Info: 3876 words (16 pages) Dissertation
Published: 9th Dec 2019
[Information security issues faced by the Healthcare in New Zealand-Possible Solutions]
Table of Contents
c) Information Security Policy
d) Information Security Awareness
IV. Identify and interpret the security issues/threats/vulnerabilities of the given scenario:
V. Suggest possible security solutions for the identified issues of the given scenario:
VI. Recommend related policies to overcome the identified issues of the given scenario:
I. Abstract
This report will identify and interpret the security issues, threats, suggest possible security solutions and will recommend related policies to overcome the identified issues of healthcare industry in New Zealand. The literature review clearly reviews all the topics which include information security, information security issues, information security policies and information security awareness. The recommendations suggested are aligned with the literature review.
II. Introduction
Modern healthcare has made a dramatic change due to help of technology. Data sharing and collaboration with physicians and their patience through the widespread use of electronic systems has lessen the medical errors and medical research. The delivery of healthcare has enhanced digitalisation of health information which made healthcare data highly vulnerable to attack (Dunlap & Pliakos 2017). Ahead of all other industries healthcare industry remains the most cyberattacked industry (‘Cybersecurity in healthcare is improving, but not fast enough’ 2017). Therefor organisation must install wide range of tools and mechanisms for the security of the information and mainly to their portfolio managerial, organisational and technical defences of information security policy. Even after much research and many practical initiatives security breaches is the main area of concern for all the organisations and in particular to healthcare sector (Stahl, Doherty & Shaw 2012).
The nature of information security threats have changed significantly during the past years. Still the incidence of information security breaches remain very high. Information Technology and network connections are the core modules of each organisations. End users are ignorant of the security concerns caused by the certain actions. For employees Information Technology is just a tool to perform as fast as they can and as efficiently as possible. In ensuring the security of Information Technology systems and information process one of the most vital part is its employees. (Hansche 2001) .
Mostly Information Technology incidents are have occurred due to the result of employees actions originated either from inattention and unaware of the security policies and procedures. So trained employees plays an important role for crucial role for the effective functioning and protection of information system.
III. Literature Review
a) Information Security
The high priority of information security problem not only affecting information security experts but also a large communities like company managers and university staff. There is no boundary for cyber threats their landscape is fast expanding. The technology on its own cannot offer information security. Even the present IT solutions offer means to protect user’s information and security. Most risks are not properly understood nor addressed properly emphasizes the global 2013 survey performed by PWC (PWC, 2013). For the effectiveness of security a proactive approach have to be adopted in information security which is reactive with regard to IT risks (EY 2014). The higher rate of attacks after recognising the sophistication from information security specialists. (Stanciu & Tinca 2016).
The increase in attack which exploit the weakness or the vulnerabilities found special emphasis should be given to information security. In a recent survey held in UK in 2014 states that the worst 31% security breaches happened due to inadvertent human errors the rest 20% are caused by the deliberate misuse of system by employers (PWC 2014). Most enforce security policy and the best adequate information security actions can be taken by companies but if the employers are not trained in regards to this real awareness can never be achieved. So the companies will remain less protected in regards to Information security policies and IT risks. The ultimate success of the security measures depends on the end users actions which has been stated by Rastogi and von Solms in the year 2012 (Stanciu & Tinca 2016).
b) Information Security Issue
Considering different organisations of today majority of them dependent on information security for survival (Knapp et al. 2006). The higher number of threats and ferociousness attacks has made the data protection a challenge. To avoid biggest risk business organisations should ensure the information system of theirs is running well. In this context information security means the safe storage of data. It is a careful balance of user access and information safeguard. Attacks can come from either external or internal firms. The attacks can be either way either the denial of service or damaging the entire framework. The threat to information can be of any forms like natural, man-made disasters, errors of employees, acts of competitors, hackers and viruses. Viruses, worms, hackers, employee’s abuse and misuse created the need for understanding and implementing the need for better quality information security. If the organisation fails to succeed in their information security issues and reduce information security issues diligently organisations will encounter into problems. Information security issues are ignored by top managers, middle managers and employees. Many organisations lose their trust for the reason of failure in information security. The fundamental building-blocks for the development of information Security as identified by Fitzgerald are: Information security policy document; Allocation of security responsibilities; Information security education and training; Reporting of security incidents; Virus control; Business continuity planning process; Control of proprietary copying; Safeguarding of company records; Compliance with data protection legislation”. To handle the problem of information security breaches effectively more importance should be given to human, organisational and training factors. (‘IT Security Consultancy in Malaysia: Hindrances and Impacts’ n.d.). The table listed below states the top five information security and risk management issues the organisations dealt with during this era (‘Information security issues, strategies and spending in 2010’ n.d.).
