Cryptographic Procedures to Guarantee Data Security
Info: 10087 words (40 pages) Dissertation
Published: 9th Dec 2019
CHAPTER-1
- Introduction
With the developing prevalence of system and the improvement data handling, a high rate of computerized picture data transmission in the system are identified with individual security and private privileged insights. It is without a doubt vital to guarantee data security. Information encryption is a vital measure to guarantee information security in a system domain; be that as it may, at this stage, the greater part of the encryption and validation secret word framework structures are instant messages, in light of the fact that advanced pictures include substantial measure of information and high excess; current scrambling strategies have pretty many deficiencies. In this way, to guarantee secure transmission of pictures in the system, the new investigation of advanced picture encryption strategy has turned into a critical need. Through PC systems, it is exceptionally advantageous for individuals to work and to have admittance to study assets; asset sharing has turned out to be much less demanding. Be that as it may, individuals need to confront different security issues meanwhile. As per insights around the world, a hacking occurrence happens about like clockwork. An assortment of security episodes result in the loss of over $17 billion in the U.S consistently. Information hacking episode has expanded 250% in the previous 5 years, about 99% of huge organizations endure an assortment of hacking occurrences, and even RSA securities sites were assaulted. The multifaceted nature and the adaptability of system environment decide the presence of system security dangers. Computerized pictures in system transmission are inclined to an assortment of man-made assaults, including data robbery, information altering, information erasure, and infection assaults, which cause enormous misfortunes to the data owners. Thus, how to guarantee data security of the picture has turned into a hot issue. Cryptographic procedures can be utilized principally to ensure data security [1]. A sound secret word framework can ensure the classification of data, as well as is valuable to guarantee the honesty and genuineness of data.
Cryptographic procedures can be utilized basically to ensure data security. A sound secret key framework can ensure the classification of data, as well as is valuable to guarantee the respectability and credibility of data. The turbulent encryption innovation is a developing encryption innovation that utilizations disorderly signs produced by riotous framework for encryption, which has fine components of the watchword, for example, being a class of irregular tumult, and amazingly delicate to introductory conditions. Consequently, the utilization of turbulent signs can construct a decent encryption framework. Plus, the tumultuous encryption framework can be basically actualized and run quick; it is reasonable for picture encryption with substantial measure of information.
To guarantee the security of advanced picture data, there are two compelling defensive measures. The first is advanced watermarking innovation, which inserts a watermark in a whole picture to adequately ensure computerized copyright. However, this technique is not ready to change the presence of a picture, which is not appropriate for the secret needs of picture. The other strategy is picture encryption. Through scrambling operations of this technique, the first picture is changed to data like channel arbitrary clamor, and such irregular commotion is not conspicuous to individuals Immense development of web and its supporting innovation gives speedier and straightforward entry to different data. Fast development of innovation encourages transmission of various sorts of messages. Expansive utilize and development of web results in broad utilization of pictures. Secure capacity and transmission of computerized pictures over the system has its significance in the correspondence framework. Cryptography assumes essential part in creating secure pictures. Calculations that are utilized to scramble content should be improved in light of the fact that size of the picture will be high when contrasted with content and pictures contain associated pixels. Among the calculations that are utilized for picture encryption AES Advanced Encryption Standard (AES) is a particular for the encryption of electronic information. It has been received by the U.S. government and is currently utilized around the world. AES is a symmetric-key calculation, which means a similar key is utilized for both encoding and unscrambling the information [2]. AES is the best known and most broadly utilized square figure. Its three variants (AES-128, AES-192, and AES-256) contrast in their key sizes (128 bits, 192 bits and 256 bits) and in their number of rounds (10, 12, and 14, separately). On account of AES-128, there is no known assault which is speedier than the 2128 unpredictability of comprehensive hunt. Be that as it may, AES-192 and AES-256 were as of late appeared to be fragile by assaults which require 2176 and 2119 time, individually [3]. While these complexities are much quicker than comprehensive inquiry, they are totally non-useful, and don’t appear to represent any genuine risk to the security of AES-based frameworks.
1.2 Background
Image Encryption is a wide zone of research. Encryption essentially manages changing over information or data from its unique shape to some other frame that conceals the data in it. The first information is normally alluded as plain information and the changed over frame is called figure information. Encryption can be characterized as the craft of changing over information into coded shape which can be disentangle by proposed collector just who postures learning about the unscrambling of the figured information. Encryption can be connected to content, picture and video for information insurance. The assurance of picture information from unapproved get to is imperative. Encryption is utilized to build the information security. The Encrypted Image is secure from any sort cryptanalysis.
Computerized pictures are appealing information sorts with across the board scope of utilization and numerous clients are intriguing to execute content assurance strategies on them to keep from see, copyright or control. In numerous applications like military picture databases, secret video conferencing, therapeutic imaging framework, digital TV, online individual photo collection, security in fundamental. Additionally wide use of pictures in mechanical process transforms it into an asset and resource, so it is vital to shield the secret picture information from unapproved get to.
AES calculation is not just for the content information, it can connect for the pictures, more often than not picture handling manages a picture, which is made out of many picture focuses. The picture focuses, to be specific pixels, spatial co-ordinates that demonstrate the position of the focuses in the picture and power values. The uses of the picture preparing have been regularly found in the Military correspondence, Forensics, Robotics, Intelligent frameworks and so on. In this paper, we actualize the AES calculation which is a productive plan for both equipment and programming usage.
For picture encryption, individuals used to scramble picture by customary encryption calculations. In light of the mystery keys utilized as a part of the procedures of encryption and decoding, conventional encryption strategy can be separated into lopsided key cryptography (otherwise called secret key and public key) and symmetric-key cryptography . Symmetric-key cryptography calculation utilizes a similar key for encryption and decoding , and just imparting parties know the mystery key, which can encode or unscramble message, for example, DES (Data Encryption Standard), and IDEA (International Data Encryption Algorithm) In a deviated key encryption, the encryption and the decoding keys are distinctive. Encryption key is known to everybody and just the expected beneficiary has the way to unscramble the message. The run of the mill calculations, for example, RSA (Rivest, Shamir and Adleman) and ElGamal are regular specimens of this sort. In principle, the picture can be encoded through conventional encryption strategies, however most customary encryption advances depend on content plan without considering the innate qualities of pictures, along these lines, utilizing the above approach is wasteful as well as less secure [4]. To take care of these issues, numerous researchers swing to image encryption calculations.
