Types of Denial of Service Attacks
Info: 12610 words (50 pages) Dissertation
Published: 11th Jan 2022
Chapter One - DoS and DDoS attacks
Denial of Service attacks
Availability, confidentiality and integrity are the main aims of computer security [1]. Availability is defined as the capability of using the desired resources or information. Denial of Service attacks threaten the resource’s availability in the network.
Various systems can communicate with an attacker using different methods; this is due to the fact that network protocols and operating systems were established without considering security issues [4]. As a result, hackers are provided with many vulnerable systems on the Internet, where the attacker can misused this vulnerability to build armies of attackers. An attacker can implement a malicious code in a computer system to attack the victim. Creating zombie botnets makes it easy to attack the victim by sending an enormous amount of traffic [4].
DoS attacks can happen when an attacker attempts to make Internet-based applications or a website and other services unreachable to legitimate users. Also DoS attacks can be defined as an attack which aims to prevent the users form using an internet-based service by disturbing the usual functionality of a server that host an application [2]. DoS attacks generally include an attacker sending messages to take advantage of particular vulnerabilities which leads to anomaly or disability in the network systems or sending a large amount of messages quickly to a single node to consume the resources of the system that cause crash in the system [3].
The attacker can use several techniques to do this, often consuming the bandwidth of the network, the RAM memory of the victim or the CPU cycles. Dos attacks can be classified into three classes based on what damage they create [4]:
- Devastating DoS attacks: In this class, the device will not continue to work properly. The attacker can cause power interruption or destruction of the configuration information. This is the easiest way to interrupt the service accessibility but it may have dangerous consequences.
- Resource exhaustion DoS attacks: this causes resource exhaustion because the principle of the attack is resources overuse of the system hardware.
- Bandwidth consuming DoS attacks: bandwidth consuming DoS attacks drain the network bandwidth by sending large amount of requests to the victim, consequently blocking the victim subnetwork with fake traffic [4].
Distributed Denial of Service Attack
If a DoS attack results from many distributed sources, it is called a Distributed Denial of Service attack (DDoS) [3]. In this type of attack, multiple bots called zombies are used to send a large amount of traffic to the victim.
A Distributed Denial of Service attack (DDoS)aims to expand the Denial of Service attack strength by using more than one computer [4]. DDoS attacks are considered to be more efficient than DoS attacks because they raise the attack density through the use of many computers simultaneously. DDoS attacks are a repeated disorder to services in web servers of high profile sites such as insurance companies, banks, credit card payment gateways and others. DDoS occurs when many systems overflow the resources or bandwidth of a victim system, making the attack more effective and difficult to find the creator or origin of the attack [4] [5].
DDoS attacks are able to cause a great damage to network services. Because they can quickly degrade the performance of the network and are hard to detect, DDoS attacks are considered to be one of the most serious security threats to the present Intrusion detection systems. If DDoS attacks can be discovered in adequate time, the damage that the attack causes can be minimized. Until now, efficient and complex solutions to overcome all DDoS attacks’ characteristics have not been found. Thus, detection of DDoS attacks represent an attractive domain for researches [4]. DDoS is typically executed in a logical structure as showed in fig (1).
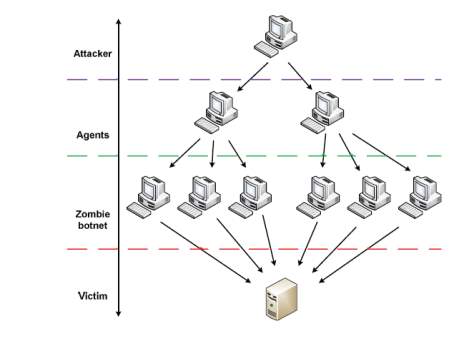
Figure 1 Structure of DDoS Attack [4]
The structure of DDoS includes a client, who represents the attacker and is connected to a number of cooperated systems called handlers. The handlers direct commands to a number of zombie agents that ease the DDoS onto the victim system. Each handler is able to dominate thousands of zombie agents. The attacker often uses an Internet Relay Channel (IRC) to communicate with agents [4] [7].
IRC is an application layer protocol which is used to simplify communication through text. The process works through a client-server network model [6]. A user can install IRC clients on their system, which are computer programs. These clients communicate with chat servers that send or transfer messages to clients. IRC is primarily designed for group communication such as in discussion forums, often called channels, but they also allow one-on-one communication through private messages, including file sharing [6]. Fig (2) shows the IRC network.
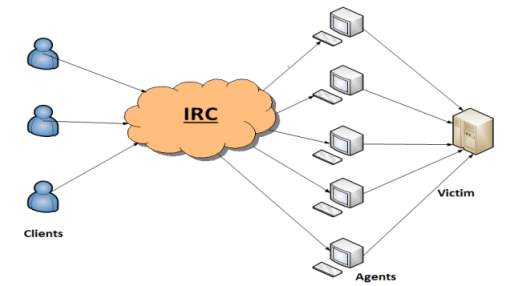
Figure 2 Internet relay chat model [8]
The attacker can use IRC to communicate with agents instead of using a handler program installed on a network server [8][7]. The IRC channel enables the attacker to use legitimate IRC ports to forward commands to agents. Using legitimate ports prevent DDoS command packets to be tracked. In addition, IRC servers have large volumes of traffic, allowing attackers to conceal their presence. The attacker does not need to preserve a listing of agents, as he can directly access the IRC server and check all existing agents. The agent software within the IRC network sends and receives messages via an IRC channel, where the attacker is informed when an agent becomes operational [7].
Reflector Denial of Service (RDoS)
Staying anonymous or hiding the original source of traffic is an important aim for an attacker [4]. Attackers have found a new approach of attack, which is called Reflector Denial of Service (RDoS) shown in Fig (3).
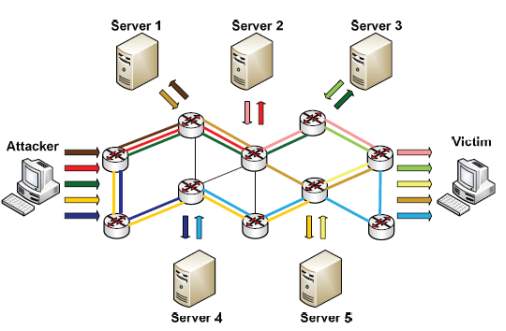
Figure 3 RDoS principle [4]
The purpose of a bandwidth attack is to hide the attack traffic source using Web servers or routers to send malicious traffic to the victim [8] [4]. These third parties are innocent and are called reflectors [9] [4]. A machine can be a potential reflector if it replies to an incoming packet. Conceptually, attackers send packets where the source addresses are made up; the victims address surrounding routers or web servers. Network devices answer incoming packets, where they then appoint them to the relevant address, which is obtained as a source address for the victim. Thus, the victim receives a large volume of traffic and is under DoS attack. Reflective DoS attack is implemented either in a simple way or in a distributed way. The Distributed Reflective Denial of Service attack (DRDoS) contains three levels. The first one is identical to a typical DDoS attack, where the attacker is connected to a number of agents. But, at the second level, there is a slight difference when the attacker agents control zombies. Rather than ordering zombies to direct malicious traffic to the victim straightway, the zombies are instructed to direct traffic forged source third party IP addresses using the victims’ IP addresses. At the third level, the reflectors will send the response traffic to the target victim, which results in to a DRDoS attack. As compared to typical DDoS attack, DRDoS attacks are more scattered with third parties and make it difficult to identify the attack source. Additionally, the attack traffic source IP addresses comes from innocent machines that make tracing back the original attack highly difficult [4].
IP Spoofing
IT world spoofing means deceiving other computer systems or computer clients. This is normally done by concealing one’s identity over the internet. It can be done through an IP address or email, among other methods. We are interested in spoofing through IP addresses [11].
Internet Protocol (IP) is the main protocol to send and receive data over the Internet [7]. The IP packet header includes, among other things, the packet source and destination addresses. Typically, the source address represents the address from which the packet is sent. By tampering with the header of the packet so it includes different addresses, the attacker is able to make it look like the packet is sent from another machine. When the machine receives a spoofed packet, it will reply back to the tampered source address. This technique is used when the attacker is less interested in the response or the attacker can potentially guess the response.
IP spoofing represents the most common type of online disguise [7]. The term IP spoofing aims to conceal the sender identity or to impersonate another machine. In a spoofing attack, the attacker sends packets to a machine showing that the packet comes from a confidential system. In order to be successful, first the attacker has to define the IP address of a confidential system, modifying the headers of the packet so that it seems like packets are coming from a reliable system. In principle, the attacker is tricking the victim computer to believe that it is an authentic machine in the network. This enables the attacker to establish a connection and gain access to the victim, permitting the formation of a backdoor entry to the target machine. Fig (4) illustrates the valid source IP address.