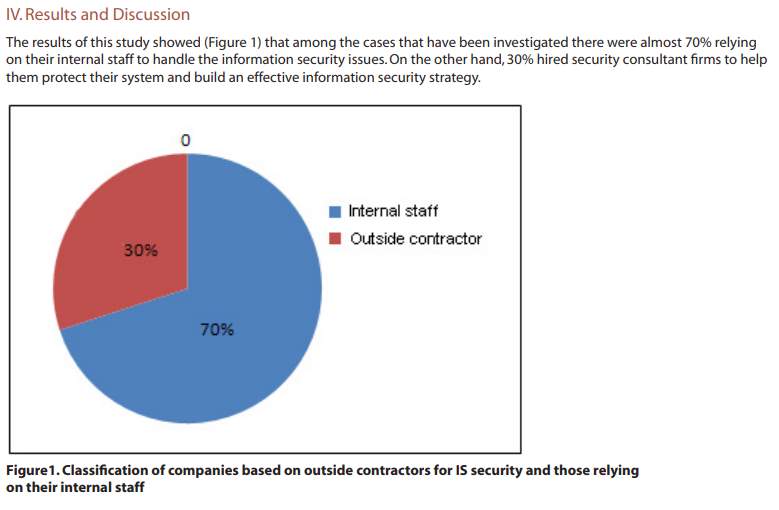
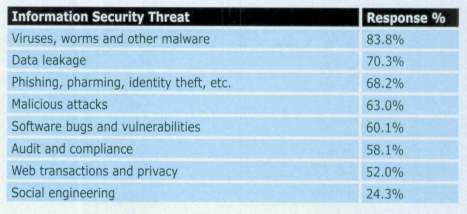
The table listed below states the information security which must be addressed as per priority:
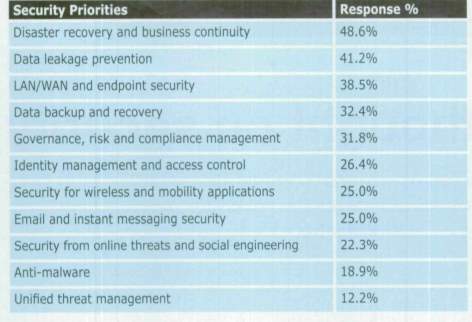
c) Information Security Policy
Information security policy development is a critical activity. Well drafted information security policy is the credibility of the complete information security program of an organisation. (Kadam 2007) . An information security policy will supply the organisation clear high level and comprehensive strategy to shape security problems in relation to business objectives. By accepting the best policy framework the organisation can assess, improve and develop information security policy. A better framework can bring in better communication among information security teams and management executives and its owners. This also provides better understanding of basics required for effective information security. Due to the nature of open computer environments the risks are higher in number. Policies remain relevant and applicable for a period of time and does require revision when fundamental changes or operational objectives of organisation differs (‘Information Security Policy Framework: Best Practices for Security Policy i…’ n.d.).
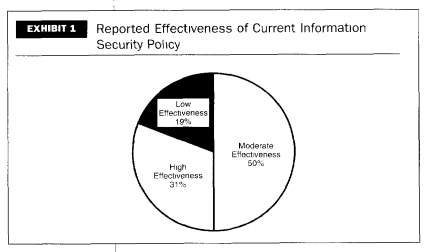
d) Information Security Awareness
Each and every organisation has its own state of the art hardware and network security protection but it takes just a second for an uneducated person to download virus which will compromise the system of the organisation which in turn accidently publishes confidential information. It can be either intentional or unintentional errors caused by security incidents of employees which underline the importance of security awareness program. National Institute of Standards and Technology (NIST) states information security awareness as “Awareness is not training. The purposes of awareness presentations are simply to focus attention on security. Awareness presentations are intended to allow individuals to recognize IT security concerns and respond accordingly”. For the overall information security infrastructure implementing security awareness program is a must. (Wilson & Hash, 2003).
