Internet Evolution and Effects of Cybercrime
Info: 8811 words (35 pages) Dissertation
Published: 1st Mar 2022
Tagged: CriminologyCyber Security
Abstract
This paper will talk about internet evolution, and how its use has changed the world and the way people live and function. The internet has definitely revolutionized the way people connect these days and also the way data is distributed between interacting parties. Internet technology has made the world smaller in its distinctive way, as it has become an everyday standard and relatively essential part for everyday living.
The Internet of Things (IoT) technology, mobile apps, and instant communication across the globe are now settled in all aspects of public businesses. As people continue to sail in cyberspace waters and handle majority of professional businesses virtually, this has generated huge chances for cyber-crime.
Widespread cybercrime, that has become a transnational crime, has brought together crime fighting entities all around the globe and forced them into international collaboration, more than any other criminal activity. A lot of things and laws needs to come in place before cyberworld become safer place. United against cyber-crime, people on this planet will win over and aggressively fight back to strengthen national cybersecurity position in a limitlessly connected world. The whole planet needs to contribute to make an important difference with a sound and multidimensional approach against cybercrime.
Internet has made the world smaller
The internet has definitely revolutionized the way people connect these days and also the way data is distributed between interacting parties. Thanks to internet technology people can easily virtually travel to any destination in the world, while it was never imaginable before.
Internet technology is in charge of the global immediate interaction that comes by advantage of technology. This advantage also promotes increase in productivity and assists businesses to operate more efficiently than in the past. With just a few key strokes people are able to buy goods, exchange ideas, meet new people and new cultures that exist in other parts of the world, which used to be impossible to realize for some people. Instant access to the information has greatly contributed to extend human reach. Products and services have become easily accessible with advance of telecommunication, free social media and flexible mobile networks. Also, internet technology, enables instant access to current worldwide news, and traditional businesses are able to function much easier and more proficient and effective.
Internet technology has made the world smaller in its distinctive way, as it has become an everyday standard and relatively essential part for everyday living due to the fact that everyone and everything relies and revolves around internet technology. It is inevitable, especially for those living in an urban city and modern society. Old methods such as dial-up internet and switchboard have been replaced with condensed systems. All these facts are the true evidence that internet technology has made this world smaller place and through internet connection, people are able to interact and communicate like they are minutes away instead thousands of miles away across the globe.
Despite all the benefits that internet technology has to offer, there are some downsides that also makes our world smaller. One third of population across the globe still does not have access to internet and technology, therefore those countries have difficulties to catch up with the rest of the world, and therefore they are actually falling behind or even stand still in comparison with the countries with advanced communication industries.
Throughout life, people experience numerous changes, bringing advances in way people communicate, operate and exist. Those changes and technology evolution will not stop here, rather it will continue to bring new ways people operate, communicate and conduct their businesses on global level. After all, whether the world is getting bigger or smaller thanks to internet technology, awareness that evolves around its use and its psychological influence on society makes it more important fact to keep in mind. The speed that the internet technology has changed, forced our human beings to change as fast and acclimate to this new cyber trend.
IoT - Internet of Things
Connection leads into connection. In 1999, when only 4% of the world’s population was able to connect online, the term Internet of Things (IoT) was discovered by Kevin Ashton. Ever since then, world has seen continuous smartification of electronic devices and technology: TVs, phones, cameras, thermostats, microphones, pressure gauges, glucose sensors, EKGs, and many more. In today society, 49% of the world’s population has an internet connection and an approximately 8.4 billion people worldwide have things connected online. Currently, the IoT is in full bloom. The most public things in the flourishing of IoT are voice activated assistants, cars, household appliances and other systems, medical devices, smart meters, personal health and fitness trackers, and many more. This advantage of connectivity brings along security and safety weaknesses. Many developers are recognizing the potential dangers and thinking of ways how to produce better IoT technology with improved security. Despite of major cybersecurity concerns, incidents and privacy violations, most technology experts predict that the Internet of Things will continue to successfully grow in the next few years, binding machines to machines and connecting people to valuable services, resources and opportunities. (Rainie & Anderson, 2017).
Cyber Crime - Global Crisis
The Internet of Things (IoT) technology, mobile apps, and instant communication across the globe are now settled in all aspects of public businesses such as health, education, banking, transportation, and other critical infrastructure. According the authors Stalans and Finn (2016):” Over 3 billion people and over 40% of the world population, have used the Internet in 2016. The majority of households (at least 80%) have access to the Internet in their homes in Canada, France, Germany, the United States, and the United Kingdom (http://www.internetlivestats.com). Over half of the population in the Middle East and Latin America, 40% of the population in Asia, and about one quarter of the African population accessed the Internet on one day in November 2015 (http://www.internetworldstats.com/stats.htm). “
As people continue to sail in cyberspace waters and handle majority of professional businesses virtually, this has generated huge chances for cyber-crime. Cybercrime is a new trend of crime and thanks to internet businesses, cyber criminals use their twisted skills to commit identity thefts, various fraudulent activities and even property crimes. The wide extent of cyberspace enables terrorist groups to recruit, organize, spread and promote their ideas through cyber channels, online propaganda and other virtual resources. Online crime is affecting millions people and numerous businesses across the globe on a daily basis. Cyber-crime has become one of the most challenging and difficult problem for today society, for the court system and law enforcement. Due to incompetent, inadequate, inaccurate, and often partial analysis, it is hard to define the full extent of cyber-crimes. For example, cybercrime statistic reports in security systems industry may cause fault estimate of hacking incidence by reporting low-level programmed interruptions that actually do not interrupt functioning or eliminate important information. Furthermore, some cybercrimes containing worms, malware, or ransomware very often are built as resistance methods to business practices or unjust government, missing consensus on identifying and labeling the particular forms of hacking as a lawbreaking conduct.