1.3 Image Encryption
1.3.1 Need of Image Encryption
Numerous computerized administrations like vision and sound frameworks, restorative and military imaging frameworks, web correspondence require dependable security away and transmission of advanced pictures. Because of development of web, phones, mixed media innovation in our general public advanced picture security is the most basic issue. In these innovation advanced pictures assumes more critical part than the conventional writings. It requests genuine security of clients’ protection for all applications. Along these lines picture encryption systems are generally used to dodge interruption assault. Due to the advancement of technology in our society digital images and videos are playing a major role than just plain and simple text, thus demanding a serious protection of user privacy. In order to make everything secure, the encryption of audio and video is very important as it helps to minimize malicious attacks from unauthorized parties. The recent advancement in science and technology, mainly in the computer and communication industry, allows potentially a huge market for distributing digital multimedia content through the internet [5]. However, the rapid increase of digital document, multimedia processing tools and the availability of internet access throughout the world has given birth to a perfect environment for copyright fraud and uncontrollable distribution of multimedia content. One of the major challenges currently is the protection of intellectual content in multimedia networks.
In order to deal with the technical challenges, there are two major security technologies being developed:
1. Multimedia encryption technology providing end-to-end security while the digital content is being distributed over a huge number of distribution systems.
2. Watermarking technology is being used to prevent copyright fraud, ownership trace, and authentication.
Confidentiality means protecting of personal information from unauthorized access. An unwanted party known as adversary should not be able to access the material. Data integrity makes sure that the information has not been tampered in any kind of unwanted way. Therefore, the authentication methods are being studied in two groups:
- Entity Authentication
Entity authentication makes sure that the receiver of the message receives both the identity of the sender and his active participation during the transmission time.
- Message Authentication
Message authentication provides verification of the identity of the message sender. It also holds all evidence of data integrity if it is modified during the transmission period, then the sender is not the originator of the message.
Relationship among pixels and high excess, these attributes changes as per kind of sight and sound information. Consequently for the most part same procedure can’t be utilized to ensure a wide range of media information.
We may not utilize the conventional encryption calculations to scramble pictures specifically in light of the fact that two reasons.
1) The size of picture is regularly bigger than content. Thus customary encryption calculations set aside bigger opportunity to scramble and unscramble pictures contrasted with content.
2) In content encryption both decoded and unique content must be equivalent. This condition is never valid for pictures. Because of human recognition; decoded picture with little contortion is generally worthy (Chang et al, 2001), (Jiri Jan, 2005), (David Salomon, 2005). We can diminish this discernible data by diminishing the connection among picture components utilizing certain change strategies (Mitra et al, 2006).
1.4 Digital Images
An advanced picture is characterized by a variety of individual pixels and every pixel has its own esteem. The exhibit, and consequently the arrangement of pixels, is known as a bitmap. In the event that we have a picture of 512 pixels × 512 pixels, it implies that the information for the picture must contain data around 262144 pixels (Steinmetz and Nahrstedt, 2002), (Kristian Sandberg, 2000).
Advanced pictures are created through a procedure of two stages:
Sampling and Quantization. Examining is the way toward isolating the first picture into little locales called pixels, though quantization is the way toward relegating a whole number esteem (i.e. shading) to every pixel.
The quantity of hues (i.e. shading space) that can be appointed to any photo component or pixel is an element of the quantity of bits, which is once in a while alluded to as the shading profundity or bits determination. This idea is otherwise called bits per pixel (bpp) that speaks to the shading for every esteem. The shading space is figured utilizing the accompanying condition:
ColorSpace = 2b….……………………….……………….Equation 1
where: b: the bit depth
Shading values utilized as a part of every bitmap relies on upon the particular bitmap organize. This implies every pixel in a bitmap contains certain data, normally translated as shading data. The data substance is dependably the same for every one of the pixels in a specific bitmap. In this way, every shading esteem in a bitmap is a parallel number. A paired number is a progression of parallel digits that can be either 0 or 1 and called bits. This twofold number in a given configuration will vary long contingent upon the shading profundity of the bitmap, where the shading profundity of a bitmap decides the scope of conceivable shading values that can be utilized as a part of every pixel. For instance, every pixel in a 24-bit picture can be one of about 16.8 million hues. This implies every pixel in a bitmap has three shading values in the vicinity of 0 and 255 and afterward those hues are shaped by combining shifting amounts of three essential hues: red, green and blue (Vaughan, 2004), (Rafael and Richard, 2002), (Sander, 2000).
Table 1.1 Image Properties
| Image Type | Bits resolution | Color space |
| Binary image (black and white) | 1 | 2 colors |
| Gray scale (monochrome) | 8 | 256 gray levels |
| Colored image | 8 | 256 colors |
| Colored image | 16 | 65536 colors |
| True color (RGB) | 24 | 16,777,216 colors |
As seen from Table 1.1, as the number of bits increases, the image quality is also increased. However, storage requirements will increase, resulting in a direct relationship between the image storage size and the bits resolution. Image storage size for an uncompressed image is computed using the following equation:
IMGSS = IMGR × BR …………….………………………..Equation 2
where:
IMGSS: Image storage size
IMGR: Image resolution (i.e. image width × image height)
BR: Bits resolution (bits depth)
For example, the storage size of a 640 pixels × 480 pixels, true colored image is given as follows:
IMGSS = W × H × BR = 640 × 480 × 24 bits = (7372800/1024/8) = 900 KB.
1.4.1 Digital Image Formats
Fundamentally, there are three sorts of picture records: bitmap, vector, and metafiles. At the point when a picture is put away as a bitmap record, its data is put away as an accumulation of pixels, show as hued or highly contrasting spots. At the point when a picture is put away as a vector document, its data is put away as scientific information. The metafile organization can store picture data as pixels (bitmap), scientific information (vector), or both. There is no single arrangement that is fitting for a wide range of pictures. As per research, bigger documents take more time to stack, require more plate space and can take more time to print, while little record sizes implies more prominent execution. The most well-known document organizations are talked about underneath:
a) BMP Files
As per Bourke (1998), the BMP Bitmaps are characterized as a consistent rectangular work of cells called pixels (Bourke, 1998). Every pixel contains a shading esteem as appeared in Figure 2.1
 M Pixels vertically
M Pixels vertically
N Pixels on a level plane
Figure 1.1 Image pixels
Bitmaps are described by just two parameters: the quantity of pixels, and the data content (shading profundity) per pixel, and they are the most ordinarily utilized sort to speak to pictures on the PC.