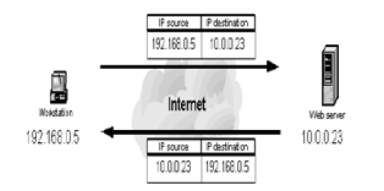
Figure 4 Valid source IP address [7]
The above diagram (Figure xx) explains a typical communication between computers with a legal source IP address, asking for web pages from a web server that is replying to the requests [7]. The request includes the IP address of the workstation (192.168.0.5), which represents the source IP address and the web server IP address (10.0.0.23) of the destination IP address. The web server replies with a web page using a source IP address (192.168.0.5) as the destination IP address and its IP address (10.0.0.23) as the source IP address. Fig (5) illustrates the Spoofed source IP address:
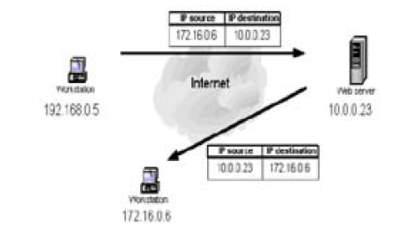
Figure 5 Spoofed source IP address [7]
The above figure illustrates the communication between a computer requesting web pages with spoofed source IP from a web server [7]. The spoofed source IP (172.16.0.6) is used by the workstation; the web server replies to the request and sends data to the actual workstation that have the IP (172.16.0.6). The spoofed IP address system then receives unwelcome connection tries from the web server, where they are merely discarded.
IP Spoofing is Easy because [7]:-
- Authentication only depends on Source addresses.
- Issues with routers. IP routing is hop after hop. Each IP packet is routed individually. All the routers that the packet goes through determine the route for an IP packet.
- Only the Destination addresses are looked by the Routers.
- Changing the source address filed in the header of the packet is easy.
A main technique in all DoS attacks is to conceal the identity of an attacker using IP spoofing by sending packets with a fake source IP address [13]. A particular kind of a value in the field of the source IP address is also a requirement for some DoS attacks. By setting the victim’s address in the source field of the packet, the packet is sent from the victim. An unused IP address within the source forces the victim in contacting a non-existing host.
It is likely to perform DoS attacks without spoofing the IP address if an attacker has cooperated with sufficient hosts or if a series of cooperated hosts is used [13]. An attacker traced through a chain is made difficult or even impossible through selecting compromised hosts from sites with weak security practices or from countries with appropriate regulation. In this type of IP spoofing, it is not essentially required for guarding an attacker.
Conclusion
DoS attacks cause severe damage to services available online. These kind of attacks try to prevent legitimate users from using their rights to online services by bringing down servers. Issues in internet security provide the hackers with ways to attack network systems. An attacker may use single machines to perform DoS attacks or he/she may employs many zombie botnets to increase the attack’s intensity. In this case, DoS attacks are called DDoS attacks. DDoS attacks are considered to be one of the most serious security threats to internet systems. Staying unknown is an important desire for the attacker. The attacker always finds new ways to hide its identity. Therefore, the attacker uses reflectors to make the DDoS attack more complicated. Spoofing techniques are also used to conceal the identity of the attacker and make it difficult for anyone to know his IP address.
Chapter Two - Literature Review
DoS and DDoS Attacks Incidents
DoS attacks represent the main security issues that threatened internet services and result in senior income losses [15]. Despite the fact that Denial of Service attacks existed during the1980s and early 1990s, the attacks were not common security occurrences [6]. But, this changed when the Internet started to become a common medium. The backscatter analysis was used to evaluate the duration and the number of DoS attacks over the Internet [4]. The results showed that more than 5,000 distinct targets were the victims of more than 12,000 attacks during a period of 3 weeks checked in February, 2001.
This section highlights the most common and notable DoS and DDoS attacks Incidents.
1999
In August, 1999 the first notified large scale DDoS attack happened against a university [4]. This attack closed the network of the victim for more than two days.
2000
The websites of CNN, Yahoo, eBay, Datek, Buy, Amazon, ZDNet, Dell and ETrade were the victims of a 15 year old Canadian called (Mafiaboy) in February 2000 [6]. These attacks had a rate of 1GB/s, which damage the victims’ corporate activities and shifted thinking about the seriousness of DoS attacks.
2001
In May, 2001, the Computer Emergency Response Team (CERT) was the victim of a DDoS attack that caused its web site to go offline for more than two days [4].
2002
The UK’s Internet service providers (ISP) were the victims of DDoS attacks in 2002. Some clients suffered from a 12 hours shutdown in one of these attacks [4].
The Domain Name System (DNS) is a constant victim for DoS attacks. All root name servers faced an extraordinary heavy DoS attack in October 2002 [4].
2004
During 2004, the UK online gambling, betting, and bookmaking sites have been experienced DoS attacks by unidentified attackers [4].
2005
In January 2005, Al Jazeera’s Internet based business service went offline by a DoS attack [4]. Al Jazeera offers many Arabic language news services.
2006
The text-to-speech translation application running in the Sun Microsystem’s Grid Computing system was disabled by a DoS attack in March 2006 [73]. This attack was carried out during the opening day of this service.
2007
In April and May 2007, Estonia was attacked by perhaps, at the time, the world’s largest DDoS attack [1]. The bad political relationship between Russian and Estonian leds to a type of cyber war. Estonian websites were under 128 DDoS attacks, 4 of these were TCP SYN floods, 115 were ICMP floods and 9 were generic floods.
2009
In August 2009, many social networking sites such as, Facebook, Live journal Twitter, and Google blogging pages were brought down by Ping flood attacks, seemingly targeted by Georgian blogger (Cyxymu) [3].
2010
In July and August 2010, the server of the Irish government, Central Applications Office, went offline by a denial of service attack producing problems for thousands of students who wanted to use the CAO in order to apply for College and University places [3].
In December 2010, a group called “Anonymous” executed coordinated DDoS attacks on websites such as PostFinance, Mastercard.com, Visa.com and PayPal as part of the campaign “Operation Payback” [3].
2012
The 75th most visited website in the world is Pirate Bay, a Swedish website, which was brought down by DDoS. The site was brought down on November 14, 2012 when a discontent user was not able to admit a private tracker [4].
2014
The Ministry of Justice in UK was disrupted by DDoS attacks [5].
15 million users of the Feedly website were stopped by many DDoS attacks.
A successful DDoS was launched by Anonymous against Boston Children’s Hospital, damaging the operations of the hospital and healthcare.
The DDoS launched against the organizers and sponsors of the 2014 World Cup, disrupting many news, marketing events and broadcasts [5].
Denial of Service Attacks Categories
In order to understand DoS attacks, we need know how researchers classify different types of this attacks.
Based on my study, I would like to classify DoS attacks into two classes:
- Weaknesses-based Attacks: – This kind of attack misuses any flaws or weaknesses in the internet protocols or the internet system in order to perform the denial of service attacks. For example, the misuse of the ICMP, HTTP and TCP protocols.
- Flooding Attacks: – The attacker sends enormous amount of traffic to consume the resources of the victim, thereby the requests from legitimate users are dropped. The term resources refer to memory, CPU cycles, bandwidth, buffers, descriptors, etc.
Several literatures classified DoS attacks, for example, that can be categorized into a Bandwidth Attack or called Volume Based Attack [4]. This attack overloads the network traffic by sending enormous broadcast traffic. The attacker particularly spoofs the source IP addresses in order to make the attack untraceable from the victim’s network. Report [3] describes the Bandwidth denial of service attacks as the increasing of the network traffic to the target victim servers so that the bandwidth becomes overloaded. A network is flooded with requests, whereby it is difficult for legitimate network requests from typical users to reach the website whereby the infrastructure is jammed and cannot serve the requests that come from users.
Loukas in his thesis mentioned that the target of this attack is the bandwidth of the network with either flood attacks, for example ICMP floods or UDP floods [6].
Alvaro Garcia declared that high data volume attacks are able to exhaust all the bandwidth existing between a target and an (Internet Service Provider) ISP [1]. The ISP networks require to have a high bandwidth because they are obliged to route from many resources to many ends. The connections between the victim and the ISP typically have a smaller amount bandwidth than the ones inside the ISP networks. Therefore once high capacities of traffic coming from the ISP going over these connections, the links overfill and valid traffic slows down. The attacker is able to consume bandwidth by sending any traffic to all the network connections. For instance, sending high amount of simple ICMP packets to exhaust the bandwidth.