In the news article “Cyber-crime could trigger a global crisis”, written by Tony Glover in 2012, it was discussed that the widespread cyber fraud that is affecting banks worldwide as high as it is can potentially lead into another global financial crisis. There is a strong evidence that this problem has possibly devastating consequences. Glover (2012) also stated that according to some reports, cyber criminals are spending their massive fortune on buying political authorities and paying for various forms of protection to cover their criminal activities. While there are no reliable indicators available to estimate cyber fraud, cyber-security experts think that the cyber fraud involving banks is far more profitable than the worldwide distribution of illegal drugs. However, cyber fraud has something in common with the worldwide distribution of illegal drugs. According to security specialists, cyber criminals use “mules” to smuggle money in similar way the drug dealers use individuals, also called “mules”, to smuggle drugs. The only difference is that while drug “mules” smuggle quite small amounts of illegal drugs across the border, cyber “mules” commonly use their personal accounts to keep and handover millions of dollars fraudulently deposited from virtually robbed banks.
The new crime trend, cyber hacking, started by the Triad mobs in Hong Kong. Glover (2012) wrote in his article: “At first, it took a fairly primitive form. The stiff cardboard from the tops of Cornflake packets was used to create fake bank cards for insertion into cash machines. For years, the banks would not admit that the Triad’s hackers could break their security codes. Today, cyber hacking is taking place on a far greater scale, with China now becoming a key player and hacking into corporate as well as private bank accounts.” Without a doubt, hackings and cyberattacks are streaming from China, but it is also likely that many of such activities actually originate from other countries with activities channeled through China to shift the blame. (Glover 2012).
Data breaches have international scope
Data breach incidents has reached its high record in 2016. According to a cybersecurity company “Risk Based Security “there were 4,149 incidents in102 world countries, causing a breach of more than 4.2 billion records. Another survey, so called Ponemon’s survey, has underestimated the extent of global data breaches, stating that 51% of respondents reported a global record breach in the past five years, and 56 % of companies suffering from the breach, has been hit by the incident more than once. (Experian, 2017).
Wong and Solon (2017), in their article: “Massive ransomware cyber-attack hits nearly 1000 countries around the world” wrote that:” Security researchers at Kaspersky Lab have recorded more than 45,000 attacks in 99 countries, including the UK, Russia, Ukraine, India, China, Italy, and Egypt. In Spain, major companies including telecommunications firm Telefónica were infected”. Authors Wong & Solon (2017) also wrote that a ransomware that may have begun from the “cyber weapon” theft associated to the U.S. Government, has possibly staggered hospitals across England and then extended to the countries across the world. “This is not an attack that was meant for large institutions. It was meant for anyone who got it.” Said Wong & Solomon, (2017). When compared with traditional weapons, cyber weapons have several different capabilities. First, cyber-weapons cause damage that’s less apparent but more extensive; Second, cyber-attack can happen instantly, and it can hit anywhere in the world, cyber-world has no boundaries, and third, if happens to be used, cyber weapon will be used only one time.
International cooperation efforts leave something to be desired
Currently, what is happening among many countries, the joint effort to pursue cyber-criminal investigation nationally is showing some good results. Unfortunately, on a regular basis, some vital information slip through the cracks, because of poor communication between state governments, and such lost information could have been used to avoid future problems.
In 2007, the FBI has formed a group of specialists jointly with U.S. intelligence and other organizations to fight the Internet crime and to detect and counter any form of cyber threats that arises towards the U. S. Their name is the National Cyber Investigative Joint Task Force (NCIJTF) and its recruits are training together at an anonymous site near Washington. This force is currently expanding and includes members of the U.S. Secret Service and numerous additional federal agencies. This type of cyber investigative association directed by the FBI is responsible for organizing, collecting, and distributing relevant information that are critical for conducting cyber threat investigations. In Internet Business Law Services (IBLS) article, published 2017, the Department of Homeland Security says about the joint project, that the task force is being expanded to include the U.S. Secret Service and other federal parties. The Secret Service explains that their responsibility as a part of fighting frauds will be to investigate “computer-based attacks on our nation’s financial, banking, and telecommunications infrastructure.” (IBLS, 2017). Also in the IBLS article (2017), the leader of NCIJTF group, Shawn Henry said that: “Our response has to constantly change and grow because the threat is constantly changing and growing.” (IBLS, 2017).
International cooperation helps cyber-crime investigation
Widespread cybercrime, that has become a transnational crime, has brought together crime fighting entities all around the globe and forced them into international collaboration, more than any other criminal activity. Cybercrime is extremely contemptuous to national authorities and physical borders, and such activity can spread criminal events internationally in a matter of seconds. It poses exceptional challenges to law enforcement entities everywhere in the world. On the other side, this type of activity has brought law entities together and it made them dependent on one another in fight with the criminals that commit the crimes. Besides having a mutual interest, it also benefits them to have mutual territories to operate together more proficiently and effectively.
One of the crucial steps taken to control international cybercrime issues was the implementation of Cybercrime Convention by European Council on 23 November 2001. This was the first international contract on technical and juridical aspects of discovering, investigating and indicting cybercriminals. It indicates efforts controlled at the national and international level, specifies the actions focused and directed towards prevention of illegal intrusion into computer systems. This Convention classified cybercrimes into four categories: 1. Computer system hacking; 2. Computer system fraud; 3. Forbidden content circulating on internet (such as racist websites and child pornography) and 4. Violation of copyright laws. (Golubev, 2005).