BMP is the local bitmap organization of Windows. BMP is a general arrangement that stores pictures in various shading profundities without pressure (Betcher and Gardner, 2006), (Paul Bourke, 1998), (James and William, 1996).
The BMP focal points are that every pixel is freely accessible for any adjustment or change, and that rehashed utilization of them doesn’t ordinarily corrupt the picture quality (Lancaster, 2003). The fundamental burden of this configuration is because of the extent of the records, which is generally bigger contrasted with different arrangements or other lossy pressure plans. All in all, a BMP document comprises of a header, illustrative data about the picture, (for example, width, stature, and so on), a discretionary Color Lookup Table (CLUT) region which contains the genuine shades of the picture pixels, and a pixel information territory (Shalini, 2004). The parts of the BMP document are shown in Table 1.2.
| Table 1.2 BMP file header | |
| Header | Stores general information about the BMP file. |
| Information header | Stores detailed information about the bitmap image. |
| Optional palette | Stores the definition of the colors being used for indexed color bitmps. |
| Image data | Stores the actual image, pixel by pixel. |
Header stores general data about the BMP document.
Data header stores definite data about the bitmap picture.
Discretionary palette stores the meaning of the hues being utilized for recorded shading bitmaps.
Picture data stores the real picture, pixel by pixel.
Shading Lookup Tables (CLUTs) take after the header for those lower execution modes in which they are utilized, for example, (1, 4, 8 or 16 query hues). These, thusly, are trailed by the real pixel information. The principle intrigue lies in the 24-bit uncompressed RGB shading mode. In this mode, there are no shading query tables utilized. Every pixel comprises of an 8-bit red esteem, an 8-bit green esteem and an 8-bit blue esteem [6].
b) GIF Files
The Graphics Interchange Format (GIF) was initially created by CompuServe in 1987. It is a standout amongst the most prominent document positions for web design and trading representation records between PCs. The GIF organize underpins 8 bits of shading data that is constrained to 8 bits palette and 256 hues. Hence, just 256 distinct hues are accessible to speak to the photo. It can be seen by every normal program.
GIF pictures are naturally packed when they are spared utilizing a lossless pressure technique known as LZW (Lempel-Ziv-Welch) that does not debase the picture quality. GIF arrange gives four principle highlights: intertwining, straightforwardness, record pressure, and primitive activity. The intertwining highlight permits the program to show parts of the picture as it overhauls. The first picture begins off with low quality yet shows signs of improvement as a greater amount of the joining parts are upgraded. GIF records permit clients to see a segment of the picture as the document is mountained. One of GIF’s shortcomings is that GIF pictures are constrained to a most extreme of 256 hues. The nature of the picture endures if the shading profundity is diminished to not as much as the shading profundity of the first picture. GIF records can store any of the 16.8 million hues however just a most extreme 256 hues in each GIF document. Accordingly, while changing over a picture to GIF, the program packs the document by lessening the quantity of hues in the picture from 24-bit (a huge number of hues) to 8-bit (256 hues). Be that as it may, the GIF document arrange can store different pictures in a solitary record and play the pictures in a circle, along these lines giving the presence of movement
c) JPEG Files
The Joint Photographic Experts Group, (JPEG) configuration, is a standout amongst the most prevalent organizations for web illustrations. It underpins 24 bits of shading data. The JPEG document organize stores the greater part of the shading data in a RGB picture, and after that it packs the record size to spare storage room, or it spares just the shading data that is fundamental to the picture. Dissimilar to GIF, JPEG does not bolster straightforwardness.
The pressure strategy utilized as a part of JPEG is generally lossy pressure, implying that some visual quality is lost all the while. JPEGs can be spared in an assortment of lossy pressure levels. This implies pretty much pressure can be connected to the picture, contingent on which looks best. JPEG can be utilized by any program. Since JPEG is a picture compressor, it is best utilized for photographic quality pictures and point by point delineations with many hues
The upside of JPEG is that it is a very compacted record arrange. Consequently, the picture can be compacted while the quality is kept up. JPEG shortcoming is that lossy pressure may bring about low quality design. Another shortcoming noted in JPEG configurations is that there is no support for pixel straightforwardness. JPEGs lose quality each time they are opened, altered and spared. It is imperative to minimize the quantity of altering sessions between the underlying and last form of a JPEG picture
d) PICT Files
The Picture File Format (PICT) is utilized basically on the Macintosh stage. It is the default organizes for Macintosh picture documents as its standard metafile design. The PICT arrangement is most generally utilized for bitmap pictures however can be utilized for vector pictures also. The PICT is a lossless configuration. Since the PICT design underpins just restricted pressure on Macintoshes with QuickTime introduced, PICT documents are normally vast. PICT is utilized for pictures in video altering, movements, desktop PC presentations, and sight and sound composing.
e) EPS Files
The Encapsulated PostScript (EPS) document configuration is planned to make records usable as a representation document arrange. The EPS record organization is a metafile design. It can be utilized for vector pictures or bitmap pictures. It can likewise be utilized on an assortment of stages, including Macintosh and Windows. In the event that an EPS picture is put into a report, we can scale it up or down without data misfortune.
f) PNG Files
The Portable Network Graphics (PNG) arrangement is a bitmapped picture organizes that utilizes lossless information pressure. It will probably be the successor to the GIF record organizes. PNG is required to end up distinctly a standard configuration for web pictures and could supplant GIF altogether. It is stage autonomous and ought to be utilized for single pictures just (not movements). Contrasted and GIF, PNG offers more prominent shading backing and better pressure, gamma rectification for splendor control crosswise over stages, better support for straightforwardness, and a superior technique for showing dynamic pictures.
g) TIFF Files
The Tag Interchange File Format (TIFF) is a tag-based universal standard for putting away and exchanging bitmaps amongst applications and equipment stages. It is good with an extensive variety of programming applications and can be utilized crosswise over stages, for example, Macintosh, Windows, and UNIX. The TIFF configuration is mind boggling; hence TIFF records are by and large bigger than GIF or JPEG documents. TIFF bolsters lossless LZW pressure. The organization comprises of things called labels which are characterized by the standard. Every tag is trailed by a label subordinate information structure.