Haiqin Liu classified DDoS attacks into a bandwidth attacks based on the target of DDoS attacks [14]. He stated that for bandwidth DDoS attacks there are two types: denial of network service attacks and denial of edge service as shown in Fig (a and b). The former type, the attacker typically tries to saturate the entry bandwidth of the victim side. However, he was not clear in defining what exactly denial of network service attacks and denial of edge services are.
a) 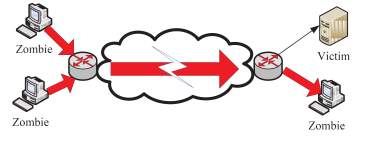
b) 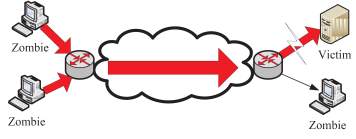
Figure 6 a) Denial of network service [b) Denial of edge service [14]
Another researchers have classified DoS attacks into protocol attacks. For example, Albiz classifies DoS attacks into various groups depending on targeted protocols of the layer in the TCP/IP stack [2]. It divided protocol DoS attacks into DoS at the application layer and the DoS at the network and transport layers. In terms of DoS at the application layer, protocols such as Telnet, HTTP, IMAP, FTP, SSH, IRC, SMTP/POP, XMPP, BOOTP/DHCP, SNMP, DNS, NTP, RTP, TLS/SSL, SIP can become an object to launch a DoS attack. While in DoS at the network and transport layers, protocols like TCP, UDP, and ICMP are used to perform DoS attacks.
Another category of DoS attacks is the Resource attack which is stated by researches [14] and [3]. This type of attack consumes the computing resources which are assigned for an application [14]. For example, a file-processing server or an email server have limitations or constraints in resources where it can handle a certain number of user sessions in a given time. As Muharish [3] stated, the resource attack happened when an attacker attempts to send a huge number of virtual connections to consume memory and CPU resources of the victim server [3]. As the resource of the victim is limited, a huge number of broken connections will make the server unable to reply to legitimate clients.
DoS and DDoS Common Tools
Denial of service tools, at least at the beginning, were proof-of-concept code examples that demonstrated insecurities in common operating systems, including Windows, Linux, Solaris and UNIX [9]. Today, many DoS and DDoS tools are available online such as Low Orbit Ion Canon (LOIC), which is one of the most common DoS attacks tools and it is available freely on the Internet. The famous hackers group (Anonymous) used this tool to attack many networks of big companies [10]; they even requested Internet users to join their DDoS attack using IRC. LOIC is a simple tool for flooding that able to produce huge volume of TCP, HTTP or UDP traffic in order to make a server be under a heavy network load [1]. LOIC was developed by Praetox Technologies and was intended to be used by developers who needed to make their own servers to be under a heavy traffic load for experimental purposes [1] [3] [4] [2]. But, the hackers Anonymous took the open-source tool and used it to execute organized DDoS attacks. Later, LOIC was amended and given its “Hivemind” characteristic to allow any LOIC user to obtain a LOIC’s copy at an IRC server, where control is transferred to a master user who can then send commands using IRC to LOIC clients simultaneously.
A single user can apply this tool to launch a DoS attack against small servers by sending UDP, HTTP or TCP requests to the targeted server. A user needs to obtain the IP address or URL of the server; the LOIC will perform the rest [10].
Once Anonymous throw down LOIC from their choice, High Orbit Ion Cannon (HOIC) soon attracted attention because it was used to attack the United States Department of Justice in reply to its decision to take down Megaupload.com [1]. The tool can be used for a high speed attack and can flood up to 256 websites at one instance [2]. Additionally, HOIC is a simple application for sending GET and HTTP POST requests covered in an easy GUI.
Hping or hping3 is a tool that is able to deal with the size of a random packet and its fragmentations [2]. Hping implements the testing of the firewall rule, the testing of the protocol based-network performance and port scanning [8] [2]. It presents more employment than just transmitting an ICMP echo request, which is the classical use of ping [1]. It can be used to send massive volumes of TCP traffic to a victim and spoofing the source IP addresses to make it look to be random or initiate from a particular user source.
Slowloris is a software that enables a machine to attack the web server of another machine with limited bandwidth and side effects on not related ports and services. This program is written by Robert “RSnake” Hansen [8]. This tool can generate denial-of-service traffic on a target server using a very slow HTTP request. It seends HTTP headers to the victim server in small parts and slowly so as to make the server wait for the next small part until a time out on the request is finished (i.e., the server is enforced to carry on waiting for the headers to reach) [1]. Slowloris also attempts to keep many connections of the web server open and keep them opened as long as possible [8].
Trinity is a DoS tool that can be controlled using IRC or ICQ [7]. This tool is able to generate SYN, UDP, RST, fragment, random, null flood and flag requests that cause exhaustion and link congestion to endpoint resource [2].
Trinoo is an efficient DDoS attacks tool that uses a master node and many broadcast nodes. In this case, a master host commands several broadcast hosts to perform the attack [2]. Mirkovic and Loukas [7] and [6] describe this tool as a tool used to organize distributed UDP flood attacks, where the attacker connects to a Trinoo master (handler) and orders it through a TCP connection to execute a DoS attack at one or more IP addresses of victims. Then, the Trinoo master connects with the Trinoo agents through UDP and instructs them to launch the attack for a particular period of time through sending UDP packets of a specified size to random ports of one or more IP addresses of victims.
Review on Detection and Defence Mechanisms of DoS attacks
DoS attacks try to prevent legitimate users from accessing a system by decreasing availability of the system [1]. They enforce heavy computation functions to the victim by abusing system weakness or flooding it by a massive volume of useless packets. The target server can be enforced to be out of service for a few minutes or even a few days. This leads to severe damage to the services available at the target. Therefore, efficient detection of DoS attacks is important to protect online services [2]. Despite the fact that software patching protects against some attacks, it fails to defend against DoS flooding attacks [1]. A secondary protection, which contains both detection of the attack and defences, is essential. Observing the traffic of the network, including using intelligent routers and firewalls configuration, may help to stop DoS/DDoS attacks to some degree [3].
The development of network-based detection techniques is mostly focused on the detection of DoS attack [2]. Systems for detection applying these mechanisms help monitor transmission over the protected network. Such mechanisms sever the protected online servers from the monitoring attacks, helping to ensure they provide quality service with a minimal response. They are loosely coupled with operating systems that run on host machines that they are protection. Consequently, network-based detection systems’ configurations are less complex than the configurations of host-based detection systems.
In this section, the focus is on DoS attacks detection mechanisms, where the defence is then descrbed.
Koc and Carswelll [6] have implemented experiments using KDD99 dataset, Naïve Bayesian (NB) and its variables; Averaged One-Dependence Estimators (AODE), Weightily AODE (WAODE), Tree-Augmented Naïve Bayesian (TAN),Decision DTNB, Tree (NBTree) and Hidden Naïve Bayesian (HNBNB). The results of their experiments show that Proportion K-Interval discretization techniques, along with HNB, offer high accuracy to detect DDoS attack.
Lohit Barki et al. [4] have proposed an IDS to detect DDoS attack in Software Defined Network (SDN) using machine learning algorithms such as K-Nearest neighbour, Naive Bayes, K-medoids and K-means to categorise incoming traffic into regular and irregular categories. The detection rate and efficiency parameters are used to measure these algorithms. The algorithm has more accuracy in choosing to implement Signature IDS; its results are then processed by Advanced IDS, where the intent is to detect anomalous behaviour using open connections. This helps to provide accurate results of the hosts involved in the DDOS attack.
Katkar and Bhatia [3] have performed an experiment for intrusion detection using REPTree classifier and assess the variation in its performance when it is combined with different feature selection and data pre-processing techniques. Experiment results show that the accuracy of REPTree classifier in detecting intrusion is better when used with Numeric to Binary preprocessing technique on the data set of KDD99.
Zhiyuan Tan et al. [2] have presented detection system to detect DoS attack using multivariate correlation analysis (MCA). This is used for characterization of the network by extracting geometrical correlations between different network traffic features. Such a DoS attack detection system employs anomaly based detection in its attack recognition. The advantage is it makes the solution able to detecting known and unknown DoS attacks through learning legitimate network traffic patterns. Additionally, a triangle-area-based method is suggested to improve and to accelerate MCA processes. The efficiency of this suggested detection system is assessed using the data set of the KDD Cup 99; the effects of both normalized and non-normalized data on the proposed detection system performance are tested.
Detection methods such as Client Puzzle Protocol (CPP) and Ingress filtering are used to detect DoS and DDoS attacks at the Application layer. CPP is an algorithm that is used in internet communication and aims to stop misuse of server resources. CPP requires that all clients that want to connect to the server to resolve a mathematical puzzle before the connection is to be established. After solving the puzzle, the client passes the solution to the server. If the client failed to solve the puzzle, the server refuses the connection. The puzzle is not hard to solve but the attacker attempt to establish a huge number of connections with the victim and this will be difficult because of the time delay.
The Ingress filtering technique is used to ensure that the arrival packets do not have fake source IP addresses in their header. Every packet is sent with the IP source address in the header. If this IP address is fake, this is considered as an attack. In Ingress filtering, packets are examined based on the information from the past so that the server will not be allowed to respond to packets from possible attacking IP addresses.