Lack of cooperation is problem in Europe and US
European countries and their law enforcement bodies suffer from the data retention directive assigned by the EU Court of Justice whose policy is fragmented. Eurojust and Europol have detected an increase of encrypted electronic data in current cyber-crime activities, therefore EU cyber investigators have to mainly handle the cases involving with these data. Besides the encrypted messaging interaction, virtual or crypto currencies also pose a substantial challenge to law enforcement. Use of encrypted messages, payments with crypto currencies, involvement of Dark-nets and anonymous perpetrators have made cybercrime prosecutions very difficult and almost untraceable. Therefore, it is vital to start cooperation between law enforcement organizations across whole Europe at early stages of investigations. Even so that international cooperation is critical to fight cybercrime, the exchange of the current legal frameworks differs significantly in many EU countries. There is a lack of uniform definitions related to cyber offences as well as provisions to investigate cyber-crimes. Another barrier to more successful cyber-crime investigation strategy is data protection law. Data protection law makes it difficult when data transfer is needed between private and public organizations, especially involvement of the Internet of Things, whose platform design lacks privacy and security measures. Yet another issue, which seems to be one of the major issues, is lack of law enforcement experts in field of cyber-crime investigations. Evolution of cyber threats is on rise, and the law enforcement are doing everything they can to educate and train new members to combat this type of crime. (Schallbruch, 2017, April 24).
Ever since terrorist attack in 2001, FBI authorities made fight against cyberterrorism and cybercrime one of the top priorities. Unfortunately, private-sector businesses collaboration in this fight remains poor. Only one-third of the total cybercrime that has happened to the businesses has been reported, according to Mueller, FBI Director, (Verton, 2002). FBI investigation and prediction capability cannot improve, unless more businesses step forward and collaborate with law enforcement on prosecuting cybercrimes.
Bangladesh central bank hack example
Let’s look at the example of the Bangladesh Central Bank hack. In February 2016, Bangladesh’s central bank suffered cyber-attack and let hackers steal over $80 Million from the bank accounts. This incident was successful robbery, due to installed Malware in the Bank’s computer systems. According to WIRED (2016) report, it is suspected that the hackers were able to steal SWIFT login credentials from one of the Bangladesh Bank employees, by sending a Remote Access Trojan (RAT) or a similar form of spyware which gave hackers the ability to remotely access and control bank’s computer. Then, hackers applied malware that covered their actions from actual workers, to buy them some time to wire money unnoticeably. The Bank could have lost even more, to be exact $850 Million, luckily, a spelling error in one of the transactions prevented a further robbery. (Zetter, 2016).
Tien Phong Bank in Vietnam Example
Soon after the news about the Bangladesh Bank theft got spread across the globe, Tien Phong Bank in Vietnam reported that it had suffered a similar event which was also performed in similar way, through SWIFT transaction. Fortunately, the bank was diligent enough to prevent the theft, and save itself a loss of $1.1 million. (Nguyen, 2015). According to author of an article” Vietnam’s TienPhongBank Stops attempted fraud through Swift System”, Peyton (2016), the bank authorities explained that bank performs transfers using third party infrastructure from an outside vendor who was hired to link it to the Swift system ban uses for messaging. The bank did not reveal the service provider name, although the bank has immediately stopped cooperation with that vendor and switched to a new system with much stronger security that enables bank to connect directly with Swift.
The Bangladesh Bank breach could have been prevented, should the Tien Phong Bank reported their experience immediately it had happened.
Wall Street Journal SWIFT related cyber heist in Ecuador
And that was not the end of the SWIFT heist. In May, 2016, the Wall Street Journal published another incident related to SWIFT cyber theft, which has actually happened in January, 2015, in Ecuador, with financial loss of $9 million dollars. Police investigators examining the theft of $81 million from Bangladesh’s central bank were amazed to find out about the case from three years ago, in which hackers stole $250,000 from the country’s largest commercial bank using similar methods.
Astonishingly, the Ecuador bank never reported the incident which was exactly the same as the Bangladesh Bank event. (Barrett & Burne 2016). The most unfortunate fact about these robberies is that $900 million dollars’ loss could have been prevented should Banks in Ecuador and Vietnam did what they supposed to do, report the incidents and rise international awareness. Unintentional error did more favor to prevent the robbery that the joined knowledge of these two independent nations.
Examining the costs and causes of cyber incidents
Cyber threats have been described as “among the gravest national security dangers to the United States” (The White House, 2015), and “an enormous and an exponentially growing threat” (Comey, 2013). In 2013, the President Obama, signed an executive order that directed NIST to build a framework that would serve as a dependable guideline for information security best practices. (Romanosky, 2016).
Descriptive analysis of cyber events
Graphic bellow shows the total number of incidents across the four different categories with data breaches shown in the left graph, and all are shown in the right graph. These data cover the 10-year period from 2005 to 2014.