1.5 Statement of the problem
Image Encryption is a wide range of research. Encryption essentially manages changing over information or data from its unique shape to some other frame that conceals the data in it. The first information is normally alluded as plain information and the changed over frame is called figure information. Encryption can be characterized as the craft of changing over information into coded shape which can be interpret by planned recipient just who postures learning about the unscrambling of the figured information. Encryption can be connected to content, picture and video for information security the insurance of picture information from unapproved get to be critical. Encryption is utilized to build the information security. The encrypted image is secure from any sort cryptanalysis.
Digital images are alluring information sorts with far reaching scope of utilization and numerous clients are intriguing to actualize content insurance strategies on them to keep from see, copyright or control [7]. In numerous applications like military picture databases, private video conferencing, therapeutic imaging framework, digital TV, online individual photo collection, security in basic. Additionally wide utilization of pictures in mechanical process transforms it into an asset and resource, so it is vital to shield the private picture information from unapproved get to.
AES calculation is not just for the content information. The image focuses, in particular, pixels, spatial co-ordinates that show the position of the desired information in the picture. The uses of the picture handling have been usually found in the Military correspondence, Forensics, Robotics, Intelligent frameworks and so on. In this paper, we actualize the AES calculation which is a proficient plan for both equipment and programming usage.
“To improve the execution of AES (Advanced Encryption Standard) calculation for giving secure pictures over open systems”
1.6 Definition of terms
Cryptography: Art and Science of making secure messages
Encryption: Procedure for change of Plain Text to Cipher Text.
Decryption: Conversion of Cipher Text to Plain Text.
Symmetric Key Cryptography: Usage of same key for encryption and unscrambling
Asymmetric Key Cryptography: Usage of various key for encryption and decoding.
AES: Advanced Encryption Standard: It is a symmetric key calculation utilized for encryption of information.
1.7 Purpose of the study
Multimedia encryption technology was first introduced in 1980 and became a hot topic for research during the mid-90s. Its development can be categorized into three stages; raw data encryption, compressed data encryption, and partial encryption. Before the 90s, only a few multimedia encoding methods were standardized. Most multimedia data (image, video) were transmitted or stored in raw form. Multimedia encryption was mainly based on permutation or scrambling of pixel, i.e., the video/image is modified so that the resulting data is incomprehensible. For example, space-filling curves are used to modify the image/video data, which hence confuses the relation between neighboring images/video pixels. European TV networks use the Euro crypt standard to encrypt the signals, which modifies the field line by line. These methods are used for the reason of having low computing complexity and cost. Nevertheless, this type of modification changes the relation between neighboring pixels, making compression operation not work. Therefore, these encryption algorithms are only useful for an application that does not require compression.
During the early1990s, with the advancement of multimedia technology, some image and audio/video encoding standards were developed such as JPEG, MPEG, etc. Generally, these types of multimedia data are compressed before being stored or transmitted making raw data encryption not suitable for this application.
After the advancement of internet technology during late 1990, a multimedia application created required more real-time operation and interaction. By only encrypting certain parts of the data, the size of the final encrypted file can be reduced improving the encryption efficiency. Due to the rapid growth of the network, the advancement in information security becomes vital in order to protect the secrecy and privacy. Encryption algorithms play a vital role in information security [8].
The most commonly used encryption algorithms include AES and DES. These algorithms can be used by someone who wants to secure a large quantity of information by making a data file which can be encrypted or decrypted using the AES or DES algorithm. An extensive variety of connected media conveyance later on system is turning out to be progressively predominant. Data securities issues have likewise turned out to be progressively conspicuous particularly image cryptography for secure transmission. Be that as it may, customary encryption strategies for computerized picture are constrained. Along these lines, it is important to investigate new elements for image encryption. The approach of individual correspondence frameworks like portable PCs, cell phones and individual tablets, and the expanding reliance on the Internet prompting to rupture of security. Embracing diverse cryptographic calculations in advanced computerized correspondence frameworks utilizing an assortment of systems guarantees secrecy. Already AES is being utilized for instant messages. Image encryption procedures scramble the pixels of the picture and abatement the connection among the pixels, with the end goal that the encoded picture can’t be gotten to by unapproved client. In this review, execution of AES is improved to produce secure pictures.
1.8 Theoretical basis
Nowadays with more mechanical headways in the field of correspondence there is considerably more continually expanding danger to information which is being uncovered in the earth of cryptographic assaults. With more headway in web applications there is a great deal of basic information which is shared by the client and that must be shielded from illicit use by the programmers. As the development of innovation, correspondence through web and remote techniques has turned into a progressive headway recently. So the never showing sign of change quality which is of most extreme unmistakable quality is the exceptionally fundamental need to shield the information from its unapproved access of the data. With expanding slant towards data security there was much more preference concerning security calculations which goes about as a blockade between the programmer and the basic information. As there were a great deal of security calculations which advanced out of the cause and were picking up its own thankfulness at various fields of its utilization, the US government needed to institutionalize a cryptographic calculation which will be utilized generally by them called AES (Advanced Encryption Standards). In 1997 NIST declared a program to create and pick an Advanced Encryption Standard to supplant the maturing Data Encryption Standard (DES).They requested calculations from the cryptographic group, with the purpose of picking a solitary standard. Fifteen calculations were submitted to NIST in 1998, and NIST picked five finalists in 1999. In 2000, Rijndael was chosen by getting the most votes as the AES calculation. NIST’s’ three choice criteria were security, execution, and adaptability. Effectiveness of calculations was additionally another essential model. Two attributes were resolved as basic in the choice of the AES: security and effectiveness
1.8.1 Working and Structure of AES
This method was developed by two Belgian researchers, Vincent Rijmen and Jon Daemen. There are three phases in the AES calculation. The principal stage is the key timetable calculation, which produces the 10 round keys which are to be utilized as a part of the encryption and unscrambling operation. The encryption operation delivers the ciphertext and the unscrambling operation creates the first plaintext. Every sub-change in each round is known as a stage. There are 4 such strides in the encryption operation, which are “Add Round Key”, “Sub Bytes”, “Shift Rows” and “Mix Columns” in a specific order. These means are basic in each round of the encryption calculation aside from the last round where the Mix-Columns step is excluded. The “Sub-bytes” and “Mix Columns” steps have their reverse partners in the decoding operation and are called “inv-Sub-bytes” and “inv-Mix-Columns” separately. The decoding operation likewise highlights an indistinguishable arrangement of ventures from the encryption operation where the last round change is feeling the loss of the “inv-Mix-segments” step.