Xiuzhen Chen et al. [7] proposed a model to assess DoS attacks threats on some attributes of network security such as availability of service in real time, monitoring security threat evolution of a system under organized DoS attacks and improving its assessment accuracy. The technique depends on using a sensor on chosen servers to constantly observe pre-identified parameters of network act. The threat index value (TI) can be obtained using the DS evidence reasoning algorithm in order to merge suitable metrics of network rendering in order to make decisions concerning operational states of observed systems. As soon as the evolution of the security threat is obtained, some proper response policies can be adopted to restrain DDoS from occurring in the networked systems. Tests in a real network situation are designed to try the suggested model of threat evaluation. This method compared with other methods averts the one-sided result acquired from a single sensor. Additionally, it assists administrators to define the security threat state and gives threat evolution of service availability over time. The real network experiment shows that the technique enhances the precision of threat evaluation. Also, it proves the effect of DoS attacks on the security of the network is unlike at the start to the finish of denial of service attacks and provides administrators with a threat evolution picture macroscopically. Additionally, it puts the basis for administrators to take on security reply policies in real environment for robust network.
Regarding the defence mechanisms against DoS attacks, Jarmo Mölsä claimed in his report that there is no single defense against DoS attacks that is enough [13]. Comprehensive set of defenses have to be applied to provide depth. If one layer of fails, other layers have the possibility in detecting and preventing or minimizing an attack. Successful intrusion requires would require all defensive layers to fail.
Subramani Rao [2] has used Access Control Lists (ACL) to Mitigate DoS attack. ACL are rules applied to a machine to control permissions. His project aims to apply ACL on the Cisco routers to block particular set of IP packets. This list offers defense to a network because it controls incoming and outgoing traffic from a single point. He used ACL rules to block traffic from the attacking network. These rules are applied to the command line interface of the router. The results showed that the traffic is completely blocked from the attacking network.
A H M Jakaria [1] and his colleagues have proposed a mechanism called VFence to defend against DDoS attacks that influence the ability of the architecture of Network Function Virtualization (NFV). NFV is virtualizing network functions within virtual machines on servers, allowing flexible and dynamic network function implementation. The mechanism uses network agents to intercept packets where there is a potential attack to verify authenticity and to keep the server safe through the removal of illegitimate packets. Because the intensity of the attack is often changed, the framework of NFV-based defence dynamically organises agents in order to balance the load of the attack. The results of the simulation prove that the technique is able to successfully fail the DDoS attacks by making all the requests from legitimate users served; the increase in the response time of the server is unimportant in comparison to one from a successful DDoS attack.
Weiler [6] has presented a scheme that assistances in depth defense in a network against DDoS attacks. This system lures attackers into the confidence that DDoS attack is successful and convinces the malicious user that the salves are compromised effectively. Actually, the scheme is a sort of a honeypot that lures the attacker to believe that. By this means, the honeypot operator can study the attacker strategies and can perform effective defenses in the rest of his network.
Bellaïche and Grégoire [1] have presented a mechanism to allocate and find an appropriate time-out value for connection-establishment to situations. The experiments have proved the effectiveness of the proposed scheme in controlling backlog queue size by quickly eliminating failed or fake connection tries. The technique is able to decrease the size of the backlog queue to 50% with maintaining normal connections. This mechanism is easy to perform with no change in the TCP protocol.
Luo et al. [4] have constructed a defence technique for DDoS in Software-Defined Networks (SDN) by analysing the specific characteristics of SDN and determining if it is beneficial to countermeasure DDoS attack. SDN is a communication network architecture that decouples network forwarding and control. It has some specific characteristics such as programmability and central control to defend against DDoS attack. They illustrate how this technique could resist DDoS attacks using spoofed UDP flood attacks as an example.
Subramanian and others have proposed a technique using Hop Count Filtering (HCF) system and the Support Vector Machine (SVM) algorithm to filter the majority of the spoofed traffic on the network layer. DDoS attackers using genuine IP addresses are subjected to traffic limits at the initiating application layer. The two-layer defence method defends legitimate packets from being denied, thus mitigating DDoS efficiently. Hop Count Filtering (HCF) system recognises packet with spoofed source IP address. The source IP address and corresponding hops from a server (victim) are recorded in a record table. The incoming packet could then be checked against the table for authenticity. The design of the table of an IP2HC decreases the amount of storage space by IP address clustering.
HCF-SVM runs on the side of the possible victim at the network layer, which has a strong motivation to perform the filtering function. There is no need for collaboration with routers. It uses narrow information such as source IP addresses and (Time-to-Live) TTL values to filter the attack packets, facilitating the need for execution. The scheme of IP2HC tables decrease the storage space amount. Additionally, a rate limiter at the application layer penalises attack flows and offers bandwidth for legitimate users with no denial of services. HCF-SVM scheme proves 98.99% accurate and reduces the false positive (FP) rate.
Conclusion
Many DoS and DDoS attacks incidents have accrued in the past years and are a recurrent problem. The most common DoS and DDoS attacks from 1999 to 2014 have been highlighted. Most companies and organizations do not tell when they are hit by an attack because this damages their reputation.
Many researchers try to classify DoS and DDoS attacks into different categories. Most of them are classified DoS and DDoS attacks into bandwidth DoS attacks and protocol DoS attacks. In bandwidth DoS attacks, the attacker floods the network traffic by sending a huge amount of traffic. DoS attacks take advantage of weaknesses in the internet protocol system to perform the attack.
The attackers can execute DoS and DDoS attacks manually, but there are many free tools available and online that perform different types of DoS attacks. They are very simple to use, where attackers only need to know the IP address or the URL of the target server. Low Orbit Ion Canon (LOIC) and High Orbit Ion Cannon (HOIC) are the most popular DoS attack tools.
Many researchers have proposed different techniques to detect and prevent DoS and DDoS attacks. Most of the DoS attack are detection mechanisms based on the Intrusion Detection System (IDS), machine learning algorithms and data mining techniques. Researchers have tried to develop new techniques to defend against DoS attacks or combine more than one mechanism to make attack execution more sophisticated. However, attackers often find ways to compromise internet systems and launch DoS attacks.
Denial of Service Attack at Different OSI Model Layers
OSI Model in Brief
Open System Interconnection (OSI) is a framework to define the agreements and functions required for communications between network systems [1]. Working on the OSI model started in the late of 1970s by Telephone Consultative Committee or (CCITT) and International Organization for Standardization (ISO) [1]. The OSI model applies a structuring technique that is called layering. This partitions communications into a set of vertical layers, where each layer performs functions that apply and enhance the layer that is immediately at a lower level [1]. Figure 1 shows the OSI Model Layers:
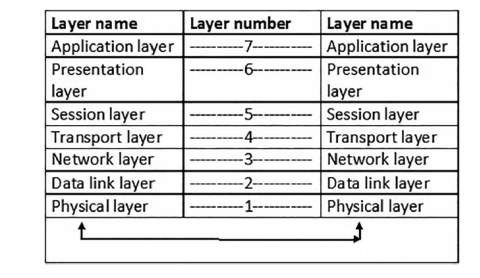
Figure 1 OSI Model Layers [2]
There are seven layers to the OSI model. The first, Layer 7, is the Application layer that permits access to resources on the network. It helps to send and receive data between different applications [2]. Message/data are the main communication unit (PDU) at this layer. Layer 6 is the Presentation layer, which is responsible for data formatting to exchange between communication’s points such as translation, data compression and encryption. Layer 5 is the session layer, where the layer provides termination, governing and establishing sessions through the network. Layer 4 is the Transport layer, which is responsible for providing reliable data delivery from one procedure to another. It guarantees having an orderly sequence, being error free and having no repetition of the transmission of packets. Segments, datagrams or packets are the (PDU) or unit of communication this layer is based on. Layer 3 is the Network layer which is responsible for packets’ movement between source and destination. It offers routing and addressing to the packets. Packet is the PDU at this layer. Layer 2 is the Data link layer, it ensures error free of data transmission over physical media. Frame is the PDU at this layer. Layer 1 is the physical layer, which manages the transmission of binary data (0s and 1s) through the transmission media. It translates bits into signals, where the bit is the PDU at this layer.
Denial of Service Attack at the Application Layer
DoS attacks at the application layer are more complex [3]. They incapacitate particular features or functions as dissenting to the entire network. Application layer protocols have two main categories: user protocols and support protocols. User protocols provide services to users directly, such as through HTTP, SMTP/POP, FTP, IMAP, XMPP, SSH, IRC, etc. Support protocols aim to provide common system functions. Such as DNS, NTP, SNMP, BOOTP/DHCP, TLS/SSL, RTP, SIP, etc [3] [4]. Any of these protocols can be a means or an object to launching a DoS attack. Most protocols at the application layer are structured in a client-server model [4]. A server is a procedure to implement a particular service, such as email or file transfer services. A client is a procedure to request services from a server. Clients can be classified to make them legitimate or not, that is those who do not have malicious logic and malicious clients who do have malicious logic [4].