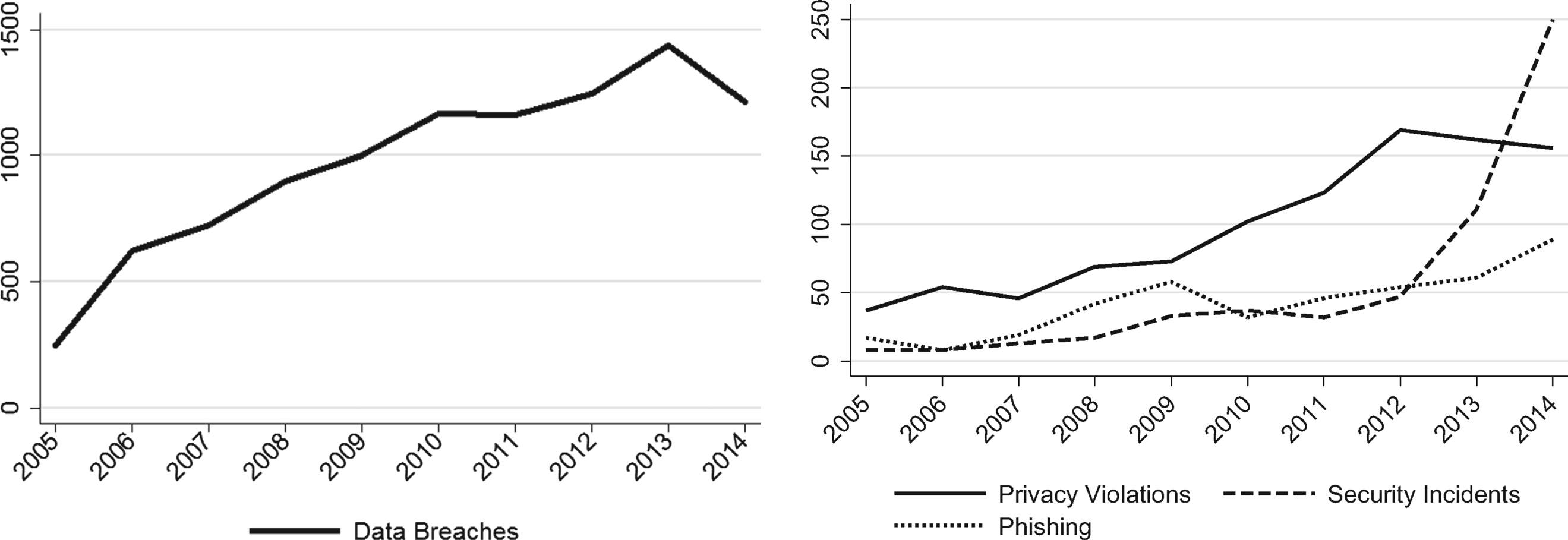
From: Examining the costs and causes of cyber incidents: J Cyber Security. 2016;2(2):121-135. doi:10.1093/cybsec/tyw001
Data presented in the graph shows increase of events from year 2005 on, though the amount of reported data breaches in some instances is to a greater degree than some other incidents. For example, data breach reports experience four-time increase in 2014 year compared to 2005 year. Privacy violations have face only a steady increase from 2005 year till 2014 year. The increase in data breaches could be due to efforts of some states to adopt breach disclosure laws. The modest increase in privacy violations is probably because of the nationwide attentiveness that suspected violations and early privacy incidents happened (such as rise in Facebook popularity, Google Street View, surveillance movement, etc.).
Looking at security incidents occurrences, we can see a very sharp rise between 2012 and 2014 year. The causal issue is uncertain because there were no significant industry and policy mediations that would initiate visible deviations in reporting. This absence in reporting can possibly mean that the rise is due an increase of actual events such as more security intrusions happening in the organizations.
Next graph bellow shows incidents and incident rates classified by North American Industry Classification System (NAICS):
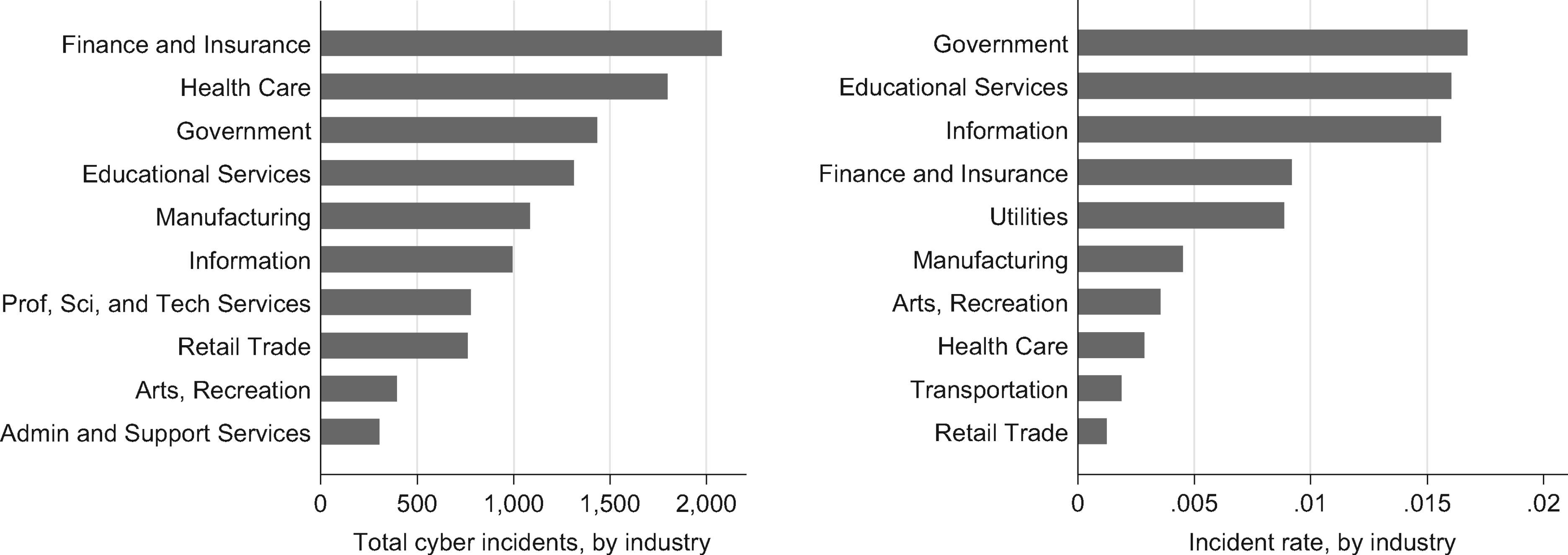
From: Examining the costs and causes of cyber incidents
J Cyber Security. 2016;2(2):121-135. doi:10.1093/cybsec/tyw001
There are some discrepancies that the NAICS (North American Industry Classification System) used for coding-it might have included only one segment of firms by industry and may not reflect actual perception of a firm’s activity. For example, Apple Inc. is categorized under manufacturing business, and health insurance companies are coded as Finance and Insurance, instead under Health Care. The left graph shows the most recurrent incidents by industry, whereas the right graph demonstrates the incident occurrence rate. This data has been collected from the database located at federal, state and local government. The results in the left graph show that Finance and Insurance, Health Care, and Government entities have experienced the highest occurrences of reported breaches. Looking at the graph on the right, its shown that Government agencies and companies within Education and Information systems are affected at a higher rate compared to all other industries. It is definitely true that not all cyber incidents are reported, detected, or recorded in database, neither that there are currently reliable methods that would estimate the number of ‘unknown’ cyber-attacks. (Romanosky, 2016).
