Method of Quantifying the Financial Impact Due to Downtime Incurred from a DDOS Attack
Info: 10365 words (41 pages) Dissertation
Published: 9th Dec 2019
Tagged: FinanceCyber Security
Method of Quantifying the Financial Impact Due to Downtime Incurred from a DDOS Attack
Abstract
In the current day and age, were computing and the internet is crucial for many services, such as banking, communication, education, e-commerce, etc. Where cyber-attacks have become the norm, hearing on the news about another data-breach, or system outages due to DDOS attacks. As computers and cloud computing is getting used more and more, paired with the growth of IoT devices are allowing DDOS attacks to have a greater impact on a system or service. In this paper, I will be providing an overview of DDOS attacks, I will also be providing a method that can be used to calculate the financial impact from downtime caused by a DDOS attack.
List of Abbreviations
- DDOS – Distributed Denial of Service.
- DOS – Denial of Service.
- IoT – Internet of Things.
- Dox – Searching and releasing for private information on an individual over the internet
- VPN – Virtual Private Network
List of Figures
Table of Contents
1. Introduction Have a very thorough read through
1.2. Project Aims and Objectives
1.2.1. Discussion / Dissertation Overview
2.2. Distributed Denial of Service Attack Overview
2.2.2. Variations of DDOS attacks
2.3. Proposed DDOS Detection Mechanisms
2.4. Proposed DDOS Defence Mechanisms
2.6.2. Financial / Economic Impact
2.7. Related Work ##add two More
6. Critical Analysis of Solution
1. Introduction
A Distributed denial of service attacks (DDOS) is amongst the most popular cyber-attacks used in today’s cyber warfare. The purpose of a Distributed denial of service attack is to render a web service, such as computer system, or website/service, unavailable, this is done by means of sending mass of data, to crash a service, thwarting genuine users from accessing the web service. Distributed denial of service (DDOS) consists of many infected computer systems, which are targeted to attack a specific computer system, and is a newer more coordinated version of a Denial of service (DOS) attacks – which usually only comprises of one machine sending traffic. Making a Distributed denial of service (DDOS) much more of a powerful attack as it can send much more data, while remaining anonymous, due to the infected systems performing the attack.
Distributed denial of service (DDOS) have grown larger and larger every year causing more impacts to companies, especially those who are primarily we based. In a report, which was submitted by NoSpec, name Distributed denial of service one of the top security threats to be aware of 2017, citing attacks have hit up to almost 1.2 terabits (Nospec, 2017, p. 4). The most common and obvious impact to follow a Distributed denial of service attack is downtime of the service, however, there are many more impacts such as stock price/market value, financial, customer satisfaction, etc. The beginning section of this paper will analyse and discuss details about Distributed denial of service attack, discussing; variations of the attack, tools used and the impacts that follow a DDOS attack. In the latter sections of this paper, there will be a more in-depth discussion into the financial impacts following a Distributed denial of service attack. I will also provide a method to calculate the financial impact of the downtime of a DDOS attack.
1.1. Problem statement
As discussed above Distributed denial of service (DDOS) attacks are becoming larger with a greater impacts year by year. The impacts are becoming larger due to the sheer growth in magnitude of IoT devices, allowing for larger botnet sizes. With large Distributed denial of service attacks happening on an almost monthly basis, which such attacks as the Dyn attack, KrebsOnSecurity, etc. However, these attacks are occurring on a regular basis, without relatively small amounts of research done to calculate the financial impacts seen specifically during the downtime of an e-commerce website. In this paper, I will provide real-life case studies of attacks performed on e-commerce websites, finally I will provide a method of calculating the financial impact to a company during downtime.
1.2. Project Aims and Objectives
- Perform an overview of Distributed denial of service, and along with the various types of DDOS attacks, detection and defence solutions that can be used.
- Perform research and compile a list of real-life case studies on e-commerce businesses that have been the victim to DDOS attacks.
- Perform research into the financial effects that distributed denial of service attacks have on an e-commerce business.
1.2.1. Discussion / Dissertation Overview
In the beginning section of this project, I am going to perform an overview analysis of Distributed denial of service (DDOS), along with the different variations of Distributed denial of service attacks that attackers perform. Following the analysis, I will describe proposed methods of DDOS detection, along with potential mitigation methods, which can be used to protect companies and computer systems before and during attacks. I will also be providing an analysis in the ways in-which the downtime caused by distributed denial of service attacks can financially impact a company. I will be calculating how downtime financially impacts an e-commerce business by consider the affect to customer loss, stock loss, revenue loss, etc. I have chosen to use primarily e-commerce due to the majority – if not all, of their business being conducted purely over a network, meaning the lack of availability following an attack is more damaging, compared to a company whose business is primarily brick and mortar stores.
My deliverables for this research project is to display a clear detailed overview of Distributed denial of service and the attacks performed. Along with proposed detection methods, and proposed mitigation methods, both supported with peer-reviewed literature. This will allow the reader to understand the subject and area around distributed denial of service. Next, as stated above I will be researching the financial affects during a company outage, I will be using customer loss, stock price and revenue loss to quantify the financial impacts caused by attacks.
2. Literature review
2.1. Cyber Attack Overview
2.1.1. Cyber Security
Cyber security has been a concern since the conception of computers and networks, it was Gene Spattord that said – “The only truly secure system is one that is powered off, cast in a block of concrete and sealed in a lead-lined room with armed guards” (Dewdney, 1989, p. 110). The need for good cyber security has grew exponentially since the occurrence of mainstream home computers around the 1980’s, such as; Apple 1, IBM 5150, etc. along with these computers came a growing access to the internet in the late 80’s / early 90’s. These had a profound impact on the cyber space and the ability for people to access and learn how to attack these new systems.
As today’s society becomes more dependent on computes for many day-to-day tasks, it is more important now more than any other time to increase cyber security, to prevent more attacks from taking place. Chad nelson states “Today’s world is becoming increasingly dependent on computers and increasingly connected through the Internet. These two facts have created a new battlefield for countries to wage war on” (Nelson, 2011). Chad Nelson wrote a paper called “Cyber Warfare: The New Battlefield”. In this paper, He proposes two types of defence technique for defence against cyber-attacks:
- Active Defense – “Active defense take action to prevent or retaliate when the system is attacked”, This method introduces both preventative and retaliation technique for cyber-attacks. (Nelson, 2011, p. 7).