One of the best way followed in organisations is to communicate security information policies, tips and best practices to everyone in the organisation. Information security awareness is not about training but designed to change employee’s behaviour. Security awareness program must run alongside in conjunction with information technology, hardware and software to avoid threads to organisation. A successful security awareness program should state all details to users about the use of information technology systems and data assets. The information security policy and procedures must be uniformly followed by everyone in the organisation. Proper education should be done and informed about information security policies and expectations (‘Developing an Information Security Awareness Program for a Non-Profit Organ…’ n.d.).
IV. Identify and interpret the security issues/threats/vulnerabilities of the given scenario:
The higher number of data breaches will be the volume of conceded record. These state in years to come there will be much more expensive attacks can happen for any organisations. Some of the traditional areas which will incur these costs are network clean-up and customer notification but additional costs will arise from newer areas which include litigation involving a growing number of parties. There are also prediction that angry customers will pressure government to introduce much more tightly secure data protection rules (Olavsrud 2017). The cause of the higher number of failure is caused by capacity issues and operational failures. During a study of top security threats perceived by organizations with over 500 employees, the top five threats are (1) deliberate software attacks; (2) technical software failures or errors; (3) acts of human error or failure; (4) deliberate acts of espionage or trespass; and (5) deliberate acts of sabotage or vandalism (‘Information Security Threats: A Comparative Analysis of Impact, Probability…’ n.d.).
A thread depends on the attacker’s degree of skills, knowledge, resources, authority and motives. Apparently, the same will remain for the information security professionals who are supposed to protect against threat. No one can expect appropriate protection lacking the skills, knowledge, resources, authority and motives. During these years threats have become a huge impact for all organisations. Computer security and information security both are supreme in running an organisation. For ensuring organisations information assets retain their accuracy, confidentiality, and availability it is highly significant to prioritise the security of their computer system. The major provider to systems security are the users which is considered to be internal threats (Chekwa et al. 2013).
Basic security responsibility must be followed by all employees. There are number of contribute to cyber vulnerabilities in healthcare sector which include real life urgent situations, tension between department priorities and budget considerations. When dealing with critical conditions health care person has no choice but to leave their work station unlocked which permit others to access important data and find potential patient safety issues. Urgent need for information can lead to conflict with best practices in relation to privacy and security. There are reports that which indicate cybersecurity at organisational level is often viewed as information technology problem not as important as high level priority. Information security professionals are under trouble in convincing healthcare organisations these types of attacks cause risks to patient care. To protect the organisation against longer reputational damage proactive measures should be taken. All sizes of healthcare organisations are under target in part for the reason of black market for medical records and valuable nature of healthcare data.
V. Suggest possible security solutions for the identified issues of the given scenario:
The present business plan which is already existing should be done in a way to protect information security which is a valuable business strategy. The preparedness plan must be divided into physical security, information security, emergency response, crisis management, and business continuity planning. As soon as the risk is realised business continuity planning will describe the steps to take. There should be systems and process in place before anything can happen. (‘Information Security Threats: A Comparative Analysis of Impact, Probability…’ n.d.).
Periodical review and evaluation of all management programs and security awareness program must be done. A survey questionnaire should be circulated among employees seeking input. During new employee orientation a brief awareness should be conducted, follow up with employees every three to six months should be done and should ask how the briefing was apparent (i.e, what they can memorise, what information need to add on etc.). Others should also be asked about the awareness programme. The security incidents that occurred before and after the programme should be tracked. If there is a higher number of reported incidents that is a positive sign. The users should be well aware of the person to be contacted in case of any suspect of security breach or incident. Spot check in a user friendly manner should be done.
This must include walking through office checking whether unattended workstations are logged in and adequate protection is given to sensitive media. Awareness materials should be distributed via computer based delivery which include intranet etc. A basic check should be done as to who reviewed the material. To those employees who have done with online material a targeted questionnaire must be given. Against each employees password a system manager must run a password cracking programme. In many cases evaluations focus deviate and end up in a wrong item. Employees are the key phase of information security programme and management support for ensuring the goal of awareness programme (Hansche 2001).