Before the beginning of the first round, the initial state matrix of the plaintext data is bit-wised XORed with th e round key as explained in the“AddRoundKey” Step.
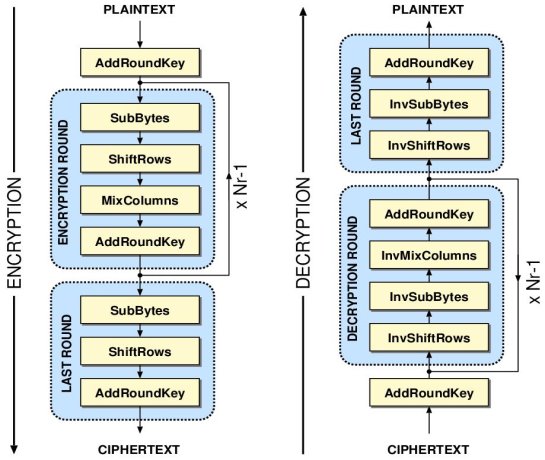
Figure1.2 Structure of AES Encryption and Decryption Process
1.8.2 AES Block Cipher Mode of Operation
ECB, CBC, OFB, CFB, CTR, and XTS are the distinctive methods of operation of AES. Taking after segment quickly presents cryptographic modes and cushioning methods.
A. What is Mode of Operation?
In cryptography some calculation utilizes a square figure to give a data administration, for example, privacy or legitimacy, these calculations are called as method of operation of cryptography. The safe cryptographic change (encryption or decoding) of one settled length gathering of bits called a square is the main capacity performs by square figure. To safely change measures of information bigger than a square it is expected to over and over apply figure’s single-piece operation.
The methodology of applying this operation is depicted by method of operation calculation. For every encryption operation the vast majority of the modes require a remarkable two fold succession which is called initial vector (IV). The IV is constantly should have been non-rehashing and for a few modes irregular as well. Notwithstanding when the same plaintext is scrambled various circumstances freely with a similar key, un mistakable cipher texts must be created every time. To guarantee that utilization of instatement vector is essential. Size of pieces inside a square figure mode might be variable however amid change the piece size is dependably settled. Operation on part of figure is performed onto the total square.
Amid this operation, it is require that, the last part of the information must be cushioned to a full square on the off chance that it is littler than the present piece measure. In a few modes piece figure is adequately utilized as a stream cipher. In such modes padding does not require.
Customarily, primary utilization of encryption modes is to give blunder spread property under different situations of information modification. As of late up rightness assurance is a totally isolate cryptographic objective.
In effective route mix of secrecy and realness is given by some cutting edge methods of operation. These modes are known as verified encryption modes.
In AES calculation classification is given by piece figure modes for example, ECB, CBC, OFB, CFB, CTR, and XTS, yet they don’t ensure against unplanned alteration or malevolent altering. These mis chances are recognized with a different message verification code, for example, CBC-MAC, or a computerized signature.
B. Initial Vector (IV)
Introduction vector (IV) or beginning variable (SV) is a piece of bits. A few modes utilize it to randomize the encryption. By this randomization it produces particular cipher texts regardless of the possibility that the same plaintext is encoded various circumstances, without the requirement for a slower re-keying process. Security necessities of an introduction vector are not the same as a key, so the IV ordinarily does not should be mystery. In this manner as a rule, it is essential that an instatement vector is never reused under a similar key.
In any case, for CBC and CFB mode, because of reusing an IV releases some data about the main square of plaintext, and about any basic prefix shared by the two messages. For OFB and CTR both modes viably make a bit stream that is XORed with the plaintext, and this bit stream is needy on the secret key and IV as it were. Because of that in these modes, reusing an IV totally crushes security. This can be seen on the grounds that both modes successfully make a bit stream that is XORed with the plaintext, and this bit stream is reliant on the secret word and IV just. In CBC mode utilize of the IV is must; what’s more, it ought to be unusual at encryption time. In this manner it can be presume that, the (beforehand) basic practice of re-utilizing the last figure content square of a message as the IV for the following message is shaky.
In CBC IV assault, if an aggressor knows the IV or he knows the past piece of figure content before he indicates next plaintext. In such situation an assailant can figure about the plaintext of some piece that was encoded with a similar key before.
C. Padding
A square figure takes a shot at settled piece measure units, however length of coming messages are variable. So, a few modes like ECB and CBC require that the last square must be padded before encryption. In cushioning technique additional bits are cushioned (i.e. included) in instant message to make require size of square for encryption.
A few cushioning plans exist. In least difficult cushioning plan we add invalid bytes to the plaintext to convey its length up to several of the square size. In this plan mind must be taken that the first length of the plaintext can be recouped. For instance, on the off chance that the plaintext is a java style string which contains no invalid bytes with the exception of toward the end.
Another more mind boggling illustration is the first DES technique. In this technique to fill out the square a solitary piece is included, trailed by enough zero bits. An entirety cushioning piece will be included at whatever point this message closes a square limit.
1.8.3 Salient component of AES:
AES is a block cipher with a piece length of 128 bits. It takes into account three diverse key lengths: 128, 192, or 256 bits. AES Encryption comprises of 10 rounds of preparing for 128-piece keys, 12 rounds for 192-piece keys, and 14 rounds for 256-piece keys. With the exception of the last round for every situation, every single round is identical. Each round of method incorporates one single-byte based substitution step, a line wise change step, a segment insightful blending step, and the expansion of the round key. The request in which these four stages are executed is diverse for encryption what’s more, unscrambling. To welcome the handling steps utilized as a part of a solitary round, it is ideal to think about a 128-bit×4 piece grids comprising of a 4 of bytes, orchestrated as takes after:
 byte0 byte4 byte8 byte12
byte0 byte4 byte8 byte12
byte1 byte5 byte9 byte13
byte2 byte6 byte10 byte14
byte3 byte7 byte11 byte15
In this way, the initial four bytes of a 128-piece input square involve the principal section in the 4 x4 framework of bytes. The following four bytes possess the second section, and so on. The×4 4 framework of bytes is alluded to as the state exhibit. Each round of preparing takes a shot at the information state exhibit and creates a yield state cluster.