- Passive Defence – “Passive defence don’t search for problems on the computer. Instead, they try to prevent the computer from being attacked in the first place”, This method employs the use of Anti-virus, firewalls, etc. to prevent the attack from ever happening. (Nelson, 2011, p. 4).
2.1.2. Cyber-Attacks
Cyber-attacks are almost always driven by some form of motivation, e.g. financial or political, the nature / motivation behind a cyber-attack have been categorised and documented in an article written by Robin Ghandi et al, called “Dimensions of Cyber-Attacks: Cultural, Social, Economic, and Political” (Ghandi, et al., 2011). As you can read from the title of the article, the author has divided cyber-attacks into Cultural, Social, Political and Economic.
- Politically motivated attacks – These are known as attacks which are used to spread political propaganda, steal money to fund their activities, etc. Including Protesting government actions (Website defacing / DDOS), Dissatisfaction with public documents, policy or law (Data Breach, Dox), retaliation against physical violence (Website Defacing, DDOS). (Ghandi, et al., 2011, p. 2)
- Socially / Culturally motivated attacks – These are described as “viewed as competition between individuals or groups over incompatible goals, scarce resources, or power,”. These types of attacks have been seen between Taiwan – China, Russia – Georgia. (Ghandi, et al., 2011, p. 3)
- Economically motivated attack – These are attacks that are motivated via greed or financial gain. An example given in the article is of Ukrainian cyber attackers stealing $172,00 in goods. (Ghandi, et al., 2011, p. 4)
As You have read above, cyber-attacks have motivations behind, to further discuss cyber-attacks, there have been studies to categorise cyber-attacks by type of attack, rather than the motivation behind the attack. In a taxonomy on cyber-attacks and their effects written by Ian M. Chapman called “Taxonomy of Cyber Attacks and Simulation of their Effects” (Chapman, et al., 2011), He classified cyber-attacks into three separate tiers, these are;
- Tier 1: “No network or computer access” – These are attacks that need no special access privileges; the Tier 1 attacks are: Denial of service, Distributed Denial of service, Buffer-Overflow attack and Phishing. (Chapman, et al., 2011, p. 2)
- Tier 2: “User access with limited privileges” – These are attacks where the attacker has access to a computer with limited privileges; the tier 2 attacks are: Password Hacking, Sniffing and Nuisance attacks. (Chapman, et al., 2011, p. 3)
- Tier 3: “Root Access / Administrative Privileges” – These are attacks that allow an attacker to gain root access to a victim computer; the tier 3 attacks are: Backdoor, Rootkit, Spyware and Trojan Horses. (Chapman, et al., 2011, p. 4)
It was John D. Howard that categorised a cyber-attack as “an event that occurs on a computer or network is part of a series of steps intended to result in something that is not authorized to happen”. This was stated in a paper, “A Common Language for Computer Security Incidents” (Howard & Longstaff, 1998), the author categorises the intended results for a cyber-attack, this is what an attacker wants to achieve from a cyber-attack; Increased Access, Disclosure of information, Corruption of Information, Denial of Service and Theft of Resources (Howard & Longstaff, 1998, p. 12).
2.1.3. Cyber-Attack Impacts
Former U.S secretary of defence said – “A cyber-attack perpetrated by nation states or violent extremist’s groups could be as destructive as the terrorist attack on 9/11. Such a destructive cyber-terrorist attack could virtually paralyze the nation. “(Panetta, 2011). Regardless of how great or innovative cyber security has become cyber-attacks can still happen and can cause devastating impacts when they are performed. Below are studies performed to quantify the damage caused once a cyber-attack hits;
There are many impacts that can be found during or after a cyber-attack has taken place. In a paper written by Hemraj Saini et al, called “Cyber Crimes and their impacts: A review” (Saini, et al., 2012). The aim of this study was to discuss the various impacts that follow a cyber-attack. The author categorised the impacts into three types of impact;
- Potential Economic Impact – This the financial impacts on a country or business following a cyber-attack, the author discusses that a cyber-attack on one region or country could potentially cause disruptions to the rest of the world’s financial markets. (Saini, et al., 2012, p. 4)
- Potential Market Value Impact – This is the companies value to their respective market, and the impact a cyber-attack can have on this value, the author notes that knowledge of a cyber-attack taking place can have a noticeable impact on a company value within its market. (Saini, et al., 2012, p. 4)
- Impact on consumer trust – Hemraj notes “the slightest perception of security risk or amateurish commerce seriously jeopardizes potential business”. Once a cyber-attack becomes public knowledge it can make users turn to other service which may be deemed safer. (Saini, et al., 2012, p. 5)
A main impact caused by cyber-attacks is economic impact – this isn’t just about money, it can include market value, stock price, etc. This has been quantified by the United states in a report named “The Economic impact of Cyber-attacks” (Cashell, et al., 2004). This report was submitted to United States congress in 2004, even though this report is over a decade, old a lot of the data shown is still relevant in discussion on the financial impact of a cyber-attack. Included in this report is discussion into the impact on the Market values of attacked firms, the authors include many previous studies to describe the impact a company can face on its market value. In the latter sections of this report is further discussion into the economic impacts of a cyber-attack.
Although the previous study was very dated (almost 14 years old), it was a descriptive study which still has relevance in today’s discussion into economic damage. However, in a more recent study which was written by McAfee, called “The economic impact of cybercrime and cyber espionage” (McAfee, 2013). This study is incredibly thorough, the author has categorised the financial cost of a cyber-attack into two categories; United States and Global costs, with comparatives to other forms of crime e.g. Car crashes, drug trafficking. In the later section of this report, the impact of a cyber-attack is discussed, which includes further financial statistics.