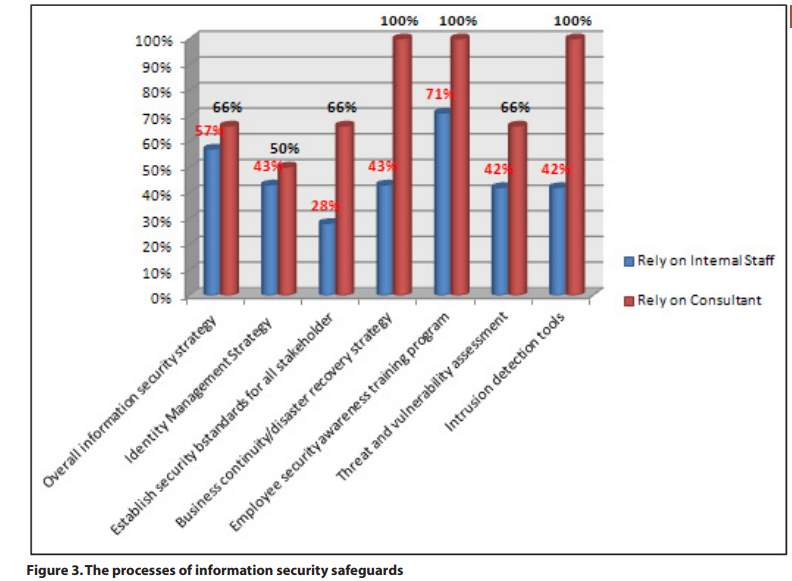
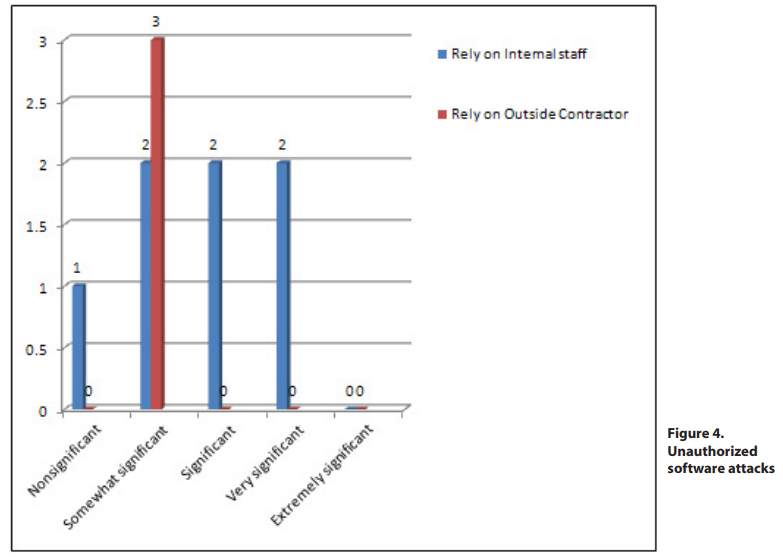
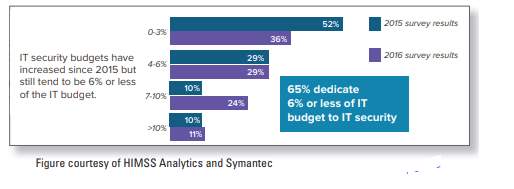
Table below displays the summary means of preparedness for information security threats.
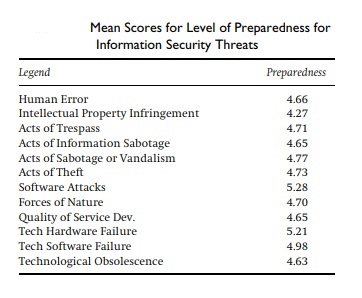
The table given below shows the organisations response to survey conducted for information security protection mechanisms:

VI. Recommend related policies to overcome the identified issues of the given scenario:
Organisations information security plan must be line item of security awareness programme. Apart from the operational and technical counter measures which is a must in protecting the system awareness and training is also essential part of it. The first priority should be given to goals of the programme, what must be achieved, then programme plan must be developed. It should be professionally presented at the management meetings (Hansche 2001).