The yield state exhibit created by the last round is adjusted into a 128-piece yield square [9]. Unlike DES, the unscrambling calculation contrasts generously from the encryption calculation. Although, by and large, similar strides are utilized as a part of encryption and decoding, the request in which the means are completed is distinctive. While AES requires the block size to be 128 bits, the first Rijndael figure works with any square size (furthermore, any key size) that is a numerous of 32 the length of it surpasses 128.
The state exhibit for the diverse piece sizes still has just four columns in the Rijndael figure. Be that as it may, the quantity of sections relies on upon size of the block.
For instance, when the block size is 192, the Rijndael figure requires a state cluster to comprise of 4 lines and 6 columns. In terms of security no assault has been found for AES, utilizing the full number of rounds, which is more proficient than 296 for AES-192. Of particular note in this setting is the way that AES, because of an expansive torrential slide impact, is viewed as safe to related content assaults. The torrential slide impact in this setting alluding to the property that a little contrasts in-put prompts to extensive contrasts in the yield. However some side-channel assaults, assaults on Implementations that spill data somehow, has been found for a few executions of AES, however the greater part of them have been immediately fixed at the point when the assault got to be distinctly known.
1.8.4 Strengths:
- AES is extremely fast compared to other block ciphers. (Though there are tradeoff between size and speed)
- The round transformation is parallel by design. This is important in dedicated hardware as it allows even faster execution.
- AES was designed to be amenable to pipelining.
- The cipher does not use arithmetic operations so has no bias towards big or little endian architectures.
- AES is fully self-supporting. Does not use SBoxes of other ciphers, bits from Rand tables, digits of or any other such jokes.
- AES is not based on obscure or not well understood processes.
- The tight cipher and simple design does not leave enough room to hide a trap door.
1.9 Contributions of the study
ENCRYPTION
| AES | Proposed (AES NEW) |
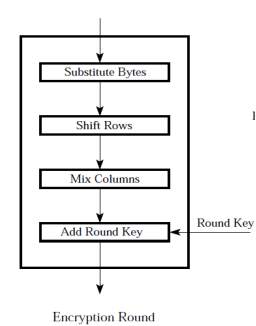 |
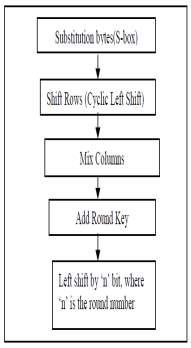 |
Fig 1.3 Present Method vs. Proposed Method
S-BOX
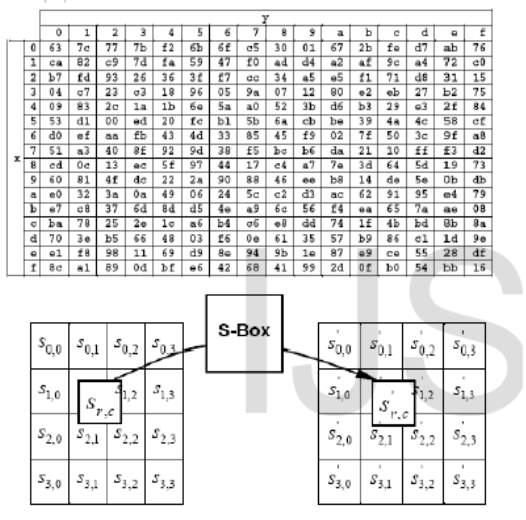
Fig 1.4 S-Box
The properties S-boxes have been widely used as a base of new encryption strategies such as nonlinearity, differential uniformity, and strict avalanche criterion A (x, y)-S-box is a map,
S : {0,1}x →{0,1}y .
It comprises of n-variable component Boolean functions:
(f1 (x1 ,…,xn),f2 (x1 ,…,xn),…,fn(x1 ,…,xn)) each of which need to satisfy S-box properties.
The following are the list of several properties in S-box.
- Robustness
Let F = (f1, f2,…,fn) be an n × n S-box, where fi is a component function of S-box mapping fi : {0, 1}n →{0, 1}
F is Robust to against differential cryptanalysis
- Balancing
S:{0,1}n→{0,1}m balanced, if HW(f) = 2n-1. The significance of the balance property is based on the higher the magnitude of function imbalance, a high probability linear approximation being obtained.
- Strict Avalanche Criterion (SAC): A change in one bit of input bits of S-box should produce a change in half of output bits of S-box. It is harder to perform an analysis of ciphertext, when trying to come up with an attack. A cryptographic function which satisfies the above condition is said to be satisfied Strict Avalanche Criteria.
- Nonlinearity S :{0,1}x →{0,1}y is defined as the least value of nonlinearity of all nonzero linear combinations of x Boolean functions fi : {0,1}→{0,1}, i= x-1,…,1,0. The nonlinearity of an S-box must be high to resist against linear cryptanalysis.
- Differential Uniformity: The smaller is the Differential Uniformity; the better is the S-box’s resistance against differential cryptanalysis.
vi) Linear Approximation: The lower is the Linear Approximation value, the better is the S-box’s resistance against linear cryptanalysis.
vii) Algebraic Complexity: The Algebraic Complexity is important to resist against interpolation attack and other concerning algebraic attacks.
viii) Fixed (Fp) and Opposite Fixed Points (OFp): The number of these Fp and OFp should be kept as low as possible to avoid leakage in any statistic cryptanalysis.
ix) Bit independence criterion: The bit independence is a highly desirable property as with increasing independence between bits, it becomes more difficult to understand and predict the design of the system.
“S-box to resist against linear cryptanalysis and differential cryptanalysis attacks”.