6th Annual International Conference on cybersecurity in New York City – PPD 41
At the sixth annual International Conference on Cyber Security in New York City, Director James Comey announced Presidential Policy Directive 41, which confirmed that the FBI’s is going to be a major cyber incident response party, and highlighted the significance of a national discussion over encryption and the Going Dark concern. (Fbi, 2016).
The Scope of the Presidential Policy Directive 41 is to direct the Federal Government’s response to any cyber security event, for both government and private sectors. For major cyber security incidents, this PPD 41 is to coordinates the wider Federal Government response. The Departments of Justice and Homeland Security have to provide updated contact information available for general public in instances when cyber incidents happen, where and how to report such events to the appropriate authorities.
The Presidential Policy Directive 41have determined universal definitions as follows:
a. Cyber incident. An event occurring on or conducted through a computer network that actually or imminently jeopardizes the integrity, confidentiality, or availability of computers, information or communications systems or networks, physical or virtual infrastructure controlled by computers or information systems, or information resident thereon. For purposes of this directive, a cyber incident may include a vulnerability in an information system, system security procedures, internal controls, or implementation that could be exploited by a threat source.
b. Significant cyber incident. A cyber incident that is (or group of related cyber incidents that together are) likely to result in demonstrable harm to the national security interests, foreign relations, or economy of the United States or to the public confidence, civil liberties, or public health and safety of the American people.” According to publication “The White House” (2016).
PPD 41 Principles that will guide Incident Response are listed below:
a. Shared Responsibility. Individuals, the private sector, and government agencies have a shared vital interest and complementary roles and responsibilities in protecting the Nation from malicious cyber activity and managing cyber incidents and their consequences.
b. Risk-Based Response. The Federal Government will determine its response actions and the resources it brings to bear based on an assessment of the risks posed to an entity, our national security, foreign relations, the broader economy, public confidence, civil liberties, or the public health and safety of the American people.
c. Respecting affected entities. To the extent permitted under law, Federal Government responders will safeguard details of the incident, as well as privacy and civil liberties, and sensitive private sector information, and generally will defer to affected entities in notifying other affected private sector entities and the public. In the event a significant Federal Government interest is served by issuing a public statement concerning an incident, Federal responders will coordinate their approach with the affected entities to the extent possible.
d. Unity of Governmental Effort. Various government entities possess different roles, responsibilities, authorities, and capabilities that can all be brought to bear on cyber incidents. These efforts must be coordinated to achieve optimal results. Whichever Federal agency first becomes aware of a cyber incident will rapidly notify other relevant Federal agencies in order to facilitate a unified Federal response and ensure that the right combination of agencies responds to a particular incident. State, local, tribal, and territorial (SLTT) governments also have responsibilities, authorities, capabilities, and resources that can be used to respond to a cyber incident; therefore, the Federal Government must be prepared to partner with SLTT governments in its cyber incident response efforts. The transnational nature of the Internet and communications infrastructure requires the United States to coordinate with international partners, as appropriate, in managing cyber incidents.
e. Enabling Restoration and Recovery. Federal response activities will be conducted in a manner to facilitate restoration and recovery of an entity that has experienced a cyber incident, balancing investigative and national security requirements, public health and safety, and the need to return to normal operations as quickly as possible”. According to publication “The White House” (2016).
Cybercrime continues to fuel cybersecurity market growth
Cybersecurity Enterprises forecasts that global expenditure on cybersecurity services, experts, and products will exceed $1 trillion over the next five years. In 2004, the global cybersecurity marketplace was worth $3.5 billion and in it is estimated that it is worth more than $120 billion currently. It shows that cybersecurity marketplace increased roughly 35 times over 13 years. While all other technology divisions are motivated towards reducing inefficiencies and promoting efficiency, cybersecurity field expenses are inspired by cybercrime. The extraordinary cybercriminal activities currently happening, are causing so much investing in cyber spending, and it has become almost impossible for experts to accurately keep records of occurrences and expenditures. (Morgan, 2017).
IT analyst forecasts 12-15 percent cybersecurity market growth until 2021. Unfortunately, cybersecurity analysts are still unable to keep up with the dynamic cybercrime increase, epidemics of ransomware, malware relocating from desktop computers and laptops to mobile devices and smartphones, the distribution of billions of IoT devices that are under-protected, the masses of hackers-for-hire, and the more complex cyber-attacks affecting businesses, healthcare and educational institutions, governments, and consumers globally. Many businesses are tentative to publicize cybersecurity breaches they’ve experienced, as well as the expanses of their added security budgets, out of fear that it would spoil their reputation and out of fear to further irritate cybercriminals. (Morgan, 2017)
Luckily, there are some big organizations who have shown increase in cybersecurity budgets. For example, J.P. Morgan Chase & Co. has doubled their annual cybersecurity budget, and Bank of America has come forward stating that they have unlimited budget to spend on fight against cybercrime. Also, Microsoft continues to invest over $ 1 billion annually in many aspects of cybersecurity prevention, such as development and research.
According to The White House statement, the U.S. Government is planning on investing over $19 billion for cybersecurity in 2017. (Morgan, 2017).
IT security spending has become more difficult to track
IT security basically involves other non-computer devices, environments and platforms, which includes whole sub-markets such as aviation security, IoT security, automotive security, and IIoT (Industrial Internet of Things) security. These are all parts of the cybersecurity market. According to SANS institute, most organizations enclose their cybersecurity spending and budgets into another cost center.