In order to protect the resources as well as securing the important information of firms from any threats, the starting point must be development of information security policy documents (Moody, Siponen & Pahnila 2018). Further support is needed for the importance of security in computing and information systems (IS). There is no complete definition that will cover all aspects of security. It’s recognised as its important role in social and organisational dimensions. There has been a significant change in the nature of information security threats. Apparently, the incidents of information security breach remains high. Information security policy is a significant business document which will cover a wide area of security concern. This document will set out approach to managing organisations information security. The policy will be a working document which offers rules on means of information security management at the same time desired ends. The role of policy is to stressing management’s obligation and upkeep for information security (Stahl, Doherty & Shaw 2012). The organisation can use technologies like E-mail encryption, spam filtering, user training on the job and patching(Victor 2017).
VII. Conclusions
The aim of this study was to study the literature topics about information security, information security issues, information security policy and information security awareness. Apparently, identify and interpret security issues, threats and vulnerabilities. Suggest possible security solutions and recommend related policies to overcome identified issues.
The advancement of the technology plays a crucial role in organisations profitability. The main aim of information security is to secure the organisation from thread and help the business in attainment of anticipated level of consistency and efficiency by ensuring integrity, availability and confidentiality. The requirement of security specification is to recognise organisations requirement in relation to security (Istikoma et al. 2015).
References
Chekwa, C, Ogungbure, A, Mmutakaego Chukwuanu & Thomas, J, Eugene 2013, ‘Information Security Threats: What Is Public Versus Private Sector’s Perception?’, International Journal of Business & Public Administration, vol. 10, no. 1, pp. 87–97.
‘Cybersecurity in healthcare is improving, but not fast enough’ 2017, Health Management Technology, vol. 38, no. 4, pp. 12–12.
‘Developing an Information Security Awareness Program for a Non-Profit Organ…’
Dunlap, SE & Pliakos, LB 2017, ‘Healthcare cybersecurity is due for a checkup: The digitization of information has enhanced delivery of care, but it has also made data more vulnerable to attack’, New Hampshire Business Review, vol. 39, no. 15, p. 22.
Hansche, S 2001, ‘Designing a Security Awareness Program: Part I’, Information Systems Security, vol. 9, no. 6, p. 14.
‘Information security issues, strategies and spending in 2010’.
‘Information Security Policy Framework: Best Practices for Security Policy i…’
‘Information Security Threats: A Comparative Analysis of Impact, Probability…’
Istikoma, Bt Fakhri, NF, Qurat-ul-Ain & Ibrahim, J 2015, ‘Information Security Aligned To Enterprise Management’, Middle East Journal of Business, vol. 10, no. 1, pp. 62–66.
‘IT Security Consultancy in Malaysia: Hindrances and Impacts’.
Kadam, AW., awkadam@vsnlne 2007, ‘Information Security Policy Development and Implementation’, Information Systems Security, vol. 16, no. 5, pp. 246–256.
Knapp, KJ, Marshall, TE, Rainer, J, R Kelly & Morrow, DW. 2006, ‘The Top Information Security Issues Facing Organizations: What Can Government Do to Help?’, Information Systems Security, vol. 15, no. 4, pp. 51–58.
Moody, GD, Siponen, M & Pahnila, S 2018, ‘Toward a Unified Model of Information Security Policy Compliance’, MIS Quarterly, vol. 42, no. 1, pp. 285-A22.
Olavsrud, T 2017, ‘5 information security threats that will dominate 2018’, Computerworld Philippines – Online Edition, pp. 1–1.
Stahl, BC, bstahl@dmuac u, Doherty, NF., NF Doherty@lboroac u & Shaw, M, mshaw@dmuac u 2012, ‘Information security policies in the UK healthcare sector: a critical evaluation’, Information Systems Journal, vol. 22, no. 1, pp. 77–94.
Stanciu, V & Tinca, A 2016, ‘Students’ awareness on information security between own perception and reality – an empirical study’, Accounting & Management Information Systems / Contabilitate si Informatica de Gestiune, vol. 15, no. 1, pp. 112–130.
Victor, A 2017, ‘Arming your organization with cybersecurity: An information security policy is a crucial layer of security defense’, New Hampshire Business Review, vol. 39, no. 15, p. 24.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Healthcare"
Healthcare is defined as providing medical services in order to maintain or improve health through preventing, diagnosing, or treating diseases, illnesses or injuries.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