DoS attacks at the Application layer are more disturbing than other layers attacks because of [3]:
- High obscurity: these attacks use legitimate UDP or TCP connections, making it hard to distinguish them from legitimate users.
- Highly efficient: DoS attacks at the Application layer require fewer numbers of connections.
- Affect multiple applications:they affect different applications because any one of the protocols mentioned above can be used to launch a DoS attack.
- Highly targeted: These attacks aim at a specific application such as web servers running applications in Java, PHP5, and ASP.NE. Targets are crafted using HTTP requests; there could be collisions with the web server´s hashing operation as non-unique and overlapping responses are returned.
- Simplicity in exploitation: they take advantage of the simplicity in Layer 7; for instance, a server may collapse by simultaneously refreshing the browsers by thousands of users.
- Multiple effects: they can directly or indirectly impact many victims. For instance, DNS attacks at one DNS provider can affect all its users.
- Limited resources requirement: they require limited resources. An attacker can achieve a successful attack by a limited investment.
- Normal traffic rules: these attacks follow the rules of normal traffic and complete the process of the TCP handshake so that traffic in those attacks look like legitimate traffic [3].
An attacker may exhaust memory or CPU of a victim by sending a huge number of service requests. Each request can cause the victim to execute memory and/or CPU intensive operations. For instance, an attacker may order malicious agents to send HTTP requests to a server for downloading a large file. As the server must read the huge file from the hard disk into the memory and send it in a large number of packets to the malicious user, a single HTTP request can cause heavy resource depletion at the server in terms of, CPU, I/O, bandwidth and memory [4].
HTTP GET and HTTP POST Attacks
In HTTP or HTTPS, two protocols are usually misused: HTTP GET and HTTP POST [5]. An HTTP GET flood attack can be implemented by the exploitation of a weakness in the HTTP protocol [5]. In this attack, the attacker sends a large number of pernicious attacks using the HTTP protocol. A large number of malicious HTTP GET requests are sent to the victim’s server. Because of the HTTP payloads of these packets is legitimate, the victim server cannot differentiate the malicious HTTP GET requests from normal requests. Therefore, the server have to treat all requests as legitimate requests, where this process then consumes its resources [5].
Another type of DoS attack at the application layer is when the attacker executes a Slowloris attack [5] or what is called a Slow Header Attack [6]. This attack is also dependent on the weakness of the HTTP GET request, but the target server is not overflowed with spoofed requests and it exploits the time delay in HTTP GET headers. The attacker does not send an HTTP GET request one at a time, but the lines of the header are separated and sent. The web server builds the connection with the attacker and waits for the request header to be finish, where this can take a long time. The malicious request for the request is detained for a long time. A default threshold is setup, indicating a maximum timeout for the next header to arrive, where anything over that time will lead to a closed connection. The default threshold of the Apache web server is 300s. This is put as a pause time to send the next line of the header of the attacker’s request. As a result, the attacker can consume the resources of the web server by creating multiple connections with the victim’s server [5] [6].
An attacker also can take advantage of the weakness in the HTTP POST request [5], also called a Slow Message Body attack [6]. A POST request contains a message body, which may use any encoding. The HTTP Header includes a filed Content-Length that informs the web server about the message’s body size. The attacker finishes the HTTP Header portion and sends it to the web server in full. The attacker then sequentially sends the HTTP message body as 1 Byte per 110 seconds. Web servers simply obey the Content-Length that is on the header field while waiting for the remainder of the message. Waiting for the whole message body to be sent allows web servers to backing users with slow or sporadic connections. If there are number of such types of connections, the server will be under DoS attack [5].
Denial of Service Attack at the Presentation Layer
DoS attacks at the presentation layer include deformed Secure Socket Layer (SSL) requests. SSL or TLS offers security for web services such as online shopping, online banking, etc [2] [3]. Because of security advantages, many well-known organizations utilise SSL for securing their services [4]. Currently, most transactions are secured by SSL. However, SSL also has attracted attackers. The TCP protocol and TCP handshake is a frequent victim of DoS attacks. After completing the TCP handshake, the exchange of messages starts to authorize the authenticity of communicating entities. Afterwards, the encryption key for communication is built [3] [2].
Several attacks take advantage of the SSL handshake to consume server resources [3] [2]. The Pushdo botnet performs this by sending incompressible data to the SSL server. The SSL protocol needs sufficient computation time and to produce additional workload on the server to treat the un-useful data as a normal handshake. At this stage, the server may stop processing SSL connections or restart them. Firewalls may fail in such a scenario, as both entities have ended the TCP handshake. Attackers often use SSL to tunnel their HTTP-based DoS attacks, as they appear to be a secure request.
SSL DDoS Attacks can be divided into two classes [3] [2]:
1. Protocol misuse attacks
These attacks exploit the protocol being used. A DoS attack is mounted without completing the secure connection, potentially lacking the need for secure keys. As one example, THC-SSL-DOS, which can be used to ‘renegotiate’ in the connection, can be applied without the benefit of a secure channel. Mitigation techniques, such as IPS signatures, help to detect these attacks [2].
2. SSL Traffic Floods
These attacks send a large amount of traffic over an established secure channel that results in depleting the bandwidth and other resources. Without additional information, mitigation devices are not able to differentiate between normal connections and malicious connections. Such attacks cannot issue a web challenge in attempting to assess source legitimacy. You are prone to false actions because you have either nothing to connect to a rate limit [2].
Denial of Service Attack at the Session Layer
The session layer includes the synchronization and termination of connections over the network [7]. An attacker takes advantage of log-on and log-off protocols to launch DoS attacks in the session layer; for instance, launching a Telnet DoS attack. A Telnet application permits a terminal to communicate remotely with the counterpart. The Telnet uses the network to send and receive data via a port (e.g.23) [2].
The attacker may execute the DoS attack at this level so that defects in Telnet are misused at the switch level, making the services of the switch unobtainable, whereby the administrator will be prevented from controlling the switch [7].
Attacks in Telnet can be classified into three classes [2]:
1) Telnet brute force attack: in this attack, the attacker uses a list of frequently used passwords and a program is designed to attempt to create a Telnet session by using each word in the list;
2) Telnet communication sniffing: the lack of encryption is the most serious problem in a Telnet protocol. The transmissions between parties over the network are sent without any encryption. This vulnerability is exploited by the attacker for frame sniffing. It can be easy for the attacker to sniff the plain text that flows over the network;
Telnet DoS: this attack is a way to damage the communication between two devices over the network by consuming the bandwidth of their connection. To implement this, the attacker sends a large number of irrelevant and useful data frames, thereby stifling the connection. As a result, a legitimate communication cannot use this connection. This attack is also used to stop administrators from using Telnet in their devices [2].
Denial of Service Attack at Transport Layer
Layer 4 DoS attacks are based on transmission and generation of an enormous volume of traffic to deactivate or totally block the availability of services or resources in the network for legal clients [2]. These attacks usually include misuse of TCP and UDP protocols for flooding resources in the network.
DoS attacks at Transport layer classified into flooding attacks and de-synchronization attack [15]:
Flooding
If an attacker is iterating to make a new connection with the same server, which wants to retain status at each end of connection, the resources that are needed for each one of these connections will be consumed [15]. As a result, any further connections from any other users cannot be served, where they may even be dropped.
De-synchronization
De-synchronization attack is the disturbance of a current connection [15]. For example, the attacker can spoof messages continually to a node and this causes the node to retransmit the lost frames. End hosts may not be able to exchange data effectively, if the attack is done in a timely manner, where the resources are then wasted in the connection.
TCP/IP Protocol
In order to understand DoS attacks at the transport layer, brief explanation of the TCP/IP protocol is needed. The USA military Defence Department was the first to implement the TCP/IP protocol suite [17]. The Internet, at that time, was very limited and the TCP/IP protocol was capable of providing the required security. But, by time the Internet started to mature, the TCP/IP protocol had not improved. Today, the TCP/IP suite is neither considered secure nor resistant to attacks.
An Internet protocol (IP) is defined as a service with packet delivery [18]:
- Delivery without assurances of acknowledgments,
- IP Protocol is connection less i.e. each packet is handled individually from all other packets.