2.2. Distributed Denial of Service Attack Overview
2.2.1. What is a DDOS Attack
“Distributed DOS [Denial of Service] (DDoS) attacks are brute force high volume data traffic attacks which are launched against a target to render services running on the target device unavailable to legitimate users of those services” – (Dooley & Rooney, 2017). In a recent article released by NoSpec which detailed the biggest cyber security threats to expect in 2017 (Nospec, 2017). One of the biggest threats which was discusses in this study was Distributed Denial of Service (DDOS) attacks. The authors note that in the fall of 2016 was the largest DDOS attack seen in history, however, only a month later that attack was surpassed by an even larger DDOS attack, the author noted about this trend in size of attack – “Based on 2016’s trends, we expect in 2017 to see more frequent and severe DDoS incidents.”(Nospec, 2017).
A DDOS attack are usually performed with the use of a botnet, Chao Li et al define a botnet as “A network of bot under the control of the Botmaster and usually used for malicious activities” (Li, et al., 2009, p. 1). botnets can be used for many malicious activities, i.e. distributed denial of service attacks, spam, phishing, steal sensitive data (Li, et al., 2009, p. 2). The lifecycle of a botnet has many steps to recruit new bots and using the botnet, this has been documented in a recent report by Nabil Hachem et al, the first step being,
- Spreading infection via malware: This can be done in various ways, such as; software vulnerability, instant messaging, file sharing network and other botnets. (Hachem, et al., 2011, p. 2)
- Command & Control botnet This is the method in-which the attacker(s) communicate with the bots, i.e. HTTP, P2P, IRC. (Hachem, et al., 2011, p. 2)
- Botnet Application: This is the intended use the attacker has for the botnet, such as; spamming and spreading malware, espionage, DDOS, etc (Hachem, et al., 2011, p. 2).
Botnets mainly consist of Internet of Things device (IoT), Kimberly Hengst defines IoT as “smart devices interconnected through the Internet. This interconnected network has been called the Internet of Things (IoT).”. IoT is made up of many devices, such as, televisions fridges, C.C.T.V, etc. (Hengst, 2016, p. 1). IoT device are exponentially growing year by year, this has been research in a paper called “DDoS through the Internet of Things” (Hengst, 2016), which discusses the forecast growth, along with the estimated amount of devices that could be used in an attack.
There are two main models of how DDOS attacks are structured, the first being an Agent/handler model. In the book named – “Network Security: Current Status and Future Directions” by (Mitrokotsa & Christos, 2007). In this book, the authors categorise a DDOS attack as “an attack designed to render a computer or network incapable of providing normal services” – (Mitrokotsa & Christos, 2007, p. 118). The first model of a DDOS attack is the Agent Handler model:
- The real attackers – The is the attacker(s) that are behind the attack, not necessarily the people performing the actual attack.
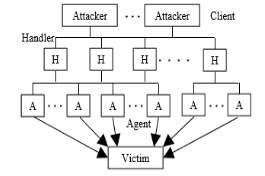 The Handlers / Masters – Machines which contain a special program that means the machine can control multiple hosts / agents.
The Handlers / Masters – Machines which contain a special program that means the machine can control multiple hosts / agents.- The attack demon agents – These are comprised devices / machines infected with a program, these devices are responsible for performing the attack, this is done by the infected device generating numerous packets for the intended victim.
Figure 1 (Specht M. & Lee B., 2004)
 The victim / target host – This is the target for the DDOS attack. (Mitrokotsa & Christos, 2007, p. 5)
The victim / target host – This is the target for the DDOS attack. (Mitrokotsa & Christos, 2007, p. 5)
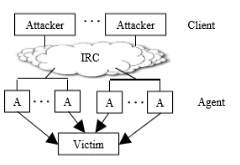
The second structure which is called the IRC based model, this model is almost identical to the agent/handler model above. However, this method removes the handler machines, and instead uses the IRC (Internet Relay Chat) protocol to communicate with the attack agents (Specht M. & Lee B., 2004) – see figure 2.
Further description of the selection process can be seen in the paper. Distributed Denial of service attacks (DOS) are possible due to there being many inherent internet defence issues, such as;
Figure 2 (Specht M. & Lee B., 2004)
- Highly Independent Internet Security – While individual networks / nodes may have their own computer security implementations, which is up to the owner to implement, the internet doesn’t have a standard DDOS protection used by the internet as a whole.
- Inherently Difficult to Detect DOS Attacks – Due to DOS traffic looking similar to real-user traffic it is inherently difficult to distinguish an attack from a flash crowd of users. Along with the attacker methods of anonymity such as; IP Spoofing, VPN’s, etc. Also Distributed Denial of Service utilize many, many hosts making the discovery of the source extremely hard.
- Limited Resources – The target of a DOS / DDOS such as, a network or server, only has a limited number of connections available before it will start denying requests or become unavailable all together.
- Automated Tools – The DOS & DDOS tools that attackers have made available for virtually anybody to use. These tools automate the process and the actual DDOS attack, making it extremely fast, without having any technical skills.
- Target rich environment – The internet is extremely large with many, many hosts available for attackers to attack. (Mitrokotsa & Christos, 2007, p. 5)
There are many reasons an attacker would perform a Distributed denial of service attack, these reasons have been documented in a paper, written by Abdulaziz Aldaej called “Information Security and Distributed Denial of Service Attacks: A Survey” (Aldaej, 2017). The many reasons the author has discussed that an attacker would perform a DDOS attack are;
- Economical – “These types of attacks are motivated by economic or financial considerations.”, the examples the author gives are; turning customers away from certain websites, forcing customers to buy their own product or services in absence of rival, disseminating mistrust for particular web services. (Aldaej, 2017, p. 3).
- Political – These are attacks that can be used to promote political views, DDOS attacks can also be used to create amnesty between political oppositions.
- Ideological considerations – This type of motivation is where an attacker uses a DDOS attack to promote their own ideological views, such as; religious views, governmental views, freedom of speech, etc.
- Extortion or Ransom – these types of attackers threaten to attack a company or debilitate their services unless their demands are met.
- Personal feuds – This type of attacker uses a DDOS attack to inflict losses on his/her opponent.