Consumer spending on information-security is not encountered for and is often impossible to track, according to author Morgan (2017). Expenses that individuals pay someone to fix malware problems, to wipe and restore computer or smartphone, is usually unrecorded, therefore analysts are unable to take that into a count when they analyze cybersecurity costs. A consumer expenses include: installation of anti-virus programs, personal identity theft protection services, installation of malware protection software, computer and mobile phone patch-up services iin order to remove viruses or malware, data recovery and user instruction for future safer use and better cyber protection. The consumer cybersecurity marketplace is much bigger nowadays, and just like businesses, consumers are investing time and money to prevent future cyberattacks.
Ransomware developed and sold on dark-web
Ransomware has become one of the most profitable businesses for cybercriminals. If people know where to look, it’s very easy to buy it. Ransomware attacks are easy to do and majority of victims are willing to pay for ransom in order to quickly gain back access in their computer system. Some of the recent and well-known ransomware attacks that stroke computer systems across the world are Cerber, Locky, and the most famous one, WannaCry, which was the greatest challenge of the year, according to cybersecurity experts. The total profit of ransomware sales sold on dark web are estimated to be between $250,000 to over $6m for just one year. (Palmer, 2017).
The US cyber-security firm “Carbon Black” reported 2,502% increase in the ransomware Dark Web economy, compared to the 2016 year. To collect data for their report, Carbon Black researched the Dark Web websites that had forum posts offering to sell ransomware or ransomware services. They have found over 6,300 places where cyber criminals had broadcasted their crooked businesses with more than 45,000 ads listed. “Comparing 2016 vs. 2017 YTD, the ransomware marketplace on the dark web has grown from $249,287.05 to $6,237,248.90, a growth rate of 2,502%,” Carbon Black experts write in their report. “This economy extorts, according to the FBI, ransom payments that totaled about $1B in 2016, up from $24M in 2015.”, stated author of an article “Ransomware Dark Web Economy Increased by 2,502%”, Cimpanu (2017). Ransomaware as a Service (RaaS) promotion started in early 2017, which significantly contributed to Ransomware aggressive growth. Beside all this, there are also sole sellers (malware authors) who only sell the ransomware basics, and let the buyers deal with the rest the best they can. Interesting fact also discovered by Carbon Black experts is that some ransomware authors profit is more than $100,000 per year, which is much profitable than the average income of the legitimate software developer whose average annual salary is around $69,000. (Cimpanu, 2017).
Following the WannaCry ransomware attacks, that targeted hospitals and other main organizations, Microsoft has released a new patch for Windows XP. This product is formally no longer supported, but Microsoft is out of concerned for state-sponsored cyberattacks that has happened so far and will probably continue to happen. “In reviewing the updates for this month, some vulnerabilities were identified that pose elevated risk of cyberattacks by government organizations, sometimes referred to as nation-state actors, or other copycat organizations,” said Adrienne Hall, general manager of crisis management at Microsoft, in the article “Microsoft releases new update citing concern over state-sponsored attacks” by author Breland, (2017).
Nation-state sponsored attacks remain grave concern
Majority of nation state attacks, and we hear about them a lot lately, are about intelligence. One of the most recent and shocking example was the reported cyber-attack on the World Anti-Doping Agency (WADA), the one who suggested that all Russian athletes should be banned from participating in 2016 Rio Olympics, because it was exposed that the Russian government covered up doping use at the 2014 Winter Games in Sochi. Such statement caused anger among Russians, and in September 2016, A Russian Espionage Group, called “Fancy Bear “, attempted cyber-attack on WADA. As a revenge, Fancy Bear disclosed medical and Olympic records of top American athletes, and threatened to release more. Groups like “Fancy Bear” are using this type of strategy so they can be a step ahead of western countries. Therefore, western countries need to be ready to defend and prevent such attacks. (Loman, 2017).
Terrorist organizations actively recruiting on the internet
The Internet has become one of the most important tool for terrorists. According to experts, terrorist organizations communicate, share information, propaganda, coordinate attacks, recruit, raise funds through internet connections. Author Kaplan (2009) wrote in his article that, the number of terrorist web sites have drastically increased, from less than 100 to more than 4800, in the last decade. It seems that use of Internet is the most beneficial for terrorists to spread of propaganda. Why is that? It’s because, Internet offers secrecy. Terrorists have created complex encryption tools such as steganography-graphic message, and so called “dead dropping”-message sent through saved e-mail drafts accessible only to those who have a password. Western governments have strengthened surveillance of these sites, but prosecution of site operators is quite complicated, because it would violate civil rights, the Internet’s inherent anonymity, and some other factors.
Undoubtedly, Western governments and intelligence agencies have had a great success of blocking and taking down many terrorist propaganda cites by applying high-class technologies and experts. Nevertheless, they still encounter challenges, because the internet technology continues to advance at a high speed, faster that expert can catch up with such high dynamic growth. As soon as one application has been taken under control and taken down, the other one appears to replace the old one. It seems that there is no a long term solution to handle this never ending trend, rather, it seems an undoubtedly a quick fix measure. It also suffers deliberation of how these tactics are performed by the opposing political situations that may occur at the time of their distribution. Such tactics may furthermore push terrorist communications much beneath the radar and contradict any assistance that’s being offered.
Government actions indented to fight this rising threat, have been specified into three distinct methods: securitization, negotiation and intelligence-led collection and prosecution. Unfortunately, these methods did not experience a big success due to their incapability to keep up with the dynamics and highly resistant online propaganda characteristics, as well as and difficulties in designating an already demoted Islamic population who doesn’t have a trust in Western government authorities. A promising solution has been recommended that when used in combination with current government tactics and spreading on the current intelligence-led collection method, may offer more effective interruption of terrorist radicalization schemes. This approach has a goal to utilize secretly collected personal information of a terrorist that can be applied to discredit their reputation in the Islamic society, and that way to destabilize the radicalizing ideas that they propagate online. (Taylor, 2017).
All we could do now is to continue to bond together in a joint effort and keep fighting the good fight.