Shift Rows:
AES 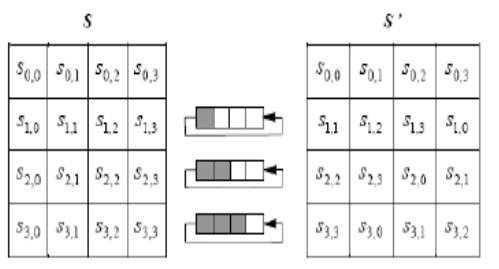
Fig1.5: Shift Rows
Mix Column
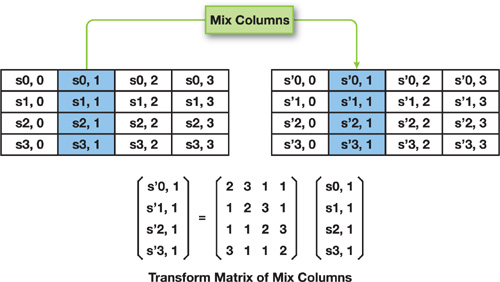
Fig1.6 Mix Columns
Add Round Key
The logic behind generation of round key is, to retain avalanche effect change in bit should affect round keys for many rounds and if the key gets changed then after decryption with such keys will not give the original image back, but will result in different image or some noise.
To ensure diffusion property after add round key again the bits are left shifted as per the round number.
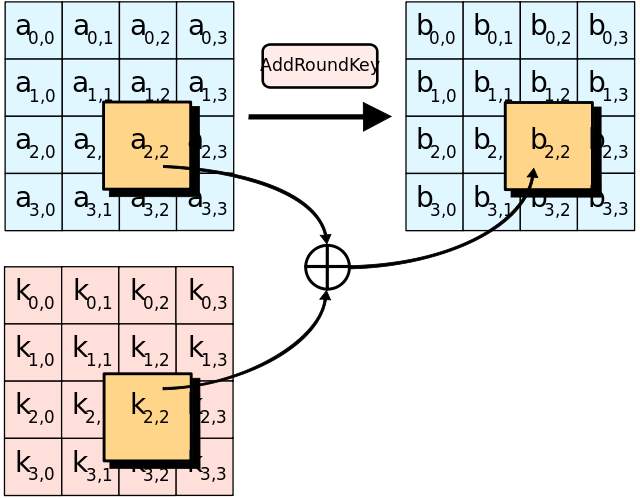
Fig1.7 Add Round Key
1.10 Organization of the remainder of the study
The remaining part of the Thesis is divided into various chapters. Chapter 2 is about the Literature Survey which helped to understand the concepts through observations of various eminent research scholars and find the research gaps. In Chapter 3 the focus is on the Methodology which explains about how to enhance the performance of Advanced Encryption Standard for getting more secure images. Results and Validation of results is depicted in Chapter 4.. While and before developing the thesis, guidelines are obtained by referring to various publication, books, and websites. All these are mentioned in Chapter 5 as References. The content which is indirectly relevant to making the thesis but plays a key-role is embellished at the end of thesis in chapter 6, Appendices.
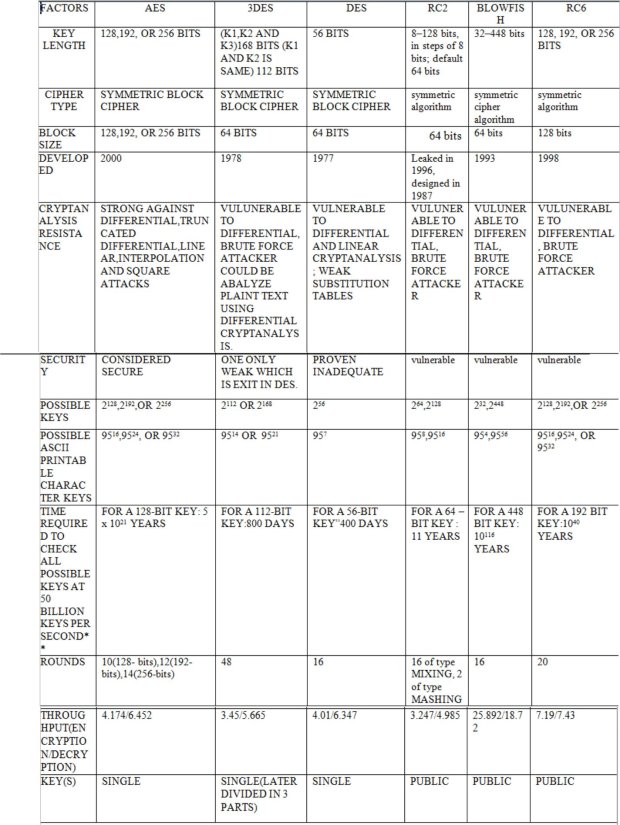
Fig 1.8: Comparison of various Symmetric key algorithms
CHAPTER-2
2.1 Literature Review
The AES is utilized by numerous analysts for encode plain content just, it was restricted to scramble an extensive size documents, and it sets aside a long opportunity to scramble the substantial plain content records, for this situation on its square information is 64 for every cycle. The Researcher Wang and Xu [10] is prevailing with regards to expanding the block size from 64 to 512 bits for every cycle, and expanding the rounds from 12 to 24 in various techniques for utilizing modified round keys with the AES. The National Institute of Standards and Technology (NIST) characterize six methods of operation that can be utilized with AES: Electronic Code Book (ECB), Cipher Block Chaining (CBC), Cipher Feed Back (CFB), Output Feed Back (OFB), Galois Counter Mode (GCM) and Counter (CTR) where CTR is default mode in AES algorithm. A few specialists changed the name of this calculation from AES to new name ” Extended AES Algorithm”, the outcomes increment the course of events process with a high expansive document length, for instance, 1GB takes a couple of minutes to finish the encryption, dissimilar to the standard AES which take a more drawn out time if contrasted and the former [Wikpedia, 2008].
Image Encryption [11] can be obtained by utilizing different techniques. Most broadly utilized techniques utilize production of perplexity utilizing CHAOTIC METHODS, scrambling the pixels of the picture, which diminishes the connection between’s the pixels of the Image. A few techniques additionally utilize compression before applying encryption techniques, keeping in mind the end goal to manage huge size of pictures. Compressions are of two sorts: lossless compression and lossy compression. Each has its own particular strength and weaknesses. One needs to pick between these two relying upon the application. Some encryption systems makes utilization of Message Digest, Digital Signatures and Hash values of the picture other than the picture in the subject and utilize same as the key for encryption and decoding of the pictures. Hybrid methodologies were being used. It guarantees more security by taking the benefits of the both the techniques and conquering disservices of each. Propelled strategy for existing encryption strategies can likewise be utilized for image encryption.