- The Internet makes a reasonable effort to deliver packets to the best of its abilities. Figure 2 represents the IP header:
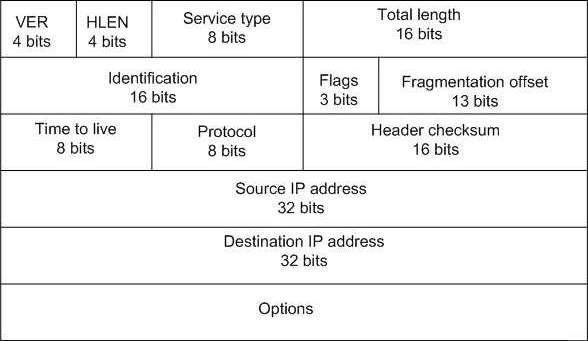
Figure 2 IP header [18]
Transmission Control Protocol (TCP) is a process to process protocol [18]. TCP protocol uses port numbers to provide program to program communication. TCP is a connection oriented; in order for program A to communicate with program B, there must be a connection has been set up between A and B. This connection allows the sending and receiving processes to deliver and receive data as a stream of bytes. TCP is part of the transport layer above the network-layer; variable length data streams can be sent and received. Figure 3 shows the TCP header:
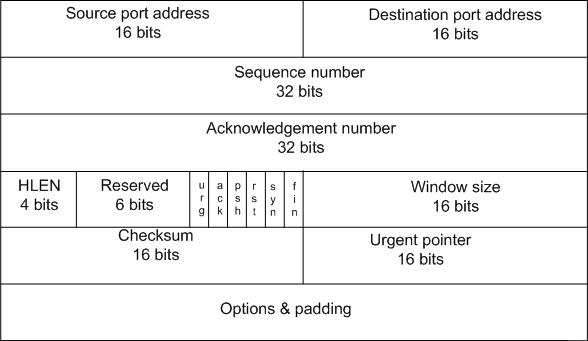
Figure 3 TCP Header [18]
TCP SYN Flood Attack
TCP is a connection oriented, stream protocol which offers full duplex service where the data can flow over the internet in both directions [19]. To establish the connection, TCP uses the three way handshake process. In Figure 4, the illustration shows a three way handshake process between a TCP client and a TCP server:
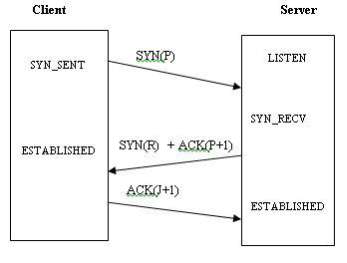
Figure 4 TCP Three Way Handshake [19]
- First, the client sends a packet marked with SYN to the server.
- After the SYN packet is received from the client, the server sends a SYN+ACK packet to the client.
- The client reply with an ACK packet and the connection is established with the server. Now, the client is able to send the data messages [19].
A TCP SYN flood attack represents easiest and most dangerous ways to launch a DDoS attacks [20]. This attack uses the weaknesses in the TCP protocol, but it was not considered a weaknesses when the protocol was developed. In 1994, Steve Bellovin and Bill Cheswick discovered the weakness in the TCP protocol (TCP SYN flood attack).
In such TCP SYN attacks, a synchronize flag in TCP headers is utilised in messages sent [21]. This flag is set when the system sends a packet in a TCP connection; there is an indication that the receipt system has to store the sequence number contained within this packet.
TCP SYN flood attack characteristics are [20]:
- The attacker attempts to generate a huge number of server connections.
- SYN sets up a RECEIVED state; the victim then receives a request to form a connection that allocates memory to it.
- After the server receives a request for connection, which is a packet with SYN flag, the server leaves this half-open connection in the backlog queue and a reply packet to the client with SYN and ACK flags.
- When the server does not receive any reply from the client, it sends the SYN ACK packet again until a timeout finishes; it removes this half opened connection from the backlog queue.
- The whole procedure of SYN requests may take about three minutes for operating systems.
- TCP SYN flood attack generates a large number of half-open connections that the server cannot handle; new requests cannot be received.
- Connections remain at a SYN RECEIVED status until the backlog queue becomes full.
- The operating system is able to serve only some of the half opened connections, depending on the size of the backlog. As an example, 2048 bytes is the default size of the backlog queue of the Debian Squeeze. If it reaches this size, the server cannot receive any connection requests [20]. Figure 5 shows TCP SYN Flood DoS attack network:
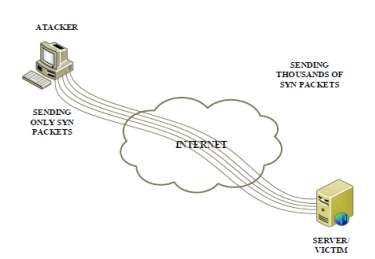
Figure 5 TCP SYN Flood DoS attack [20]
The attacker may either not send the ACK reply or he can spoof the source IP address in the SYN packet that results in the server replying to a forged SYN-ACK packet. Also, this false IP address will not send back an ACK reply because it does not send a SYN [14]. Figure 6 shows Three Way Handshake of TCP SYN Attack:
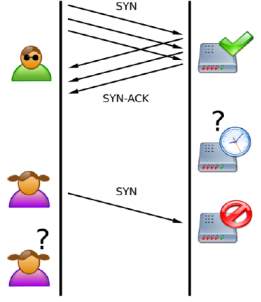
Figure 6 Three Way Handshake of TCP SYN Attack [14]
If the malicious client quickly sends SYN packets without spoofing the IP source address, this attack is called a direct attack [21]. This attack can be implemented by simply sending many TCP connection requests. The attacker’s operating system may not reply to the SYN-ACKs, where RSTs, ACKs, or ICMP messages may move the TCB (Transmission Control Block) from the SYN-RECEIVED state. The attacker can avoid responding to the SYN-ACK packets by setting some of the firewall configurations by which the firewall can filter leaving packets to the listener (i.e., permitting only SYN packets out); the firewall can filter arriving packets so that the SYN-ACK packets are dropped before approaching the processing code of the local TCP [21]. Figure 7 represents the network for the Direct TCP SYN Flood Attack:
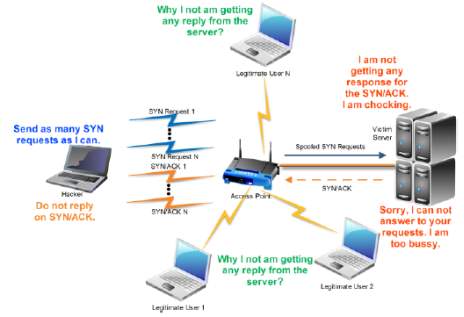
Figure 7 TCP SYN Flood Attack: Direct Attack [21]
That attacker can also use spoofing of the source IP address to perform the TCP SYN attack; this is more complicated than the technique used in a direct attack [21]. In this kind of TCP SYN flood attack, the attacker changes firewall rules and generates and send IP packets that have valid IP and TCP headers. Furthermore, the techniques of IP address spoofing can be classified into different categories, depending on what spoofed IP source address is used in the attacking packet [21]. Figure 8 illustrates the Spoofing TCP SYN Flood Attack:
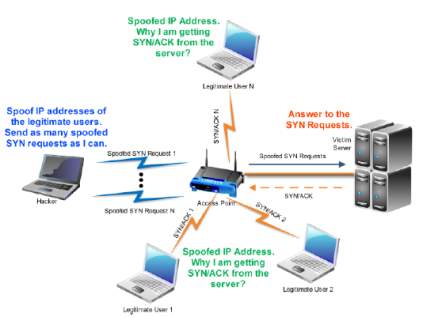
Figure 8 TCP SYN Flood Attack: Spoofing Attack [21]
TCP SYN flood attack attempts to fill the Backlog queue of the victim server [22]. Any request that enters the node containing SYN sign for communications is kept orderly in a part of the memory. These requests are considered and answered to establish the connections for communication. This fragment of memory is known as the Backlog Queue. If this part becomes full with a large number of requests, the server is enforced to discard new requests and not to be processed [22].
The DDoS TCP SYN flood attack is very dangerous to the victim server because it raises the amount of the traffic that is sent to the victim [20]. Chasing the distributed attack is considered to be a very difficult task, which is the major reason that makes the defence against a TCP SYN DDoS attack very hard. In Figure 9 shows the Distributed TCP SYN flood Attack:
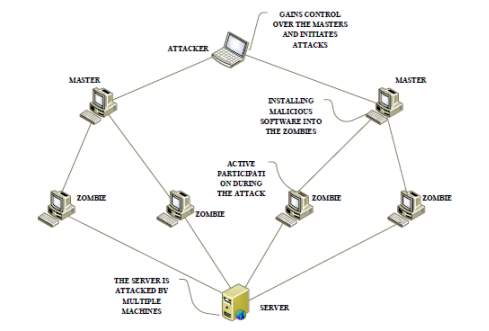
Figure 9 Distributed TCP SYN flood Attack [20]
UDP Flooding Attack
User Datagram Protocol (UDP) is a protocol in the transport layer and the application layer uses this protocol widely, including DNS servers [8]. UDP is not like TCP; this protocol is connectionless and there is no guarantee that data reach their destination. Figure 10 represents the UDP header:
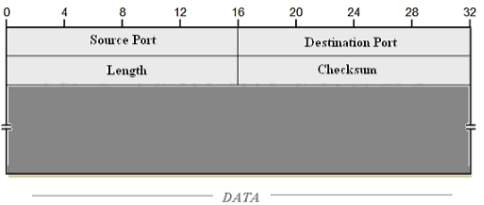
Figure 10 UDP Header [8]
In UDP flood DoS attacks, the attacker uses the UDP to performthis type of attack [14]. Using the UDP protocol to launch DoS attacks is not as simple as using the TCP protocol. But, the UDP flood attack is executed by sending many UDP packets to random ports of the target victim [7] [14]. As a result, the victim server will:
- Examine the application which listen at the port.