- Cyber Warfare – This is the type of attack that is performed by intelligence agency, military organisation, or non-state trying to wage war against the enemy. (Aldaej, 2017, p. 3)
2.2.2. Variations of DDOS attacks
Here are many different types of Distributed denial of service attacks (DDOS), there are many variations based on targets, protocols used, etc. In a paper, written by researchers from Princeton University, called – “Distributed Denial of Service: Taxonomies of Attacks, Tools and Countermeasures” (Specht M. & Lee B., 2004). The authors of this paper performed a taxonomy of the different types of DDOS attack. The authors of this paper have classified two categories that the different attacks fall into, 1. Bandwidth depletion attacks, these are attacks which flood the victims network to prevent legitimate users, such as; (Specht M. & Lee B., 2004, p. 3)
- UDP Flood – This is where a large amount of User Datagram Protocol packets is sent the victims network or system. The system will then try to process all the UDP data, to see what applications have been requested. If no applications have been requested, it will send an ICMP ‘unreachable’ message. With enough UDP packets sent the system will be unavailable to legitimate users.
- ICMP Flood – This is where a large amount of ‘ping’ messages are sent to the victim’s system, forcing the system to respond, using up all of the bandwidth.
- Smurf Attack – This is where the attacker’s send packets to a network amplifier, with a spoofed return address. The system then send’s the amplified packets to all systems on the network, which all then send a packet back, causing the original packet to be amplified 10’s of 100’s of times.
- TCP – SYN Attack – This is where the attacker instructs the zombie machines to send lots of fake TCP requests, making the server respond to many connection requests, causing the processor resources to be used up, causing it to become unavailable
- PUSH – ACK Attack – This is where an attacker will send a TCP packet with the PUSH and ACK bits set to one, meaning the server has to unload the whole TCP buffer and respond when done, repeating this many, many times can cause the system to become unresponsive.
- Malformed Packet Attack – This is where an attacker orders the zombie machines to send incorrectly formed packets to the victim’s system to crash it.
While the old style of Distributed denial of service attack used to be called Denial of service (DOS), DOS attacks usually only consisted of one machine been used to perform the attack. However, the newer style is Distributed denial of service attack, utilizes many machine / devices to send traffic to the victim, increasing the power tenfold. Many Distributed denial of service attacks are performed using a botnet, Nazrul Hoque et al defines a Botnet as “A botnet is a collection of many malware infected machines called zombies that are controlled by a malicious entity called the botmaster” – (Hoque, et al., 2015). In a paper called “Botnet in DDoS Attacks: Trends and Challenges”, In this paper there is an overview of DDOS attacks, along with a discussion on the life cycle of a botnet. In the latter section of this paper is a taxonomy in the different types of live botnets in use. Along with the information about these botnets.
2.2.3. DDOS Tools
Distributed denial of service attack is performed the majority of the time via an automated tool, which can be used by attackers without having to be tech savvy. In a paper called “Classification of DDoS Attack Tools and Its Handling Techniques and Strategy at Application Layer” (Mahadev, et al., 2016). The authors aim to summarise data about many different existing DDOS attack tools. This paper includes a classification of many existing tools used by attackers in DDOS attacks, such as; Stacheldraht, The mstream, Knight, etc. Along with a brief description on what each tool does. Another paper similar to this topic, the paper is called “Characterization and Comparison of Distributed Denial of Service Attack Tools” (Kaur, et al., 2015), this paper discusses the different attributes of DDOS attack tools, such as; types of interface, attack rate dynamics, attack models, operating systems supported, etc.
2.3. Proposed DDOS Detection Mechanisms
DDOS attacks are tough to detect as most attacks mimic real world traffic. However, there are many studies of proposed detection mechanisms and techniques. In a survey performed in 2017 by researchers from ABES Engineering College called “ (Kamboj, et al., 2017), where many different detection techniques were discussed, along with methods on how to detect many different forms of attacks. The discussed detection methods were;
- IP Traceback – This is a method used to determine the true IP of an attackers. This method involves two schemes; Reactive, this is performed while the attack is active. Along with Proactive, this method is performed as the attack is active.
- Packet Marking – This is where packets are marked as they pass through the router.
- Entropy technique – This is a mechanism that helps a server determine between flash traffic and DDOS traffic packets.
- Signature based detection – Using a set of rules or pre-defined knowledge which given a pattern of data can decide if the traffic is malicious.
- Anomaly detection – detects events that go against normal system behaviour. (Kamboj, et al., 2017, p. 3)
In a paper, written by A. Rukavitsyn, called – “Self-learning Method for DDoS Detection Model in Cloud Computing” (Rukavitsyn, et al., 2017). In this paper, the author proposes a self-learning solution, this method of detection is split into two steps; first the incoming traffic is split into legitimate and malicious traffic, traffic is then sent through the learning algorithm to be re-learned. Testing this solution has shown improved detection, with less false positives.
Another proposed solution for DDOS detection is discussed in a paper written by K. Garg (Kanwal & Chawla, 2011). This solution proposes many different concepts that utilization data-mining to detect and prevent DDOS attacks on a network. In a paper, written by J. Kang, called “Protect E-commerce against DDoS Attacks with Improved D-WARD Detection System” (Kang, et al., 2004). Discussed in this paper is a method of detection of DDOS attacks aimed at e-commerce sited, the proposed detection solution utilises an improved D-WARD algorithm paired with a CUSUM algorithm for detection. The results from this method of detection showed that this method is more efficient at detecting and attack, along with being able to be adapted to more complex networks.
2.4. Proposed DDOS Defence Mechanisms
As stated above DDOS attacks can be hard to detect, however, once they are detected there are many methods that can be performed to mitigate the effects to the victim’s network. Here are some methods and proposed methods of how to mitigate a live DDOS attack. In a paper, written by Md. Khamruddin, called – “A Rule Based DDoS Detection and Mitigation Technique” (Khamruddin & Rupa, 2012). The author Proposes a three-step approach to mitigating a live attack. The first proposed step is to monitor the victims network for patterns, until an attack is detected, then the next step is to use a NAT (Network Address Translator), to spread the load of the attack out. The final proposed step is to determine the type of DDOS attack and roll out a mitigation tactic to match.