It turned out to be that the world is a small place after all and internet use trend is going to continue to grow, instead, it will advance into even more sophisticated operations. But that is not only thing that will continue to grow and develop. As the new technology arises, the criminal minds who are skilled enough to make a quick money on the easiest way possible, with big chance for not being caught, will grow in number and progress their skills. With that in mind, government leaders and private sectors are coming together to build a cohesive force, to prevent future cyberattacks and fight back, because a weakness in any area can cause worldwide chaos.
The International Multilateral Partnership Against Cyber-Terrorism (IMPACT) has been put together to unite the worldwide community to recognize, prevent and obstruct cyber-threats. Participation in the IMPACT organization is available to all countries, and developing countries are encouraged to join and take advantage of existing capability and knowledge, all together with the more developed countries that can assist in stopping attacks. Even research agencies and some corporations are called to join the organization.
IMPACT intentions are to discover network ideas and solutions that currently don’t exist. Its members will evaluate current security actions to establish what needs to be done to strengthen and protect the computer networks better. Besides protecting computer networks, this organization will also strive to defend critical infrastructure such as power grid, transportation, water system, communications, public and financial services, utilities and other personal information.
The main goal of IMPACT organization is to be more proactive against global cybercrimes rather than to be reactive to them. IMPACT goal is to also develop quick and immediate response systems so threats happened in one state can be stopped and removed before they spread to other regions. Through the joint effort, smaller and less developed countries will be better prepared to protect their computer network. “Each country, business and individual has to do their part to secure cyberspace,” Howard Schmidt, a member of the nine-person IMPACT international advisory board, says. Schmidt served as the cybersecurity adviser to the White House during part of the George W. Bush administration, and he also has worked as the chief security officer for major computer and Internet companies.” Written by author Boland, (2008).
International approach in fight is a must
It is discovered that around 80 percent of existing cyber breaches are caused by negligence and lack of users’ knowledge. Remaining 20 percent are due to more complexed methods, such as ransomware, malware, botnets, distributed denial of service attacks and other threats. Overall concern for cybercrime is on alert, but improving basic cyber hygiene will significantly contribute to overall better cyber protection and reduce cybercrime rates and overall damages that are result of it. Internet user education and training on cyber related criminal activities is a key factor that will need to get in effect immediately. Strategies to address cybercrime problems should include: raising awareness, being able to identify trusted resources, building an economic framework, working with invested partners, and implementing a response plan. (Dix, 2017). There are many proposed ideas related to this topic but realization of this proposals is still up in the air. Continuing improvement in cybersecurity requires comprehensive, coordinated and joint approach throughout stakeholder community.
U.S. The most prepared for cyberattacks
According to statistic graph bellow, United States appears to be the most prepared country to fight cybercrime, but it also showed that the U. S is the number one target for cyber espionage and cyber -attacks. Besides that, the U.S. is the second-most targeted country in DDoS (Denial of Service). With the average cost of a cyber-attack in the U.S. ranking at around $17.4 million, government and business organizations cannot allow that any cyber-incident might happen. It is recommended that organizations and companies should think of ways to improve security, as long as justifying these risks will balance off the costs. Graph bellow shows the list of countries from most prepared to least prepared for cyberattacks. (Desjardins, 2017).
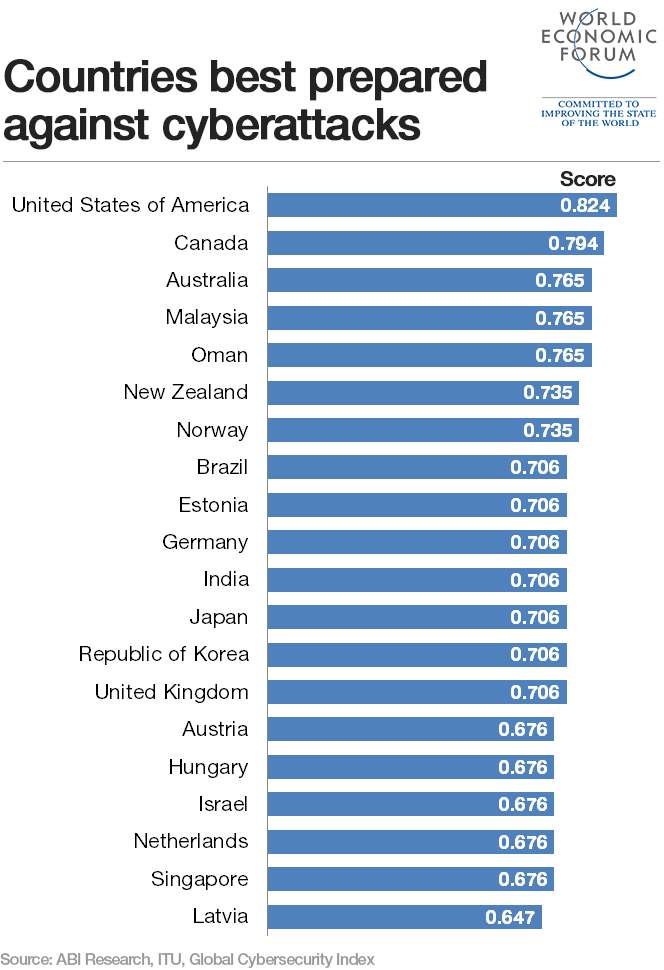
From: In a World Where Criminals keep Getting smarter, how should we fight cybercrime. https://www.weforum.org/agenda/2017/11/cybercrime-how-we-should-fight-criminals/
Conclusion
The internet has definitely revolutionized the way people connect these days and also the way data is distributed between interacting parties. Internet technology has made the world smaller in its distinctive way, as it has become an everyday standard and relatively essential part of our lives due to the fact that everyone and everything relies and revolves around internet technology. Despite all the benefits that internet technology has to offer, there are some downsides that also makes our world smaller. As people continue to sail in cyberspace waters and handle majority of professional businesses virtually, this has generated huge chances for cyber-crime. Widespread cybercrime, that we can freely say it is transnational crime, has brought together crime fighting entities all around the globe and forced them into international collaboration, more than any other criminal activity. Battle against cybercrime includes from the federal government, through state, tribal, local and territorial agencies. It must include Public sectors and industries to engage and cooperate in this fight. Cybercrime is not just a domestic problem, its worldwide problem that strikes and threatens economic and national security. Every living thing on this planet plays an important role in improving and protecting individual and mutual cybersecurity. With the mobile devices invention explosion and proliferation of the Internet of Things bringing new cyber challenges, people globally must involve at least basic protective techniques that will lower the risk, increase the cost and create difficulties for cybercriminals. United against cyber-crime, people on this planet will win over and aggressively fight back to strengthen national cybersecurity position in a limitlessly connected world. The whole planet needs to contribute to make an important difference with a sound and multidimensional approach against cybercrime.