- If there is no application listening at that port, the server responds with an ICMP packet Destination Unreachable message [14].
By sending a large amount of UDP traffic, the victim server will be enforced to send a large number of ICMP packets and this makes the server unreachable by other users. Additionally, the attacker can spoof the source IP address of the malicious UDP packets to ensure that the returned ICMP packets cannot reach the attacker’s node and no one is able to know the network location [14]. Figure 11 shows the UDP Flood Attack:
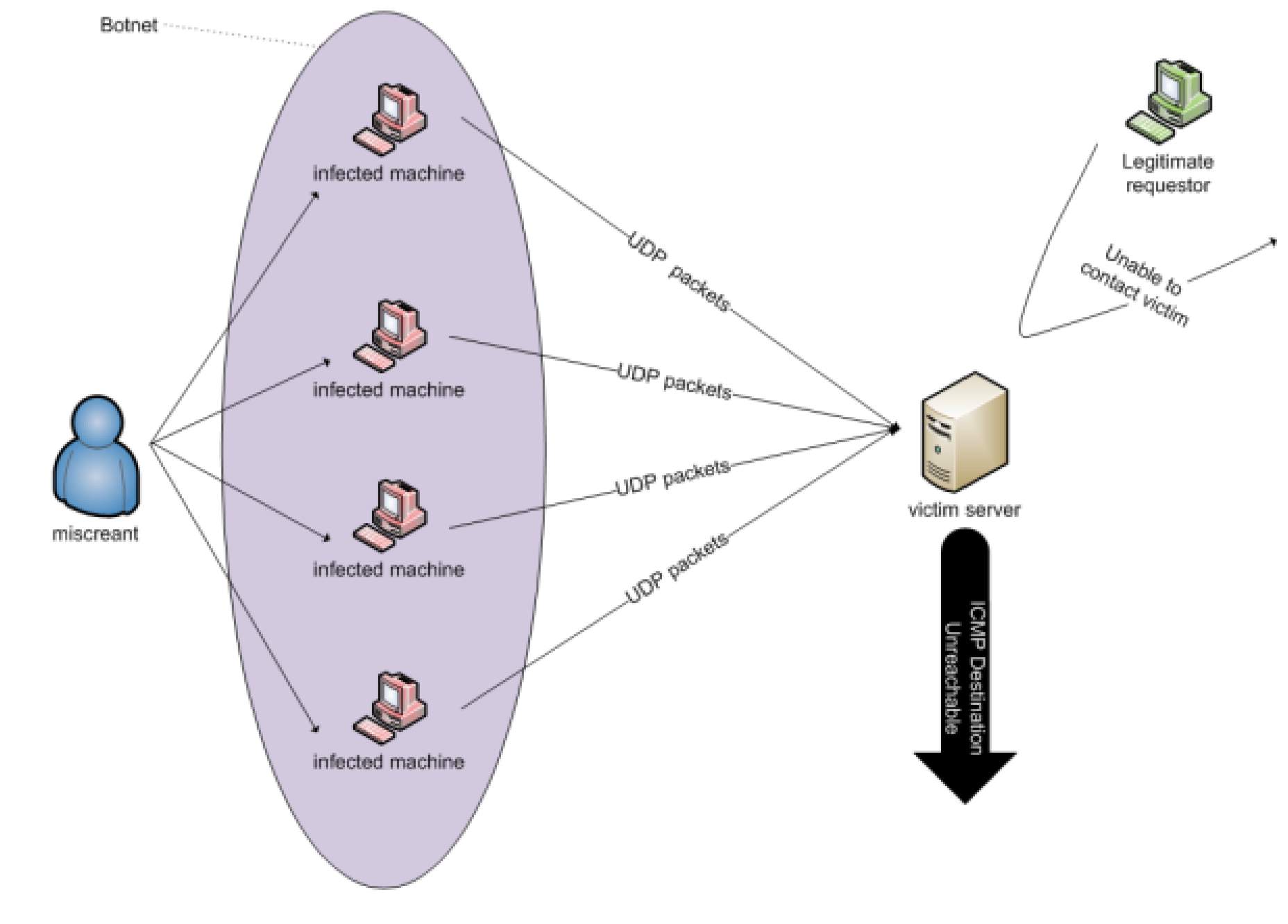
Figure 11 UDP Flood Attack [7]
Denial of Service Attack at the Network Layer
Layer 3 of the OSI model is responsible for data packets’ routing and switching to various networks and LANs. It depends on IP, ARP, RIP and ICMP protocols, relying on routers [7]. DoS attacks at the Network layer include injecting the victim’s network with a large amount of traffic that it cannot handle. As a result, the victim network begins to respond slowly or it neglects some packets. The loss of some packets can cause an overflow of retransmitted packets and causes extra traffic. Increasing the network traffic overfeeds the network and it becomes inaccessible for the legitimate users [2].
ICMP Protocol
ICMP is one of the important protocols that is used for diagnosing the connections between devices/applications or when the sent data cannot reach its destination [8]. It is mainly used to send error messages by operating systems of the network computers; for instance, if a requested service is unavailable or a host cannot be reached [9].Figure 12 illustrates the ICMP components:
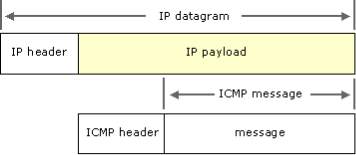
Figure 12 ICMP components [9]
ICMP ECHO:ICMP packets are sent if the IP datagram produces errors, sends diagnostic requests, or for routing purposes. Echo requests are ICMP messages where the reply is an echo (ping) containing the same data as that was received as shown in Figure 13 [9].
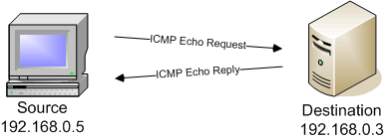
Figure 13 Echo Request [9]
BROADCAST: is a simple message sent to all devices over a LAN [9]. For an IP network that has no subnets, the host bits’ broadcast address range is set to 1’s as shown in Figure 14.
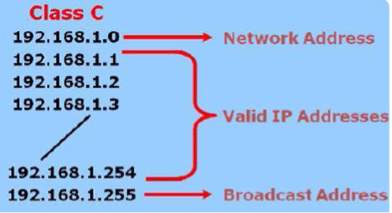
Figure 14 Broadcast address for Class C [9]
Smurf Attack
Smurf Attack is an old DoS attack where the attacker sends an echo packet to a routing machine in the network and the source of the data is concealed. By using a broadcast address, the request is sent to all machines over the network. All machines that receive the echo packet send a reply to the sender, which is the victim [7]. Smurfing considers internet control message protocols (ICMP) and internet protocols. A network administrator uses an ICMP protocol for data exchange, the network status, and pinging devices to define their operational state. The machines that are operative send back an echo packet as a response to ping requests. The Smurf program generates a network packet that seems to have originated from another address; this is called IP spoofing. The packet includes an ICMP ping message, which is sent to all IP addresses in the network by using an IP broadcast. Thus, the echo responses are sent to the IP address of the victim. A large number of ping requests and echo replies make the network unavailable for real traffic [9]. Figure 15 shows the Smurf Attack
Smurf attack Steps:
- The attacker determines IP address of the victim.
- The attacker identifies intermediate site to help in increasing attack.
- The attacker sends huge amount of traffic to the broadcast address at a specific intermediate sites.
- Intermediate sites offer broadcast to all hosts in a subnet.
- Hosts reply to the victim’s address.
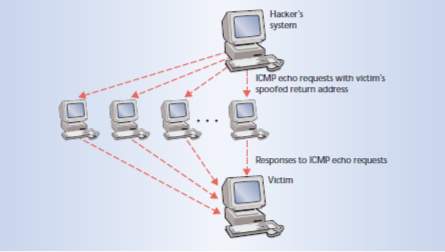
Figure 15 Smurf Attack [10]
ICMP Flood Attack
In ICMP Flood, also called a Ping flood, where the attacker sends an enormous number of ICMP Echo packets to the victim server in order to exhaust all existing bandwidth and prevent legitimate users [11] [12].