In a paper written by LI Lei-Jun, from the Chinese Academy of Sciences, called – “A New Type of DDoS Defence System Study” (Lei-Jun, 2010). In this study, the author proposes a solution which utilizes honeynet and honeypot technology, along with an intrusion detection system. This method of using honeypot and honeynet is useful as it keeps logs of everything, this allows for the study of the attack and how it interacts with the victim’s system. Another solution, which was presented at a conference at China in 2009, called – “An Adaptive Control Mechanism for Mitigating DDoS Attacks” (WU, et al., 2009). In this solution, this is a chart-based threshold is in place, which is designed to allow as much as possible legitimate traffic through, while not exceeding the set threshold. This is done by monitoring the victims network, to find suspicious traffic. Even though the studies performed are simulated, the results from the studies are shown to be very effective.
2.5. Future Trends
##Finish this
2.6. DDOS Impacts
Impacts from cyber-attacks are almost unavoidable, no matter how good a company’s cyber security is they can still succumb to a cyber-attack. However, they can be mitigated, but cannot be completely removed. Distributed denial of service attacks can have serious impacts for an online business, such as; Downtime, loss of service for a company can lead to many impacts. Economic loss, attacks can lead to a financial loss to a company, i.e. stock price loss, revenue loss, etc. Along with other impacts, e.g. customer loss, reputational loss.
2.6.1. Downtime
As seen above cyber-attacks in general can have dire effects on a victim’s network and business, as-well as having a grave effect on the country. “The availability of Internet is very critical for the socio-economic growth of the society” (Sachdeva, et al., 2010), as people’s reliance on the internet has grown overtime, the damage attacks that make services unavailable has a greater impact. In a review that was written in 2008, the author discusses various aspects of DDOS attack, such as; defence and vulnerabilities. The author, then displays numerous DDOS attacks on important websites, with data about the impact the attack caused to the website.
A DDOS attacks main purpose is to cause downtime to a system making it unavailable to users trying to access the service. In a paper written in 2012, called “Recent DDoS Incidents and Their Impact” (Sachdeva & Saluja Kumar, 2014), this paper provides an in-depth overview of DDOS. In the latter half of the of the paper, the author has done a taxonomy of DDOS attacks around the time of the paper and their impacts on the victim’s service. The main takeaway from this paper is that downtime is a major impact to a business, seen in this paper is a timescale of downtime from 10 hours to 2+ days.
In a paper called “Impact Analysis of Recent DDoS Attacks” (Ketki, et al., 2011), in this journal article, the author first writes a brief overview of DDOS along with the type of attacks that can be done with DDOS. The author discusses recent DDOS attacks, which He has created a table displaying many recent DDOS attacks, which had many different targets. The table also contains the date in-which the attacks occurred. The impacts of these attacks are also displayed, the impacts range from a short power outage, to causing disruptions to millions of users.
2.6.2. Financial / Economic Impact
As seen above downtime is a major impact of a DDOS attack, however, another impact stemming from a DDOS attack is the financial aspect of the attack. There are many, many variables when calculating financial loss incurred by downtime via a DDOS attack, such as; loss of business, attack mitigation and recover, customer loss, etc. These all have significant financial cost and impact to an e-commerce business, who do the majority – if not all – their business online. The cost to a business from a DDOS attack has been studied, in a survey published by Incapsula called “Incapsula Survey: What DDoS Attacks Really Cost Businesses” (Incapsula, 2014). In this paper, the author discusses the scope of DDOS attack, the business impact, along with mitigation techniques.
Stock price and market value of a victim is an impact from a DDOS attack, which can cause serious losses to a business. In a recent paper written by researchers from the University of Twente, called – “Analysing the Impact of A DDoS Attack Announcement on Victim Stock Prices” (Abhishta, et al., 2017), they performed a study on thirty-five companies from various infrastructures and types. “In most cases we do not see a negative effect on the victim stock prices”, this study found that no significant impact on a victim’s stock price from an attack alone.
In another study which focuses on the market value of the firms following an attack, called “The impact of Denial-of-service attack announcement on the market value of firms” (Hovav & D’Arcy, 2003), this study focused on two major stock exchanges NASDAQ and the New York Stock Exchange (NYSE). The results of this study found that information-based websites, such as, AOL, Fox, Microsoft, etc. found no significant impact to their value. The research suggested that no significant impact is found following a DDOS attack, however, companies that are internet-specific e.g. get more that 50% of their business from the web, had a greater impact following an attack compared to non-ecommerce websites.
2.6.3. Other Impacts
##add impacts like customer reputation etc.
2.7. Related Work
Thomas D¨ubendorfer et al wrote a paper called “An Economic Damage Model for Large-Scale Internet Attacks” (D¨ubendorfer, et al., 2004), in this paper the author divides up the various aspects needed to calculate financial losses incurred from an attack, these are;
- Downtime – The cost experienced by the business when their service is offline.
- Disaster Recovery – The cost of the work and materials to get the system back up and running.
- Liability – This is the loss incurred to the business by not being able to fulfil contracts from third-parties who may demand compensation.
- Customer Loss – This is revenue loss for each customer who cannot access the service and go elsewhere.
This is a great paper discussing a method for calculating the total economic loss of all large-scale attacks. However, my paper focuses on DDOS attacks along with the economic impact of only downtime.
Rangarajan Vasudevan et al wrote a paper called “MIDAS: An Impact Scale for DDoS attacks” (Vasudevan, et al., 2004). In this paper, the author discusses a proposed method of calculating the impact of a DDOS attack called M.I.D.A.S, this method is;
- SLA Violation Cost – Service level violations, aka support tickets, a company may provide compensation if they are not met within a specified time.
- Risk Cost – The cost of covering the risk of a DDOS attack, i.e. customer revenue, whether the customer decides to take their business else-where.
- Risk of Customer Leaving – This is the cost of the risk of customer leaving due to DDOS attack. (Vasudevan, et al., 2004, pp. 2, 3).
David A. Patterson wrote a paper, called “A Simple Way to Estimate the Cost of Downtime” (Patterson, 2002). In this paper the author discusses a simple method in-which a rough downtime cost can be estimated. The author calculates;
- Employee cost per hour.
- Fraction affected by outage.
- Average income per Hour
- Fraction of income affected by outage (Patterson, 2002, p. 3).
However, this study is quite outdated, and fails to account for other costs within the business, which can cause further financial damage to the company.