References
Barrett, D. & Burne, K. (2016, May 19). Now It’s Three: Ecuador Bank Hacked Via Swift. Retrieved from: https://www.wsj.com/articles/lawsuit-claims-another-global-banking-hack-1463695820
Breland, A. (2017, June 13). Microsoft Releases New Update Citing Concern Over State-Sponsored Attacks. Retrieved from: http://thehill.com/policy/technology/337646-microsoft-releases-unusual-update-out-of-nation-state-concerns
Cimpanu, C. (2017, October 11). Ransomware Dark Web Economy Increased by 2,502%. Retrieved form: https://www.bleepingcomputer.com/news/security/ransomware-dark-web-economy-increased-by-2-502-percent/
Comey, J.(2013, July 12) Confirmation Hearing of James Comey. https://www.fbi.gov/news/podcasts/thisweek/james-comeys-confirmation-hearing.mp3/view
Desjardins, J. (2017, March 21). These are the Countries Most (and Least) Prepared for Cyber Attacks. Retrieved from: http://www.visualcapitalist.com/countries-least-prepared-cyber-attacks/
Dix, R. B. (2017, January 11). 5 Strategies for Addressing Cyber Crime. Retrieved from: https://gcn.com/articles/2017/01/11/strategies-addressing-cybercrime.aspx
Experian. (2017, June 27). Survey, Most Companies Ill-prepared for a global data breach. Retrieved from: http://www.experian.com/blogs/data-breach/2017/06/27/survey-companies-ill-prepared-global-data-breach/
Fbi. (2016, July 27). FBI Director Speaks at Cyber Security Gathering. Retrieved from: -https://www.fbi.gov/news/stories/fbi-director-speaks-at-cyber-security-gathering
Glover, T. (2012, January 7). Cyber-crime could trigger a global crisis. Retrieved from https://www.thenational.ae/business/money/cyber-crime-could-trigger-a-global-crisis-1.371191
Golubev, V. (2005, April 16). International cooperation in fighting cybercrime. Retrieved from: http://www.crime-research.org/articles/Golubev0405/
Internet Business Law Services. (2017). Internet Law- New US National Cyber Investigative Joint Task Force Will Be Led by FBI. Retrieved from: http://www.ibls.com/internet_law_news_portal_view.aspx?id=2044&s=latestnews
Loman, M. (2017, May 31). The Rise of Nation State Attacks- with Intelligence Gathering the Aim. Retrieved from:
Morgan, S. (2017, May 31). Cybersecurity Ventures Predicts Global Cybersecurity Spending will exceed $1 trillion from 2017 to 2021. Retrieved from: https://cybersecurityventures.com/cybersecurity-market-report/
Nguyen, H., K. (2016, May 15).Vietnam’s Tien Phong Bank says it was second bank hit by SWIFT cyberattack. Retrieved from: https://www.cnbc.com/2016/05/15/vietnams-tien-phong-bank-says-it-was-second-bank-hit-by-swift-cyber-attack.html
Palmer, D. (2017, October 11). Ransomware is now a big business on the dark web and malware developers are cashing in. Retrieved from: http://www.zdnet.com/article/ransomware-is-now-big-business-on-the-dark-web-and-malware-developers-are-cashing-in/
Rainie, L. & Anderson, J. (2017, June 6). The Internet of Things Connectivity Binge: What are the Implications? Retrieved from http://www.pewinternet.org/2017/06/06/the-internet-of-things-connectivity-binge-what-are-the-implications/
Romanosky, S. (2016, August 8). Examining the costs and causes of cyber incidents. Retrieved from https://academic.oup.com/cybersecurity/article/2/2/121/2525524
Schallbruch, M. (2017, April 24). Common Challenges in Combating Cybercrime. Retrieved from https://blog.esmt.org/dsi/?p=606
Stalans, L. J. (2016). Understanding How the Internet Facilitates Crime and Deviance. Retrieved from: http://www.tandfonline.com/doi/full/10.1080/15564886.2016.1211404?scroll=top&needAccess=true
The White House (2015, February 25) FACT SHEET: Cyber Threat Intelligence Integration Center. The White House, Office of the Press Secretary. Retrieved from: https://www.whitehouse.gov/the-press-office/2015/02/25/fact-sheet-cyber-threat-intelligence-integration-center
The White House, (2016, July 26). Presidential Policy Directive — United States Cyber Incident Coordination. Retrieved from https://obamawhitehouse.archives.gov/the-press-office/2016/07/26/presidential-policy-directive-united-states-cyber-incident
Wong, J. C.& Solon, O. (2017, May 12). Massive Ransomware Cyber-attack Hits Nearly 1000 Countries around the World. Retrieved from: https://www.theguardian.com/technology/2017/may/12/global-cyber-attack-ransomware-nsa-uk-nhs
Zetter, K. (2016, May 17). That Insane, $81M Bangladesh Bank Heist? Here’s What We Know. Retrieved from: https://www.wired.com/2016/05/insane-81m-bangladesh-bank-heist-heres-know/
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