The ping command is one example of this attack [11]. The ping command is mainly used for testing the connectivity of the network by examining whether a particular device can send and receive messages over the network.
This attack is more efficient by using the flood of ping options (i.e. sending ICMP packets at a very fast rate) without waiting for replies from the victim server. Most of ping executions need that the attacker has bandwidth more than the victim [31]. Figure 16 ICMP Flood Attack represents the ICMP Flood Attack:
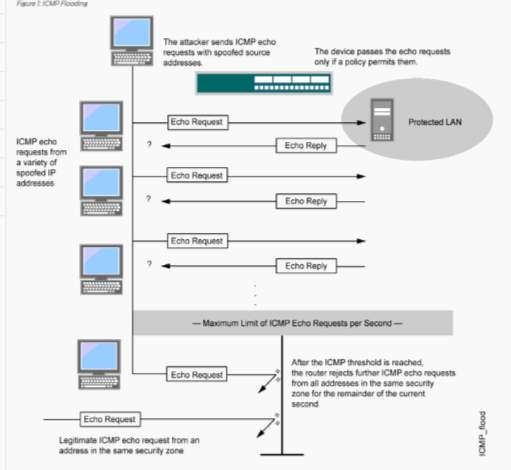
Figure 16 ICMP Flood Attack [11]
Ping of Death
This type of denial of service (DoS) attack occurs when an attacker intentionally sends IP packet sizes more than the 65,536 bytes, which is more than what is allowed by the IP protocol [14]. Fragmentation is a feature in TCP/IP; it break down a single IP packet into smaller fragments. In 1996, attackers started to exploit that feature because they found that breaking down a packet into segments allows up to larger than 65,536 bytes to be used in attacks. Most operating systems do not function properly in these cases, leading to having to crash or necessitating a reboot.
Denial of Service Attack at the Data Link Layer
Layer 2 ensures that the data is effectively handed over to the physical layer [7]. The media access control (MAC) or link layer offers channel settlement neighbour to neighbour transmission. Cooperative systems, which depend on carrier sense and allows nodes to sense other nodes are communicating, are particullarly susceptible to DoS attacks.
Attacks such us Collision, Unfairness and Exhaustion are based on attacking data frame detection, medium access control, multiplexing of data-streams and error control [15].
Collision Attack
A collision in one octet may only be needed for a transmission to cause disruption [16]. Any change in the data part may cause a mismatch in the checksum at the receiver end. In some MAC protocols, a distorted ACK control message can produce expensive exponential back-off. At any layer, error-correcting codes offer a good method for bearing changing levels of distortion in messages. These codes can function best as counters to probabilistic or environmental errors. In one encoding, attackers may distort more data than the system can correct at a large cost to the system. Codes for correcting errors themselves can cause further communication and processing overhead. A network may employ collision detection to detect the attacking collisions, but it generates a link layer jamming process and no efficient defence is known. Appropriate communication still need cooperation between machines, which are predictable to prevent distortion of others’ packets. Access may be denied through the subservient node, where less energy is expended in fulltime jamming [16].
Exhaustion Attack
Simple implementation of link layer may attempt retransmission frequently, while even having been triggered by a late collision, including such a collision near the end of the frame [16]. An Exhaustion attack is an active DoS attack that can exhaust battery resources in neighbouring nodes. The attack compromises availability at little expense to the attacker. Random back-offs reduce the likelihood of inadvertent collision; therefore, they could be unsuccessful in stopping such an attack. Time division multiplexing offers each node a slot to broadcast without needing adjudication for each frame. This technique could resolve the unlimited delay problem in a back-off algorithm; however, it is still vulnerable to collisions. A self-sacrificing node can take advantage of the cooperating nature of most protocols at the MAC layer in an interrogation attack.
For instance, Request to Send, Data/Ack and Clear to Send messages are used by IEEE 802.11 MAC protocols to detain channel access and data transmission. A node could frequently request to access the channel by sending RTS, obtaining a CTS reply from the targeted neighbour. Continuous transmission could consume the energy resources of both nodes. A solution is making the MAC admission monitoring rate limited, thus the network can disregard unnecessary requests without sending costly radio transmissions. This limit cannot be less than the predictable maximum data rate that the network can support. One strategy to protect against battery exhaustion attack is limiting the inessential replies that the protocol requires. Engineers often code this ability into the system for generic effectiveness; coding to deal with possible attacks may need, however, extra logic [16].
Unfairness Attack
Misusing a cooperating MAC layer priority system or sporadic application of those attacks can result in an Unfairness Attack, which is a weak format type of DoS attack [16]. This menace may not completely block legal access to the channel, but this can reduce service by making users miss their deadlines in a real time MAC protocol. One mechanism to defend against this threat is using small frames so that a node may access the channel only for a short time. However, this approach can increase framing overhead if the network sends long messages. In addition, an attacker can fail this defence by deception, where competing for access, such as by replying fast, whilst others delay randomly [16].
References
[1] S. D. V. D. Sumit Kumar, “THE OSI MODEL: OVERVIEW ON THE SEVEN LAYERS OF COMPUTER NETWORKS,” International Journal of Computer Science and Information Technology Research, 2014.
[2] G. Kumar, “Denial of service attacks – an updated perspective,” Systems Science & Control Engineering, 2016.
[3] G. Kumar, “Understanding Denial of Service (Dos) Attacks Using OSI Reference Model,” International Journal of Education and Science Research, pp. 13-14, 2014.
[4] M. ABLIZ, “Internet Denial of Service Attacks and Defense Mechanisms,” 2011. [Online]. Available: https://people.cs.pitt.edu/~mehmud/docs/abliz11-TR-11-178.pdf.
[5] V. Durcekova, L. Schwartz and N. Shahmehri, “Sophisticated Denial of Service Attacks Aimed at Application Layer,” IEEE, 2012.
[6] N. H. Y. S. Nikhil Tripathi, “How Secure are Web Servers? An Empirical Study of Slow HTTP DoS Attacks and Detection,” in International Conference on Availability, Reliability and Security, 2016.
[7] E. Y. M. Muharish, “PACKET FILTER APPROACH TO DETECT DENIAL OF SERVICE ATTACKS,” California State University, San Bernardino, 2016.
[8] A. Saied, “Distributed Denial of Service (DDoS) Attack Detection and Mitigation,” King’s College London, 2016.
[9] R. Sandeep, “A Study of DOS & DDOS – Smurf Attack and Preventive Measures Preventive Measures,” International Journal of Computer Science and Information Technology Research, vol. 2, no. 4, pp. 312-317, 2014.
[10] L. Garber, “Denial-of-Service Attacks Rip the Internet,” IEEE, vol. 33, no. 4, pp. 12-17, 2000.
[11] A. J. P. S. V. G. Neha Gupta, “DDoS Attack Algorithm using ICMP Flood,” IEEE, 2016.
[12] R. M. J. B. Boris Sieklik, “Evaluation of TFTP DDoS amplification attack,” ELSEVIER, 2015.
[13] “Wikipedia,” [Online]. Available: https://en.wikipedia.org/wiki/Ping_flood.
[14] K. Shaker, “Analyzing DoS and DDos Attacks to Identify Effective Mitigation Techniques,” Department of Computer Science, American International University, Bangladesh, 2014.
[15] Y. Xia, “SELECTIVE DROPPING OF RATE LIMITING AGAINST DENIAL OF SERVICE ATTACKS,” UNIVERSITY OF DAYTON, Dayton, Ohio, 2016.
[16] J. A. Anthony D.Wood, “Denial of Service in Sensor Networks,” IEEE, 2002.
[17] M. Shah, V. Soni, H. Shah and M. Desai, “TCP/IP Network Protocols-Security Threats, Flaws and Defence Methods,” IEEE, 2016.
[18] C. N. Maregeli, “A Study On TCP{SYN Attacks And Their Effects on A Network Infarstructure,” Faculty of Electrical Engineering, Mathematics and Computer Science Network Architectures and Services, Delft, The Netherlands, 2010.
[19] N. G. a. S. K. C. Deepak Singh Rana, “A Study and Detection of TCP SYN Flood Attacks with IP spoofing and its Mitigations,” Int.J.Computer Technology & Applications, 2012.
[20] A. T. D. B. a. M. B. Mitko Bogdanoski, “A novel approach for mitigating the effects of the TCP SYN flood DDoS,” World Journal of Modelling and Simulation, 2016.
[21] T. S. a. A. R. Mitko Bogdanoski, “Analysis of the SYN flood DoS Attack,” I. J. Computer Network and Information Security, 2013.
[22] D. E. B. N. Nozar kiani, “Detection and prevention from denial of service attacks (DoS) and distributed denial of service attacks (DDoS),” Advances in Information Science and Applications, 2014.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