3. Problem Analysis
3.1. Scale of DDOS attacks
Cyber-attacks cause major impacts to businesses every year, there is an issue when attempting to calculating the impacts to expect, there are many unquantifiable variables to consider, i.e. customer reputation. In a survey, performed on 359 businesses, reported average losses from 347,000 – 497,000 – depending on the size of the company (Kaspersky Lab, 2017). The survey also found that on average the companies were victim to between 2 and 5 cyber incidents within the previous 12 months (Kaspersky Lab, 2017, p. 4), with the average consequence and recovery from an attack costing ~$381,000 (Kaspersky Lab, 2017, p. 9). The reported total costs of cyber-attacks to the United Kingdom are estimated to be £7.21 Million, in the 2017 financial year (Richards, et al., 2017, p. 13).
Since the first case of a largescale Denial of service (DOS) attack, which occurred in 2000 called ‘Rivolta’ (Bene, 2016), performed by hacker named ‘MafiaBoy’. This attack was responsible for bringing down many large commercial websites at the time, e.g. Yahoo!, Amazon, Dell, CNN, etc. With damages estimated to be around $1.2 Billion. Since attacks such as these, Denial of service attacks have grown more and more common and powerful. This growth is due in-part to the sheer number of IoT devices and more sophisticated botnets. With the large amount of low cost IoT devices, were security isn’t a priority, this has allowed attackers to upload their malware to the device, recruiting then to be part of botnet, which end up being used as part of Distributed denial of service.
One of the most prolific cyber-attacks, which occur on a daily basis, are distributed denial of service attacks. The reason DDOS attacks are so wildly used is due to the ease in-which attackers can perform the attack, either using a simple, user-friendly tool, or paying a DDOS service to perform the attack. A study into the cost of DDOS attack found a service could be bought on the ‘underground’ for as little as $5 – $1000 depending on the size and strength of the attack needed (Symantec, 2017, p. 51). Distributed denial of service attacks are increasing on a yearly basis, in a survey published by Accenture, which showed that amongst the survey participants, DDOS attacks had raised from 49 in 2016 to 53 in 2017 (Richards, et al., 2017, p. 23). With another study showing the growth of these DDOS attack, with only 10% of attacks reaching over 50Gbps, whereas, in 2017 this has grown to 42% of attacks reaching 50Gbps and above (A10 Networks, 2017).
In a press release in 2016 found that in the previous 18 months, a reported 124,000 distributed denial of service attacks per week were discovered (Arbor Networks, 2016). The press release also revealed there were 46 documented attacks in 2016 reaching above 200 Gbps – with a reported peak of 480 Gbps, while only 16 attacks in 2015 were able to reach 200+ Gbps (Arbor Networks, 2016). There was an exponential growth of DDOS attacks during 2017, with 6.1 million attacks documented throughout the year, averaging 22,426 attacks per day (Arbor Networks, 2017, p. 2). It was reported that the number of organisations experiencing between 6 -25 attacks a year has grew from 14% in 2015, to 55% in 2017 (A10 Networks, 2017, p. 3). Studies have shown the growth of DDOS peak sizes has been growing annually, in 2016 an increase of 82% was seen compared to 2015 (Verisign, 2016, p. 5), with a 26% increase in 2017 compared to 2016 (Verisign, 2017). A leading cause for the growth of DDOS attacks is in-part to blame on the growth of IoT allowing for larger botnets.
Internet of Things is the name given to the internetwork of internet connected devices, which is estimated to consist of 15.4 billion devices in 2015 (Lucero, 2016, p. 5), and 31 Billion devices by 2018 (IHS Markit, 2018, p. 5). Whereas, Intel predicts the IoT to reach 200 billion devices by 2020 (Intel, 2017). With sheer number of devices now and coming in the future connected to the internet, along with the weak security of these devices (Ballano Barcena & Wueest, 2015), are allowing hackers to recruit the IoT devices to a botnet to be maliciously used.
It is very hard to determine just how many botnets are around, or how many devices are contained in a botnet, however, taxonomy studies have been performed of botnets (Hoque, et al., 2015), with a botnet called Conficker, containing 10.5 million devices (Hoque, et al., 2015, p. 2252). One of the most prolific botnets ever seen used for attacks is called Mirai botnet, in a paper written by Antonankakis et al documenting the Mirai botnet, found that the bot consisted of 600,000 devices, and was responsible for many high-profile attacks, such as, Krebs on Security, OVH, Dyn (Antonakakis, et al., 2017, p. 2) – with attacks initially exceeding 600 Gbps, and reaching as high as 1.1 Tbsp.
3.2. Impact Problem
A by-product of a successful DDOS attack is loss of service to the victim aka downtime. Outages caused by DDOS can range greatly, however, a survey has shown that 39% of attacks last for one hour or less, with 16% experiencing outages for four hours and only 6% experiencing outages for 8 or more hours – with the average attack lasting for 2.3 hours (Pescatore, 2014, p. 14). However, another study showed that 1 in 3 attacks lasted 1-2 days (Neustar, 2015, p. 5). Even-though, downtime is a major issue, the impact caused by the outages is what can really impact a business e.g. financial loss, customer loss, stock price drop, etc.
A high-profile 35 example of how downtime can impact a company, was seen in an attacked aimed at Dyn, a DNS provider, which occurred on October 21st, 2016 (Hilton, 2016). The attack was performed using the Mirai botnet, which was estimated to contain over 100,000 bots sending 1.2Tbps of data, causing Dyn to go offline. Dyn DNS service was unavailable for a combined 3.5 hours – two separate attacks occurring within hours of each other. The impacts suffered to Dyn due to their outage are; customer outage, there customer’s business’ suffered outages, such as, PayPal, Twitter, Spotify, etc (Sreekanth, et al., 2016, p. 2). a study was performed to quantify the impacts, which found that following the attack Dyn lost 6,000 domains, or 4% of the total domains (Paul, 2017).