A couple of discoveries which used above said strategies
- In Thesis by Kshitij Bhetwal, describes various cryptography techniques and sub-techniques. Some techniques perform partial encryption while others perform full encryption. Some of the methods carry out image compressions but others do not. Depending on the type of application, speed, bandwidth, confidentiality, security and authenticity extent, one may select a particular type of encryption method. Each and every method has its own merits and demerits. One must think in selecting a proper cipher because now cryptanalysis techniques research is under focus [3].
- In the findings of Orr Dunkelman ,various cryptanalysis techniques of like chosen plain text attack, known cipher text attack, differential crypt analysis ,linear cryptanalysis of block cipher are analyzed along with strength of Fiestel structures.
- In thesis by Jagannath Prasad, various cryptography techniques and sub- techniques with referent to partial encryption and full encryption are detailed with emphasis criteria like type of application, speed, bandwidth, confidentiality, security and authenticity extent and selection of a proper cipher mode [5].
- In the study by Sreenivasulu Nagireddy with title “A Pattern Recognition Approach to Block Cipher Identification” focal point is finding starting position of the captured cipher text with the intention to check various vulnerabilities [6].
- Sourabh Singh and Anurag Jain published their finds under the title “An Enhanced Text to Image Encryption Technique using RGB substitution and AES” ,w when implemented will lead to a highly secure transmission of text. If a hacker any how decrypts the image then he gets another image, which further confuses him whether the actual information is in text or in image format, the blend of text to image transformation and then AES encryption makes actual information (plain text) highly secure for transmitting it on extremely vulnerable and insecure network environment[7].
- Harleen Kaur and Reena Mehta proposed new AES with new modified key expansion which results in strong cipher in addition to reduction in encryption timing. Histogram graphs are projected for showing the results [8].
- Osama Abu Zaid et all compared quality of encrypted image with another image, which was encrypted using a different algorithm based on the parameters like maximum deviation factor ,correlation coefficient in their work titled “Encryption Quality Measurement of a Proposed Cryptosystem Algorithm for the Colored Images Compared with Another Algorithm “[9]
- Junshe Wang et all proposed “Improvement of the Round Key Generation of AES” improvement in the round key generation of AES by taking 10 round AES algorithm as the example , the initial 4 words seed key expands to 44 word sub-key. Among them, Key dependent relationship for Ki depends Ki-1 and Ki-4 (for i=4….43).First it generates the original key and 40 words sub key are generated by the seed key and subsequent transformation [10]
- Shikha Jaryal and Chetan Marwaha has shown comparative analysis of various image encryption techniques with respect to key space, correlation between the pixels, Number of Pixels Change Rate(NPCR) in reference to Brute force attack, statistical attack, differential attack and signal to noise ratio attack.[11]
- Mamta Junega and Parvinder has reviewd various cryptographic techniques like AES,DES,BlowFish,3DES and image encryption by AES.This has been published under the title “A review of cryptographic techniques and Implementation of AES for images” [12]
- Mohit Kumar et all worked on various image encryption algorithms and concluded with a note that chaotic approach exhibits extreme uncertainty and provides incredible Security. Encryption algorithms should provide large key space, generate uniform histogram ,satisfy Shanon’s confusion and diffusion property.[13]
- Vikas Agrawal et al detailed the process of Encryption and Decryption in case of Symmetric key and public key cryptography using AES and DES algorithms and modified RSAalgorithm w.r.t the propertiesof(a) Lossless encryption of image. (b) Less computational complexity. (c) Convenient realization. (d) Choosing a suitable size of matrix according to the size of image. (e) Encryption/decryption scheme uses integer arithmetic and logic operations. Both colour and black & white image of any size saved in tagged image file format (TIF) can be encrypted & decrypted using blowfish algorithm. MREA algorithm is used to encrypt files and transmit encrypted files to other end where it is decrypted. Main feature of this method is that it satisfies the properties of Confusion and diffusion and also has a perfect guess of encryption key makes decryption impossible[14]
- Ismet et al analyzed current image encryption algorithms and compression is added for two of them (Mirror-like image encryption and Visual Cryptography). In this work MIE and VC algorithms have been improved by adding compression capability. As we can see from the experimental results jpeg with quality parameter set to 100 does not compress grayscale image, besides size of the grayscale image increases, because noise in the image cannot be compressed productively. Quality setting set to 90 or below reaches good compression ratios. However jpeg is not suitable for color images (even with quality set to 100) because of the loss in the color. Thus PNG lossless compression is ideal for color image compression with MIE. VC is not a lossless encryption in nature, thus compression algorithm have to chosen carefully. Lossless PNG compression for gray-level and color images has a big compression ratio because it has only one color plane to encrypt and saves storage space and network bandwidth up to 91.4%.[15]
- Priya Deshmukh Described Image Encryption and Decryption using AES algorithm is implemented to secure the image data from an unauthorized access. A Successful implementation of symmetric key AES algorithm is one of the best encryption and decryption standard available in market. With the help of MATLAB coding implementation of an AES algorithm is synthesized and simulated for Image Encryption and Decryption. The original images can also be completely reconstructed without any distortion. It has shown that the algorithms have extremely large security key space and can withstand most common attacks such as the brute force attack, cipher attacks and plaintext attacks[16]
- Mrs. Smita Desai wrote paper is about encryption and decryption of images using a secret-key block cipher called 64-bits Blowfish designed to increase security and to improve performance. This algorithm will be used as a variable key size up to 448 bits. It employs Feistel network which iterates simple function 16 times. The blowfish algorithm is safe against unauthorized attack and runs faster than the popular existing algorithms. The proposed algorithm is designed and realized using Visual basic. To achieve this result to be true, we are comparing different parameters such as processing time, bandwidth, correlation, entropy etc of above mentioned algorithms with the other algorithms such as AES, DES, RijnDael. Blowfish cannot be broken until an attacker tries 28r+1 combinations where r is the number of rounds Since Blowfish has not any known security weak points
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