The financial impact to a business during outage incurred from a DDOS attack is one of the major issues a company faces, once a DDOS attack has hit. A report published by Neustar in 2015, found that 22% of companies lose between £50,000 – £99,000 during outages during peak hours, while 16% of companies reported peak losses of £100,000+ in revenue per hour, whereas 12% of businesses losing more £600,000 (Neustar, 2015, p. 13). Kaspersky published a survey on DDOS attacks, the findings showed that the average cost of a DDOS attack on a small / medium business is $52,000, whereas, the cost for a large business is on average $444,000 (Kaspersky, 2014, p. 8). Even with the statistics stated above there is an inherent issue, the relatively unknown financial impacts that come with the outage of a system. This paper aims to provide a method for quantifying the financial impacts associated with downtime cause by a distributed denial of service attack system outage.
3.3. Requirement Analysis
##complete this
4. Methodology
As you can see above, distributed denial of service attacks causes many, many impacts, one of which is downtime. My research paper aims to produce a method of quantifying the financial impacts downtime causes to a business, however, there are copious number of variables to consider when calculating the impacts caused to a business. Some of which are extremely hard to quantify, for example, business reputation, which is near impossible to accurately assess the reputational impact. However, below, I have decided on these sections to account for as much of the financial damage as possible.
4.1. Revenue Loss
The business dictionary describes a business’s revenue as “The income generated from sale of goods or services” (Business Dictionary, 2018). Revenue is also one of the main financial impacts that an e-commerce business will face, this is because of most of their products and/or services are sold online. If a system outage occurs therefore no sales can be made, causing significant losses to the company. Therefore, I have decided to include this in the calculation method, which can be calculated for the whole company, and by each department of a business.
4.2. Incident Response Cost
Sans states that an incident response team is a “carefully selected and well-trained group of people whose purpose is to promptly and correctly handle an incident so that it can be quickly contained, investigated, and recovered from” – (SANS Institute, 2001). The majority of larger e-commerce companies are expected to have some form of an incident response team. The team can con consist of specialists who can help mitigate and recover from an attack, along with helpdesk employees, this is due to the surge in calls that will occur while the company’s services are down. However, incident response teams come at a premium charge, whether this is employees already a part of the company, or a third-party service.
4.3. Customer Loss
Customer are at the source of any e-commerce business, without customers the business wouldn’t make any revenue, and be unable to continue as a business. Cyber-attacks can cause many issues that may make a customer decide to take their business elsewhere, for example, having their sensitive data stolen may make customers feel uncomfortable carrying on using their service. However, in this paper, I will use this as a method of calculating the future cost to an e-commerce business of losing customers.
4.4. Operational Cost Loss
In every company there is an operational cost to the day to day running of the business, such as; utilities (Gas, Electricity, etc.), employee pay, etc. this is no different for an online e-commerce business, which will have its own costs, such as; Employees wages, Utilities (Gas, Electricity, etc.), cost of networking equipment, along with other fees. However, this costs a business money every day, if a DDOS attack were to hit and caused a complete outage, then there is an operational cost of the business which will not make any financial return, therefore considered as a loss, for example, cost of wages while employees cannot perform their work.
4.5. Other Forms of Loss
Other than the forms of loss that I have sub-divided above there are some forms which can cause a business financial loss, however these are very hard to quantify with an exact percentage. Such as, customer reputation, this is very hard to exactly quantify, as the only way to exactly measure such an impact, would be to question each customer before an attack and following to see the impact on their view of the company. Business reputation, this again, is very hard to exactly quantify as it can any number of variables that cause a company to have a bad reputation, while there isn’t a way to accurately record reputation of a company. Same as above, Market Share, is also a hard variable to calculate as it can be any number of dislike can cause impact to the overall market share of a business.
9. References
A10 Networks, 2017. A10 NETWORKS SECURITY REPORT SHEDS LIGHT ON COMBATING THE DELUGE OF MULTI-VECTOR DDOS ATTACKS. [Online]
Available at: https://www.a10networks.com/news/security-report-combating-deluge-multi-vector-ddos-attacks?src=home&mdm=banner
[Accessed 12 March 2018].
Abhishta, Joosten, R. & Nieuwenhuis, L., 2017. Analysing The Impact Of A DDoS Attack Announcement On Victim Stock Prices. s.l., IEEE.
Antonakakis, M., April, T., Bailey, M. & Bernhard, M., 2017. Understanding the Mirai Botnet, s.l.: Google Research.
Arbor Networks, 2016. Arbor Networks Releases Global DDoS Attack Data for 1H 2016. [Online]
Available at: https://www.arbornetworks.com/arbor-networks-releases-global-ddos-attack-data-for-1h-2016
[Accessed 12 March 2016].
Arbor Networks, 2017. 2017 DDoS Attack Activity. [Online]
Available at: https://www.arbornetworks.com/blog/insight/2017-ddos-attack-activity/
[Accessed 12 March 2018].
Ballano Barcena, M. & Wueest, C., 2015. Insecurity in the Internet of Things, s.l.: Symantec.
Bene, N., 2016. A Brief History of DDoS Attacks. [Online]
Available at: https://eugene.kaspersky.com/2016/12/06/a-brief-history-of-ddos-attacks/
[Accessed 06 March 2018].
Cashell, B., Jackson, W. D., Jickling, M. & Webel, B., 2004. The Economic Impact of Cyber-Attacks. p. 31.
Chapman, I., Leblanc, S. & Partington, A., 2011. Taxonomy of Cyber Attacks and Simulation of their Effects, San Deigo: Society for Computer Simulation International.
D¨ubendorfer, T., Wagner, A. & Plattner, B., 2004. An Economic Damage Model for Large-Scale Internet Attacks, s.l.: The Computer Society.
Dewdney, A. K., 1989. Computer Recreations: Of Worms, Viruses and Core War. ed. s.l.:Scientific American.
Dooley, M. & Rooney, T., 2017. DNS Security Management. 1st Edition ed. s.l.:IEEE.
Ghandi, R. et al., 2011. Dimensions of Cyber-Attacks: Cultural, Social, Economic, and Political. IEEE TECHNOLOGY AND SOCIETY MAGAZINE, p. 11.
Hachem, N., Ben Mustapha, Y., Gonzales Granadillo, G. & Debar, H., 2011. Botnets: Lifecycle and Taxonomy, Evry: IEEE.
Hengst, K., 2016. DDoS through the Internet of Things. s.l., Twente Student Conference .
Hilton, S., 2016. Dyn Analysis Summary Of Friday October 21 Attack. [Online]
Available at: https://dyn.com/blog/dyn-analysis-summary-of-friday-october-21-attack/
[Accessed 13 March 2018].
Hoque, N., Bhattacharyya, D. K. & Kalita, J. K., 2015. Botnet in DDoS Attacks: Trends and Challenges , s.l.: IEEE COMMUNICATION SURVEYS & TUTORIALS.
Hovav, A. & D’Arcy, J., 2003. The Impact of Denial-of-Service Attack Announcement on the Market Value of Firms. Risk Management and Insurance Review, 6(2), pp. 97-121.
Howard, J. D. & Longstaff, T. A., 1998. A Common Language for Computer, s.l.: Sandia.
IDC, 2017. Internet of Things Spending Forecast to Grow 17.9% in 2016 Led by Manufacturing, Transportation, and Utilities Investments, According to New IDC Spending Guide. [Online]
Available at: https://www.idc.com/getdoc.jsp?containerId=prUS42209117
[Accessed 12 March 2018].
IHS Markit, 2018. IoT Trends Watch 2018, s.l.: IHS.
Incapsula, 2014. Incapsula Survey : What DDoS really cost business, s.l.: Incapsula.
Intel, 2017. A Guide to the Internet of things. [Online]
Available at: https://www.intel.com/content/dam/www/public/us/en/images/iot/guide-to-iot-infographic.png
[Accessed 12 March 2018].
Kamboj, P., Chandra Trivedi, M., Kumar Yadav, V. & Kumar Singh, D. V., 2017. Detection Techniques of DDoS Attacks:A Survey , s.l.: IEEE.
Kang, J., Zhang, Z. & Ju, J.-b., 2004. Protect E-commerce against DDoS Attacks with Improved D-WARD Detection System, s.l.: National Natural Science Foundation.
Kanwal, G. & Chawla, R., 2011. DETECTION OF DDOS ATTACKS USING DATA MINING. International Journal of Computing and Business Research, 2(1), p. 11.
Kaspersky Lab, 2017. The state of industrial cybersecurity 2017, s.l.: Kaspersky Lab.
Kaspersky, 2014. Global IT Security Risks Survey 2014 – Distributed denial of service (DDOS) Attacks, s.l.: Kaspersky.
Ketki, A., Krishan, K. & Monika, S., 2011. Impact Analysis of Recent DDoS Attacks. International Journal on Computer Science and Engineering, Volume 3, p. 8.
Khamruddin, M. & Rupa, D. C., 2012. A Rule Based DDoS Detection and Mitigation Technique , NIRMA: CONFERENCE ON ENGINEERING.
Lei-Jun, L., 2010. An Adaptive Control Mechanism for Mitigating DDoS Attacks, s.l.: IEEE.
Li, C., Jiang, W. & Zou, X., 2009. Botnet: Survey and Case Study. s.l., IEEE Computer Society.
Lucero, S., 2016. IoT platforms: enabling the Internet of things, s.l.: IHS Technology.
Mahadev, Kumar, V. & Kumar, K., 2016. Classification of DDoS Attack Tools and Its Handling Techniques and Strategy at Application Layer, Haridwar: IEEE.
McAfee, 2013. The economic impact of cybercrimeand cyber espionage, s.l.: Center for Strategic and international studies.
Mitrokotsa, A. & Christos, D., 2007. Network Security: Current Status and Future Directions. s.l.: Institute of Electrical and Electronics Engineers.
Nelson, C., 2011. Cyber Warfare: The Newest Battlefield. p. 7.
Neustar, 2015. March 2015 Neustar DDOS attacks & protection report: EMEA, s.l.: Neustar.
Nospec, 2017. The Top Cybersecurity threats of 2017, s.l.: Nospec.
Panetta, L. E., 2011. US Department of Defence News Transcript. [Online]
Available at: http://archive.defense.gov/transcripts/transcript.aspx?transcriptid=5136
[Accessed 05 03 2018].
Paul, 2017. Mirai Attack Was Costly For Dyn, Data Suggests. [Online]
Available at: https://securityledger.com/2017/02/mirai-attack-was-costly-for-dyn-data-suggests/
[Accessed 13 March 2018].
Pescatore, J., 2014. DDoS Attacks Advancing and Enduring: A SANS Survey, s.l.: Sans Institute.
Richards, K. et al., 2017. Cost of Cyber Crime Study, Michigan: Accenture.
Rukavitsyn, A., Borisenko, K. & Shorov, A., 2017. Self-learning Method for DDoS Detection Model in Cloud Computing. s.l., IEEE.
Sachdeva, M. & Saluja Kumar, K., 2014. Recent DDOS Incidents and their impacts, s.l.: Research Gate.
Sachdeva, M., Singh, G., Kumar, K. & Singh, K., 2010. DDoS Incidents and their Impact: A Review , s.l.: IEEE.
Saini, H., Shankar Rao, Y. & Panda, T., 2012. Cyber-Crimes and their Impacts: A Review. International Journal of Engineering Research, 2(2), p. 7.
Specht M., S. & Lee B., R., 2004. Distributed Denial of Service: Taxonomies of Attacks, Tools, and Countermeasures. New Jersey, Research Gate.
Sreekanth, A., Sri, P. & Vartiainen, T., 2016. Dyn DDOS Cyberattack – a case study, s.l.: s.n.
Symantec, 2017. Internet Security Treat Report, s.l.: Symantec.
Vasudevan, R., Morley Mao, Z., Spatscheck, O. & Van der Merwe, J., 2004. MIDAS: An Impact Scale for DDoS attacks, s.l.: IEEE.
Verisign, 2016. VERISIGN DISTRIBUTED denial of service trends report, s.l.: Verisign.
Verisign, 2017. Q1 2017 DDOS TRENDS REPORT: 26 PERCENT INCREASE IN AVERAGE PEAK ATTACK SIZE. [Online]
Available at: https://blog.verisign.com/security/q1-2017-ddos-trends-report-26-percent-increase-in-average-peak-attack-size/
[Accessed 12 March 2018].
WU, Q., Zheng, R., Pu, J. & Sun, S., 2009. An Adaptive Control Mechanism for Mitigating DDoS Attacks, s.l.: IEEE.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




